Configure anti-malware policies in EOP
Tip
Did you know you can try the features in Microsoft Defender for Office 365 Plan 2 for free? Use the 90-day Defender for Office 365 trial at the Microsoft Defender portal trials hub. Learn about who can sign up and trial terms on Try Microsoft Defender for Office 365.
In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, email messages are automatically protected against malware by EOP. EOP uses anti-malware policies for malware protection settings. For more information, see Anti-malware protection.
The default anti-malware policy automatically applies to all recipients. For greater granularity, you can also create custom anti-malware policies that apply to specific users, groups, or domains in your organization.
Tip
The default anti-malware policy applies to inbound and outbound email. Custom anti-malware policies apply to inbound email only.
Instead of creating and managing custom anti-malware policies, we typically recommend turning on and adding all users to the Standard and/or Strict preset security policies. For more information, see Configure protection policies.
To understand how threat protection works in Microsoft Defender for Office 365, see Step-by-step threat protection in Microsoft Defender for Office 365.
You can configure anti-malware policies in the Microsoft Defender portal or in PowerShell (Exchange Online PowerShell for Microsoft 365 organizations with mailboxes in Exchange Online; standalone EOP PowerShell for organizations without Exchange Online mailboxes).
What do you need to know before you begin?
You open the Microsoft Defender portal at https://security.microsoft.com. To go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2.
To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell. To connect to standalone EOP PowerShell, see Connect to Exchange Online Protection PowerShell.
You need to be assigned permissions before you can do the procedures in this article. You have the following options:
Microsoft Defender XDR Unified role based access control (RBAC) (If Email & collaboration > Defender for Office 365 permissions is
 Active. Affects the Defender portal only, not PowerShell): Authorization and settings/Security settings/Core Security settings (manage) or Authorization and settings/Security settings/Core Security settings (read).
Active. Affects the Defender portal only, not PowerShell): Authorization and settings/Security settings/Core Security settings (manage) or Authorization and settings/Security settings/Core Security settings (read).-
- Add, modify, and delete policies: Membership in the Organization Management or Security Administrator role groups.
- Read-only access to policies: Membership in the Global Reader, Security Reader, or View-Only Organization Management role groups.
Microsoft Entra permissions: Membership in the Global Administrator*, Security Administrator, Global Reader, or Security Reader roles gives users the required permissions and permissions for other features in Microsoft 365.
Important
* Microsoft recommends that you use roles with the fewest permissions. Using lower permissioned accounts helps improve security for your organization. Global Administrator is a highly privileged role that should be limited to emergency scenarios when you can't use an existing role.
For our recommended settings for anti-malware policies, see EOP anti-malware policy settings.
Tip
Settings in the default or custom anti-malware policies are ignored if a recipient is also included in the Standard or Strict preset security policies. For more information, see Order and precedence of email protection.
Use the Microsoft Defender portal to create anti-malware policies
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Anti-Malware in the Policies section. To go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2.
On the Anti-malware page, select
 Create to open the new anti-malware policy wizard.
Create to open the new anti-malware policy wizard.On the Name your policy page, configure these settings:
- Name: Enter a unique, descriptive name for the policy.
- Description: Enter an optional description for the policy.
When you're finished on the Name your policy page, select Next.
On the Users and domains page, identify the internal recipients that the policy applies to (recipient conditions):
Users: The specified mailboxes, mail users, or mail contacts.
Groups:
- Members of the specified distribution groups or mail-enabled security groups (dynamic distribution groups aren't supported).
- The specified Microsoft 365 Groups.
Domains: All recipients in the organization with a primary email address in the specified accepted domain.
Tip
Subdomains are automatically included unless you specifically exclude them. For example, a policy that includes contoso.com also includes marketing.contoso.com unless you exclude marketing.contoso.com.
Click in the appropriate box, start typing a value, and select the value that you want from the results. Repeat this process as many times as necessary. To remove an existing value, select
 next to the value.
next to the value.For users or groups, you can use most identifiers (name, display name, alias, email address, account name, etc.), but the corresponding display name is shown in the results. For users or groups, enter an asterisk (*) by itself to see all available values.
You can use a condition only once, but the condition can contain multiple values:
Multiple values of the same condition use OR logic (for example, <recipient1> or <recipient2>). If the recipient matches any of the specified values, the policy is applied to them.
