Key compliance and security considerations for US banking and capital markets
Introduction
Financial services institutions surpass nearly all commercial businesses in their demand for stringent security, compliance, and governance controls. The protection of data, identities, devices, and applications isn't only critical to their business, it's subject to compliance requirements and guidelines from regulatory bodies such as the U.S. Securities and Exchange Commission (SEC), the Financial Industry Regulatory Authority (FINRA), the Federal Financial Institutions Examination Council (FFIEC), and the Commodity Futures Trading Commission (CFTC). In addition, financial institutions are subject to laws such as Dodd-Frank and the Sarbanes-Oxley Act of 2002.
In today's climate of increased security vigilance, insider risk concerns and public data breaches, customers also demand high levels of security from their financial institutions in order to trust them with their personal data and banking assets.
Historically, the need for comprehensive controls directly impacted and constrained the IT systems and platforms that financial institutions use to enable collaboration internally and externally. Today, financial services employees need a modern collaboration platform that's easy to adopt and easy to use. But financial services can't trade the flexibility to collaborate between users, teams, and departments with security and compliance controls that enforce policies to protect users and IT systems from threats.
In the financial services sector, careful consideration is required for the configuration and deployment of collaboration tools and security controls, including:
- Risk assessment of common organizational collaboration and business process scenarios
- Information protection and data governance requirements
- Cybersecurity and insider threats
- Regulatory compliance requirements
- Other operational risks
Microsoft 365 is a modern workplace cloud environment that can address the contemporary challenges financial services organizations face. Secure and flexible collaboration across the enterprise is combined with controls and policy enforcement to adhere to stringent regulatory compliance frameworks. This article describes how the Microsoft 365 platform helps financial services move to a modern collaboration platform, while helping keep data and systems secure and compliant with regulations:
- Enable organizational and employee productivity by using Microsoft 365 and Microsoft Teams
- Protect modern collaboration by using Microsoft 365
- Identify sensitive data and prevent data loss
- Defend the fortress
- Govern data and comply with regulations by effectively managing records
- Establish ethical walls with information barriers
- Protect against data exfiltration and insider risk
As a Microsoft partner, Protiviti contributed to and provided material feedback to this article.
The following downloadable illustrations supplement this article. Woodgrove Bank and Contoso are used to demonstrate how capabilities described in this article can be applied to address common regulatory requirements of financial services. Feel free to adapt these illustrations for your own use.
Microsoft 365 information protection and compliance illustrations
| Item | Description |
|---|---|
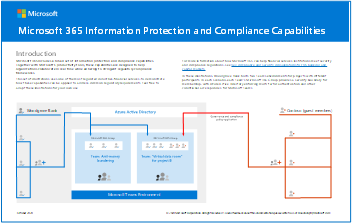 English: Download as a PDF | Download as a Visio Japanese: Download as a PDF | Download as a Visio Updated November 2020 |
Includes:
|
Empower organizational and employee productivity by using Microsoft 365 and Teams
Collaboration typically requires various forms of communication, the ability to store and access documents/data, and the ability to integrate other applications as needed. Employees in financial services typically need to collaborate and communicate with members of other departments or teams and sometimes with external entities. Therefore, using systems that create silos or make information sharing difficult is undesirable. Instead, it's preferable to use platforms and applications that enable employees to communicate, collaborate, and share information securely and according to corporate policy.
Providing employees with a modern, cloud-based collaboration platform allows them to choose and integrate tools that make them more productive and empower them to find agile ways to work. Using Teams in conjunction with security controls and information governance policies that protect the organization can help your workforce communicate and collaborate effectively.
Teams provides a collaboration hub for the organization. It helps bring people together to work productively on common initiatives and projects. Teams lets team members conduct 1:1 and multi-party chat conversations, collaborate and coauthor documents, and store and share files. Teams also facilitates online meetings through integrated enterprise voice and video. Teams can also be customized with Microsoft apps such as Microsoft Planner, Microsoft Dynamics 365, Power Apps, Power BI, and third-party line-of-business applications. Teams is designed for use by both internal team members and permitted external users who can join team channels, participate in chat conversations, access stored files, and use other applications
Every Microsoft Team is backed by a Microsoft 365 group. That group is considered the membership service for numerous Office 365 services, including Teams. Microsoft 365 groups are used to securely distinguish between "owners" and "members" and to control access to various capabilities within Teams. When coupled with appropriate governance controls and regularly administered access reviews, Teams allows only members and owners to utilize authorized channels and capabilities.
A common scenario where Teams benefits financial services is when running internal projects or programs. For example, many financial institutions, including banks, wealth management firms, credit unions, and insurance providers, are required to have anti-money laundering and other compliance programs in place. A cross-functional team comprised of IT, lines of business such as retail and wealth management, and a financial crime unit may be required to share data with each other and communicate about the program or specific investigations. Traditionally, these programs have used shared network drives, but this approach can present numerous challenges, including:
- Only one person can edit a document at a time.
