Configure audit policies for Windows event logs
To enhance detections and gather more information on user actions like NTLM logons and security group changes, Microsoft Defender for Identity relies on specific entries in Windows event logs. Proper configuration of Advanced Audit Policy settings on your domain controllers is crucial to avoid gaps in the event logs and incomplete Defender for Identity coverage.
This article describes how to configure your Advanced Audit Policy settings as needed for a Defender for Identity sensor. It also describes other configurations for specific event types.
Defender for Identity generates health issues for each of these scenarios if they're detected. For more information, see Microsoft Defender for Identity health issues.
Prerequisites
- Before you run Defender for Identity PowerShell commands, make sure that you downloaded the Defender for Identity PowerShell module.
Generate a report of current configurations via PowerShell
Before you start creating new event and audit policies, we recommend that you run the following PowerShell command to generate a report of your current domain configurations:
New-MDIConfigurationReport [-Path] <String> [-Mode] <String> [-OpenHtmlReport]
In the preceding command:
Pathspecifies the path to save the reports to.Modespecifies whether you want to useDomainorLocalMachinemode. InDomainmode, the settings are collected from the Group Policy objects (GPOs). InLocalMachinemode, the settings are collected from the local machine.OpenHtmlReportopens the HTML report after the report is generated.
For example, to generate a report and open it in your default browser, run the following command:
New-MDIConfigurationReport -Path "C:\Reports" -Mode Domain -OpenHtmlReport
For more information, see the DefenderforIdentity PowerShell reference.
Tip
The Domain mode report includes only configurations set as group policies on the domain. If you have settings defined locally on your domain controllers, we recommend that you also run the Test-MdiReadiness.ps1 script.
Configure auditing for domain controllers
Update your Advanced Audit Policy settings and extra configurations for specific events and event types, such as users, groups, computers, and more. Audit configurations for domain controllers include:
- Advanced Audit Policy settings
- NTLM auditing
- Domain object auditing
For more information, see Advanced security auditing FAQ.
Use the following procedures to configure auditing on the domain controllers that you're using with Defender for Identity.
Configure Advanced Audit Policy settings from the UI
This procedure describes how to modify your domain controller's Advanced Audit Policy settings as needed for Defender for Identity via the UI.
Related health issue: Directory Services Advanced Auditing is not enabled as required
To configure your Advanced Audit Policy settings:
Sign in to the server as Domain Administrator.
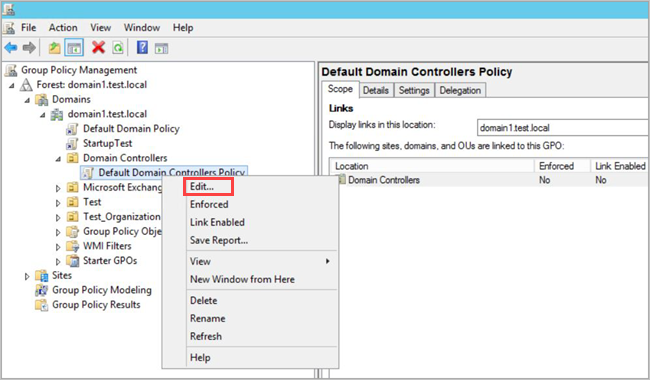
Open the Group Policy Management Editor from Server Manager > Tools > Group Policy Management.
Expand Domain Controllers Organizational Units, right-click Default Domain Controllers Policy, and then select Edit.
Note
Use the Default Domain Controllers policy or a dedicated GPO to set these policies.
In the window that opens, go to Computer Configuration > Policies > Windows Settings > Security Settings. Depending on the policy you want to enable, do the following:
Go to Advanced Audit Policy Configuration > Audit Policies.
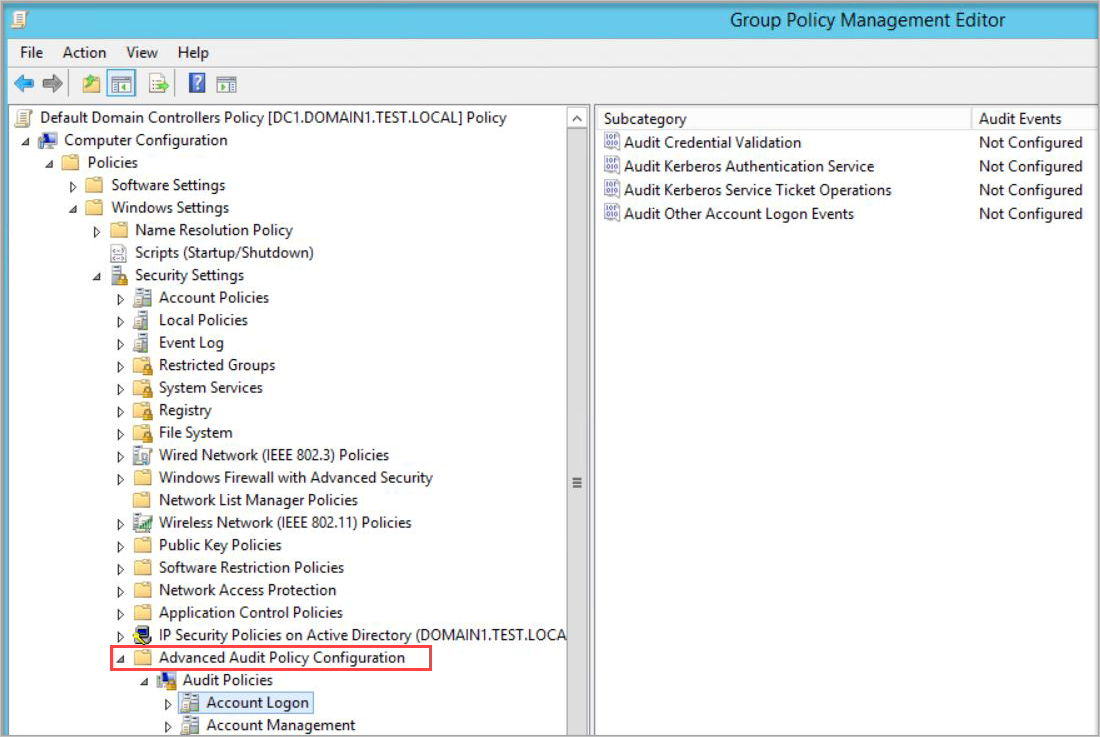
Under Audit Policies, edit each of the following policies and select Configure the following audit events for both Success and Failure events.