Different types of conditions use AND logic. The recipient must match all of the specified conditions for the policy to apply to them. For example, you configure a condition with the following values:
- Users:
romain@contoso.com - Groups: Executives
The policy is applied to
romain@contoso.comonly if he's also a member of the Executives group. Otherwise, the policy isn't applied to him.- Users:
Exclude these users, groups, and domains: To add exceptions for the internal recipients that the policy applies to (recipient exceptions), select this option and configure the exceptions.
You can use an exception only once, but the exception can contain multiple values:
- Multiple values of the same exception use OR logic (for example, <recipient1> or <recipient2>). If the recipient matches any of the specified values, the policy isn't applied to them.
- Different types of exceptions use OR logic (for example, <recipient1> or <member of group1> or <member of domain1>). If the recipient matches any of the specified exception values, the policy isn't applied to them.
When you're finished on the Users and domains page, select Next.
On the Protection settings page, configure the following settings:
Protection settings section:
Enable the common attachments filter: If you select this option, messages with the specified attachments are treated as malware and are automatically quarantined. You can modify the list by clicking Customize file types and selecting or deselecting values in the list.
For the default and available values, see Common attachments filter in anti-malware policies.
When these types are found: Select one of the following values:
- Reject the message with a non-delivery report (NDR) (this is the default value)
- Quarantine the message
Enable zero-hour auto purge for malware: If you select this option, ZAP quarantines malware messages that have already been delivered. For more information, see Zero-hour auto purge (ZAP) for malware.
Quarantine policy: Select the quarantine policy that applies to messages that are quarantined as malware. By default, the quarantine policy named AdminOnlyAccessPolicy is used for malware detections. For more information about this quarantine policy, see Anatomy of a quarantine policy.
Tip
Quarantine notifications are disabled in the policy named AdminOnlyAccessPolicy. To notify recipients that have messages quarantined as malware, create or use an existing quarantine policy where quarantine notifications are turned on. For instructions, see Create quarantine policies in the Microsoft Defender portal.
Users can't release their own messages that were quarantined as malware by anti-malware policies, regardless of how the quarantine policy is configured. If the policy allows users to release their own quarantined messages, users are instead allowed to request the release of their quarantined malware messages.
Notifications section:
Admin notifications section: Select none, one, or both of the following options:
- Notify an admin about undelivered messages from internal senders: If you select this option, enter a recipient email address in the Admin email address box that appears.
- Notify an admin about undelivered messages from external senders: If you select this option, enter a recipient email address in the Admin email address box that appears.
Tip
Admin notifications are sent only for attachments that are classified as malware.
The quarantine policy that's assigned to the anti-malware policy determines whether recipients receive email notifications for messages that were quarantined as malware.
Customize notifications section: Use the settings in this section to customize the message properties that are used for admin notifications.
Use customized notification text: If you select this option, use the From name and From address boxes that appear to specify the sender's name and email address for admin notification messages.
Customize notifications for messages from internal senders section: If you previously selected Notify an admin about undelivered messages from internal senders, use the Subject and Message boxes that appear in this section to specify the subject and message body of admin notification messages.
Customize notifications for messages from external senders section: If you previously selected Notify an admin about undelivered messages from external senders, use the Subject and Message boxes that appear in this section to specify the subject and message body of admin notification messages.
When you're finished on the Protection settings page, select Next.
On the Review page, review your settings. You can select Edit in each section to modify the settings within the section. Or you can select Back or the specific page in the wizard.
When you're finished on the Review page, select Submit.
On the Created new anti-malware policy page, you can select the links to view the policy, view anti-malware policies, and learn more about anti-malware policies.
When you're finished on the Created new anti-malware policy page, select Done.
Back on the Anti-malware page, the new policy is listed.
Use the Microsoft Defender portal to view anti-malware policy details
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Anti-Malware in the Policies section. Or, to go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2.
On the Anti-malware page, the following properties are displayed in the list of anti-malware policies:
- Name
- Status: Values are:
- Always on for the default anti-malware policy.
- On or Off for other anti-malware policies.
- Priority: For more information, see the Set the priority of custom anti-malware policies section.
To change the list of policies from normal to compact spacing, select ![]() Change list spacing to compact or normal, and then select
Change list spacing to compact or normal, and then select ![]() Compact list.
Compact list.
Use the ![]() Search box and a corresponding value to find specific anti-malware policies.
Search box and a corresponding value to find specific anti-malware policies.
