Create a service principal for use with Microsoft Purview
You can create a new or use an existing service principal in your Microsoft Entra tenant to use to authenticate Microsoft Purview with other services. This article explains how to prepare a service principal for Microsoft Purview to use to authenticate with other services.
App registration
Follow the steps in this linked article section to create a service principal: Register an application with Microsoft Entra ID and create a service principal.
Tip
For the Redirect URL, if you have an authentication endpoint for your organization you want to use, add it there. Otherwise
https://example.com/authwill do.Once you've registered the app, copy the Application (client) ID value. We'll use this later to create a credential in Microsoft Purview.
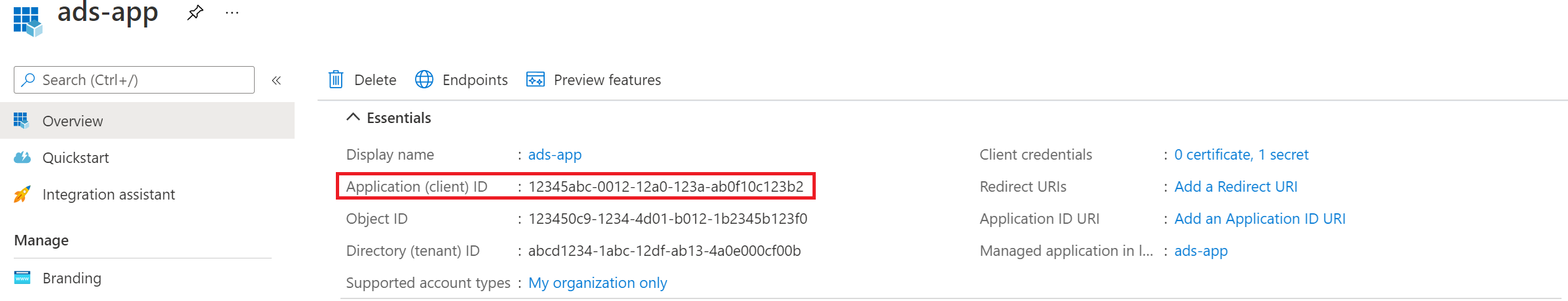
