Workloads supported by granular delegated admin privileges (GDAP)
Appropriate roles: All users interested in Partner Center
This article lists tasks for workloads supported by granular delegated admin privileges (GDAP).
Microsoft Security Copilot
Security Copilot supports GDAP access to the standalone platform and certain embedded experiences.
Supported Microsoft Entra roles
Security Copilot has its own non-Entra roles that you need to configure. The recommended roles to request for GDAP access are Security operator or Security reader, although other roles are supported. The customer must perform an extra step to assign the requested GDAP role to the appropriate Security Copilot role. For more information, see Assign roles for Security Copilot.
GDAP in Security Copilot provides access to the standalone portal. Each plugin requires extra authorization requirements that might not support GDAP. For more information, see Security Copilot plugins that support GDAP.
Embedded experiences add Security Copilot capabilities to other workloads. If those workloads support GDAP like Microsoft Defender XDR, the Security Copilot embedded capabilities support GDAP. For example, Purview has a Security Copilot embedded experience and is also listed as a workload that supports GDAP. So, Security Copilot in Purview supports GDAP.
For more information, see Security Copilot embedded experiences also.
Microsoft Entra ID
All Microsoft Entra tasks are supported except the following capabilities:
| Area | Capabilities | Issue |
|---|---|---|
| Group management | Creation of Microsoft 365 group, Administration of dynamic membership rules | Not supported |
| Devices | Administration of settings for Enterprise State Roaming | |
| Applications | Consenting to an enterprise application inline with sign-in, Administration of enterprise application 'User settings' | |
| External identities | Administration of external identity features | |
| Monitoring | Log analytics, Diagnostic settings, Workbooks, and the 'Monitoring' tab on Microsoft Entra overview page | |
| Overview page | My feed - roles for signed-in user | May display incorrect role information; doesn't affect actual permissions |
| User settings | 'User features' management page | Not accessible to certain roles |
Known issues:
- Partners who are granted Microsoft Entra roles Security Reader or Global Reader via GDAP are experiencing a "No Access" error when trying to access Entra Roles and administrators on a customer tenant with PIM enabled. Works with Global Administrator role.
- Microsoft Entra Connect Health doesn't support GDAP.
Exchange admin center
For the Exchange admin center, GDAP supports the following tasks.
| Resource type | Resource subtype | Currently supported | Issue |
|---|---|---|---|
| Recipient management | Mailboxes | Create Shared Mailbox, Update Mailbox, Convert to Shared/User Mailbox, Delete Shared Mailbox, Manage Mail-flow Settings, Manage Mailbox Policies, Manage Mailbox Delegation, Manage Email Addresses, Manage Automatic Replies, Manage More Actions, Edit Contact Information, Groups Management | Open another user's mailbox |
| Resources | Create/Add a Resource [Equipment/Room], Delete a Resource, Manage Hide from GAL setting, Manage Booking delegates settings, Manage Resource delegates settings | ||
| Contacts | Create/Add a Contact [Mail User/Mail Contact], Delete a Contact, Edit Organization Settings | ||
| Mail-flow | Message Trace | Start a Message Trace, Check default/custom/autosaved/downloadable queries, Rules | Alert, Alert Policies |
| Remote Domains | Add a Remote Domain, Delete a Remote Domain, Edit Message Reporting, Reply Types | ||
| Accepted Domains | Manage Accepted Domains | ||
| Connectors | Add a Connector, Manage Restrictions, Sent email identity, Delete Connector | ||
| Roles | Admin Roles | Add Role Group, Delete Role Groups that aren't in-built Role Groups, Edit Role Groups that aren't in-built Role Groups, Copy Role Group | |
| Migration | Migration | Add Migration Batch, Try Google Workspace Migration, Approve Migration Batch, View Details of the Migration Batch, Delete Migration Batch | |
| Microsoft 365 admin center link | Link to go to Microsoft 365 Admin Center | ||
| Miscellaneous | Give Feedback Widget, Support Central Widget | ||
| Dashboard | Reports |
Supported RBAC roles include the following:
- Exchange Administrator
- Global Administrator
- Helpdesk Administrator
- Global Reader
- Security Administrator
- Exchange Recipient Administrator
Microsoft 365 admin center
Important
Some key features of the Microsoft 365 admin center can be affected by service incidents and ongoing development work. You can view active Microsoft 365 admin center issues at Microsoft Admin portal.