Use ![]() Export to export the list of policies to a CSV file.
Export to export the list of policies to a CSV file.
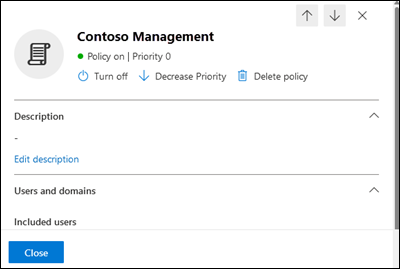
Select a policy by clicking anywhere in the row other than the check box next to the name to open the details flyout for the policy.
Tip
To see details about other anti-malware policies without leaving the details flyout, use  Previous item and Next item at the top of the flyout.
Previous item and Next item at the top of the flyout.
Use the Microsoft Defender portal to take action on anti-malware policies
In the Microsoft Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Anti-Malware in the Policies section. To go directly to the Anti-malware page, use https://security.microsoft.com/antimalwarev2.
On the Anti-malware page, select the anti-malware policy by using either of the following methods:
Select the policy from the list by selecting the check box next to the name. The following actions are available in the
 More actions dropdown list that appears:
More actions dropdown list that appears:- Enable selected policies.
- Disable selected policies.
- Delete selected policies.
Select the policy from the list by clicking anywhere in the row other than the check box next to the name. Some or all following actions are available in the details flyout that opens:
- Modify policy settings by clicking Edit in each section (custom policies or the default policy)
 Turn on or
Turn on or  Turn off (custom policies only)
Turn off (custom policies only) Increase priority or
Increase priority or  Decrease priority (custom policies only)
Decrease priority (custom policies only) Delete policy (custom policies only)
Delete policy (custom policies only)
The actions are described in the following subsections.
Use the Microsoft Defender portal to modify anti-malware policies
After you select the default anti-malware policy or a custom policy by clicking anywhere in the row other than the check box next to the name, the policy settings are shown in the details flyout that opens. Select Edit in each section to modify the settings within the section. For more information about the settings, see the Create anti-malware policies section earlier in this article.
For the default policy, you can't modify the name of the policy, and there are no recipient filters to configure (the policy applies to all recipients). But, you can modify all other settings in the policy.
For the anti-malware policies named Standard Preset Security Policy and Strict Preset Security Policy that are associated with preset security policies, you can't modify the policy settings in the details flyout. Instead, you select ![]() View preset security policies in the details flyout to go to the Preset security policies page at https://security.microsoft.com/presetSecurityPolicies to modify the preset security policies.
View preset security policies in the details flyout to go to the Preset security policies page at https://security.microsoft.com/presetSecurityPolicies to modify the preset security policies.
Use the Microsoft Defender portal to enable or disable custom anti-malware policies
You can't disable the default anti-malware policy (it's always enabled).
You can't enable or disable the anti-malware policies that are associated with Standard and Strict preset security policies. You enable or disable the Standard or Strict preset security policies on the Preset security policies page at https://security.microsoft.com/presetSecurityPolicies.
After you select an enabled custom anti-malware policy (the Status value is On), use either of the following methods to disable it:
- On the Anti-malware page: Select
 More actions > Disable selected policies.
More actions > Disable selected policies. - In the details flyout of the policy: Select
 Turn off at the top of the flyout.
Turn off at the top of the flyout.
After you select a disabled custom anti-malware policy (the Status value is Off), use either of the following methods to enable it:
- On the Anti-malware page: Select
 More actions > Enable selected policies.
More actions > Enable selected policies. - In the details flyout of the policy: Select
 Turn on at the top of the flyout.
Turn on at the top of the flyout.
On the Anti-malware page, the Status value of the policy is now On or Off.
Use the Microsoft Defender portal to set the priority of custom anti-malware policies
Anti-malware policies are processed in the order that they're displayed on the Anti-malware page:
- The anti-malware policy named Strict Preset Security Policy that's associated with the Strict preset security policy is always applied first (if the Strict preset security policy is enabled).
- The anti-malware policy named Standard Preset Security Policy that's associated with the Standard preset security policy is always applied next (if the Standard preset security policy is enabled).
- Custom anti-malware policies are applied next in priority order (if they're enabled):
- A lower priority value indicates a higher priority (0 is the highest).
- By default, a new policy is created with a priority that's lower than the lowest existing custom policy (the first is 0, the next is 1, etc.).
- No two policies can have the same priority value.