Audit policy Subcategory Triggers event IDs Account Logon Audit Credential Validation 4776 Account Management Audit Computer Account Management* 4741, 4743 Account Management Audit Distribution Group Management* 4753, 4763 Account Management Audit Security Group Management* 4728, 4729, 4730, 4732, 4733, 4756, 4757, 4758 Account Management Audit User Account Management 4726 DS Access Audit Directory Service Changes* 5136 System Audit Security System Extension* 7045 DS Access Audit Directory Service Access 4662 - For this event, you must also configure domain object auditing. Note
* Noted subcategories don't support failure events. However, we recommend adding them for auditing purposes in case they're implemented in the future. For more information, see Audit Computer Account Management, Audit Security Group Management, and Audit Security System Extension.
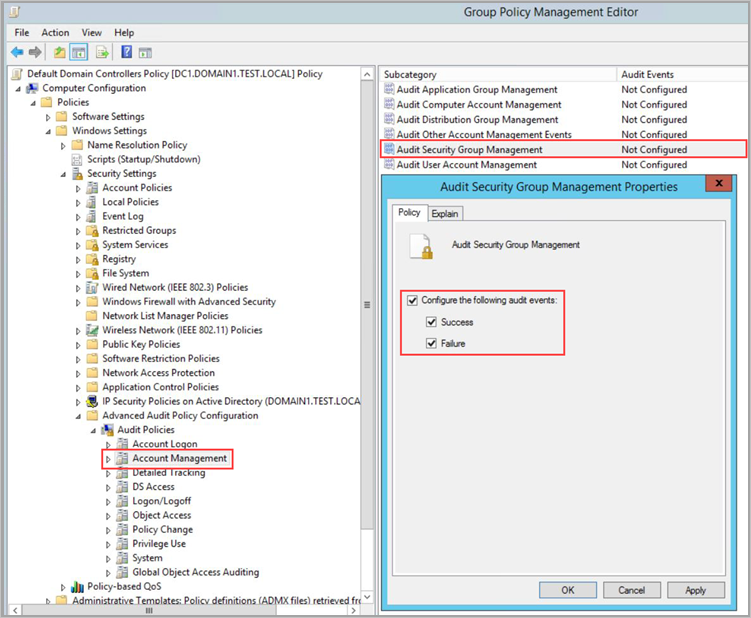
For example, to configure Audit Security Group Management, under Account Management, double-click Audit Security Group Management, and then select Configure the following audit events for both Success and Failure events.
From an elevated command prompt, enter
gpupdate.After you apply the policy via GPO, conform that the new events appear in the Event Viewer, under Windows Logs > Security.
To test your audit policies from the command line, run the following command:
auditpol.exe /get /category:*
For more information, see the auditpol reference documentation.
Configure Advanced Audit Policy settings by using PowerShell
The following actions describe how to modify your domain controller's Advanced Audit Policy settings as needed for Defender for Identity by using PowerShell.
Related health issue: Directory Services Advanced Auditing is not enabled as required
To configure your settings, run:
Set-MDIConfiguration [-Mode] <String> [-Configuration] <String[]> [-CreateGpoDisabled] [-SkipGpoLink] [-Force]
In the preceding command:
Modespecifies whether you want to useDomainorLocalMachinemode. InDomainmode, the settings are collected from the Group Policy objects. InLocalMachinemode, the settings are collected from the local machine.Configurationspecifies which configuration to set. UseAllto set all configurations.CreateGpoDisabledspecifies if the GPOs are created and kept as disabled.SkipGpoLinkspecifies that GPO links aren't created.Forcespecifies that the configuration is set or GPOs are created without validating the current state.
To view your audit policies, use the Get-MDIConfiguration command to show current values:
Get-MDIConfiguration [-Mode] <String> [-Configuration] <String[]>
In the preceding command:
Modespecifies whether you want to useDomainorLocalMachinemode. InDomainmode, the settings are collected from the Group Policy objects. InLocalMachinemode, the settings are collected from the local machine.Configurationspecifies which configuration to get. UseAllto get all configurations.
To test your audit policies, use the Test-MDIConfiguration command to get a true or false response as to whether the values are configured correctly:
Test-MDIConfiguration [-Mode] <String> [-Configuration] <String[]>
In the preceding command:
Modespecifies whether you want to useDomainorLocalMachinemode. InDomainmode, the settings are collected from the Group Policy objects. InLocalMachinemode, the settings are collected from the local machine.Configurationspecifies which configuration to test. UseAllto test all configurations.
For more information, see the following DefenderForIdentity PowerShell references:
Configure NTLM auditing
This section describes the extra configuration steps that you need for auditing Windows event 8004.
Note
- Domain group policies to collect Windows event 8004 should be applied only to domain controllers.