We're excited to announce the release of the Microsoft 365 admin center support for GDAP. With this preview release, you have the ability to sign in to the admin center with all of the Microsoft Entra roles supported by enterprise customers except Directory Readers.
This release has limited capabilities and helps you use the following areas of the Microsoft 365 admin center:
- Users (including assigning licenses)
- Billing > Licenses
- Health > Service Health
- Support Central > Creating support ticket
Note
Starting September 23, 2024, you can no longer access Billing > Purchases menu or Billing > Bills & Payments per Admin On Behalf Of (AOBO) access to pages in Microsoft 365 admin center
Known issues:
- Can't export site usage product reports.
- Can't access Integrated apps in left nav.
Microsoft Purview
For Microsoft Purview, GDAP supports the following tasks.
| Solution | Currently supported | Issue |
|---|---|---|
| Audit | Microsoft 365 auditing solutions - Set up basic/advanced audit - Search audit log - Using PowerShell to search audit log - Export/configure/view audit log - Turn auditing on and off - Manage audit log retention policies - Investigate common issues/compromised accounts - Export/configure/view audit log |
|
| Compliance Manager | Compliance Manager - Build and manage assessments - Create/extend/modify assessment templates - Assign and complete improvement actions - Set user permissions |
|
| MIP | Microsoft Purview Information Protection Learn about data classification Learn about data loss prevention Data Classification: - Create and manage sensitive information types - Create and manage Exact Data Match - Monitor what's being done with labeled content using Activity Explorer Information Protection: - Create and publish sensitivity labels and label policies - Define labels to be applied to files and emails - Define labels to be applied to sites and groups - Define labels to be applied to schematized data assets - Automatically apply a label to content using client-side autolabeling and server-side autolabeling and schematized data assets - Restrict access to labeled content using encryption - Configure privacy and external user access and external sharing and conditional access for labels applied to sites and groups - Set label policy to include default, mandatory, downgrade controls and apply them to files and emails, groups, and sites and Power BI content DLP: - Create, test, and tune a DLP policy - Perform alerts and incident management - View DLP rule match events in activity explorer - Configure Endpoint DLP settings |
- View labeled content in Content Explorer - Create and manage Trainable Classifiers - Groups and Sites label support |
| Microsoft Purview Data Lifecycle Management | Learn about Microsoft Purview Data Lifecycle Management in Microsoft 365 - Create and manage static and adaptive retention policies - Create retention labels - Create retention label policies - Create and manage adaptive scopes |
- Archiving - Import PST files |
| Microsoft Purview Records Management | Microsoft Purview Records Management - Label content as a record - Label content as a regulatory record - Create and manage static and adaptive retention label policies - Create and manage adaptive scopes - Migrate retention labels and manage your retention requirements with file plan - Configure retention and deletion settings with retention labels - Retain content when an event occurs with event-based retention |
- Disposition management |
To learn about supported Microsoft Entra roles in Microsoft 365 compliance portal, see Permissions in the Microsoft Purview
Microsoft 365 Lighthouse
Microsoft 365 Lighthouse is an admin portal that helps Managed Service Providers (MSPs) secure and manage devices, data, and users at scale for small and medium-sized business customers.
GDAP roles grant the same customer access in Lighthouse as when those GDAP roles are used to access customers' admin portals individually. Lighthouse provides a multitenant view across users, devices, and data based on users' level of delegated permissions. For an overview of all Lighthouse multitenant management functionality, see the Lighthouse documentation.