- The default anti-malware policy always has the priority value Lowest, and you can't change it.
Anti-malware protection stops for a recipient after the first policy is applied (the highest priority policy for that recipient). For more information, see Order and precedence of email protection.
After you select the custom anti-malware policy by clicking anywhere in the row other than the check box next to the name, you can increase or decrease the priority of the policy in the details flyout that opens:
- The custom policy with the Priority value 0 on the Anti-malware page has the
 Decrease priority action at the top of the details flyout.
Decrease priority action at the top of the details flyout. - The custom policy with the lowest priority (highest Priority value; for example, 3) has the
 Increase priority action at the top of the details flyout.
Increase priority action at the top of the details flyout. - If you have three or more policies, the policies between Priority 0 and the lowest priority have both the
 Increase priority and the
Increase priority and the  Decrease priority actions at the top of the details flyout.
Decrease priority actions at the top of the details flyout.
When you're finished in the policy details flyout, select Close.
Back on the Anti-malware page, the order of the policy in the list matches the updated Priority value.
Use the Microsoft Defender portal to remove custom anti-malware policies
You can't remove the default anti-malware policy or the anti-malware policies named Standard Preset Security Policy and Strict Preset Security Policy that are associated with preset security policies.
After you select the custom anti-malware policy, use either of the following methods to remove it:
- On the Anti-malware page: Select
 More actions > Delete selected policies.
More actions > Delete selected policies. - In the details flyout of the policy: Select
 Delete policy at the top of the flyout.
Delete policy at the top of the flyout.
Select Yes in the warning dialog that opens.
On the Anti-malware page, the deleted policy is no longer listed.
Use Exchange Online PowerShell or standalone EOP PowerShell to configure anti-malware policies
In PowerShell, the basic elements of an anti-malware policy are:
- The malware filter policy: Specifies the recipient notification, sender and admin notification, ZAP, and the common attachments filter settings.
- The malware filter rule: Specifies the priority and recipient filters (who the policy applies to) for a malware filter policy.
The difference between these two elements isn't obvious when you manage anti-malware policies in the Microsoft Defender portal:
- When you create an anti-malware policy in the Defender portal, you're actually creating a malware filter rule and the associated malware filter policy at the same time using the same name for both.
- When you modify an anti-malware policy in the Defender portal, settings related to the name, priority, enabled or disabled, and recipient filters modify the malware filter rule. Other settings (recipient notification, sender and admin notification, ZAP, and the common attachments filter) modify the associated malware filter policy.
- When you remove an anti-malware policy from the Defender portal, the malware filter rule and the associated malware filter policy are removed at the same time.
In Exchange Online PowerShell or standalone EOP PowerShell, the difference between malware filter policies and malware filter rules is apparent. You manage malware filter policies by using the *-MalwareFilterPolicy cmdlets, and you manage malware filter rules by using the *-MalwareFilterRule cmdlets.
- In PowerShell, you create the malware filter policy first, then you create the malware filter rule that identifies the policy that the rule applies to.
- In PowerShell, you modify the settings in the malware filter policy and the malware filter rule separately.
- When you remove a malware filter policy from PowerShell, the corresponding malware filter rule isn't automatically removed, and vice versa.
Use PowerShell to create anti-malware policies
Creating an anti-malware policy in PowerShell is a two-step process:
- Create the malware filter policy.
- Create the malware filter rule that specifies the malware filter policy that the rule applies to.
Notes:
- You can create a new malware filter rule and assign an existing, unassociated malware filter policy to it. A malware filter rule can't be associated with more than one malware filter policy.
- There are two settings that you can configure on new anti-malware policies in PowerShell that aren't available in the Microsoft Defender portal until after you create the policy:
- Create the new policy as disabled (Enabled
$falseon the New-MalwareFilterRule cmdlet). - Set the priority of the policy during creation (Priority <Number>) on the New-MalwareFilterRule cmdlet).
- Create the new policy as disabled (Enabled
- A new malware filter policy that you create in PowerShell isn't visible in the Microsoft Defender portal until you assign the policy to a malware filter rule.
