Information Sharing and Exchange
The mission of Microsoft’s Government Security Program (GSP) is to build trust through transparency. Since the program’s inception in 2003, Microsoft has provided visibility into our technology and security artifacts, which governments and international organizations can use to help protect themselves and their citizens. The Information Sharing and Exchange offering enables Microsoft to share and exchange materials about security threats, vulnerabilities, anomalous behavior, malware information, and security issues against or related to Microsoft products and services.
This offering brings together groups and resources across the Microsoft environment to help governments protect citizens, infrastructure, and organizations.
The Information Sharing and Exchange (ISE) offering provides
| Name | Detail |
|---|---|
| Advanced Notice of Security Vulnerabilities | |
| Malicious URLs | |
| CTIP Botnet Feeds | |
| Clean File Meta Data | |
| Partnership |
Data Feeds Delivery
The feeds offered under the ISE authorization reside within several groups including the Microsoft Security Response Center (MSRC), the Digital Crimes Unit (DCU), Bing, and Product Release and Security Services (PRSS).
The GSP team provides a web-based application that allows GSP agencies to access the ISE data feeds from a single interface. All communications containing sensitive data are encrypted.
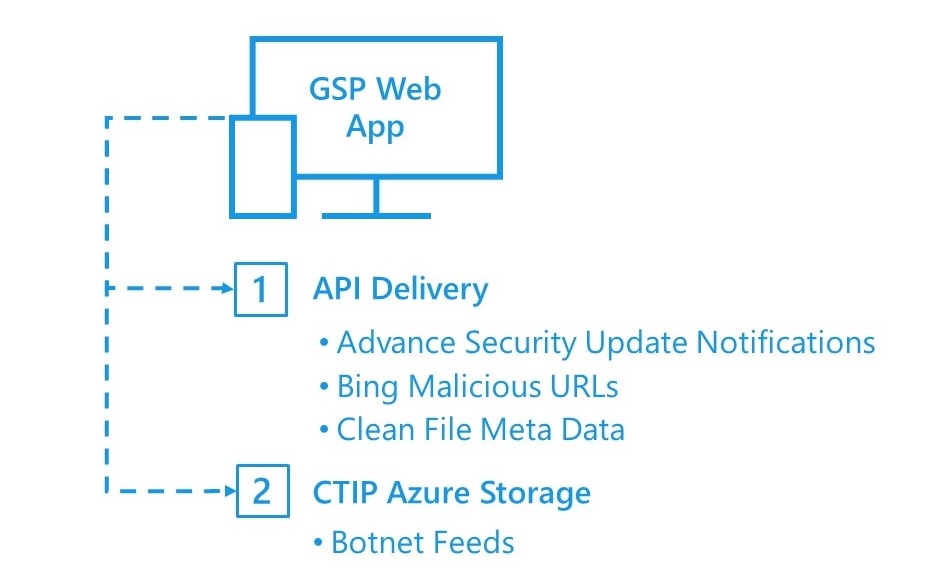
Data Use Descriptions
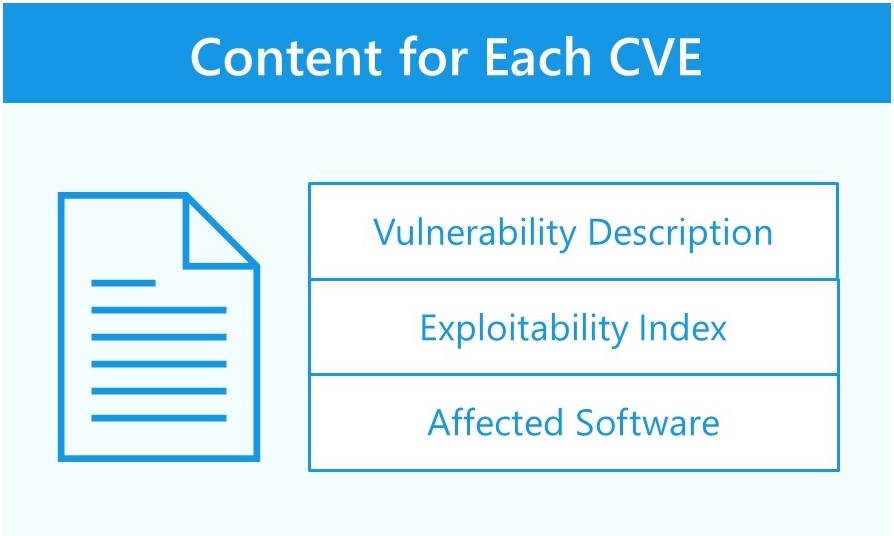
Advanced Security Update Notification The notice package lists all the CVEs (Common Vulnerabilities and Exposures) being addressed in the release. Each CVE contains a set of information including the Vulnerability Description (including metrics), Exploitability Index, and Affected Software.
