Video Page
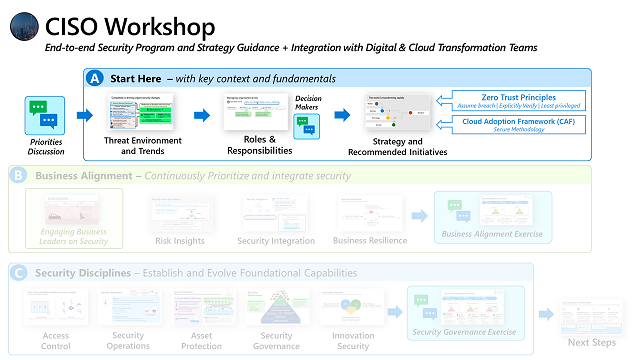
The CISO workshop provides security program and strategy guidance for securing the 'hybrid of everything' technical estate (on-premises, multi-cloud, IoT, OT, etc.)
Introduction and Overview
This video introduces the CISO workshop and provides an overview of its content.
Part A - Key Context and Fundamentals
These videos discuss threat trends, security role & responsibility evolution, and the recommended strategy and the strategic initiatives to structure your security transformation.
Threat Environment and Trends
Both the threat environment and the technical estates we operate are complex and constantly changing. Security must keep up with business and technology transformation, especially as we see ransomware and "as a service" models impacting business.
Roles & Responsibilities
This video discusses how the jobs to be done in security are evolving
Strategy and Recommended Initiatives
This video discusses the Zero Trust Transformation and modern security strategy that align to business goals, digital transformation, and cloud transformation. The 5 strategic initiatives in this video describe how to modernize your security program and capabilities using Zero Trust principles. This also includes guidance on avoiding extreme approaches that result in increased risk – skipping security completely and overly restrictive security.
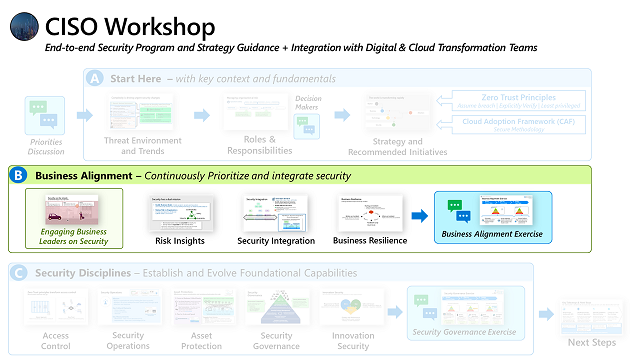
Part B - Business Alignment
These videos discuss how to engage business leaders on security, align to business priorities and risks, integrate security in IT/Business and build business resilience
Engaging Business Leaders on Security
Engaging business leaders on security topics can be tricky. This video uses a role playing approach to help security leaders take a straightforward approach with business leaders in their language. This discusses attacks and risks in business language, recommendations for measuring security program success, and asking for key business leader support that security teams need. This conversation helps you position security as an enabler and a partner to the larger organization.
Risk Insights
This video discusses how to align security priorities to business goals and existing risk management frameworks. This covers security’s dual goal of enabling business and reducing risk, as well as the various cybersecurity risk sources (and how these threats mirror legitimate organizations).
Security Integration
Discussion on how to successfully integrate security into IT and business processes and how to structure collaboration between security functions. This includes details on an emerging but critically important discipline of security posture management that focuses on reducing risk with visibility and preventative controls.
Business Resilience
Business resilience is the North Star of security programs, reducing business impact by balancing security investments before, during, and after attacks.
Maturity Model - Business Alignment
This video provides a review of maturity models describing the real-world journey to improve Risk Insights, Security Integration, and Business Resilience. This includes a discussion of specific concrete actions to help you move up to the next level.
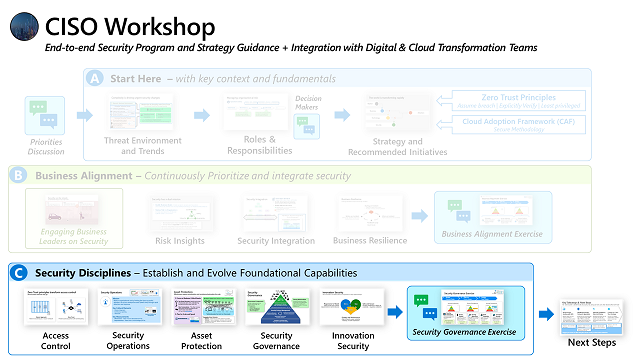
Part C - Security Disciplines
These videos discuss how to provide a clear structure for your security program using five key security disciplines
Access Control
This video is a discussion of the Zero Trust approach to access control that includes strong authentication, blending identity and network access into a single approach, and the Known-Trusted-Allowed model.
Security Operations
This video discusses modern security operations including key success metrics, key touchpoints with business leaders and functions, and key cultural elements.
Asset Protection
This is a discussion of key imperatives for teams that manage and secure assets, including prioritizing security based on business criticality and scaling efficiently across the large and growing set of assets in the technical estate.
Security Governance
This video describes Security Governance modernization and bridges the world of business goals and technology. This also covers the different components of security governance including risk, compliance, security architecture, posture management, (strategic) threat intelligence, and more.
Innovation Security
This video discusses how application security evolves into a modern approach (including DevSecOps) and key focus areas to drive success of this capability.
Maturity Model - Security Governance
This video provides a review of maturity model for the real-world journey to improve Security Architecture, Posture Management, and IT Security Maintenance. This includes a discussion of specific concrete actions to help you move these disciplines up to the next level.
Summary & Next Steps
Wrap-up of the workshop with key quick wins and next steps