How to use Microsoft Entra Health monitoring alerts (preview)
Microsoft Entra Health monitoring provides the ability to monitor the health of your Microsoft Entra tenant through a set of health metrics and intelligent alerts. Health metrics are fed into our anomaly detection service, which uses machine learning to understand the patterns for your tenant. When the anomaly detection service identifies a significant change in one of the tenant-level patterns, it triggers an alert. You can receive email notifications when a potential issue or failure condition is detected within the health scenarios. For more information on Microsoft Entra Health, see What is Microsoft Entra Health.
This article provides guidance on how to:
- Access Microsoft Entra Health.
- Configure email notifications for alerts.
- Investigate an alert.
Prerequisites
There are different roles, permissions, and license requirements to view health monitoring signals and configure and receive alerts. We recommend using a role with least privilege access to align with the Zero Trust guidance.
- A tenant with a Microsoft Entra P1 or P2 license is required to view the Microsoft Entra health scenario monitoring signals.
- A tenant with both a Microsoft Entra P1 or P2 license and at least 100 monthly active users is required to view alerts and receive alert notifications.
- The Reports Reader role is the least privileged role required to view scenario monitoring signals, alerts, and alert configurations.
- The Helpdesk Administrator is the least privileged role required to update alerts and update alert notification configurations.
- The
HealthMonitoringAlert.Read.Allpermission is required to view the alerts using the Microsoft Graph API. - The
HealthMonitoringAlert.ReadWrite.Allpermission is required to view and modify the alerts using the Microsoft Graph API. - For a full list of roles, see Least privileged role by task.
Known limitations
- Newly onboarded tenants might not have enough data to generate alerts for about 30 days.
- Currently, alerts are only available with the Microsoft Graph API.
Access Microsoft Entra Health
You can view the Microsoft Entra Health service level agreement (SLA) attainment report and the health monitoring signals from the Microsoft Entra admin center. You can also view these data streams, and the public preview of health monitoring alerts, using Microsoft Graph APIs. Enable the Scenario monitoring preview.
Sign into the Microsoft Entra admin center as at least a Reports Reader.
Browse to Identity > Monitoring and health > Health.
Select the Scenario Monitoring tab.
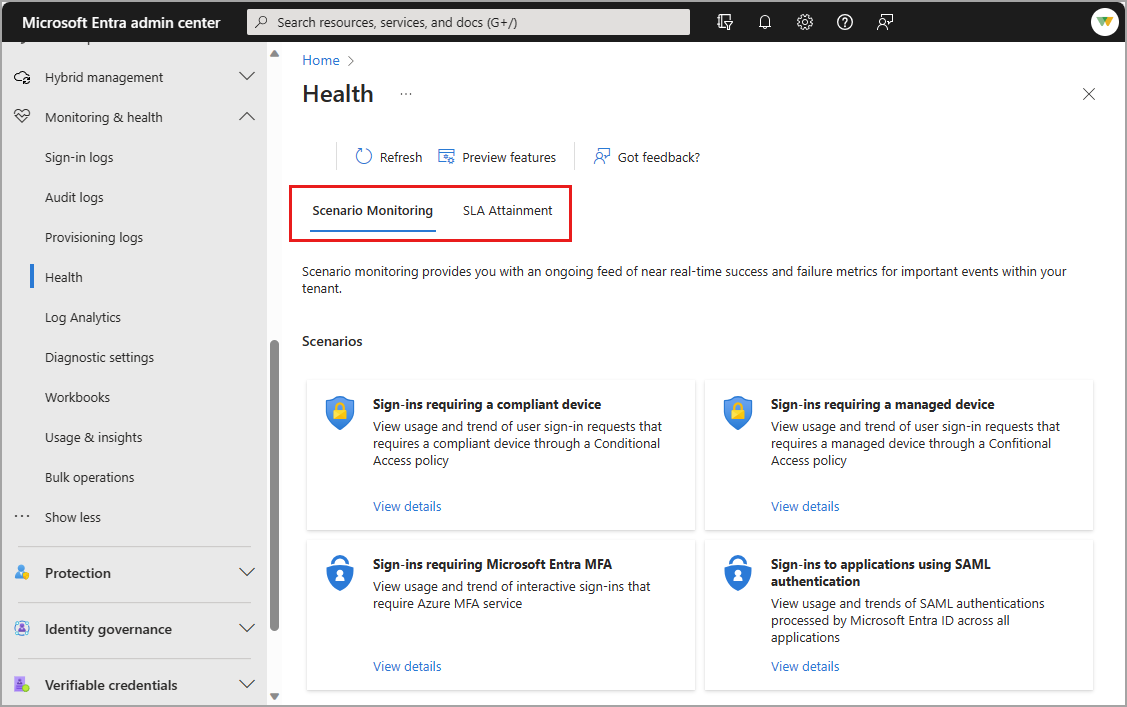
Select View details for the scenario you wish to investigate.