- When a Defender for Identity sensor parses Windows event 8004, Defender for Identity NTLM authentication activities are enriched with the server-accessed data.
Related health issue: NTLM Auditing is not enabled
To configure NTLM auditing:
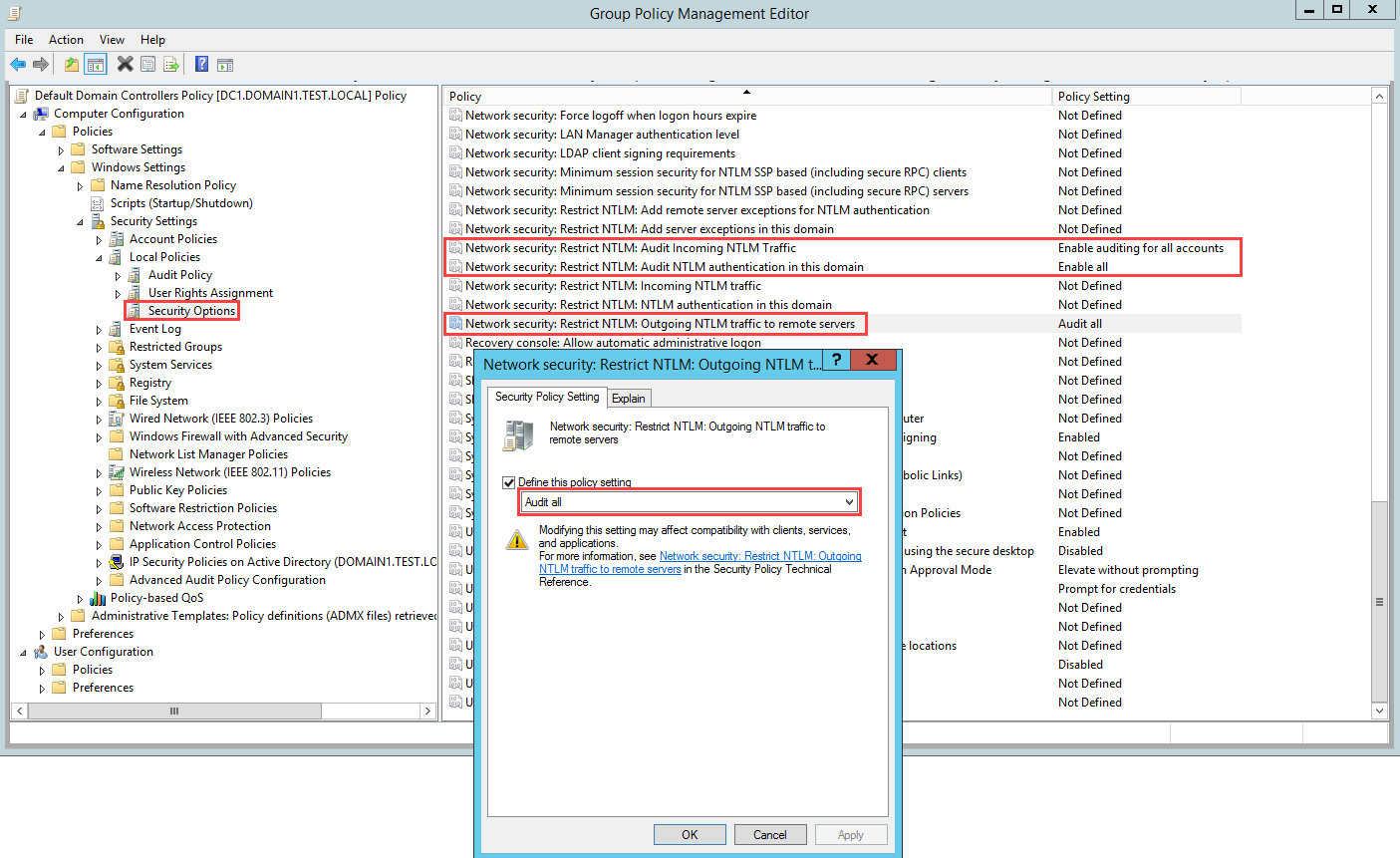
After you configure your initial Advanced Audit Policy settings (via the UI or PowerShell), open Group Policy Management. Then go to Default Domain Controllers Policy > Local Policies > Security Options.
Configure the specified security policies as follows:
Security policy setting Value Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers Audit all Network security: Restrict NTLM: Audit NTLM authentication in this domain Enable all Network security: Restrict NTLM: Audit Incoming NTLM Traffic Enable auditing for all accounts
For example, to configure Outgoing NTLM traffic to remote servers, under Security Options, double-click Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers, and then select Audit all.
Configure domain object auditing
To collect events for object changes, such as for event 4662, you must also configure object auditing on the user, group, computer, and other objects. The following procedure describes how to enable auditing in the Active Directory domain.
Important
Review and audit your policies (via the UI or PowerShell) before you enable event collection, to ensure that the domain controllers are properly configured to record the necessary events. If this auditing is configured properly, it should have a minimal effect on server performance.
Related health issue: Directory Services Object Auditing is not enabled as required
To configure domain object auditing:
Go to the Active Directory Users and Computers console.
Select the domain that you want to audit.
Select the View menu, and then select Advanced Features.
Right-click the domain and select Properties.

Go to the Security tab, and then select Advanced.

In Advanced Security Settings, select the Auditing tab, and then select Add.
