Academic year transition - user identities
Management of user provisioning and deprovisioning with adjustments to Microsoft Entra ID and on-premises or third-party identity solutions for the closing and new school year.
Microsoft Entra cleanup
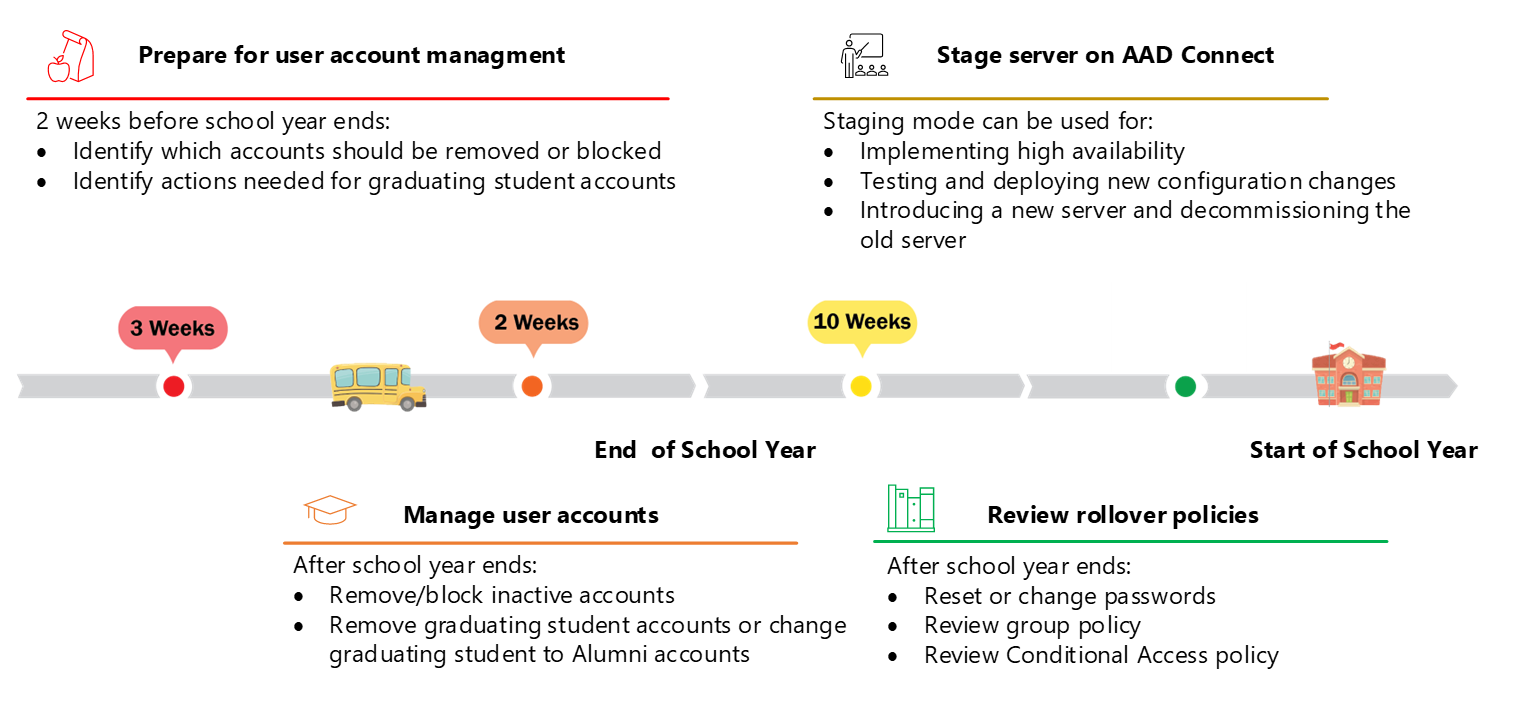
After the school year has ended, Microsoft recommends cleaning up inactive and graduating accounts in order to prepare for the new school year, keeping in mind your specific user data retention requirements. Performing a cleanup of inactive accounts in Microsoft Entra ID typically involves the following steps:
- Decide on detailed information requirements
- Identify the accounts to be removed.
- Review and manage list of potential accounts.
- Remove accounts
- Validate
For information on data lifecycle management, see Retention Capabilities.
Deciding on detailed information requirements
Several decisions need to be made to identify what defines an inactive account and which accounts need to be cleaned up in Microsoft Entra ID. Use guidelines from previous years to base your decisions. For example:
- What defines an inactive account? (for example, a user hasn't logged in during the past 18 months)
- How do we handle graduating student accounts?
- What organizational retention guidelines do we need to follow?
Graduating student accounts
Graduating students in higher education are eligible for an alumni SKU that allows them to continue to have an Exchange Online Mailbox post graduation. Organizations typically process the accounts in one of two ways:
- Change the existing user account in Office 365 from the old SKU to the alumni SKU
- Remove or disable the old user account and then create a new user account in a tenant that is designated for alumni users. This method has three main benefits:
- It logically separates alumni members from the existing school communications
- It creates a logical barrier for interactions and visibility of active students
- It frees up storage. All the content associated with the accounts from when they were active students can be removed from the tenant. Then, the content no longer counts against the tenant's storage quota. To free up the storage, you can delete and recreate (or delete) the OneDrive
Identifying accounts to be cleaned up
Inactive accounts are user accounts that aren't required anymore by members of your organization to gain access to your resources. One key identifier for inactive accounts is that they haven't been used for a while to sign-in to your environment. Because inactive accounts are tied to the sign-in activity, you can use the timestamp of the last sign-in that was successful to detect them.