- Managing security is time-consuming because adding/removing individuals typically involves IT.
- Data remains resident on shared network drives much longer than required or wanted.
Teams can provide a collaboration space to securely store sensitive client data and conduct conversations between team members where sensitive topics may be discussed. Multiple members of the team can edit or collaborate on a single document at the same time. The program owner or coordinator can be configured as the team owner and can then add and remove members as needed.
Another common scenario is to use Teams as a "virtual data room" to securely collaborate, including storing and managing documents. Team members and syndicates within investment banking, asset management, or private equity firms can securely collaborate on a deal or investment. Cross-functional teams are often involved in planning and fulfilling such deals, and the ability to securely share data and conduct conversations is a core requirement. Securely sharing related documents with external investors is also a key requirement. Teams provides a secure and fully auditable location from which to centrally store, protect, and share investment data.

Teams: Improve collaboration and reduce compliance risk
Microsoft 365 provides other common policy capabilities for Teams through its use of Microsoft 365 groups as an underlying membership service. These policies can help improve collaboration and meet compliance needs.
Microsoft 365 group naming policies help ensure that Microsoft 365 groups, and therefore teams, are named according to corporate policy. Names can be problematic if they aren't appropriate. For example, employees may not know which teams to work with or share information with if names aren't appropriately applied. Group-naming policies (including support for prefix/suffix-based policies and custom blocked words) can enforce good "hygiene" and prevent use of specific words, such as reserved words or inappropriate terminology.
Microsoft 365 group expiration policies help ensure that Microsoft 365 groups and therefore teams, aren't retained for longer periods of time than the organization wants or needs. This capability helps prevent two key information-management issues:
- Proliferation of teams that aren't necessary or used.
- Over-retention of data that's no longer required or used by the organization (except in cases of legal hold/preservation).
Administrators can specify an expiration period for Microsoft 365 groups, such as 90, 180, or 365 days. If a service that's backed by a Microsoft 365 group is inactive for the expiration period, group owners are notified. If no action is taken, the Microsoft 365 group and all its related services, including Teams, is deleted.
The over-retention of data that's stored in Teams and other group-based services can pose risks to financial services organizations. Microsoft 365 group expiration policies are a recommended way to help prevent retention of data that's no longer needed. Combined with built-in retention labels and policies, Microsoft 365 helps ensure that organizations are only retaining the data that's required to meet corporate policies and regulatory compliance obligations.
Teams: Integrate custom requirements with ease
Teams enables self-service creation of teams by default. However, many regulated organizations want to control and understand which collaboration channels are currently in use by their employees, which channels may contain sensitive data, and ownership of organizational channels. To facilitate these governance controls, Microsoft 365 lets organization disable self-service teams creation. By using business process automation tools such as Microsoft Power Apps and Power Automate, organizations can build and deploy simple forms and approval processes for employees to request creation of a new team. When approved, the team can be automatically provisioned and a link sent to the requestor. In this way, organizations can design and integrate their compliance controls and custom requirements into the team-creation process.
Acceptable digital communication channels
FINRA emphasizes that the digital communications of regulated firms meet the record-keeping requirements of Exchange Act rules 17a-3 and 17a-4, as well as FINRA Rule Series 4510. FINRA releases an annual report that contains key findings, observations, and effective practices to help organizations improve compliance and risk management. In its 2019 Report on Examination Findings and Observations, FINRA identified digital communications as a key area where firms encounter challenges complying with supervision and record-keeping requirements.
If an organization permits its employees to use a specific application, such as an app-based messaging service or collaboration platform, the firm must archive business records and supervise the activities and communications of those employees in that application. Organizations are responsible for conducting due diligence to comply with FINRA rules and securities laws, and for following up on potential violations of those rules related to employee use of such apps.
Effective practices recommended by FINRA include the following:
- Establish a comprehensive governance program for digital communication channels. Manage the organization's decisions about which digital communication channels are permitted and define compliance processes for each digital channel. Closely monitor the rapidly changing landscape of digital communication channels and keep compliance processes up to date.
- Clearly define and control permissible digital channels. Define both approved and prohibited digital channels. Block or restrict the use of prohibited digital channels, or prohibited features within digital channels, that limit the organization's ability to comply with records management and supervisory requirements.
- Provide training for digital communications. Implement mandatory training programs before giving registered representatives access to approved digital channels. Training helps clarify an organization's expectations for business and personal digital communications, and it guides staff through using permitted features of each channel in a compliant manner.
