Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
You can use certificate- or MSI-based authentication to validate your bot app instead of bot ID and secret. This authentication resolves the compliance concerns related to the use of Microsoft Entra ID and bot secret.
Prerequisites
Ensure that you have a Teams bot app deployed to Azure with the following resources:
- An Azure bot.
- An Entra ID with a secret used for bot authentication.
- A resource that hosts your bot app, such as Azure App Service, Azure Functions.
To update your bot app to use certificate-based authentication:
Create and upload certificate in Azure AD
To use a certificate for bot authentication:
Prepare a certificate and private key.
Go to Azure portal.
Select App registrations.

Select your registered app.
In the left pane, under Manage, select Certificates & secrets.
Under Certificates, select Upload certificate.
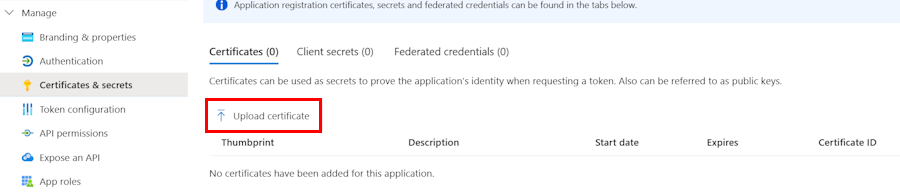
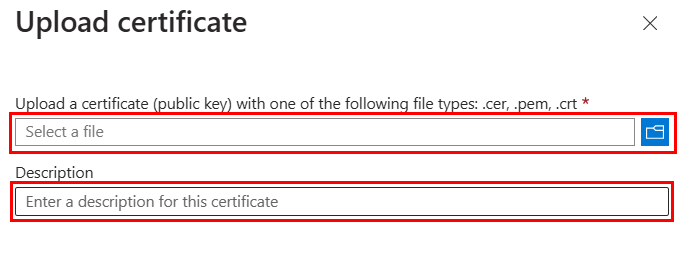
The Upload a certificate window appears.
Note
Upload a certificate (public key) with one of the following file types: .cer, .pem, .crt.
Upload the certificate you prepared.
Enter Description.
Select Add.
Update the bot app code
Follow the steps to update the bot app code:
Open your bot app project in Visual Studio or Visual Studio Code.
Update your code.
const credentialsFactory = new ConfigurationServiceClientCredentialFactory({ MicrosoftAppId: config.botId, CertificatePrivateKey: '{your private key}', CertificateThumbprint: '{your cert thumbprint}', MicrosoftAppType: "MultiTenant", }); const botFrameworkAuthentication = new ConfigurationBotFrameworkAuthentication( {}, credentialsFactory ); const adapter = new CloudAdapter(botFrameworkAuthentication);Ensure you test your bot to confirm the operation aligns with the updated authentication.
Delete bot secret
Ensure that your bot app uses the certificate for authentication before you delete the bot secret.
To delete the bot secret:
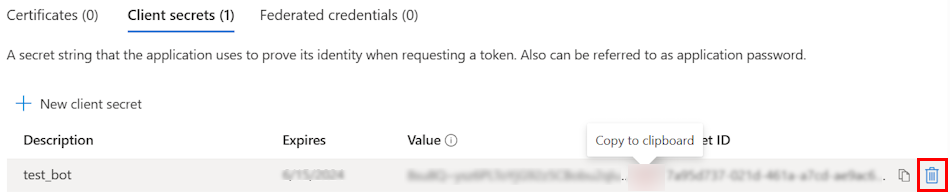
Go to Azure portal.
Select App registrations.

Select your registered app.
In the left pane, under Manage, select Certificates & secrets.
Delete the secrets from Entra.
Your bot app now uses the certificate for authentication.
See Also
Platform Docs