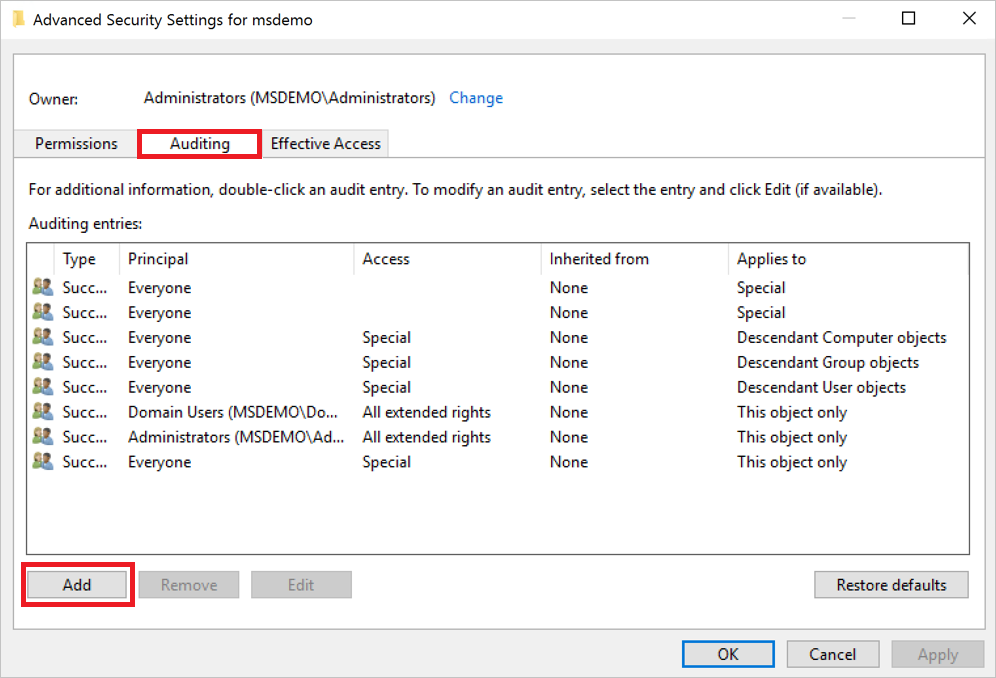
Choose Select a principal.
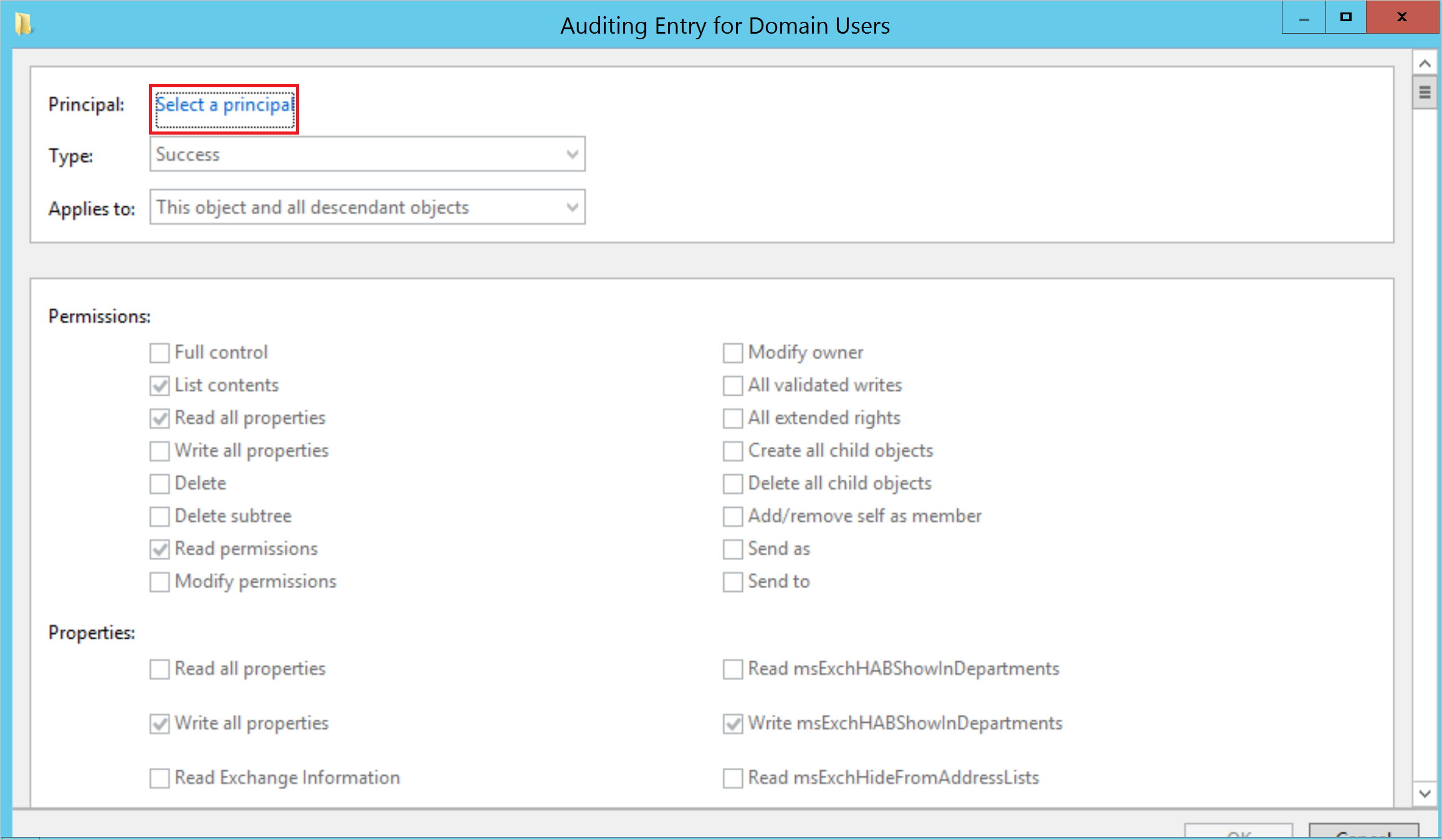
Under Enter the object name to select, enter Everyone. Then select Check Names > OK.