You can detect inactive accounts by evaluating the lastSignInDateTime property that is exposed by the signInActivity resource type of the Microsoft Graph API. Viewing the sign-in activity details through the Graph API requires a Microsoft Entra ID P1 or P2 license. Using this property, you can implement a solution for the following scenarios:
- Last sign-in date and time for all users: In this scenario, you need to generate a report of the last sign-in date of all users. You request a list of all users, and the last lastSignInDateTime for each respective user:
https://graph.microsoft.com/v1.0/users?$select=displayName,signInActivity - Users by name: In this scenario, you search for a specific user by name, which enables you to evaluate the lastSignInDateTime:
https://graph.microsoft.com/beta/users?$filter=startswith(displayName,'markvi')&$select=displayName,signInActivity - Users by date: In this scenario, you request a list of users with a lastSignInDateTime before a specified date:
https://graph.microsoft.com/beta/users?filter=signInActivity/lastSignInDateTimele2019-06-01T00:00:00Z
For more information, see How to manage inactive user accounts in Microsoft Entra ID.
Reviewing list of collected accounts
Review the list of collected accounts:
- Are all accounts that are listed going to be deleted?
- Do you have on-premises sync to AD via AD Connect?
- Do you have a third-party on-premises connection sync?
- Do you have regulatory or compliance considerations on data in question?
- (HED) - Are these accounts considered 'Alumni' accounts?
Removing accounts
After you have reviewed the list of accounts and are ready to remove them, you have a few options for deleting them:
Disabling logins or removing other students
Sometimes, instead of deleting accounts, you might need to disable or block access to them. For instance, your organization might have specific policies on retaining historical records or compliance.
When you block access to a Microsoft 365 account, you prevent anyone from using the account to sign in and access the services and data in your Microsoft 365 organization. You can use PowerShell to block access to individual or multiple user accounts.
If your users are synchronized with Microsoft Entra ID from a local Active Directory, identify and clean up the users so that they aren't recreated on the next synchronization run from Microsoft Entra Connect. We recommend that you regularly check for and remove inactive user accounts in Active Directory.
Validate
After the accounts have been removed, validate the user accounts are removed by checking Microsoft Entra ID, on-premises sync options, and audit reports.
- Validate user accounts are removed
- Confirm on-premises sync options
Retention Capabilities
Sometimes, you need to retain user data for a specified period, either for archival purposes, or potentially due to organizational or industry regulations. The following documentation contains details on retention within Microsoft 365 using both policies and labels:
- Get started with data lifecycle management
- Learn about retention policies & labels to automatically retain or delete content
- Start retention when an event occurs
Rollover Review
Bulk Password reset or change
As the Microsoft 365 admin, you can let people use the self-service password reset tool so you don't have to reset passwords for them. Less work for you!
The self-service password reset for cloud users is included with any Microsoft 365 business, education, or nonprofit paid plan. It doesn't work with Microsoft 365 trial.
However, if you're using an on-premises Active Directory, the self-service password reset requires a paid subscription to Microsoft Entra ID P1 or P2.
- Let users reset their own passwords
- Reset passwords
- Force password change for all users in Office 365
Group policy review
With the increase in usage of Microsoft 365 groups and Microsoft Teams, administrators and users need a way to clean up unused groups and teams. A Microsoft 365 groups expiration policy (available as a premium feature) can help remove inactive groups from the system and make things cleaner. An admin can also manually review the activity details from the Microsoft 365 Admin Center Usage Reports to identify sites and mailboxes that haven't been recently active.
When a group expires, the group and its associated services (the mailbox, Planner, SharePoint site, team, etc.) are "soft-deleted," which means it can still be recovered for up to 30 days. For more information, see:
Conditional Access Policy Review
If you're planning or performing a new deployment, review the Conditional Access insights and reporting workbook to understand the impact of Conditional Access policies in your organization over time.
Microsoft Entra Connect server (Staging)
If you're planning or performing a new deployment, Microsoft Entra Connect staging mode can be used to test and deploy new configuration changes or to introduce a new server and decommission the old.
For more information
The following resources provide additional information about user accounts:
- What is identity lifecycle management with Microsoft Entra ID?
- How to manage inactive user accounts in Microsoft Entra ID (Cloud only accounts)
- Block Microsoft 365 user accounts with PowerShell - Microsoft 365 Enterprise
- Delete Microsoft 365 user accounts with PowerShell - Microsoft 365 Enterprise
- Regularly check for and remove inactive user accounts in Active Directory
- Multi-tenant architecture for large institutions - Microsoft 365 Education
- Microsoft Entra security defaults | Microsoft Docs
Next steps
Next, let's look at procures for devices.