Adding Security Authorization <add>
Overview
The <add> element of the <authorization> collection defines an authorization rule that will either allow or deny access to specified users, groups, anonymous users, or all users.
The accessType attribute specifies either of two types of authorization rules:
- Allow rules let you define the user accounts or user groups that can access a site, an application, or all the sites on a server.
- Deny rules let you define the user accounts or user groups that cannot access a site, an application, or all the sites on a server.
Authorization rules can further be targeted for a list of HTTP verbs and either specific users or groups.
Compatibility
| Version | Notes |
|---|---|
| IIS 10.0 | The <add> element was not modified in IIS 10.0. |
| IIS 8.5 | The <add> element was not modified in IIS 8.5. |
| IIS 8.0 | The <add> element was not modified in IIS 8.0. |
| IIS 7.5 | The <add> element was not modified in IIS 7.5. |
| IIS 7.0 | The <add> element of the <authorization> collection was introduced in IIS 7.0. |
| IIS 6.0 | The <authorization> collection replaces the IIS 6.0 AzEnable, AzStoreName, AzScopeName, and AzImpersonationLevel metabase properties. |
Setup
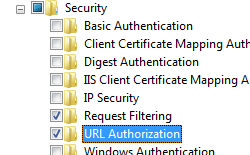
To support and configure authorization for sites and applications on your Web server, you must install the URL authorization module. To do so, use the following steps.
Windows Server 2012 or Windows Server 2012 R2
- On the taskbar, click Server Manager. - In Server Manager, click the Manage menu, and then click Add Roles and Features. - In the Add Roles and Features wizard, click Next. Select the installation type and click Next. Select the destination server and click Next. - On the Server Roles page, expand Web Server (IIS), expand Web Server, expand Security, and then select URL Authorization. Click Next.
 . - On the Select features page, click Next. - On the Confirm installation selections page, click Install. - On the Results page, click Close.
. - On the Select features page, click Next. - On the Confirm installation selections page, click Install. - On the Results page, click Close.
Windows 8 or Windows 8.1
- On the Start screen, move the pointer all the way to the lower left corner, right-click the Start button, and then click Control Panel. - In Control Panel, click Programs and Features, and then click Turn Windows features on or off. - Expand Internet Information Services, expand World Wide Web Services, expand Security, and then select URL Authorization.
 - Click OK.
- Click OK. - Click Close.
Windows Server 2008 or Windows Server 2008 R2
- On the taskbar, click Start, point to Administrative Tools, and then click Server Manager. - In the Server Manager hierarchy pane, expand Roles, and then click Web Server (IIS). - In the Web Server (IIS) pane, scroll to the Role Services section, and then click Add Role Services. - On the Select Role Services page of the Add Role Services Wizard, select URL Authorization, and then click Next.
 - On the Confirm Installation Selections page, click Install. - On the Results page, click Close.
- On the Confirm Installation Selections page, click Install. - On the Results page, click Close.
Windows Vista or Windows 7
- On the taskbar, click Start, and then click Control Panel. - In Control Panel, click Programs and Features, and then click Turn Windows Features on or off. - Expand Internet Information Services, then select URL Authorization, and then click OK.
How To
How to add an authorization rule
Open Internet Information Services (IIS) Manager:
If you are using Windows Server 2012 or Windows Server 2012 R2:
- On the taskbar, click Server Manager, click Tools, and then click Internet Information Services (IIS) Manager.
If you are using Windows 8 or Windows 8.1:
- Hold down the Windows key, press the letter X, and then click Control Panel.
- Click Administrative Tools, and then double-click Internet Information Services (IIS) Manager.
If you are using Windows Server 2008 or Windows Server 2008 R2:
- On the taskbar, click Start, point to Administrative Tools, and then click Internet Information Services (IIS) Manager.
If you are using Windows Vista or Windows 7:
- On the taskbar, click Start, and then click Control Panel.
- Double-click Administrative Tools, and then double-click Internet Information Services (IIS) Manager.
In the Connections pane, expand the server name, expand Sites, and then navigate to the site or application on which you want to configure authorization.
To add a new authorization rule, in the Actions pane click Add Allow Rule... or Add Deny Rule...
Apply the authorization settings needed for your site or application, and then click OK. For example:
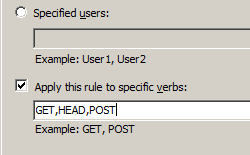
Example #1: Adding an Allow rule for all users for specific HTTP verbs:
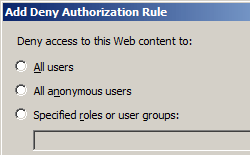
Example #2: Adding a Deny rule for a specific user for all HTTP verbs:
Note
To edit or delete an existing rule, select the rule in the Authorization rules pane, and then click Edit or Remove in the Actions pane. If you click Edit... , a dialog box appears that allows you to edit the rule; this dialog box is similar to the Add Allow Authorization Rule and Add Deny Authorization Rule dialog boxes.