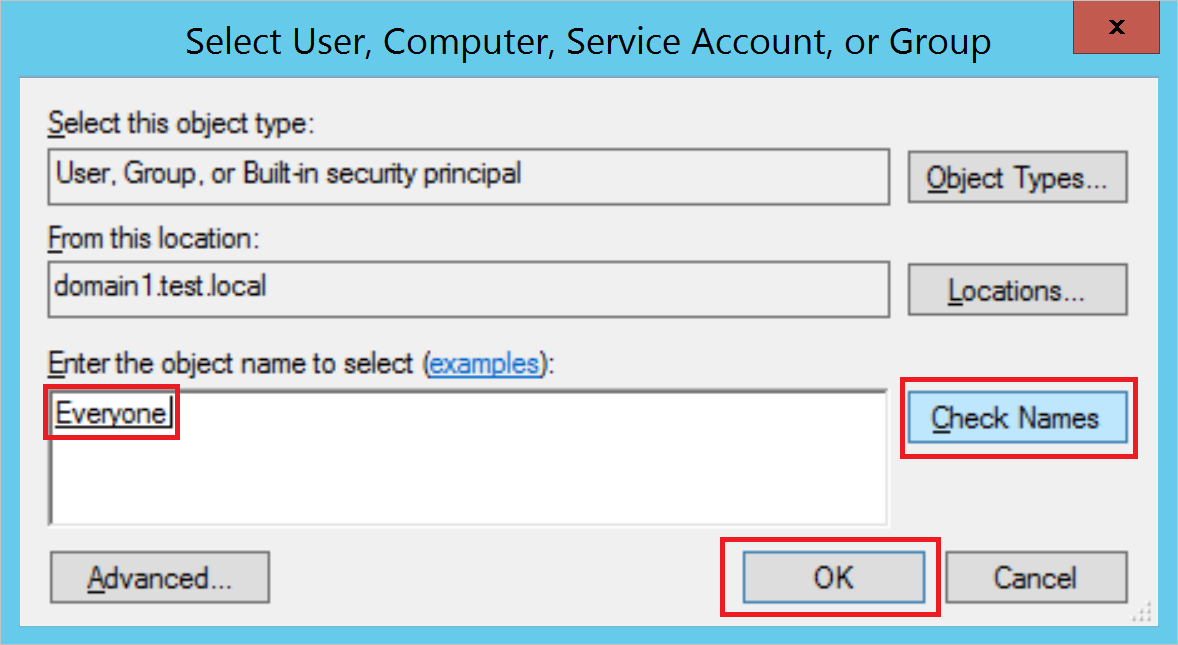
You then return to Auditing Entry. Make the following selections:
For Type, select Success.
For Applies to, select Descendant User objects.
Under Permissions, scroll down and select the Clear all button.
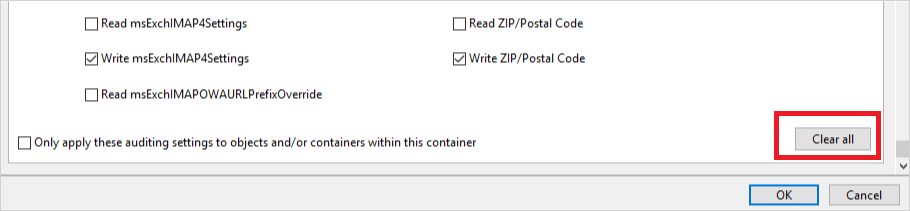
Scroll back up and select Full Control. All the permissions are selected.
Clear the selection for the List contents, Read all properties, and Read permissions permissions, and then select OK. This step sets all the Properties settings to Write.
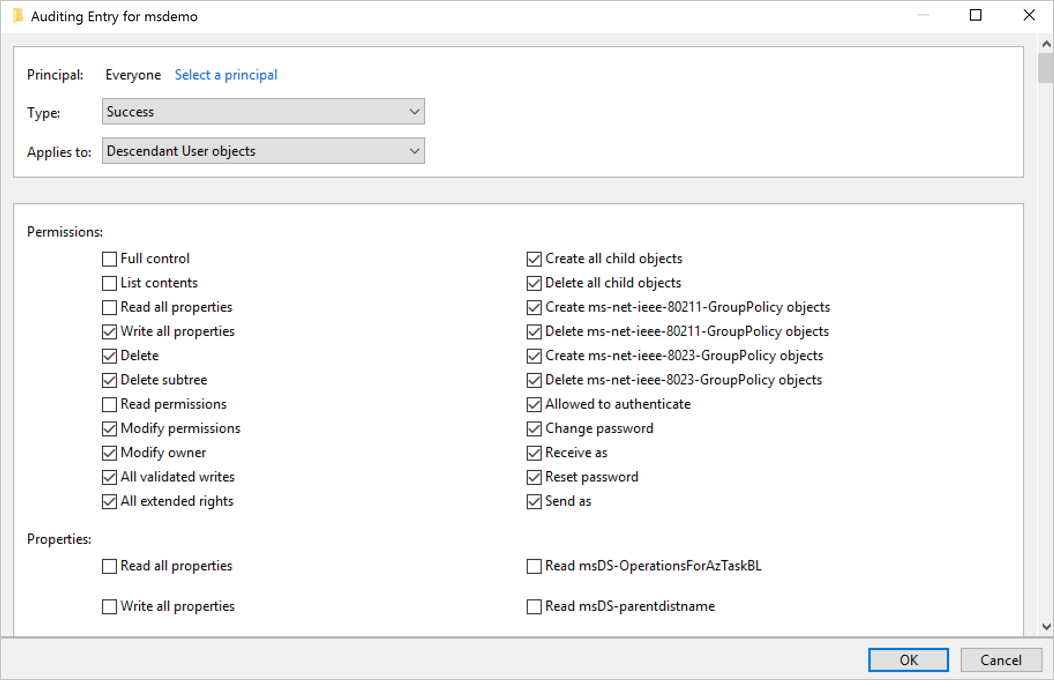
Now, all relevant changes to directory services appear as 4662 events when they're triggered.
