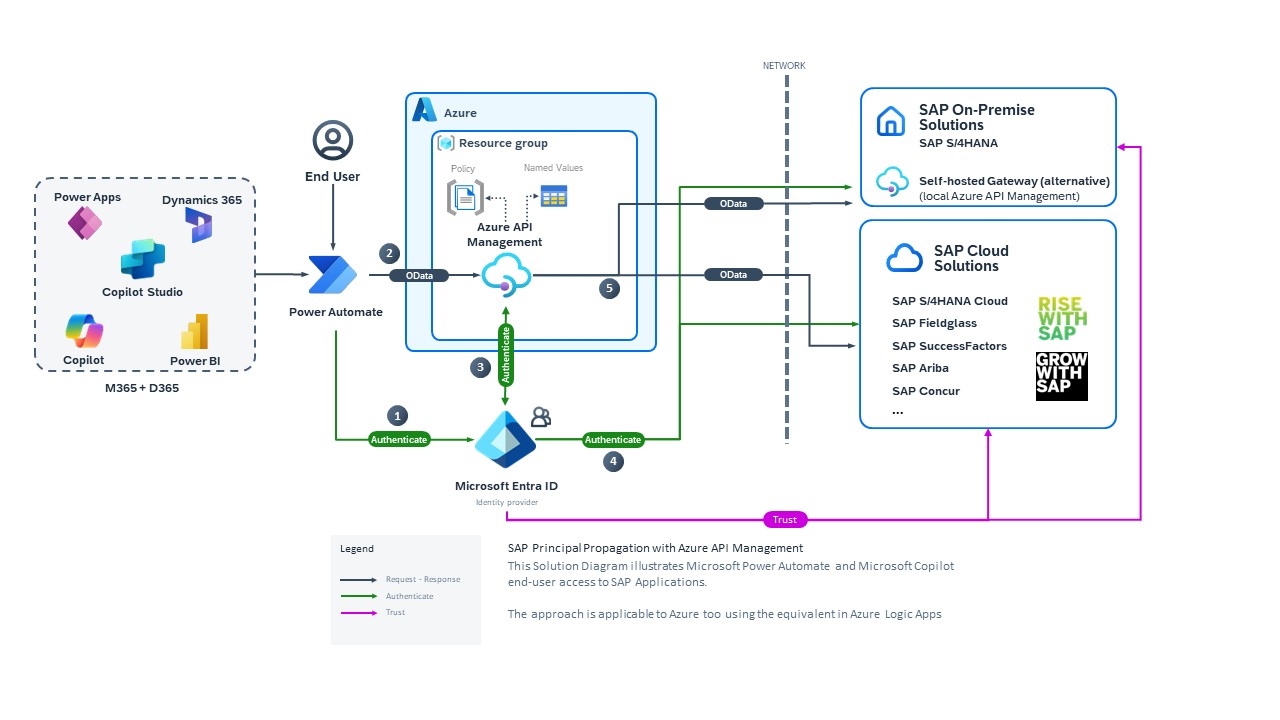
Set up Microsoft Entra ID, Azure API Management, and SAP for SSO from SAP OData connector
You can set up the SAP OData connector for Power Platform to use Microsoft Entra ID credentials for single sign-on (SSO) to SAP. This allows your users to access SAP data in Power Platform solutions without having to sign in multiple times to multiple services while honoring their authorizations and assigned roles in SAP.
This article walks you through the process, including setting up a trust between SAP and Microsoft Entra ID and configuring Azure API Management to convert the Microsoft Entra ID OAuth token to a SAML token that's used to make OData calls to SAP.
You can also gain additional insights and context into the setup process in the blog post, Hurray! SAP OData connector now supports OAuth2 and SAP Principal Propagation.
Prerequisites
- SAP instance
- Azure API Management resource
Download local provider SAML metadata from SAP
To set up a trust relationship between SAP and Microsoft Entra ID using SAML 2.0, first download the metadata xml file from SAP.
Perform these steps as an SAP Basis admin in SAP GUI.
In SAP GUI, run the transaction SAML2 to open the relevant SAP-client dependent wizard and choose the Local Provider tab.
Select Metadata, and then select Download Metadata. You'll upload the SAP SAML metadata to Microsoft Entra ID in a later step.
Take note of the URI-compliant Provider Name.
Note
Microsoft Entra ID requires this value to be URI-compliant. If Provider Name is already set and isn't URI-compliant, don't change it without first consulting your SAP Basis team. Changing the Provider Name can break existing SAML configurations. The steps for changing it are beyond the scope of this article. Check with your SAML Basis team for guidance.
Consult SAP's official documentation for additional info.
Import SAP metadata into Microsoft Entra ID enterprise application
Perform these steps as a Microsoft Entra ID admin in the Azure portal.
Select Microsoft Entra ID > Enterprise applications.
Select New application.
Search for SAP Netweaver.
Give the enterprise application a name, and then select Create.
Go to Single sign-on and select SAML.
Select Upload metadata file and select the metadata file that you downloaded from SAP.
Select Add.
Change the Reply URL (Assertion Consumer Service URL) to the SAP OAuth token endpoint. The URL is in the format
https://<SAP server>:<port>/sap/bc/sec/oauth2/token.Change the Sign-on URL to a URI-compliant value. This parameter isn't used and can be set to any value that's URI-compliant.