FINRA's findings and observations for Digital Communications relate directly to an organization's ability to comply with SEC Rule 17a-4 for retaining all business-related communications, FINRA rules 3110 and 3120 for supervision and review of communications, and Rule Series 4510 for record keeping. The Commodity Futures Trading Commission (CFTC) promulgates similar requirements under 17 CFR 131. These regulations are discussed in depth later in this article.
Teams, along with the comprehensive suite of Microsoft 365 security and compliance offerings, provides a corporate digital communication channel for financial services institutions to effectively conduct business and comply with regulations. The remainder of this article describes how Microsoft 365 built-in capabilities for records management, information protection, information barriers, and supervisory control gives Teams a robust toolset to help meet these regulatory obligations.
Protect modern collaboration with Microsoft 365
Secure user identities and control access
Protecting access to customer information, financial documents, and applications begins with strongly securing user identities. This requires a secure platform for the enterprise to store and manage identities, providing a trusted means of authentication, and dynamically controlling access to those applications.
As employees work, they may move from application to application or between multiple locations and devices. Access to data must be authenticated at each step along the way. The authentication process has to support a strong protocol and multiple factors of authentication (such as one-time SMS pass code, authenticator app, and certificate) to ensure that identities aren't compromised. Enforcing risk-based access policies is critical to protecting financial data and applications from insider threats, inadvertent data leaks, and data exfiltration.
Microsoft 365 provides a secure identity platform in Microsoft Entra ID, where identities are centrally stored and securely managed. Microsoft Entra ID, along with a host of related Microsoft 365 security services, forms the basis for providing employees with the access they need to work securely while also protecting the organization from threats.
Microsoft Entra multifactor authentication (MFA) is built into the platform and provides an additional proof of authentication to help confirm user identity when they access sensitive financial data and applications. Azure MFA requires at least two forms of authentication, such as a password plus a known mobile device. It supports several second-factor authentication options, including:
- The Microsoft Authenticator app
- A one-time passcode delivered via SMS
- A phone call where a user must enter a PIN
If password is somehow compromised, a potential hacker would still need the user's phone to gain access to organizational data. In addition, Microsoft 365 uses Modern Authentication as a key protocol, which brings the same strong and rich authentication experience from web browsers to the collaboration tools that employees use day to day, including Microsoft Outlook and the other Microsoft Office applications.
Passwordless
Passwords are the weakest link in a security chain. They can be a single point of failure if there's no additional verification. Microsoft supports a broad range of authentication options to fit the needs of financial institutions.
Passwordless methods help make MFA more convenient for users. While not all MFA is passwordless, passwordless technologies employ multifactor authentication. Microsoft, Google, and other industry leaders have developed standards to enable a simpler, stronger authentication experience across the web and mobile devices in a group called Fast IDentity Online (FIDO). The recently developed FIDO2 standard enables users to authenticate easily and securely without requiring a password to eliminate phishing.
Microsoft MFA methods that are passwordless include:
- Microsoft Authenticator: For flexibility, convenience, and cost, we recommend using the Microsoft Authenticator mobile app. Microsoft Authenticator supports biometrics, push notifications, and one-time passcodes for any Microsoft Entra connected app. It's available from the Apple and Android app stores.
- Windows Hello: For a built-in experience on the PC, we recommend using Windows Hello. It uses biometric information (such as face or fingerprint) to sign in automatically.
- FIDO2 Security keys are now available from several Microsoft partners: Yubico, Feitian Technologies, and HID Global in a USB, NFC-enabled badge or biometric key.
Microsoft Entra Conditional Access provides a robust solution for automating access control decisions and enforcing organizational policies to protect company assets. A classic example is when a financial planner wants to access an application that has sensitive customer data. They're automatically required to perform a multifactor authentication to specifically access that application, and access must be from a corporate-managed device. Azure Conditional Access brings together signals about a user's access request, such as properties about the user, the device, location, and network, and the application that the user is trying to access. It dynamically evaluates attempts to access the application against configured policies. If user or device risk is elevated, or other conditions aren't met, Microsoft Entra ID can automatically enforce policies such as requiring MFA, requiring a secure password reset, or restricting or blocking access. This helps ensure that sensitive organizational assets are protected in dynamically changing environments.
Microsoft Entra ID, and the related Microsoft 365 security services, provide the foundation on which a modern cloud collaboration platform can be rolled out to financial institutions so that access to data and applications can be secured, and regulator compliance obligations can be met. These tools provide the following key capabilities:
- Centrally store and securely manage user identities.
- Use a strong authentication protocol, including multifactor authentication, to authenticate users on access requests and provide a consistent and robust authentication experience across all applications.
- Dynamically validate policies on all access requests, incorporating multiple signals into the policy decision-making process, including identity, user/group membership, application, device, network, location, and real-time risk score.