Now MSPs can use Lighthouse to set up GDAP for any customer tenant. Lighthouse provides role recommendations based on different MSP job functions for an MSP, and Lighthouse GDAP templates enable partners to easily save and reapply settings that enable least-privileged customer access. For more information, and to view a demo, see the Lighthouse GDAP setup wizard.
For Microsoft 365 Lighthouse, GDAP supports the following tasks. For more information on permissions required to access Microsoft 365 Lighthouse, see Overview of permissions in Microsoft 365 Lighthouse.
| Resource | Currently supported |
|---|---|
| Home | Included |
| Tenants | Included |
| Users | Included |
| Devices | Included |
| Threat management | Included |
| Baselines | Included |
| Windows 365 | Included |
| Service health | Included |
| Audit logs | Included |
| Onboarding | Customers must have either a GDAP and indirect reseller relationship, or a DAP relationship to be onboarded. |
Supported Azure role-based access control (Azure RBAC) roles include the following:
- Authentication Administrator
- Compliance Administrator
- Conditional Access Administrator
- Cloud Device Administrator
- Global Administrator
- Global Reader
- Helpdesk Administrator
- Intune Administrator
- Password Administrator
- Privileged Authentication Administrator
- Security Administrator
- Security Operator
- Security Reader
- Service Support Administrator
- User Administrator
Windows 365
For Windows 365, GDAP supports the following tasks.
| Resource | Currently supported |
|---|---|
| Cloud PC | List Cloud PCs, Get Cloud PC, Reprovision Cloud PC, End grace period, Reprovision Cloud PC remote action, Bulk reprovision Cloud PCs remote action, Resize Cloud PCs remote action, Get Cloud PC remote action results |
| Cloud PC device image | List device images, Get device image, Create device image, Delete device image, Get source image, Reupload device image |
| Cloud PC on-premises network connection | List on-premises connection, Get on-premises connection, Create on-premises connection, Update on-premises connection, Delete on-premises connection, Run health checks, Update AD domain password |
| Cloud PC provisioning policy | List provisioning policies, Get provisioning policy, Create provisioning policy, Update provisioning policy, Delete provisioning policy, Assign provisioning policy |
| Cloud PC audit event | List audit events, Get audit event, Get audit activity types |
| Cloud PC user setting | List user settings, Get user setting, Create user setting, Update user setting, Delete user setting, Assign |
| Cloud PC supported region | List supported regions |
| Cloud PC service plans | List service plans |
Supported Azure RBAC roles include the following:
- Global Administrator
- Intune Administrator
- Security Administrator
- Security Operator
- Security Reader
- Global Reader
- (In verification) Windows 365 Administrator
Unsupported resources for preview:
- N/A
Teams admin center
For the Teams admin center, GDAP supports the following tasks.
| Resource | Currently supported |
|---|---|
| Users | Assign policies, Voice settings, Outbound calling, Group call pickup settings, Call delegation settings, Phone numbers, Conferencing settings |
| Teams | Teams policies, Update policies |
| Devices | IP phones, Teams Rooms, Collaboration bars, Teams displays, Teams panels |
| Locations | Reporting labels, Emergency addresses, Network topology, Networks and locations |
| Meetings | Conference bridges, Meeting policies, Meeting settings, Live events policies, Live events settings |
| Messaging policies | Messaging policies |
| Voice | Emergency policies, Dial plans, Voice routing plans, Call queues, Auto attendants, Call park policies, Calling policies, Caller ID policies, Phone numbers, Direct routing |
| Analytics and reports | Usage reports |
| Org-wide settings | External access, Guest access, Teams settings, Teams upgrade, Holidays, Resource accounts |
| Planning | Network planner |
| Teams PowerShell module | All PowerShell cmdlets from the Teams PowerShell module (available from the Teams PowerShell module - 3.2.0 Preview version) |
Supported RBAC roles include the following:
- Teams Administrator
- Global Administrator
- Teams Communications Administrator
- Teams Communications Support Engineer
- Teams Communications Support Specialist
- Teams Device Administrator
- Global Reader
Unsupported resources for GDAP access include the following:
- Manage Teams
- Team templates
- Teams Apps
- Policy packages
- Teams advisor
- Call Quality Dashboard
- Operator Connect
Microsoft Defender XDR
Microsoft Defender XDR is a unified pre- and post-breach enterprise defense suite. It natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
The Microsoft Defender portal is also the home of other products in the Microsoft 365 security stack, such as Microsoft Defender for Endpoint and Microsoft Defender for Office 365.