Adding a secret to the client credentials
Follow the steps in this linked article section to create a new client secret: Create a new client secret.
Copy the Secret value. We'll use this later to create a secret in Azure Key Vault.
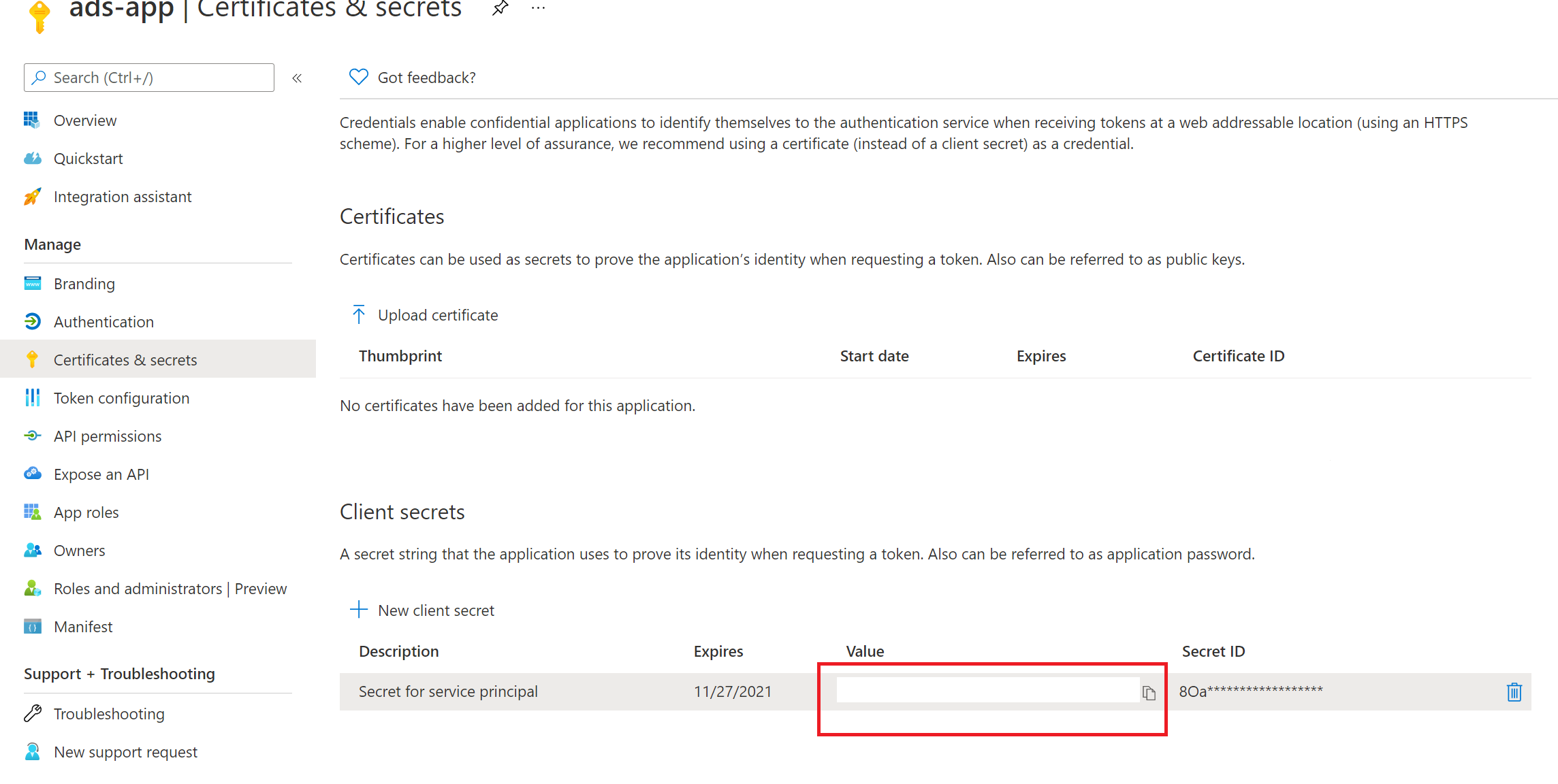
Adding the secret to your Azure Key Vault
To allow Microsoft Purview to use this service principal to authenticate with other services, you'll need to store this credential in Azure Key Vault.
- If you need an Azure Key vault, you can follow these steps to create one.
- To grant your Microsoft Purview account access to the Azure Key Vault, you can follow these steps.
Navigate to your Key vault.
Select Settings --> Secrets --> + Generate/Import
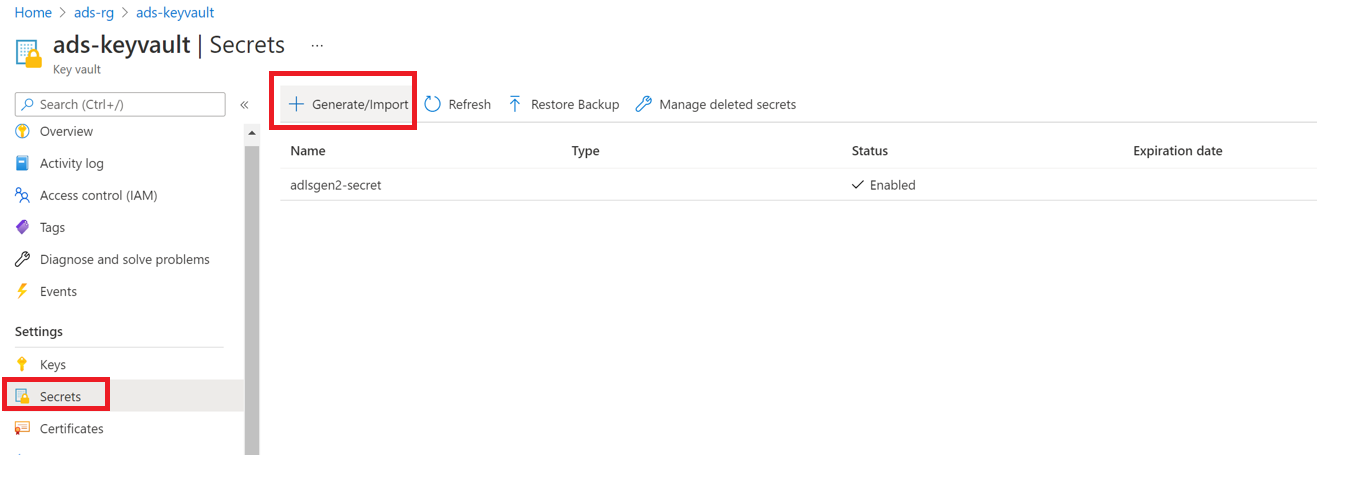
Enter the Name of your choice, and save it to create a credential in Microsoft Purview.