Configuration
Attributes
| Attribute | Description | ||||||
|---|---|---|---|---|---|---|---|
accessType |
Required Enum attribute. The accessType attribute can be one of the following possible values.
|
||||||
roles |
Optional string attribute. Specifies roles for an authorization rule. |
||||||
users |
Optional string attribute. Specifies users for an authorization rule. Multiple users can be added in a comma-separated list. In addition, the following special identifiers have been defined.
|
||||||
verbs |
Optional string attribute. Specifies the HTTP verbs for an authorization rule. If this value is left blank or is not specified, the rule will apply to all HTTP verbs. |
Child Elements
None.
Configuration Sample
The following configuration example, when included in a Web.config file, removes the default IIS authorization settings, which allows all users access to Web site or application content. It then configures an authorization rule that allows only users with administrator privileges to access the content.
<configuration>
<system.webServer>
<security>
<authorization>
<remove users="*" roles="" verbs="" />
<add accessType="Allow" users="" roles="Administrators" />
</authorization>
</security>
</system.webServer>
</configuration>
Sample Code
The following examples add an allow authorization rule that allows users in the administrators group to access a Web site named Contoso.
AppCmd.exe
appcmd.exe set config "Contoso" -section:system.webServer/security/authorization /+"[accessType='Allow',roles='administrators']"
Note
You can optionally set the commit parameter to apphost when using AppCmd.exe to configure these settings. This commits the configuration settings to the appropriate location section in the ApplicationHost.config file instead of a Web.config file.
C#
using System;
using System.Text;
using Microsoft.Web.Administration;
internal static class Sample
{
private static void Main()
{
using (ServerManager serverManager = new ServerManager())
{
Configuration config = serverManager.GetWebConfiguration("Contoso");
ConfigurationSection authorizationSection = config.GetSection("system.webServer/security/authorization");
ConfigurationElementCollection authorizationCollection = authorizationSection.GetCollection();
ConfigurationElement addElement = authorizationCollection.CreateElement("add");
addElement["accessType"] = @"Allow";
addElement["roles"] = @"administrators";
authorizationCollection.Add(addElement);
serverManager.CommitChanges();
}
}
}
VB.NET
Imports System
Imports System.Text
Imports Microsoft.Web.Administration
Module Sample
Sub Main()
Dim serverManager As ServerManager = New ServerManager
Dim config As Configuration = serverManager.GetWebConfiguration("Contoso")
Dim authorizationSection As ConfigurationSection = config.GetSection("system.webServer/security/authorization")
Dim authorizationCollection As ConfigurationElementCollection = authorizationSection.GetCollection
Dim addElement As ConfigurationElement = authorizationCollection.CreateElement("add")
addElement("accessType") = "Allow"
addElement("roles") = "administrators"
authorizationCollection.Add(addElement)
serverManager.CommitChanges()
End Sub
End Module
JavaScript
var adminManager = new ActiveXObject('Microsoft.ApplicationHost.WritableAdminManager');
adminManager.CommitPath = "MACHINE/WEBROOT/APPHOST/Contoso";
var authorizationSection = adminManager.GetAdminSection("system.webServer/security/authorization", "MACHINE/WEBROOT/APPHOST/Contoso");
var authorizationCollection = authorizationSection.Collection;
var addElement = authorizationCollection.CreateNewElement("add");
addElement.Properties.Item("accessType").Value = "Allow";
addElement.Properties.Item("roles").Value = "administrators";
authorizationCollection.AddElement(addElement);
adminManager.CommitChanges();
VBScript
Set adminManager = CreateObject("Microsoft.ApplicationHost.WritableAdminManager")
adminManager.CommitPath = "MACHINE/WEBROOT/APPHOST/Contoso"
Set authorizationSection = adminManager.GetAdminSection("system.webServer/security/authorization", "MACHINE/WEBROOT/APPHOST/Contoso")
Set authorizationCollection = authorizationSection.Collection
Set addElement = authorizationCollection.CreateNewElement("add")
addElement.Properties.Item("accessType").Value = "Allow"
addElement.Properties.Item("roles").Value = "administrators"
authorizationCollection.AddElement(addElement)
adminManager.CommitChanges()