- Validate granular policies based on user behavior and file properties and dynamically enforce additional security measures when required.
- Identify "shadow IT" in the organization, and allow InfoSec teams to sanction or block cloud applications.
- Monitor and control access to Microsoft and non-Microsoft cloud applications.
- Proactively protect against email phishing and ransomware attacks.
Microsoft Entra ID Protection
While Conditional Access protects resources from suspicious requests, Identity Protection goes further by providing ongoing risk detection and remediation of suspicious user accounts. Identity Protection keeps you informed of suspicious user and sign-in behavior in your environment around the clock. Its automatic response proactively prevents compromised identities from being abused.
Identity Protection is a tool that allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks.
- Investigate risks by using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
Identity Protection uses knowledge that Microsoft has acquired from its position in organizations with Microsoft Entra ID, in the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users. Microsoft analyzes 65 trillion signals per day to identify and protect customers from threats. The signals generated by and fed to Identity Protection can be further fed into tools like Conditional Access to make access decisions. They can also be fed back to a security information and event management (SIEM) tool for further investigation based on your organization's enforced policies.
Identity Protection helps organizations automatically protect against identity compromise by taking advantage of cloud intelligence powered by advanced detection based on heuristics, user and entity behavior analytics (UEBA), and machine learning (ML) across the Microsoft ecosystem.

Identify sensitive data and prevent data loss
Microsoft 365 allows all organizations to identify sensitive data within the organization through a combination of powerful capabilities, including:
- Microsoft Purview Information Protection for both user-based classification and automated classification of sensitive data.
- Microsoft Purview Data Loss Prevention (DLP) for automated identification of sensitive data using sensitive data types (in other words, regular expressions) and keywords and policy enforcement.
Microsoft Purview Information Protection enables organizations to classify documents and emails intelligently by using sensitivity labels. Sensitivity labels can be applied manually by users to documents in Microsoft Office applications and to emails in Outlook. The labels can automatically apply document markings, protection through encryption, and rights-management enforcement. Sensitivity labels can also be applied automatically by configuring policies that use keywords and sensitive data types (such as credit card numbers, social insurance numbers, and identity numbers) to automatically find and classify sensitive data.
In addition, Microsoft provides "trainable classifiers" that use machine learning models to identify sensitive data based on the content, as opposed to simply through pattern matching or by the elements within the content. A classifier learns how to identify a type of content by looking at numerous examples of the content to be classified. Training a classifier begins by giving it examples of content in a particular category. After it learns from those examples, the model is tested by giving it a mix of matching and non-matching examples. The classifier predicts whether a given example falls into the category or not. A person then confirms the results, sorting the positives, negatives, false positives, and false negatives to help increase the accuracy of the classifier's predictions. When the trained classifier is published, it processes content in Microsoft SharePoint Online, Exchange Online, and OneDrive for Business and automatically classifies the content.
Applying sensitivity labels to documents and emails embeds metadata that identifies the chosen sensitivity within the object. The sensitivity then travels with the data. So even if a labeled document is stored on a user's desktop or within an on-premises system, it's still protected. This functionality enables other Microsoft 365 solutions, such as Microsoft Defender for Cloud Apps or network edge devices, to identify sensitive data and automatically enforce security controls. Sensitivity labels have the added benefit of educating employees about which data within an organization is considered sensitive and how to handle that data when they receive it.
Microsoft Purview Data Loss Prevention (DLP) automatically identifies documents, emails, and conversations that contain sensitive data by scanning them for sensitive data and then enforcing policy on those objects. Policies are enforced on documents in SharePoint and OneDrive for Business. They're also enforced when users send email, and in Teams chats and channel conversations. Policies can be configured to look for keywords, sensitive data types, retention labels, and whether data is shared within the organization or externally. Controls are provided to help organizations fine-tune DLP policies to reduce false positives. When sensitive data is found, customizable policy tips can be displayed to users within Microsoft 365 applications to inform them that their content contains sensitive data and then propose corrective actions. Policies can also prevent users from accessing documents, sharing documents, or sending emails that contain certain types of sensitive data. Microsoft 365 supports more than 100 built-in sensitive data types. Organizations can configure custom sensitive data types to meet their policies.
Rolling out Microsoft Purview Information Protection and DLP policies to organizations requires careful planning and a user education program so that employees understand the organization's data classification schema and which types of data are considered sensitive. Providing employees with tools and educational programs that help them identify sensitive data and understand how to handle it makes them part of the solution for mitigating information security risks.
The signals generated by and fed to Identity Protection can also be fed into tools like Conditional Access to make access decisions or to a security information and event management (SIEM) tool for investigation based on an organization's enforced policies.