Enter the Value as the Secret value from your Service Principal.
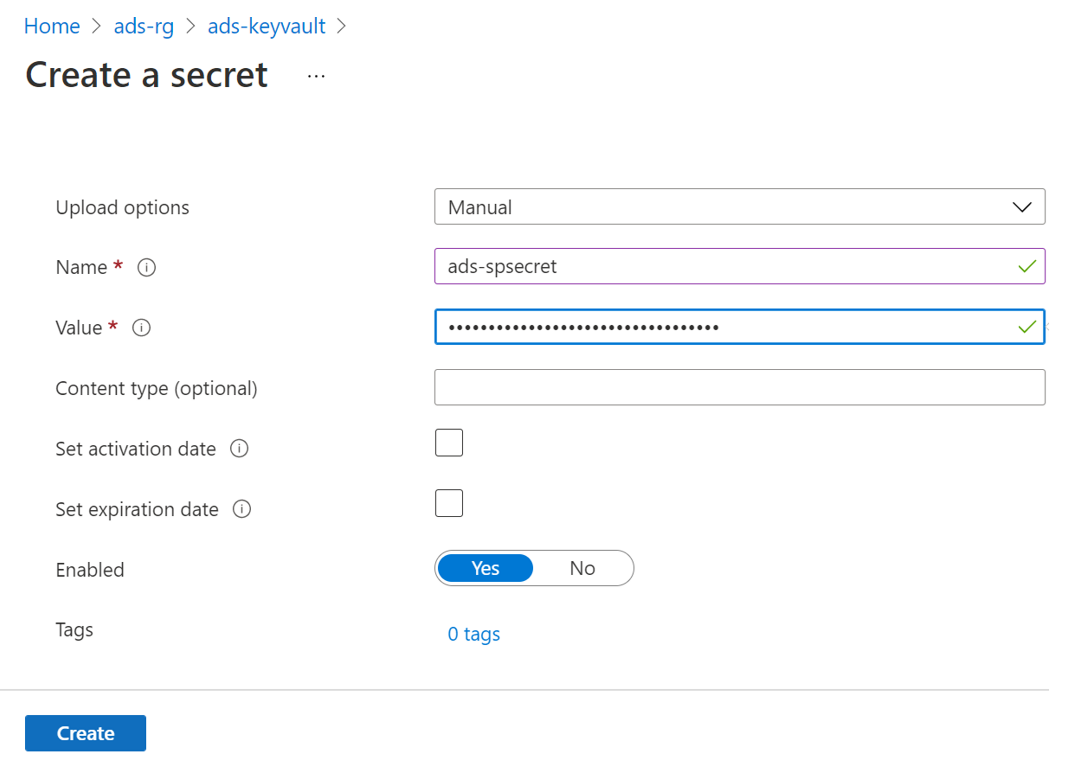
Select Create to complete.
Create a credential for your secret in Microsoft Purview
To enable Microsoft Purview to use this service principal to authenticate with other services, you'll need to follow these three steps.
- Connect your Azure Key Vault to Microsoft Purview
- Grant your service principal authentication on your source. Every source is different, so select your specific source page from the list of supported sources and follow instructions to assign permissions.
- Create a new credential in Microsoft Purview - You'll use the service principal's application (client) ID and the name of the secret you created in your Azure Key Vault.