Disable new connectors by default in GCC High and DoD
All new connectors that are introduced by Microsoft and partners to the Power Platform will be disabled by default for customers operating in the following US government clouds: GCC High and DoD. Administrators will be able to review these new connectors before authorizing their use across the organization in the Data policy page of the Power Platform admin center. Connectors already published in GCC High and DoD will remain enabled.
Power Platform and third parties continuously release new connectors and administrators can set a default classification for those connectors via its DLP policies. Depending on how these DLP policies are configured within the customer's tenant, new connectors can unintentionally become available to makers in certain environments without administrators approving their use. Such occurrences must be avoided in US government clouds where strict compliance is mandated. Administrators can rely on this safeguard mechanism in GCC High and DoD to better control the use of connectors.
Note
- Custom connectors can't be disabled via this new DLP control.
- When a connector is disabled, the administrators can still classify and configure the connector in the DLP policies, but its use will be blocked in Power Apps and Power Automate.
Availability
This feature is being progressively released, and all customers operating in GCC High and DoD will have access to it by the end of March 2022. Sign-up is not required.
Workflow
Step one: View the new connector
Select the Data policies tab where all DLP policies are located.
Select Enable connectors in the toolbar.
New connectors (those that haven’t been reviewed) have the status "Mark as reviewed".
Connectors that have already been reviewed and authorized have the status "Reviewed".
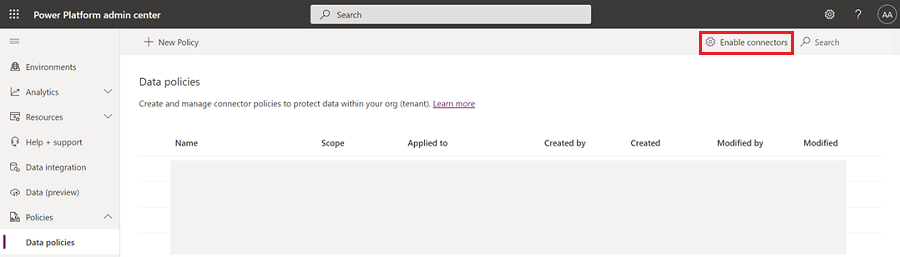
Step two: Enable or disable the new connector
If you want to keep the connector disabled, select Mark as reviewed.
If you want to enable the connector, select the Enable toggle.
In both cases, the status is changed to "Reviewing".
Select Save. The status of the connector is now set to "Reviewed".
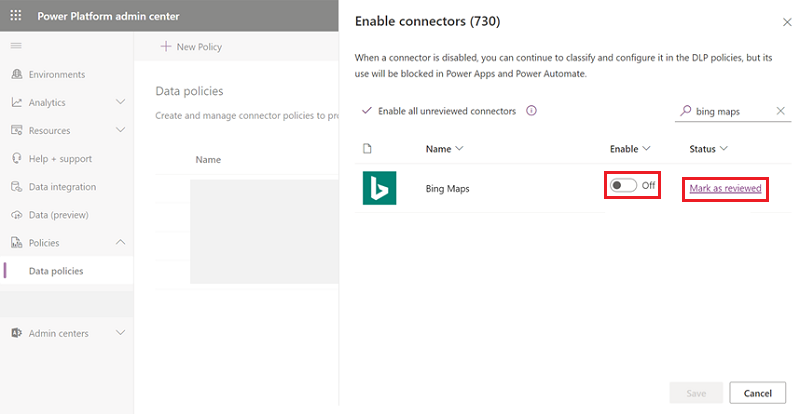
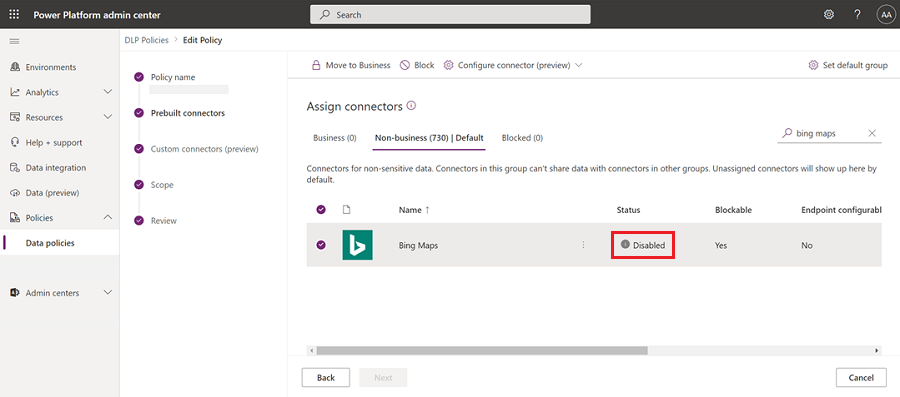
Step three: View a disabled connector in a DLP policy
Select a data policy in the Data policies page.