Identity Protection helps organizations automatically protect against identity compromise by taking advantage of cloud intelligence powered by advanced detections based on heuristics, user and entity behavior analytics, and machine learning across the Microsoft ecosystem.

Defend the fortress
Microsoft recently launched the Microsoft Defender XDR solution, which is designed to secure the modern organization from the evolving threat landscape. By leveraging the Intelligent Security Graph, the Threat Protection solution offers comprehensive, integrated security against multiple attack vectors.
The Intelligent Security Graph
Security services from Microsoft 365 are powered by the Intelligent Security Graph. To combat cyberthreats, the Intelligent Security Graph uses advanced analytics to link threat intelligence and security signals from Microsoft and its partners. Microsoft operates global services at a massive scale, gathering trillions of security signals that power protection layers across the stack. Machine learning models assess this intelligence, and the signal and threat insights are widely shared across our products and services. This enables us to detect and respond to threats quickly and bring actionable alerts and information to customers for remediation. Our machine learning models are continuously trained and updated with new insights, helping us build more-secure products and provide more proactive security.
Microsoft Defender for Office 365 provides an integrated Microsoft 365 service that protects organizations from malicious links and malware delivered through email and Office documents. One of the most common attack vectors that affects users today is email phishing attacks. These attacks can be targeted at specific users and can be very convincing, with some call to action that prompts the user to select a malicious link or open an attachment that contains malware. Once a computer is infected, the attacker can either steal the user's credentials and move laterally across the organization or exfiltrate emails and data to look for sensitive information. Defender for Office 365 supports safe attachments and safe links by evaluating documents and links at click-time for potentially malicious intent and blocks access. Email attachments are opened in a protected sandbox before they're delivered to a user's mailbox. It also evaluates links in Office documents for malicious URLs. Defender for Office 365 also protects links and files in SharePoint Online, OneDrive for Business, and Teams. If a malicious file is detected, Defender for Office 365 automatically locks that file to reduce potential damage.
Microsoft Defender for Endpoint is a unified endpoint security platform for preventative protection, post-breach detection, and automated investigation and response. Defender for Endpoint provides built-in capabilities for discovery and protection of sensitive data on enterprise endpoints.
Microsoft Defender for Cloud Apps enables organizations to enforce policies at a granular level and to detect behavioral anomalies based on individual user profiles that are automatically defined by using machine learning. Defender for Cloud Apps policies can build on Azure Conditional Access policies to protect sensitive company assets by evaluating additional signals related to user behavior and properties of the documents that are accessed. Over time, Defender for Cloud Apps learns what's typical behavior for each employee with regard to the data they access and the applications they use. Based on learned behavior patterns, policies can then automatically enforce security controls if an employee acts outside of that behavioral profile. For example, if an employee typically accesses an accounting application from 9 AM to 5 PM Monday through Friday but suddenly starts to access that application heavily on a Sunday evening, Defender for Cloud Apps can dynamically enforce policies to require the user to reauthenticate. This helps ensure that the user's credentials haven't been compromised. Defender for Cloud Apps can also help identify "shadow IT" in the organization, which helps information security teams ensure that employees are using sanctioned tools when they work with sensitive data. Finally, Defender for Cloud Apps can protect sensitive data anywhere in the Cloud, even outside the Microsoft 365 platform. It allows organizations to sanction (or unsanction) specific external Cloud apps, controlling access and monitoring usage.
Microsoft Defender for Identity is a cloud-based security solution that uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. AATP enables SecOp analysts and security professionals detect advanced attacks in hybrid environments to:
- Monitor users, entity behavior, and activities by using learning-based analytics.
- Protect user identities and credentials stored in Active Directory.
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain.
- Provide clear incident information on a simple timeline for fast triage.

Govern data and manage records
Financial institutions must retain their records and information according to their regulatory, legal, and business obligations as represented within their corporate retention schedule. For example, the SEC mandates retention periods of three to six years, based on record type, with immediate accessibility for the first two years. Organizations face legal and regulatory compliance risks if data is under-retained (discarded too early), and now also manage regulations that mandate disposal when information is no longer required. Effective records management strategies emphasize a practical and consistent approach so that information is disposed of appropriately while minimizing cost and risk to the organization.
In addition, regulatory mandates from the New York State Department of Financial Services require covered entities to maintain policies and procedures for disposal of nonpublic information. 23 NYCRR 500, Section 500.13, Limitations on Data Retention requires that "As part of its cybersecurity program, each Covered Entity shall include policies and procedures for the secure disposal on a periodic basis of any Nonpublic Information identified in section 500.01(g)(2)-(3) of this Part that is no longer necessary for business operations or for other legitimate business purposes of the Covered Entity, except where such information is otherwise required to be retained by law or regulation."