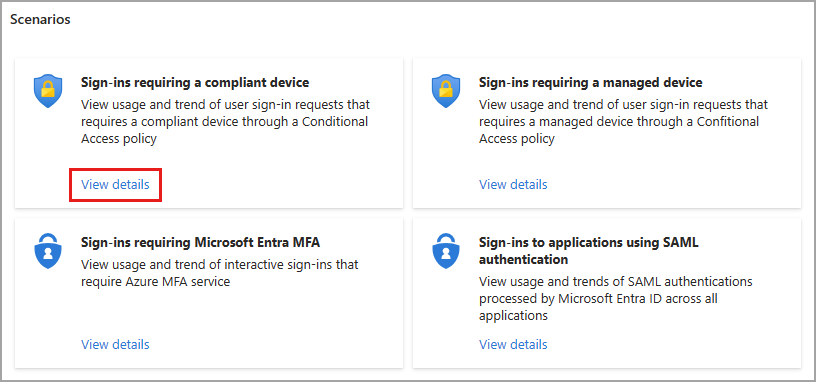
The default view is the last seven days, but you can adjust the date range to 24 hours, seven days, or one month. The data is updated every 15 minutes.
Configure the email notifications
With the Microsoft Graph health monitoring alerts API, you can configure email notifications. You can run the API calls on a regular cadence (for example, daily or hourly) or you can configure email notifications for when an alert is triggered. We recommend daily monitoring of the scenario monitoring signals and alerts.
Email notifications are sent to the Microsoft Entra group of your choice. We recommend sending alerts to users with the appropriate access to investigate and take action on the alerts. Not every role can take the same action, so consider including a group with the following roles:
To configure alert notifications, you need the ID of the Microsoft Entra group you want to receive the alerts AND the scenario alert ID. You can configure different groups to receive alerts for different alert scenarios.
Locate the group's Object ID
Sign in to the Microsoft Entra admin center as at least a User Administrator.
Browse to Groups > All groups > and select the group you want to receive the alerts.
Select Properties and copy the
Object IDof the group.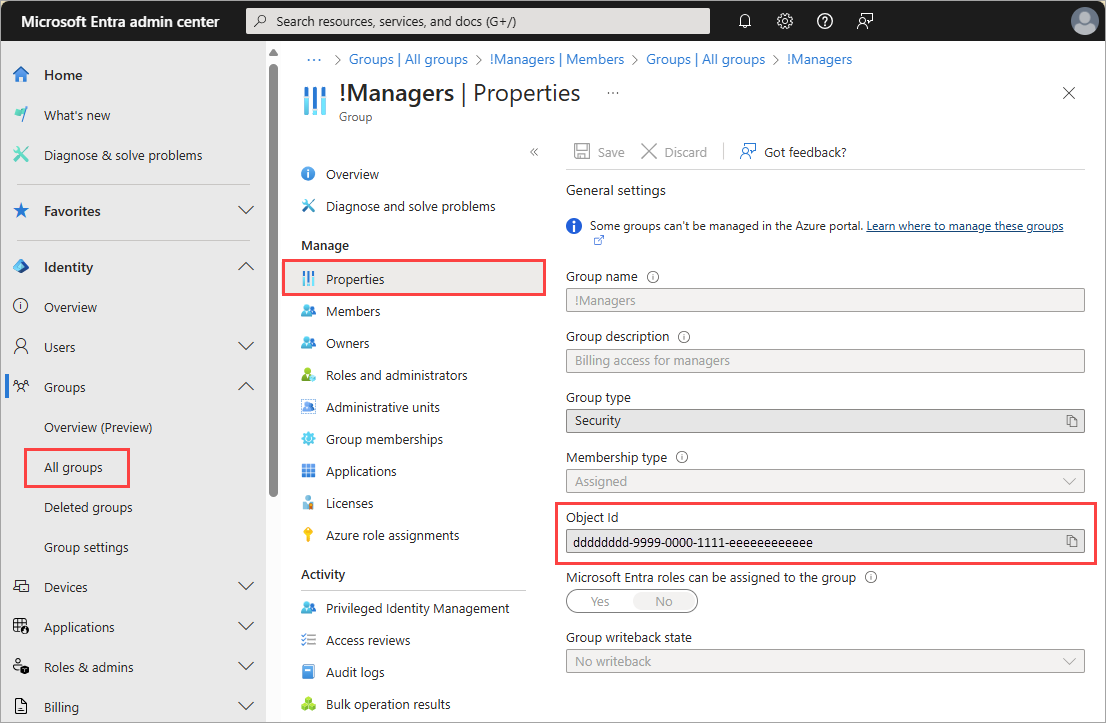
Locate the scenario alert type
Sign in to Microsoft Graph Explorer as at least a Helpdesk Administrator and consent to the appropriate permissions.