Step 1: Use PowerShell to create a malware filter policy
To create a malware filter policy, use this syntax:
New-MalwareFilterPolicy -Name "<PolicyName>" [-AdminDisplayName "<OptionalComments>"] [-EnableFileFilter <$true | $false>] [-FileTypeAction <Reject | Quarantine>] [-FileTypes FileType1,FileType2,...FileTypeN] [-CustomNotifications <$true | $false>] [<Inbound notification options>] [<Outbound notification options>] [-QuarantineTag <QuarantineTagName>]
This example creates a new malware filter policy named Contoso Malware Filter Policy with these settings:
- Notify admin@contoso.com when malware is detected in a message from an internal sender.
- The common attachments filter is enabled (
-EnableFileFilter $true) and the default list of file types is used (we aren't using the FileTypes parameter). - Messages detected by the common attachments filter are rejected with an NDR (we aren't using the FileTypeAction parameter, and the default value is
Reject). - The default quarantine policy for malware detections is used (we aren't using the QuarantineTag parameter).
New-MalwareFilterPolicy -Name "Contoso Malware Filter Policy" -EnableFileFilter $true -EnableInternalSenderAdminNotifications $true -InternalSenderAdminAddress admin@contoso.com
For detailed syntax and parameter information, see New-MalwareFilterPolicy.
Step 2: Use PowerShell to create a malware filter rule
To create a malware filter rule, use this syntax:
New-MalwareFilterRule -Name "<RuleName>" -MalwareFilterPolicy "<PolicyName>" <Recipient filters> [<Recipient filter exceptions>] [-Comments "<OptionalComments>"]
This example creates a new malware filter rule named Contoso Recipients with these settings:
- The malware filter policy named Contoso Malware Filter Policy is associated with the rule.
- The rule applies to recipients in the contoso.com domain.
New-MalwareFilterRule -Name "Contoso Recipients" -MalwareFilterPolicy "Contoso Malware Filter Policy" -RecipientDomainIs contoso.com
For detailed syntax and parameter information, see New-MalwareFilterRule.
Use PowerShell to view malware filter policies
To return a summary list of all malware filter policies, run this command:
Get-MalwareFilterPolicy
To return detailed information about a specific malware filter policy, use this syntax:
Get-MalwareFilterPolicy -Identity "<PolicyName>" | Format-List [<Specific properties to view>]
This example returns all the property values for the malware filter policy named Executives.
Get-MalwareFilterPolicy -Identity "Executives" | Format-List
This example returns only the specified properties for the same policy.
Get-MalwareFilterPolicy -Identity "Executives" | Format-List Action,AdminDisplayName,CustomNotifications,Enable*Notifications
For detailed syntax and parameter information, see Get-MalwareFilterPolicy.
Use PowerShell to view malware filter rules
To return a summary list of all malware filter rules, run this command:
Get-MalwareFilterRule
To filter the list by enabled or disabled rules, run the following commands:
Get-MalwareFilterRule -State Disabled
Get-MalwareFilterRule -State Enabled
To return detailed information about a specific malware filter rule, use this syntax:
Get-MalwareFilterRule -Identity "<RuleName>" | Format-List [<Specific properties to view>]
This example returns all the property values for the malware filter rule named Executives.
Get-MalwareFilterRule -Identity "Executives" | Format-List
This example returns only the specified properties for the same rule.
Get-MalwareFilterRule -Identity "Executives" | Format-List Name,Priority,State,MalwareFilterPolicy,*Is,*SentTo,*MemberOf
For detailed syntax and parameter information, see Get-MalwareFilterRule.
Use PowerShell to modify malware filter policies
Other than the following items, the same settings are available when you modify a malware filter policy in PowerShell as when you create the policy as described in the Step 1: Use PowerShell to create a malware filter policy section earlier in this article.
- The MakeDefault switch that turns the specified policy into the default policy (applied to everyone, unmodifiable Lowest priority, and you can't delete it) is only available when you modify a malware filter policy in PowerShell.
- You can't rename a malware filter policy (the Set-MalwareFilterPolicy cmdlet has no Name parameter). When you rename an anti-malware policy in the Microsoft Defender portal, you're only renaming the malware filter rule.
To modify a malware filter policy, use this syntax:
Set-MalwareFilterPolicy -Identity "<PolicyName>" <Settings>
For detailed syntax and parameter information, see Set-MalwareFilterPolicy.
Tip
For detailed instructions to specify the quarantine policy to use in a malware filter policy, see Use PowerShell to specify the quarantine policy in anti-malware policies.
Use PowerShell to modify malware filter rules
The only setting that isn't available when you modify a malware filter rule in PowerShell is the Enabled parameter that allows you to create a disabled rule. To enable or disable existing malware filter rules, see the next section.