Financial institutions manage vast amounts of data. And some retention periods are triggered by events, such as a contract expiring or an employee leaving the organization. In this atmosphere, it can be challenging to apply record retention policies. Approaches to assigning record retention periods accurately across organizational documents can vary. Some apply retention policies broadly or use autoclassification and machine learning techniques. Others identify an approach that requires a more granular process that assigns retention periods uniquely to individual documents.
Microsoft 365 provides flexible capabilities to define retention labels and policies to intelligently implement records-management requirements. A record manager defines a retention label, which represents a "record type" in a traditional retention schedule. The retention label contains settings that define these details:
- How long a record is retained
- What occurs when the retention period expires (delete the document, start a disposition review, or take no action)
- What triggers the retention period to start (created date, last modified date, labeled date, or an event) and marks the document or email as a record (meaning it can't be edited or deleted)
The retention labels are then published to SharePoint or OneDrive sites, Exchange mailboxes, and Microsoft 365 groups. Users can apply the retention labels manually to documents and emails. Record managers can use intelligence to automatically apply the labels. Intelligent capabilities can be based on ninety-plus built-in sensitive information types (such as ABA outing number, US bank account number, or US Social Security Number). They're also customizable based on keywords or sensitive data found in documents or emails, such as credit card numbers or other personally identifiable information or based on SharePoint metadata. For data that's not easily identified through manual or automated pattern matching, trainable classifiers can be used to classify documents intelligently based on machine learning techniques.
The Securities and Exchange Commission (SEC) requires broker-dealers and other regulated financial institutions to retain all business-related communications. These requirements apply to many types of communications and data, including emails, documents, instant messages, faxes, and more. SEC rule 17a-4 defines the criteria that these organizations must meet to store records in an electronic data storage system. In 2003, the SEC issued a release that clarified these requirements. It included the following criteria:
- Data preserved by an electronic storage system must be non-rewriteable and non-erasable. This is referred to as a WORM requirement (write once, read many).
- The storage system must be able to store data beyond the retention period required by the rule, in case of a subpoena or other legal order.
- An organization wouldn't violate the requirement in paragraph (f)(2)(ii)(A) of the rule if it used an electronic storage system that prevents the overwriting, erasing, or otherwise altering of a record during its required retention period through the use of integrated hardware and software control codes.
- Electronic storage systems that merely "mitigate" the risk that a record will be overwritten or erased, for example by relying on access control, don't meet the requirements of the rule.
To help financial institutions meet the requirements of SEC rule 17a-4, Microsoft 365 provides a combination of capabilities related to how data is retained, policies are configured, and data is stored within the service. These include:
Preservation of data (Rule 17a-4(a), (b)(4)) – Retention labels and policies are flexible to meet organizational needs and may be automatically or manually applied to different types of data, documents, and information. A wide variety of data types and communications are supported, including documents in SharePoint and OneDrive for Business, data within Exchange Online mailboxes, and data in Teams.
Non-rewriteable, non-erasable format (Rule 17a-4(f)(2)(ii)(A)) – Preservation Lock capability for retention policies allows records managers and administrators to configure retention policies to be restrictive, such that they can no longer be modified. This prohibits anyone from removing, disabling, or modifying the retention policy in any way. This means that once Preservation Lock is enabled, it can't be disabled, and there's no method by which any data to which the retention policy has been applied can be overwritten, modified, or deleted during the retention period. In addition, the retention period can't be shortened. However, the retention period can be lengthened, when there's a legal requirement to continue retention of data.
When a Preservation Lock is applied to a retention policy, the following actions are restricted:- The retention period of the policy can only be increased. It can't be shortened.
- Users can be added to the policy, but existing users configured in the policy can't be removed.
- The retention policy can't be deleted by any administrator within the organization.
Preservation Lock helps ensure that no user, not even administrators with the highest levels of privileged access, can change the settings, modify, overwrite or delete the data that has been stored, bringing archiving in Microsoft 365 in line with the guidance provided in the SEC 2003 Release.
Quality, accuracy, and verification of storage/serialization and indexing of data (Rule 17a-4(f)(2) (ii)(B) and (C)) – Office 365 workloads each contain capabilities for automatically verifying the quality and accuracy of the process for recording data on storage media. In addition, data is stored by utilizing metadata and timestamps to ensure sufficient indexing to allow for effective searching and retrieval of data.
Separate storage for duplicate copies (Rule 17a-4(f)(3(iii)) – The Office 365 cloud service stores duplicate copies of data as a core aspect of its high availability. This is accomplished by implementing redundancy at all levels of the service, including at the physical level on all servers, at the server level within the data center, and at the service level for geographically dispersed data centers.