Documentation of all capabilities and security products is available in the Microsoft Defender portal:
Microsoft Defender for Endpoint:
- Microsoft Defender for Endpoint
- Microsoft Defender for Endpoint P1 capabilities
- Microsoft Defender for Business
Microsoft Defender for Office 365:
- Exchange Online Protection (EOP)
- Microsoft Defender for Office 365 Plan 1
- Microsoft Defender for Office 365 Plan 2
App governance:
The following are capabilities that are available for tenants accessing the Microsoft Defender portal using a GDAP token.
| Resource type | Currently supported |
|---|---|
| Microsoft Defender XDR features | All Microsoft Defender XDR features (as listed in the previously linked documentation): Incidents, Advanced hunting, Action Center, Threat Analytics, Connection of the following security workloads into Microsoft Defender XDR: Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Defender for Cloud Apps |
| Microsoft Defender for Endpoint features | All Microsoft Defender for Endpoint features listed in the previously linked documentation, see details per P1 / SMB SKU in the table. |
| Microsoft Defender for Office 365 | All Microsoft Defender for Office 365 features listed in the previously linked documentation. See details per each license in this table: Office 365 Security including Microsoft Defender for Office 365 and Exchange Online Protection |
| App Governance | Authentication works for GDAP token (App+User token), Authorization policies work according to the user roles as before |
Supported Microsoft Entra roles in Microsoft Defender portal:
Documentation of supported roles in Microsoft Defender portal
Note
Not all roles are applicable to all security products. For information about what roles are supported in a specific product, refer to the product documentation.
Supported MDE features in Microsoft Defender portal per SKU
| Endpoint capabilities per SKU | Microsoft Defender for Business | Microsoft Defender for Endpoint Plan 1 | Microsoft Defender for Endpoint Plan 2 |
|---|---|---|---|
| Centralized management | X | X | X |
| Simplified client configuration | X | ||
| Threat and vulnerability management | X | X | |
| Attack surface reduction | X | X | X |
| Next-gen protection | X | X | X |
| Endpoint detection and response | X | X | |
| Automated investigation and response | X | X | |
| Threat hunting and six-month data retention | X | ||
| Threat analytics | X | X | |
| Cross-platform support for Windows, MacOS, iOS, and Android | X | X | X |
| Microsoft threat experts | X | ||
| Partner APIs | X | X | X |
| Microsoft 365 Lighthouse for viewing security incidents across customers | X |
Power BI
For the Power BI workload, GDAP supports the following tasks.
| Resource type | Currently supported |
|---|---|
| Administrator tasks | - All menu items under "Admin portal" except "Azure connections" |
Supported Microsoft Entra roles in scope:
- Fabric Administrator
- Global Administrator
Power BI properties out of scope:
- Not all nonadministrator tasks are guaranteed to work
- "Azure connections" under Admin portal
SharePoint
For SharePoint, GDAP supports the following tasks.