Repeat the steps in this procedure, but for Applies to, select the following object types:
- Descendant Group Objects
- Descendant Computer Objects
- Descendant msDS-GroupManagedServiceAccount Objects
- Descendant msDS-ManagedServiceAccount Objects
Note
Assigning the auditing permissions on All descendant objects would also work, but you need only the object types detailed in the last step.
Configure auditing on AD FS
Related health issue: Auditing on the AD FS container is not enabled as required
To configure auditing on Active Directory Federation Services (AD FS):
Go to the Active Directory Users and Computers console, and select the domain where you want to enable the logs.
Go to Program Data > Microsoft > ADFS.
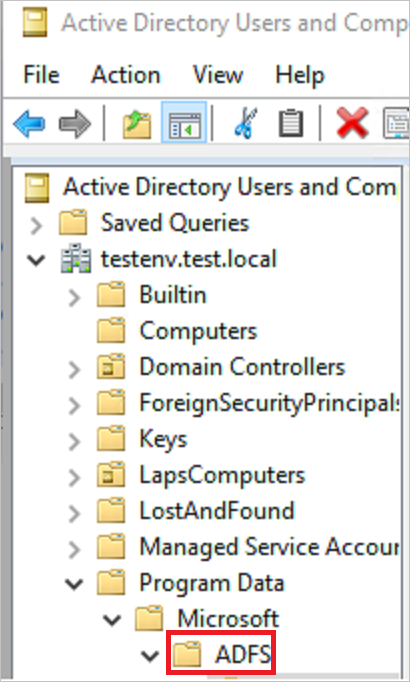
Right-click ADFS and select Properties.
Go to the Security tab and select Advanced > Advanced Security Settings. Then go to the Auditing tab and select Add > Select a principal.
Under Enter the object name to select, enter Everyone. Then select Check Names > OK.
You then return to Auditing Entry. Make the following selections:
- For Type, select All.
- For Applies to, select This object and all descendant objects.
- Under Permissions, scroll down and select Clear all. Scroll up and select Read all properties and Write all properties.
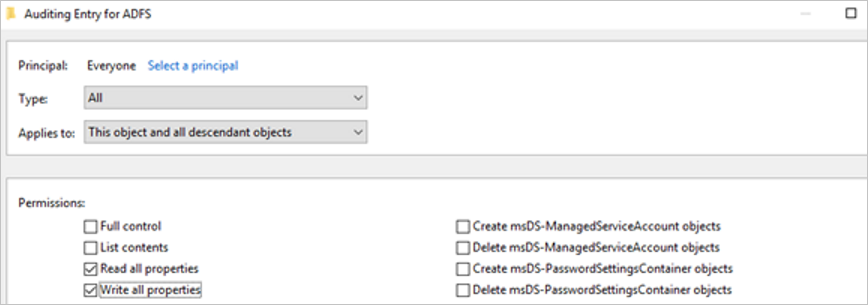
Select OK.
Configure Verbose logging for AD FS events
Sensors running on AD FS servers must have the auditing level set to Verbose for relevant events. For example, use the following command to configure the auditing level to Verbose:
Set-AdfsProperties -AuditLevel Verbose
Configure auditing on AD CS
If you're working with a dedicated server that has Active Directory Certificate Services (AD CS) configured, configure auditing as follows to view dedicated alerts and Secure Score reports:
Create a group policy to apply to your AD CS server. Edit it and configure the following auditing settings:
Go to Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Object Access\Audit Certification Services.
Select the checkboxes to configure audit events for Success and Failure.
