Onboard macOS devices into Microsoft 365 overview
MacOS devices can be onboarded into Microsoft Purview solutions using either Intune or JAMF Pro. The onboarding procedures differ depending on which management solution you use. If your macOS devices have already been onboarded into Microsoft Defender for Endpoint (MDE), there are fewer steps. See Next steps for links to the appropriate procedures for you.
Applies to:
Tip
If you're not an E5 customer, use the 90-day Microsoft Purview solutions trial to explore how additional Purview capabilities can help your organization manage data security and compliance needs. Start now at the Microsoft Purview trials hub. Learn details about signing up and trial terms.
Before you begin
Before you get started with Endpoint DLP on macOS devices (the three latest versions), familiarize yourself with these articles:
If you aren't familiar with DLP at all, you should familiarize yourself with these articles as well:
- Learn about data loss prevention
- Plan for data loss prevention (DLP)
- Data loss prevention policy reference
If you aren't familiar with Insider Risk, read these articles:
Your macOS devices must already be managed through Intune or JAMF Pro.
- To onboard into Intune, see Deployment guide: Manage macOS devices in Microsoft Intune and Enroll your Mac with Intune Company Portal.
- To onboard into JAMF Pro see, JAMF Pro administrators guide and JAMF Pro Installation and Configuration Guide for Mac
Supported processors
macOS devices with x64 and M1, M2 and M3 (ARM64) processors are supported.
Supported browsers
Endpoint DLP supports these browsers on macOS (three latest released versions):
- Microsoft Edge (latest version)
- Safari (latest version, macOS only)
- Chrome (latest version)
- Firefox (latest version)
Licensing guidance
See, Microsoft 365 licensing guidance for information protection.
Conditions supported on macOS
Once a macOS device is onboarded into Microsoft Purview solutions, you can use the following condition with data loss prevention (DLP) policies:
Content Contains – Applies to documents that contain sensitive information types and sensitivity labels.
Content is not labeled - Applies to documents that do not contain any sensitivity labels as defined by Microsoft Purview Data Loss Prevention (DLP) policies.
File type is - This condition allows you to specify which types of files you want to monitor, restrict, or apply certain rules to, based on their format.
File extension is - This condition allows you to create policies that target files based on their extensions such as pdf, docx etc.
Activities that can be audited and restricted on macOS
Once a macOS device is onboarded into Microsoft Purview solutions, you can monitor and restrict the following actions using data loss prevention (DLP) policies.
Copy to a USB removable media – When enforced, this action blocks, warns, or audits the copying or moving of protected files from an endpoint device to USB removable media.
Copy to network shares – When enforced, this action blocks, warns, or audits the copying or moving of protected files from an endpoint device to any network share.
Print – When enforced, this action blocks, warns, or audits when protected files are printed from an endpoint device.
Copy to clipboard – When enforced, this action blocks, warns, or audits data in protected file that is being copied to a clipboard on an endpoint device.
Upload to cloud – This action blocks, warns, or audits when protected files are uploaded or prevented from being uploaded to cloud services based on the allow/unallowed domains list in global settings. When this action is set to warn or block, other browsers (defined on the unallowed browsers list under Global settings) are blocked from accessing the file.
Accessed by unallowed apps – When enforced, this action prevents applications that are on the unallowed apps list (as defined in Global settings) from accessing protected files on an endpoint device.
Onboarding devices into device management
You must enable device monitoring and onboard your endpoints before you can monitor and protect sensitive items on a device. Both of these actions are done in the Microsoft Purview portal.
When you want to onboard devices that haven't been onboarded yet, download the appropriate script and deploy it to those devices.
Open the Microsoft Purview portal Settings page and choose Enable device monitoring.
Note
While it usually takes about 60 seconds for device onboarding to be enabled, please allow up to 30 minutes before engaging with Microsoft support.
Open the Microsoft Purview Portal settings page and choose Turn on macOS device monitoring.
Tip
In preview Microsoft Purview Data Loss Prevention Just-in-time protection is available for macOS devices (three latest versions).
Next steps
Getting devices onboarded into Microsoft Purview solutions is required in order to receive DLP sensor telemetry and to enforce data loss prevention policies. As mentioned, macOS devices can be onboarded into Microsoft Purview solutions using either Intune or JAMF Pro. the following articles for the procedures appropriate to your situation.
| Topic | Description |
|---|---|
| Intune | For macOS devices that are managed through Intune |
| Intune for Microsoft Defender for Endpoint customers | For macOS devices that are managed through Intune and that have Microsoft Defender for Endpoint (MDE) deployed to them |
| JAMF Pro | For macOS devices that are managed through JAMF Pro |
| JAMF Pro for Microsoft Defender for Endpoint | For macOS devices that are managed through JAMF Pro and that have Microsoft Defender for Endpoint (MDE) deployed to them |
Device configuration and policy sync status
You can check the Configuration status and the Policy sync status of all your onboarded devices in the Devices list. For macOS devices, the Microsoft Defender for Endpoint (MDE) minimum version is 101.95.07. For more information on the configuration and policy status, select an onboarded device and then open the details pane.
Configuration status shows you whether the device is configured correctly, meets DLP configuration requirements, and the last time the configuration was validated. For macOS devices, configuration includes:
- If you use Intune, check the UPN configuration by making sure your devices are onboarded into Intune.
- If you use Intune, make sure that your devices are enrolled in the Company Portal
- If you use JAMF Pro, make sure your devices are onboarded before checking the UPN configuration.
Policy sync status shows you whether the most current versions of the endpoint DLP policies have been synchronized to the device and the last time a policy sync occurred.
| Field value | Configuration status | Policy sync status |
|---|---|---|
| Updated | Device health parameters are enabled and correctly set. | Device has been updated with the current versions of policies. |
| Not updated | You need to enable the configuration settings for this device. Follow the procedures for your environment: - Onboard and offboard macOS devices into Microsoft Purview solutions using Intune - Onboard and offboard macOS devices into Purview solutions using Intune for Microsoft Defender for Endpoint customers - Onboard and offboard macOS devices into Microsoft Purview solutions using JAMF Pro - Onboard and offboard macOS devices into Purview solutions using JAMF Pro for Microsoft Defender for Endpoint customers |
This device hasn't synced the latest policy updates. If the policy update was made within the last 2 hours, wait for the policy to reach your device. |
| Not available | Device properties aren't available in the device list. This could be because the device doesn't meet the minimum OS version or configuration, or because the device was just onboarded. | Device properties aren't available in the device list. This could be because the device doesn't meet the minimum OS version or configuration, or because the device was just onboarded. |
Important
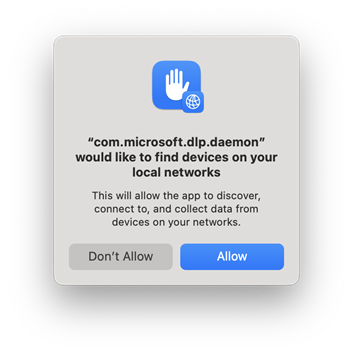
Users of macOS 15/Sequoia may see this dialog "com.microsoft.dlp.daemon" would like to find devices on your local networks. Admins can tell their user to select Allow to allow endpoint DLP to perform printer protection correctly.