| Resource type | Currently supported |
|---|---|
| Homepage | Cards render but data might not render |
| Sites Management – Active Sites | Create sites: Team site, Communication site, Assign/change site owner, Assign sensitivity label to site (if configured in Microsoft Entra ID) during site creation, Change sensitivity label of site, Assign privacy settings to site (if not predefined with a sensitivity label), Add/Remove members to a site, Edit site external sharing settings, Edit site name, Edit site URL, View site activity, Edit storage limit, Delete a site, Change built-in views of sites, Export site list to CSV file, Save custom views of sites, Associate site with a Hub, Register site as a Hub |
| Sites Management – Active Sites | Create other sites: Document Center, Enterprise Wiki, Publishing Portal, Content Center |
| Sites Management – Deleted Sites | Restore site, Permanently delete site (except for Microsoft 365 group-connected team sites) |
| Policies – Sharing | Set External Sharing policies for SharePoint and OneDrive for Business, Change "More external sharing settings," Set policies for File and Folder links, Change "Other settings" for sharing |
| Access control | Set/change unmanaged device policy, Set/change idle sessions timeline policies, Set/change network location policy (separate from Microsoft Entra IP policy, Set/change modern authentication policy, Set/change OneDrive access |
| Settings | SharePoint - Home site, SharePoint - Notifications, SharePoint - Pages, SharePoint - Site creation, SharePoint - Site storage limits, OneDrive - Notifications, OneDrive - Retention, OneDrive - Storage limit, OneDrive - Sync |
| PowerShell | To connect a customer tenant as a GDAP admin, use a tenant authorization endpoint (with the customer's tenant ID) in the AuthenticanUrl parameter instead of the default common endpoint.For example, Connect-SPOService -Url https://contoso-admin.sharepoing.com -AuthenticationUrl https://login.microsoftonline.com/<tenantID>/oauth2/authorize. |
Roles in scope include the following:
- SharePoint Administrator
- Global Administrator
- Global Reader
SharePoint Admin Center properties out of scope include the following:
- All Classic Admin features/functionality/templates are out of scope and not guaranteed to work correctly
- Note: For any SharePoint Admin Center supported GDAP roles, partners can't edit files and permissions on files and folders in the customer SharePoint site. It was a security risk to customers and is now addressed.
Dynamics 365 and Power Platform
For Power platform and Dynamics 365 customer engagement applications (Sales, Service), GDAP supports the following tasks.
| Resource type | Currently supported |
|---|---|
| Administrator tasks | - All menu items in Power Platform admin center |
Supported Microsoft Entra roles in scope include the following:
- Power platform administrator
- Global administrator
- Helpdesk Administrator (for Help + Support)
- Service Support Administrator (for Help + Support)
Properties out of scope:
- https://make.powerapps.com doesn't support GDAP.
Dynamics 365 Business Central
For Dynamics 365 Business Central, GDAP supports the following tasks.
| Resource type | Currently supported |
|---|---|
| Administrator tasks | All tasks* |
* Some tasks require permissions assigned to the administrator user within the Dynamics 365 Business Central environment. Refer to the available documentation.
Supported Microsoft Entra roles in scope include the following:
- Dynamics 365 administrator
- Global administrator
- Help Desk administrator
Properties out of scope:
- None
Dynamics Lifecycle Services
For Dynamics Lifecycle Services, GDAP supports the following tasks.
| Resource type | Currently supported |
|---|---|
| Administrator tasks | All tasks |
Supported Microsoft Entra roles in scope include the following:
- Dynamics 365 administrator
- Global administrator
Properties out of scope:
- None
Intune (Endpoint Manager)
Supported Microsoft Entra roles in scope:
- Intune Administrator
- Global Administrator
- Global Reader
- Reports Reader
- Security reader
- Compliance Administrator
- Security Administrator
To check access level for the above roles, see the Intune RBAC documentation.
Support for Intune doesn't include use of GDAP when enrolling servers for Microsoft Tunnel, or for configuring or installing any of the connectors for Intune. Examples of Intune connectors include but aren't limited to the Intune Connector for Active Directory, Mobile threat defense connector, and the Microsoft Defender for Endpoint connector.
Known Issue: Partners accessing policies in office apps are displayed "Couldn't retrieve data for 'OfficeSettingsContainer.' Use guid to report this issue to Microsoft."