Downloadable and accessible data (Rule 17a-4(f)(2)(ii)(D)) – Office 365 generally permits data that's been labeled for retention to be searched for, accessed, and downloaded in place. And it allows data in Exchange Online Archives to be searchable by using built-in eDiscovery features. Data can then be downloaded as needed in standard formats, including EDRML and PST.
Audit requirements (Rule 17a-4(f)(3)(v)) – Office 365 provides audit logging for every administrative and user action that modifies data objects, configures or modifies retention policies, performs eDiscovery searches, or modifies access permissions. Office 365 maintains a comprehensive audit trail, including data about who performed an action, when it was performed, details about the action, and the commands that were performed. The audit log can then be output and included as part of formal audit processes as required.
Finally, Rule 17a-4 requires organizations to retain records for many types of transactions so that they're immediately accessible for two years. Records must be further retained for three to six years with non-immediate access. Duplicate records must also be kept for the same period at an off-site location. Microsoft 365 records management capabilities enable records to be retained such that they can't be modified or deleted but can be easily accessed for a time period that's controlled by the record manager. These periods can span days, months, or years, depending on the organization's regulatory-compliance obligations.
Upon request, Microsoft will provide an attestation letter of compliance with SEC 17a-4 if required by an organization.
In addition, these capabilities also help Microsoft 365 meet storage requirements for CFTC Rule 1.31(c)-(d) from the U.S. Commodity Futures Trading Commission and FINRA Rule Series 4510 from the Financial Industry Regulatory Authority. Collectively, these rules represent the most-prescriptive guidance globally for financial institutions to retain records.
Additional details about how Microsoft 365 complies with SEC rule 17a-4 and other regulations is available with the Office 365 - Cohasset Assessment - SEC Rule 17a-4(f) - Immutable Storage for SharePoint, OneDrive, Exchange, Teams, and Viva Engage (2022) download document.
Establish ethical walls with information barriers
Financial institutions can be subject to regulations that prevent employees in certain roles from exchanging information or collaborating with other roles. For example, FINRA has published rules 2241(b)(2)(G), 2242(b)(2) (D), (b)(2)(H)(ii) and (b)(2)(H)(iii) that require members to:
"(G) establish information barriers or other institutional safeguards reasonably designed to ensure that research analysts are insulated from the review, pressure, or oversight by persons engaged in investment banking services activities or other persons, including sales and trading personnel, who might be biased in their judgment or supervision;" and "(H) establish information barriers or other institutional safeguards reasonably designed to ensure that debt research analysts are insulated from the review, pressure, or oversight by persons engaged in: (i) investment banking services; (ii) principal trading or sales and trading activities; and (iii) other persons who might be biased in their judgment or supervision;"
Ultimately, these rules require organizations to establish policies and implement information barriers between roles involved in banking services, sales, or trading from exchanging information and communications with analysts.
Information barriers provides the ability to establish ethical walls within your Office 365 environment, allowing compliance administrators or other authorized administrators to define policies that allow or prevent communications between groups of users in Teams. Information barriers perform checks on specific actions to prevent unauthorized communication. Information barriers can also restrict communication in scenarios where internal teams are working on mergers/acquisitions or sensitive deals, or working with sensitive internal information that must be heavily restricted.
Information barriers support conversations and files in Teams. They can prevent the following types of communications-related actions to help comply with FINRA regulations:
- Search for a user
- Add a member to a team, or continue to participate with another member in a team
- Start or continue a chat session
- Start or continue a group chat
- Invite someone to join a meeting
- Share a screen
- Place a call
Implement supervisory control
Financial institutions are typically required to establish and maintain a supervisory function within their organizations to monitor the activities of employees and to help it achieve compliance with applicable securities laws. Specifically, FINRA has established these supervision requirements:
FINRA Rule 3110 (Supervision) requires firms to have written supervisory procedures (WSPs) to supervise activities of its employees and the types of businesses in which it engages. In addition to other requirements, procedures must include:
- Supervision of supervisory personnel
- Review of a firm's investment banking, securities business, internal communications, and internal investigations
- Review of transactions for insider trading
- Review of correspondence and complaints
Procedures must describe the individuals responsible for reviews, supervisory activity each person will perform, review frequency, and the types of documentation or communications under review.
FINRA Rule 3120 (Supervisory Control System) requires firms to have a system of supervisory control policies and procedures (SCPs) that validates their written supervisory procedures as defined by Rule 3110. Firms are required not only to have WSPs but also to have policies that test these procedures annually to validate their ability to ensure compliance with applicable securities laws and regulations. Risk-based methodologies and sampling may be used to define the scope of testing. Among other requirements, this rule requires firms to provide an annual report to senior management that includes a summary of test results and any significant exceptions or amended procedures in response to test results.