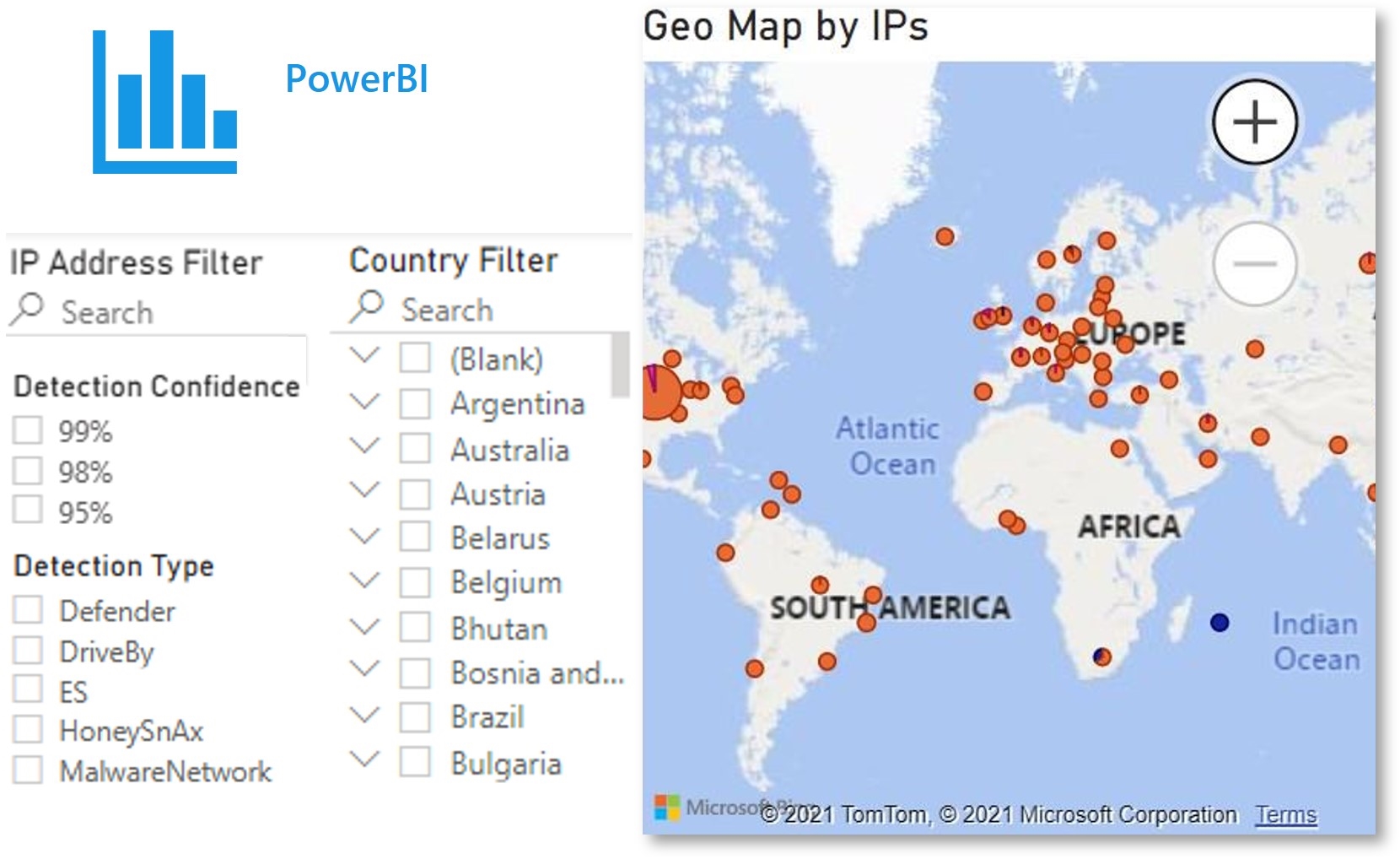
Bing Malicious URLs The Bing Malicious URL feed contains publicly facing servers or services that have been identified as being potentially malicious. New files are uploaded every three hours; full data sets are generated in 5 days. Many agencies import the JSON files directly into their existing threat intelligence analysis tools.