Consult the Prebuilt connectors tab. Connectors that are disabled have the status "Disabled".
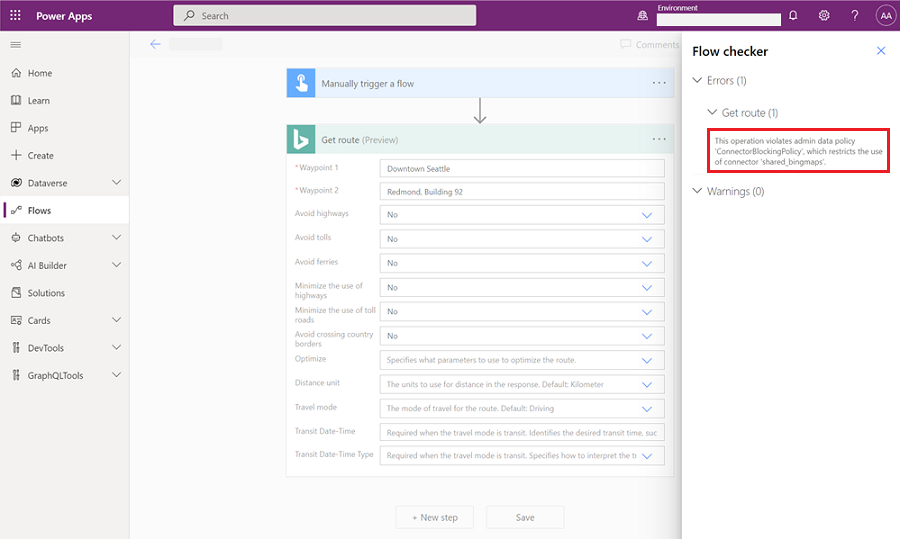
Step four: Attempt to add a disabled connector in a Power App
Open any Power App.
Add a connector that has been disabled. An error message appears.
Note
- This new tenant-level setting is also enforced on existing apps and flows that were built using connectors that are now disabled.
PowerShell support
The new DLP control has the following structure in PowerShell. The connectorSettings object is an array of connectors specifying whether it’s enabled or disabled ("behavior") and whether it has been reviewed or not ("isReviewed").
$connectorBlockingDefinition = [pscustomobject] @{
ConnectorSettings= @(
[pscustomobject] @{
id # connectorId -- string
behavior # connector behavior -- “Allow”/”Deny”
isReviewed # whether connector has been reviewed -- boolean
}
)
}
Retrieve the existing connector blocking policy for the tenant
Get-PowerAppDlpConnectorBlockingPolicies
Example:
Get-PowerAppDlpConnectorBlockingPolicies -TenantId “aaaabbbb-0000-cccc-1111-dddd2222eeee”
The above cmdlet outputs the connectors that are blocked/allowed for the evaluation and the policyId.
Create a new connector blocking policy for the tenant
New-PowerAppDlpConnectorBlockingPolicy –TenantId “aaaabbbb-0000-cccc-1111-dddd2222eeee” -ConnectorBlockingDefinition $connectorBlockingDefinition
Where $connectorBlockingDefinition = [pscustomobject] @{
ConnectorSettings= @
[pscustomobject] @{
id = “/providers/Microsoft.PowerApps/apis/connector1”
behavior = “Allow”
isReviewed = $true
},
[pscustomobject] @{
id = “/providers/Microsoft.PowerApps/apis/connector2”
behavior=”Deny”
IsReviewed=$false
}
)
}
Update the connector blocking policy for the tenant
Set-PowerAppDlpConnectorBlockingPolicy -TenantId “aaaabbbb-0000-cccc-1111-dddd2222eeee” -PolicyId “1aaaaaa1-2bb2-3cc3-4dd4-5eeeeeeeeee5” -ConnectorBlockingDefinition $connectorBlockingDefinition
Fetch the connector blocking policy using the policyId
Get-PowerAppDlpConnectorBlockingPolicy -TenantId “aaaabbbb-0000-cccc-1111-dddd2222eeee” -PolicyId “1aaaaaa1-2bb2-3cc3-4dd4-5eeeeeeeeee5”