Azure portal
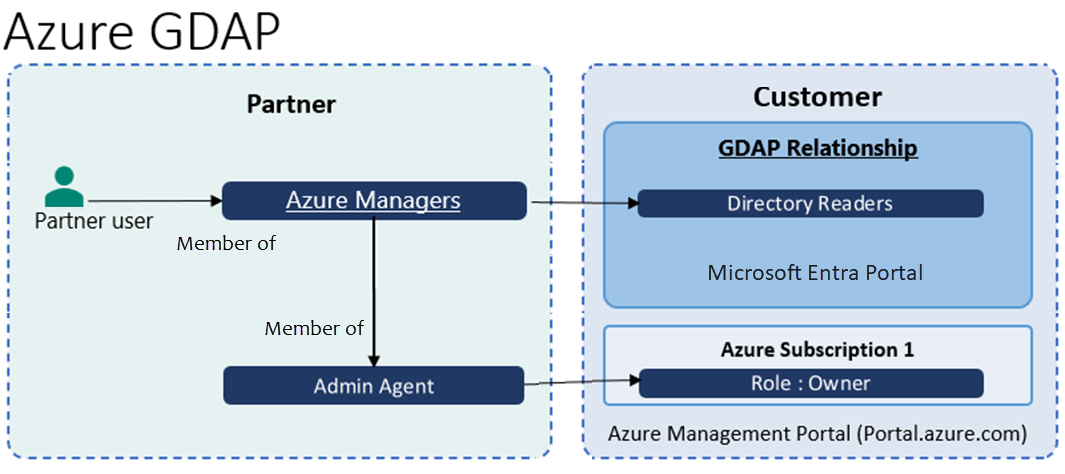
Microsoft Entra roles in scope:
- Any Microsoft Entra role such as Directory Readers (least privileged role) for accessing Azure subscription as owner
GDAP role guidance:
- Partner and customer must have Reseller relationship
- Partner must create security group (e.g Azure Managers) for managing Azure and nest it under Admin Agents for per customer access partitioning as recommended best practice.
- When partner purchases Azure plan for the customer, Azure subscription is provisioned and Admin Agents group is assigned Azure RBAC as owner on Azure subscription
- Since Azure Managers security group is member of Admin Agents group, users that are members of Azure Managers become the Azure subscription RBAC owner
- To access Azure subscription as owner for customer, any Microsoft Entra role such as Directory Readers (least privileged role) must be assigned to Azure Managers security group
Alternative Azure GDAP guidance (without using Admin Agent)
Prerequisites:
- Partner and customer have a Reseller relationship.
- Partner creates a security group for managing Azure and nested it under the HelpDeskAgents group per customer access partitioning as is a recommended best practice.
- Partner purchases an Azure plan for the customer. The Azure subscription is provisioned and the partner assigned the Admin Agents group Azure RBAC as owner on the Azure subscription but no RBAC role assignment is made for Helpdesk Agents.
Partner admin steps:
The partner admin on the subscription runs the following scripts using PowerShell to create Helpdesk FPO on the Azure subscription.
Connect to the partner tenant to get the
object IDof the HelpDeskAgents group.Connect-AzAccount -Tenant "Partner tenant" # Get Object ID of HelpDeskAgents group Get-AzADGroup -DisplayName HelpDeskAgentsEnsure that your customer has:
- The role of owner or user access administrator
- Permissions to create role assignments at the subscription level
Customer steps:
To complete the process, your customer must perform the following steps, using either PowerShell or Azure CLI.
If using PowerShell, the customer needs to update the
Az.Resourcesmodule.Update-Module Az.ResourcesConnect to the tenant in which the CSP subscription exists.
Connect-AzAccount -TenantID "<Customer tenant>"az login --tenant <Customer tenant>Connect to the subscription.
Note
This is only applicable if the user has role assignment permissions over multiple subscriptions in the tenant.
Set-AzContext -SubscriptionID <"CSP Subscription ID">az account set --subscription <CSP Subscription ID>Create the role assignment.