Otherwise, no additional settings are available when you modify a malware filter rule in PowerShell. The same settings are available when you create a rule as described in the Step 2: Use PowerShell to create a malware filter rule section earlier in this article.
To modify a malware filter rule, use this syntax:
Set-MalwareFilterRule -Identity "<RuleName>" <Settings>
For detailed syntax and parameter information, see Set-MalwareFilterRule.
Use PowerShell to enable or disable malware filter rules
Enabling or disabling a malware filter rule in PowerShell enables or disables the whole anti-malware policy (the malware filter rule and the assigned malware filter policy). You can't enable or disable the default anti-malware policy (it's always applied to all recipients).
To enable or disable a malware filter rule in PowerShell, use this syntax:
<Enable-MalwareFilterRule | Disable-MalwareFilterRule> -Identity "<RuleName>"
This example disables the malware filter rule named Marketing Department.
Disable-MalwareFilterRule -Identity "Marketing Department"
This example enables same rule.
Enable-MalwareFilterRule -Identity "Marketing Department"
For detailed syntax and parameter information, see Enable-MalwareFilterRule and Disable-MalwareFilterRule.
Use PowerShell to set the priority of malware filter rules
The highest priority value you can set on a rule is 0. The lowest value you can set depends on the number of rules. For example, if you have five rules, you can use the priority values 0 through 4. Changing the priority of an existing rule can have a cascading effect on other rules. For example, if you have five custom rules (priorities 0 through 4), and you change the priority of a rule to 2, the existing rule with priority 2 is changed to priority 3, and the rule with priority 3 is changed to priority 4.
To set the priority of a malware filter rule in PowerShell, use the following syntax:
Set-MalwareFilterRule -Identity "<RuleName>" -Priority <Number>
This example sets the priority of the rule named Marketing Department to 2. All existing rules that have a priority less than or equal to 2 are decreased by 1 (their priority numbers are increased by 1).
Set-MalwareFilterRule -Identity "Marketing Department" -Priority 2
Tip
To set the priority of a new rule when you create it, use the Priority parameter on the New-MalwareFilterRule cmdlet instead.
The default malware filter policy doesn't have a corresponding malware filter rule, and it always has the unmodifiable priority value Lowest.
Use PowerShell to remove malware filter policies
When you use PowerShell to remove a malware filter policy, the corresponding malware filter rule isn't removed.
To remove a malware filter policy in PowerShell, use this syntax:
Remove-MalwareFilterPolicy -Identity "<PolicyName>"
This example removes the malware filter policy named Marketing Department.
Remove-MalwareFilterPolicy -Identity "Marketing Department"
For detailed syntax and parameter information, see Remove-MalwareFilterPolicy.
Use PowerShell to remove malware filter rules
When you use PowerShell to remove a malware filter rule, the corresponding malware filter policy isn't removed.
To remove a malware filter rule in PowerShell, use this syntax:
Remove-MalwareFilterRule -Identity "<PolicyName>"
This example removes the malware filter rule named Marketing Department.
Remove-MalwareFilterRule -Identity "Marketing Department"
For detailed syntax and parameter information, see Remove-MalwareFilterRule.
How do you know these procedures worked?
Use the EICAR.TXT file to verify your anti-malware policy settings
Important
The EICAR.TXT file is not a virus. The European Institute for Computer Antivirus Research (EICAR) developed this file to safely test anti-virus solutions.
Open Notepad and paste the following text into an empty file:
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*Be sure that these characters are the only text in the file. The file size should be 68 bytes.
Save the file as EICAR.TXT
In your desktop anti-virus program, be sure to exclude the EICAR.TXT from scanning (otherwise, the file will be quarantined).
Send an email message that contains the EICAR.TXT file as an attachment, using an email client that won't automatically block the file, and using an email service that doesn't automatically block outbound spam. Use your anti-malware policy settings to determine the following scenarios to test:
- Email from an internal mailbox to an internal recipient.
- Email from an internal mailbox to an external recipient.
- Email from an external mailbox to an internal recipient.
Verify that the message was quarantined, and verify the admin notification results based on your anti-malware policy settings. For example, the admin email address that you specified is notified for internal or external message senders, with the default or customized notification messages.
Delete the EICAR.TXT file after your testing is complete (so other users aren't unnecessarily alarmed by it).