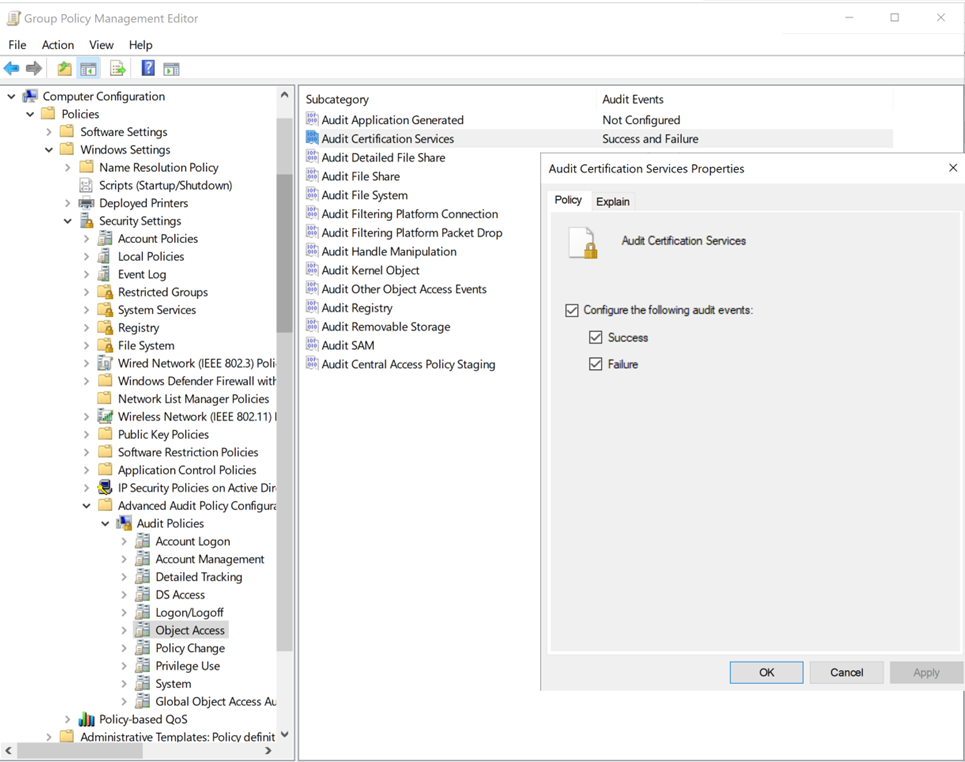
Configure auditing on the certificate authority (CA) by using one of the following methods:
To configure CA auditing by using the command line, run:
certutil –setreg CA\AuditFilter 127 net stop certsvc && net start certsvcTo configure CA auditing by using the GUI:
Select Start > Certification Authority (MMC Desktop application). Right-click your CA's name and select Properties.
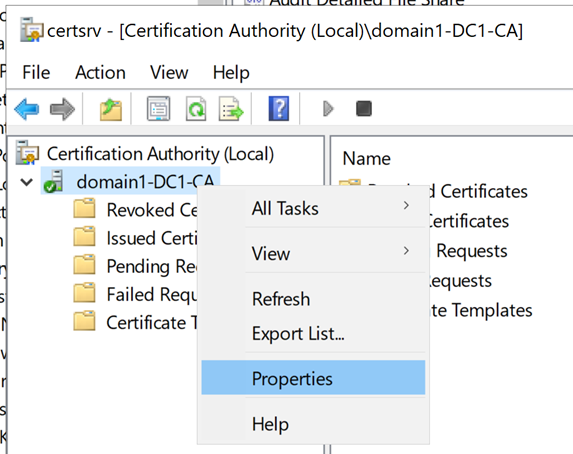
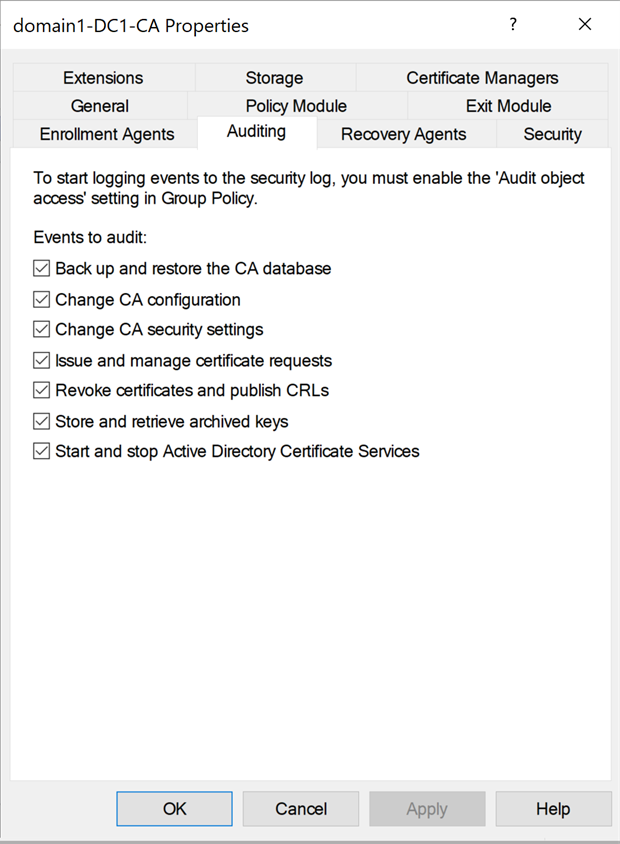
Select the Auditing tab, select all the events that you want to audit, and then select Apply.
Note
Configuring Start and Stop Active Directory Certificate Services event auditing might cause restart delays when you're dealing with a large AD CS database. Consider removing irrelevant entries from the database. Alternatively, refrain from enabling this specific type of event.