New-AzRoleAssignment -ObjectID "<Object ID of the HelpDeskAgents group from step above>" -RoleDefinitionName "Owner" -Scope "/subscriptions/'<CSP subscription ID>'"az role assignment create --role "Owner" --assignee-object-id <Object ID of the HelpDeskAgents group from step above> --scope "/subscriptions/<CSP Subscription Id>"
Visual Studio
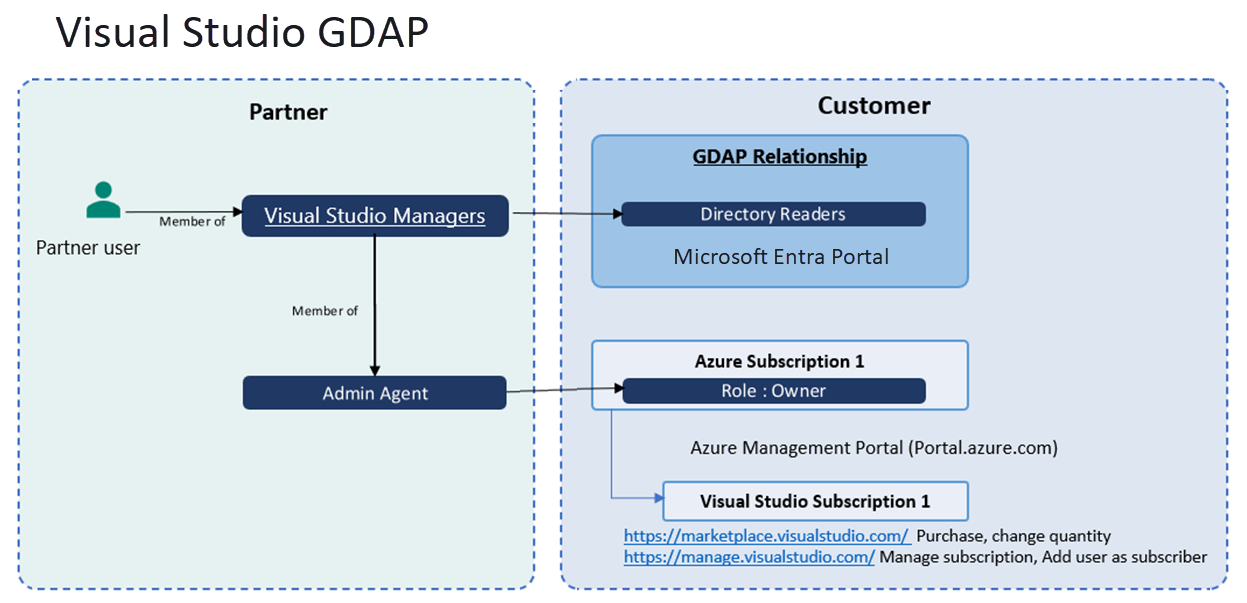
Microsoft Entra roles in scope:
- Any Microsoft Entra role such as Directory Readers (least privileged role) for accessing Azure subscription as owner
GDAP role guidance to partners:
- Prerequisites:
- Partner and customer must have a Reseller relationship
- Partner must purchase Azure subscription for the customer
- Partner must create security group (for example, Visual studio managers) for purchasing and managing Visual Studio subscriptions and nest it under Admin Agents for per customer access partitioning as recommended best practice.
- GDAP role for purchasing and managing Visual studio is same as Azure GDAP.