Select GET as the HTTP method from the dropdown and set the API version to beta.
Run the following query to retrieve the list of alerts for your tenant.
GET https://graph.microsoft.com/beta/reports/healthMonitoring/alertsLocate and save the
alertTypeof the alert you want to be notified about, for examplealertType: "mfaSignInFailure.
Configure the email notifications
In Microsoft Graph Explorer, run the following PATCH query to configure email notifications for alerts.
- Replace
{alertType}with the specificalertTypeyou want to configure. - Replace
Object ID of the groupwith theObject IDof the group you want to receive the alerts. - For more information, see configure email notifications for alerts.
PATCH https://graph.microsoft.com/beta/reports/healthMonitoring/alertConfigurations/{alertType}
Content-Type: application/json
{
"emailNotificationConfigurations": [
{
"groupId":"Object ID of the group",
"isEnabled": true
}
]
}
Investigate the alert and signals
With the email notifications configured, you and your team can more effectively monitor the health of these scenarios. When you receive an alert, you typically need to investigate the following data sets:
- Alert impact: The portion of the response after
impactsquantifies the scope and summarizes impacted resources. These details include theimpactCountso you can determine how widespread the issue is. - Alert signals: The data stream, or health signal, that caused the alert. A query is provided in the response for further investigation.
- Sign-in logs: A query is provided in the response for further investigation into the sign-in logs where the health signal was generated. The sign-in logs provide detailed event metadata that might be used to identify a problem's root cause.
- Scenario-specific resources: Depending on the scenario, you might need to investigate Intune compliance policies or Conditional Access policies. In many cases, a link to related documentation is provided in the response.
View the impacts and signals
In Microsoft Graph, add the following query to retrieve all alerts for your tenant.
GET https://graph.microsoft.com/beta/reports/healthMonitoring/alertsLocate and save the
idof the alert you want to investigate.Add the following query, using
idas thealertId.GET https://graph.microsoft.com/beta/reports/healthMonitoring/alerts/{alertId}
For sample requests and responses, see Health monitoring List alert objects.
- The portion of the response after
impactsmake up the impact summary for the alert. - The
supportingDataportion includes the full query used to generate the alert. - The results of the query include everything identified by the anomaly detection service, but there might be results that aren't directly related to the alert.
View the sign-in logs
- Sign in to the Microsoft Entra admin center as at least a Reports Reader.
- If you need to modify Conditional Access policies, you need the Conditional Access Administrator role.
- Browse to Monitoring & health > Sign-in logs.
- Adjust the time range to match the alert time frame.
- Add a filter for Conditional Access.
- Select a log entry to view the sign-in logs details and select the Conditional Access tab to see the policies that were applied.
View the scenario-specific resources
Each alert might have a different data set to investigate. For details on each alert type, see the following articles:
- Sign-ins requiring a compliant or managed device
- Sign-ins requiring multifactor authentication (MFA)
Analyze the possible root causes
After gathering all the data related to the scenario, you need to consider possible root causes and research potential solutions. Think about the seriousness of the alert. Are only a handful of users affected, or is it a widespread issue? Did a recent policy change have unintended consequences?
We recommend looking at the alerts and health monitoring data regularly to identify trends and potential issues before they become widespread problems.