Zero Trust partner kit resources
It's important to help partners and customers design, architect, and deploy security solutions. These top-requested Zero Trust resources are available for you to use with your own organization and customers. They're ready for you to add your own branding.
Co-branded progress tracking resources
These resources for tracking Zero Trust progress are co-branded with the Contoso logo. Swap in your own logo. Customize the objectives and tasks. If you're ambitious, these trackers also include instructions for updating the colors and fonts to your own branding standards.
In this download:
- Blueprint for Zero Trust (Visio, can be saved as PDF).
- Business leader tracker for Zero Trust (PowerPoint).
- Implementer tracker for Zero Trust (Excel).
To learn more about these trackers, see Progress tracking resources for the adoption framework business scenarios.
![]()
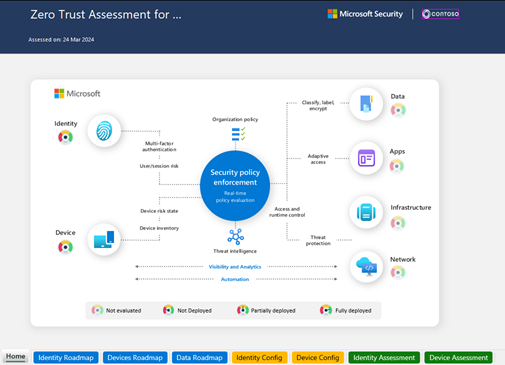
Microsoft Zero Trust workshop and assessment
This workshop is a comprehensive technical guide to help customers and partners adopt a Zero Trust strategy and deploy security solutions end-to-end to secure their organizations.
Learn how to run your own workshop and download the Excel assessment tool at https://aka.ms/ztworkshop
Co-branded architecture illustrations
Architecture diagrams like those included in our Zero Trust guidance help communicate how to apply the principles of Zero Trust to specific environments, from Microsoft 365 to specialized environments built in Azure or even Amazon Web Services (AWS). These illustrations help provide deeper technical guidance and recommendations. They provide a supported starting-point that you can adjust for your own environments. They help communicate design decisions and the relationships between components and security capabilities in an environment.
Visio templates, Visio stencils, and Microsoft icon sets
To help you work with reference architectures in the Zero Trust guidance center, you can download co-branded Visio template files along with Microsoft icon sets.
These 11x17 Visio template files are co-branded and leave plenty of room for your own work. Replace the Contoso logo with your own logo. Try out the template file that's themed with Microsoft Security colors. Or, work with the plain template file if you're not getting the results you want.
Other downloadable resources:
Visio stencils and icons To download more Visio template page sizes and, more importantly, Visio stencil files that include Microsoft icons, see Microsoft 365 architecture templates and icons. This Visio stencil set includes many conceptual icons, including many security symbols.
Azure icons To download Azure icons, see Azure architecture icons.
With both of these icon sets, you can download just the SVG files (scalable vector graphic). You can drag and drop these icon files into any tool, including Visio and PowerPoint.
Zero Trust architecture illustrations
These illustrations are replicas of the reference illustrations across the Zero Trust guidance center. Download and customize these illustrations for your organization and customers.
| Item | Description |
|---|---|
 Download Visio
Download Visio |
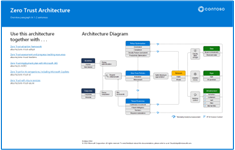
Zero Trust architecture High-level Zero Trust architecture. Use this illustration together with: |
 Download Visio
Download Visio |
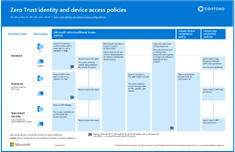
Zero Trust identity and device access policies This policy set is recommended for Microsoft 365, Azure-based solutions, and AI apps and companions. Use this illustration together with this set of articles. |
 Download Visio
Download Visio |
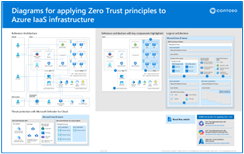
Apply Zero Trust principles to Azure IaaS Use these illustrations with these articles: |
 Download Visio
Download Visio |
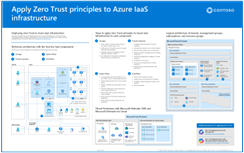
Apply Zero Trust principles to Azure IaaS - One page poster A one-page overview of the process for applying the principles of Zero Trust to Azure IaaS environments. |
 Download Visio
Download Visio |
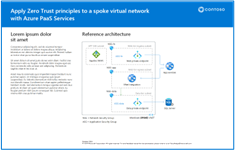
Apply Zero Trust principles to a spoke virtual network with Azure PaaS Services Use these illustrations with this article. |
 Download Visio
Download Visio |
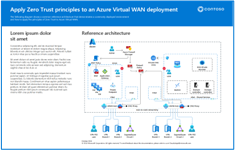
Apply Zero Trust principles to an Azure Virtual WAN deployment Use these illustrations with this article. |
 Download Visio
Download Visio |
Pilot and deploy Microsoft Defender XDR These illustrations include deployment processes and architecture illustrations for:
Use these illustrations together with: Pilot and deploy Microsoft Defender XDR. |
 Download Visio
Download Visio |
Implement Microsoft Sentinel and Microsoft Defender XDR for Zero Trust Use these illustrations together with these articles: Overview Step 1. Set up XDR tools Step 2. Architect a Microsoft Sentinel workspace Step 3. Ingest data sources and configure incident detection Step 4. Respond to an incident using Microsoft Sentinel and Microsoft Defender XDR |