- Visual studio managers Security Group must be assigned any Microsoft Entra role such as Directory Readers (least privileged role) for accessing Azure subscription as owner
- Users part of Visual studio managers Security Group is able to purchase Visual studio subscription on Marketplace https://marketplace.visualstudio.com (due to nested member of Admin Agents users have access to Azure subscription)
- Users who are part of the Visual Studio managers security group can change quantity of Visual Studio subscriptions
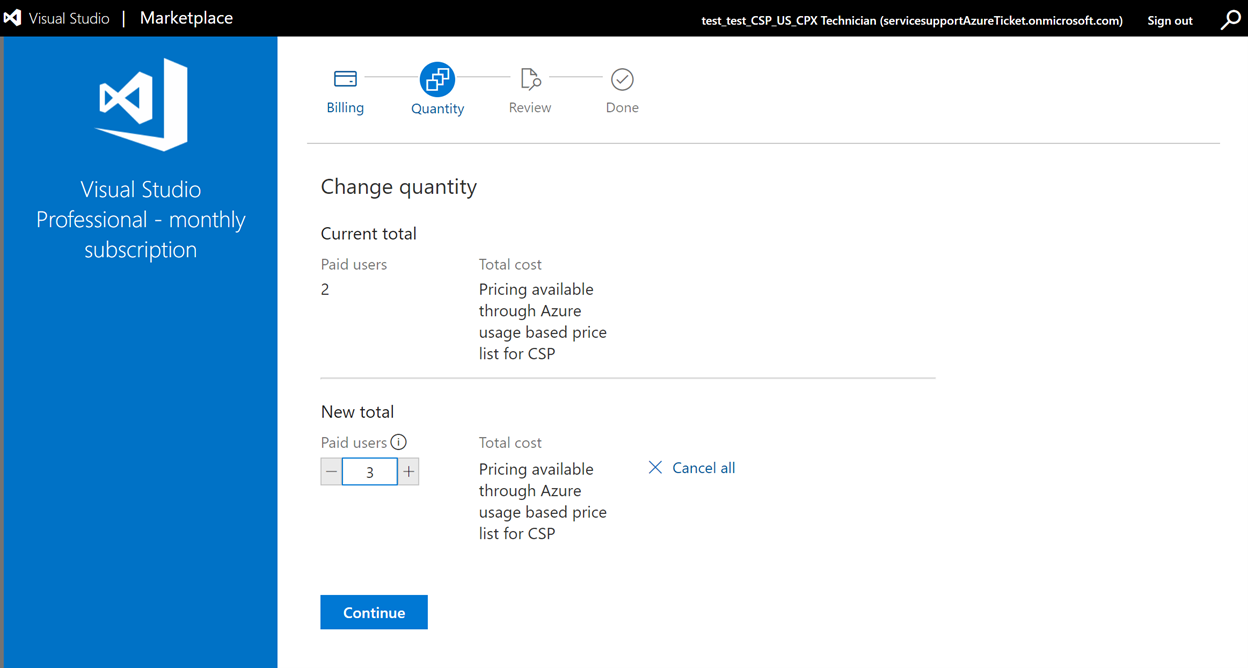
- Users who are part of the Visual Studio managers security group can cancel Visual Studio subscription (by changing quantity to zero)
- Users who are part of the Visual Studio managers security group can add subscriber to manage Visual Studio subscriptions (for example, browse customer directory and add Visual Studio role assignment as subscriber)
Visual Studio properties out of scope:
- None
Why don't I see some DAP AOBO links in GDAP Service management page?
| DAP AOBO links | Reason why it's missing in GDAP Service Management page |
|---|---|
| Microsoft 365 Planner https://portal.office.com/ |
A duplicate of the Microsoft 365 AOBO link that already exists. |
| Sway https://portal.office.com/ |
A duplicate of the Microsoft 365 AOBO link that already exists. |
| Windows 10 https://portal.office.com/ |
A duplicate of the Microsoft 365 AOBO link that already exists. |
| Cloud App Security https://portal.cloudappsecurity.com/ |
Microsoft Defender for Cloud Apps is retired. This portal merges into Microsoft Defender XDR, which supports GDAP. |
| Azure IoT Central https://apps.azureiotcentral.com/ |
Currently not supported. Out of scope for GDAP. |
| Windows Defender Advanced Threat Protection https://securitycenter.windows.com |
Windows Defender Advanced Threat Protection is retired. Partners are advised to move to Microsoft Defender XDR, which supports GDAP. |