Communication compliance
Microsoft Purview Communication Compliance is a compliance solution that helps minimize communication risks by helping you detect, investigate, and act on inappropriate messages in your organization. Pre-defined and custom policies allow you to scan internal and external communications for policy matches so they can be examined by designated reviewers. Reviewers can investigate scanned email, Microsoft Teams, Viva Engage, or third-party communications in your organization and take appropriate actions to make sure they're compliant with your organization's message standards.
Communication compliance provides reports that enable policy review activities to be audited based on the policy and the reviewer. Reports are available to validate that policies are working as defined by an organization's written policies. They can also be used to identify communications that require review and those that aren't compliant with corporate policy. Finally, all activities related to configuring policies and reviewing communications are audited in the Office 365 unified audit log. As a result, communication compliance also helps financial institutions to comply with FINRA Rule 3120.
In addition to complying with FINRA rules, communication compliance allows organizations to detect and act on communications that may be impacted by other legal requirements, corporate policies, and ethical standards. Communication compliance provides built-in threat, harassment, and profanity classifiers that help reduce false positives when reviewing communications, saving reviewers time during the investigation and remediation process. It also allows organizations to reduce risk by detecting communications when they undergo sensitive organizational changes, such as mergers and acquisitions or leadership changes.

Protect against data exfiltration and insider risk
A common threat to enterprises is data exfiltration, or the act of extracting data from an organization. This risk can be a significant concern for financial institutions due to the sensitive nature of the information that can be accessed day to day. With the increasing number of communications channels available and the proliferation of tools for moving data, advanced capabilities are typically required to mitigate the risks of data leaks, policy violations, and insider risk.
Insider risk management
Enabling employees with online collaboration tools that can be accessed anywhere inherently brings risk to the organization. Employees may inadvertently or maliciously leak data to attackers or competitors. Alternatively, they may exfiltrate data for personal use or take data with them to a future employer. These scenarios present serious risks to financial services institutions from both security and compliance standpoints. Identifying these risks when they occur and quickly mitigating them requires both intelligent tools for data collection and collaboration across departments such as legal, human resources, and information security.
Microsoft Purview Insider Risk Management is a compliance solution that helps minimize internal risks by enabling you to detect, investigate, and act on malicious and inadvertent activities in your organization. Insider risk policies allow you to define the types of risks to identify and detect in your organization, including acting on cases and escalating cases to Microsoft eDiscovery (Premium) if needed. Risk analysts in your organization can quickly take appropriate actions to make sure users are compliant with your organization's compliance standards.
For example, insider risk management can correlate signals from a user's devices, such as copying files to a USB drive or emailing a personal email account, with activities from online services such as Office 365 email, SharePoint Online, Microsoft Teams, or OneDrive for Business, to identify data exfiltration patterns. It can also correlate these activities with employees leaving an organization, which is a common data exfiltration pattern. It can detect multiple potentially risky activities and behavior over time. When common patterns emerge, it can raise alerts and help investigators focus on key activities to verify a policy violation with a high degree of confidence. Insider risk management can pseudo-anonymize data from investigators to help meet data privacy regulations, while still surfacing key activities that help them perform investigations efficiently. It allows investigators to package and securely send key activity data to the HR and legal departments, following common escalation workflows for raising cases for remediation action.
Insider risk management significantly increases capabilities of organizations to detect and investigate insider risks while allowing organizations to still meet data privacy regulations and follow established escalation paths when cases require higher-level action.

Tenant restrictions
Organizations that deal with sensitive data and put a strict emphasis on security typically want to control the online resources that users can access. At the same time, they want to enable secure collaboration through online services such as Office 365. As a result, controlling the Office 365 environments that users can access becomes a challenge because noncorporate Office 365 environments can be used to exfiltrate data from corporate devices either maliciously or inadvertently. Traditionally, organizations restrict the domains or IP addresses that users can access from corporate devices. But this doesn't work in a cloud-first world, where users need to legitimately access Office 365 services.
Microsoft 365 provides the tenant restrictions the capability to address this challenge. Tenant restrictions can be configured to restrict employee access to external Office 365 enterprise tenants using rogue identities (identities that aren't part of your corporate directory). Today, tenant restrictions apply across the tenant, allowing access to only those tenants that appear on the list that you configure. Microsoft is continuing to develop this solution to increase granularity of control and enhance the protections it provides.

Conclusion
Microsoft 365 and Teams provide an integrated and comprehensive solution for financial services companies, enabling simple yet powerful cloud-based collaboration and communications capabilities across the enterprise. By using security and compliance technologies from Microsoft 365, institutions can operate in a more secure and compliant manner with robust security controls to protect data, identities, devices, and applications from various operational risks, including cybersecurity and insider risks. Microsoft 365 provides a fundamentally secure platform on which financial services organizations can achieve more while protecting their company, employees, and customers.