Clean File Meta Data (CFMD)
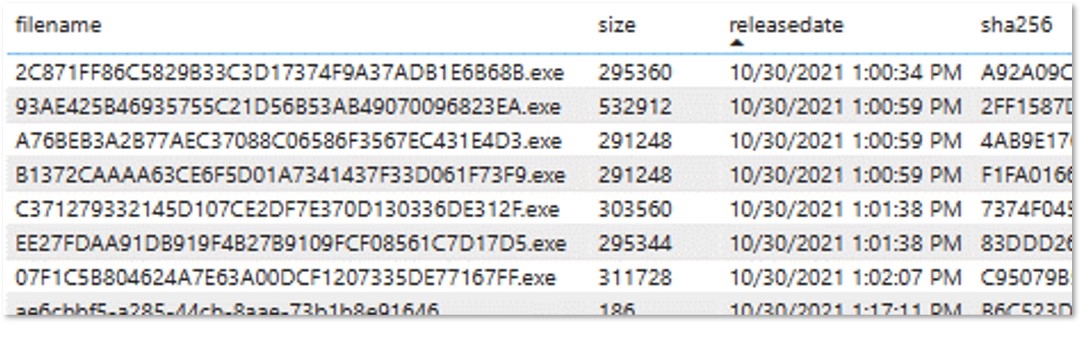
The Clean File Meta Data (CFMD) feed contains cryptographic signatures (SHA256 hashes) for the files contained within Microsoft products. These are often used in forensic examinations of potentially compromised devices and for allow/disallow file execution in critical systems.
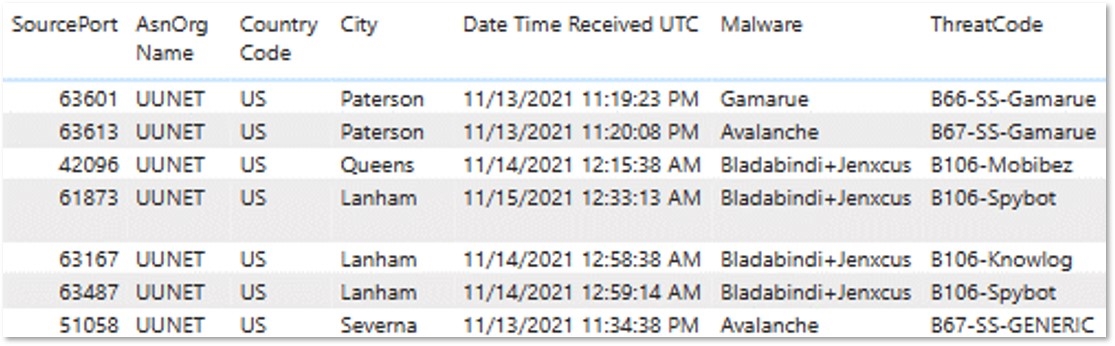
CTIP Botnet Feeds: Infected Data Feed
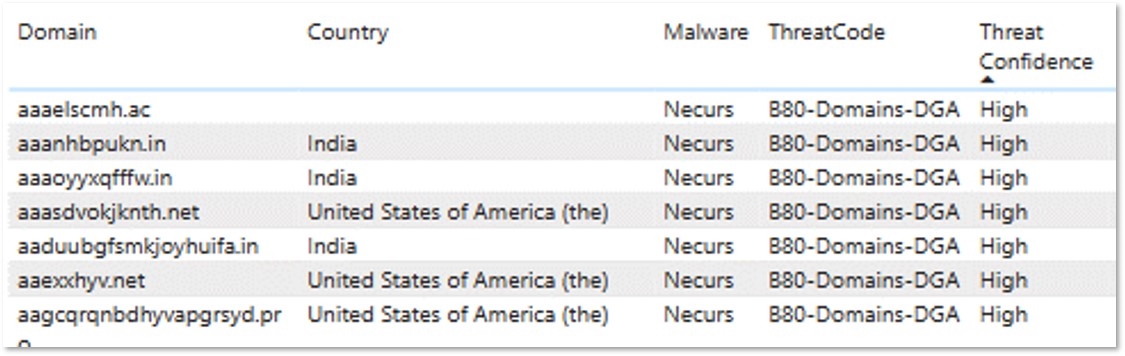
The DCU provides compromised victim botnet data via the DCU‘s CTIP threat intelligence service Infected device data feed, to enable network protection scenarios for CTIP subscribers, and to help facilitate remediation of the compromised systems with the goal of reducing the number of infected systems on the Internet. Other feeds include the Command and Control (C2), IoT, and Domains lists that are often used to restrict traffic flow to known malware networks via firewalls and protective DNS.
Contact Us
Contact your local Microsoft representative to learn more about the Government Security Program.