Select Save.
Under Attributes & Claims, select Edit.
Confirm that Claim name Unique User Identifier (Name ID) is set to user.userprincipalname [nameid=format:emailAddress].
Under SAML Certificates, select Download for Certificate (Base64) and Federation Metadata XML.
Configure Microsoft Entra ID as a trusted Identity Provider for OAuth 2.0 in SAP
Follow the steps outlined in the Microsoft Entra ID documentation for SAP NetWeaver and OAuth2 section.
Come back to this article once the OAuth2 client is created in SAP.
See SAP's official documentation about SAP NETWEAVER for additional details. Note, you must be an SAP administrator to access the information.
Create a Microsoft Entra ID application that represents the Azure API Management resource
Set up a Microsoft Entra ID application that grants access to the Microsoft Power Platform SAP OData connector. This application allows an Azure API Management resource to convert OAuth tokens to SAML ones.
Take these steps as a Microsoft Entra ID admin in the Azure portal.
Select Microsoft Entra ID > App registrations > New Registration.
Enter a Name, and then select Register.
Select Certificates & secrets > New client secret.
Enter a Description, and then select Add.
Copy and save this secret somewhere secure.
Select API Permissions > Add a permission.
Select Microsoft Graph > Delegated permissions.
Search for and select openid.
Select Add permissions.
Select Authentication > Add a platform > Web.
Set Redirect URIs to
https://localhost:44326/signin-oidc.Select Access tokens and ID tokens, and then select Configure.
Select Expose an API.
Next to Application ID URI, select Add.
Accept the default value and select Save.
Select Add a scope.
Set Scope name to user_impersonation.
Set Who can consent? to Admins and users.
Select Add a scope.
Copy the Application (client) ID.
Authorize the Azure API Management resource to access SAP Netweaver using the Microsoft Entra ID enterprise application
When a Microsoft Entra ID enterprise application is created, it creates a matching app registration. Find the App registration that matches the Microsoft Entra ID enterprise application that you created for SAP NetWeaver.
Select Expose an API > Add a client application.
Paste the Application (client) ID of the Microsoft Entra ID app registration of your Azure API Management instance into Client ID.
Select the user_impersonation scope, and then select Add application.
Authorize the Microsoft Power Platform SAP OData connector to access APIs exposed by Azure API Management
In the Microsoft Entra ID app registration of Azure API Management, select Expose an API > Add the client id of the Power Platform SAP OData connector
6bee4d13-fd19-43de-b82c-4b6401d174c3under authorized client applications.Select the user_impersonation scope, and then select Save.
Configure SAP OAuth
Create an OAuth 2.0 client in SAP that allows Azure API Management to obtain tokens on behalf of users.
See SAP's official documentation for details.
Perform these steps as an SAP Basis admin in SAP GUI.
Run the transaction SOAUTH2.
Select Create.
On the Client ID page:
- For OAuth 2.0 Client ID, select an SAP system user.
- Enter a Description, and then select Next.
On the Client Authentication page, select Next.
On the Grant Type Settings page:
- For Trusted OAuth 2.0 IdP, select the Microsoft Entra ID entry.
- Select Refresh Allowed, and then select Next.
On the Scope Assignment page, select Add, select the OData services that Azure API Management uses (e.g. ZAPI_BUSINESS_PARTNER_0001), and then select Next.
Select Finish.
Configure Azure API Management
Import the SAP OData XML metadata into your Azure API Management instance. Then, apply an Azure API Management policy to convert the tokens.
Open your Azure API Management instance and follow the steps to create an SAP OData API.
Under APIs, select Named values.
Add the following key/value pairs:
| Key | Value |
|---|---|
| AADSAPResource | SAP local provider URI |
| AADTenantId | Your tenant GUID |
| APIMAADRegisteredAppClientId | Microsoft Entra ID Application GUID |
| APIMAADRegisteredAppClientSecret | Client secret from earlier step |
| SAPOAuthClientID | SAP system user |
| SAPOAuthClientSecret | SAP system user password |
| SAPOAuthRefreshExpiry | Token refresh expiration |
| SAPOAuthScope | OData scopes chosen during SAP OAuth configuration |
| SAPOAuthServerAddressForTokenEndpoint | SAP endpoint for Azure API Management to call to perform the token acquisition |
Note
Be aware that the settings differ slightly for SAP SuccessFactors. For more information, see the Azure API Management policy for SAP SuccessFactors.
Apply the Azure API Management token policy
Use Azure API Management policies to convert a Microsoft Entra ID issued token to one that SAP NetWeaver accepts. This is done using the OAuth2SAMLBearer flow. See SAP's official documentation for more information.
Copy the Azure API Management policy from Microsoft's official GitHub page.
Open the Azure portal.
Go to your Azure API Management resource.
Select APIs, and then select the OData API that you created.
Select All operations.
Under Inbound processing, select Policies </>.
Delete the existing policy and paste the policy that you copied.
Select Save.
Related content
- SAP OData connector
- SAP OData connector now supports OAuth2 and SAP Principal Propagation | Power Automate community blog
- Azure API Management policy for SAP SuccessFactors | GitHub
- SAP OData connector for SAP SuccessFactors | SAP community blog
- The SAP Business Accelerator Hub also offers content related to the SAP integration suite policy for SuccessFactors and NetWeaver. You must have an SAP account to access this content.