Configure auditing on Microsoft Entra Connect
To configure auditing on Microsoft Entra Connect servers:
Create a group policy to apply to your Microsoft Entra Connect servers. Edit it and configure the following auditing settings:
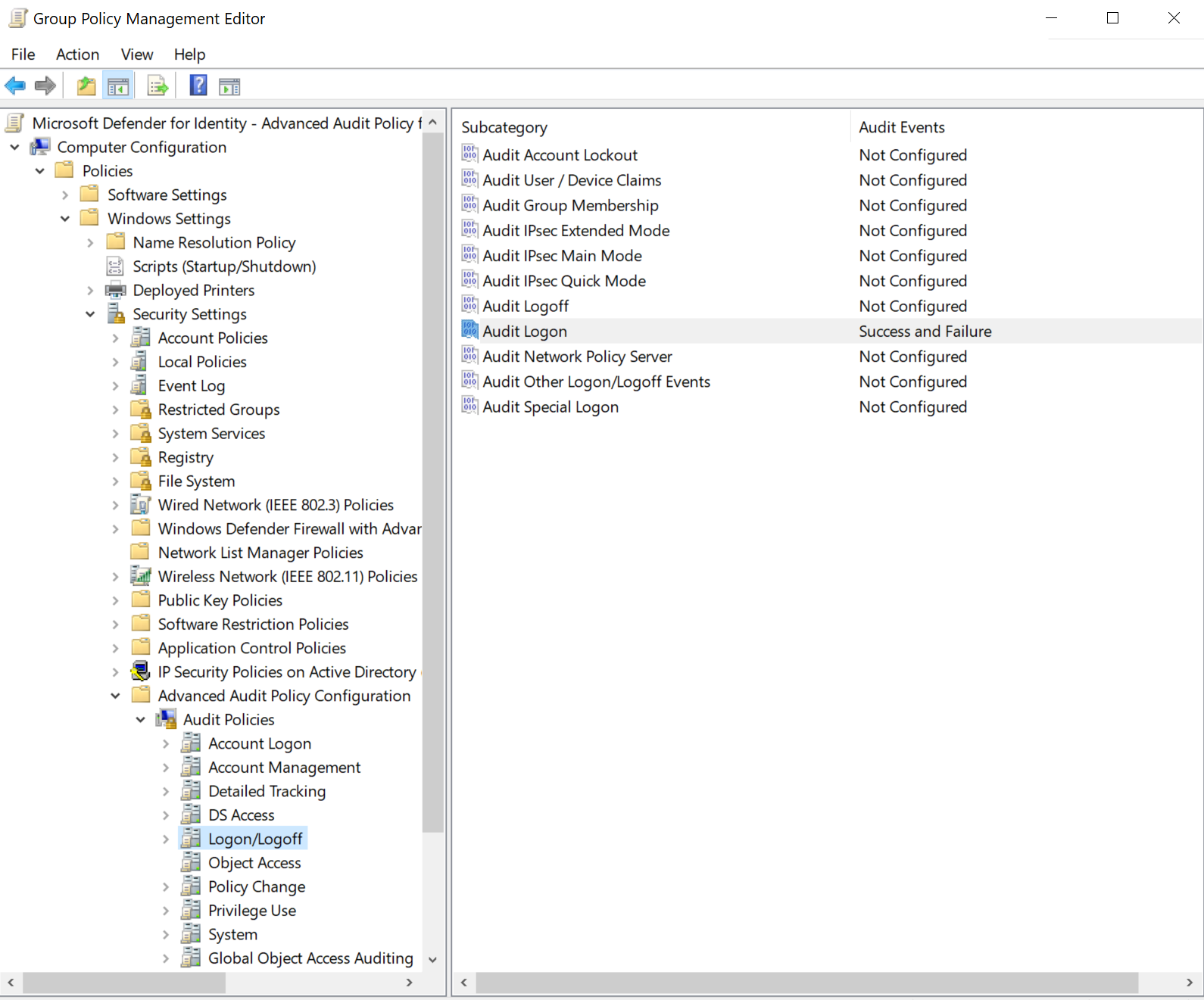
Go to Computer Configuration\Policies\Windows Settings\Security Settings\Advanced Audit Policy Configuration\Audit Policies\Logon/Logoff\Audit Logon.
Select the checkboxes to configure audit events for Success and Failure.
Configure auditing on the configuration container
Note
The configuration container audit is required only for environments that currently have or previously had Microsoft Exchange, as these environments have an Exchange container located within the domain's Configuration section.
Related health issue: Auditing on the Configuration container is not enabled as required
Open the ADSI Edit tool. Select Start > Run, enter
ADSIEdit.msc, and then select OK.On the Action menu, select Connect to.
In the Connection Settings dialog, under Select a well known Naming Context, select Configuration > OK.
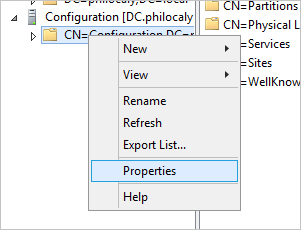
Expand the Configuration container to show the Configuration node, which begins with "CN=Configuration,DC=...".

Right-click the Configuration node and select Properties.
Select the Security tab, and then select Advanced.
In Advanced Security Settings, select the Auditing tab, and then select Add.
Choose Select a principal.
Under Enter the object name to select, enter Everyone. Then select Check Names > OK.
You then return to Auditing Entry. Make the following selections:
- For Type, select All.
- For Applies to, select This object and all descendant objects.
- Under Permissions, scroll down and select Clear all. Scroll up and select Write all properties.
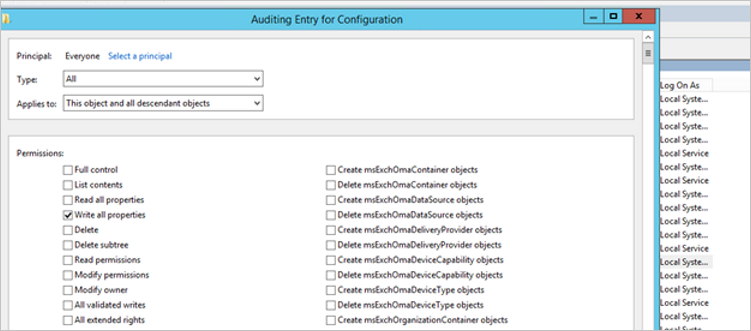
Select OK.
Update legacy configurations
Defender for Identity no longer requires logging 1644 events. If you have either of the following settings enabled, you can remove them from the registry.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostics]
"15 Field Engineering"=dword:00000005
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters]
"Expensive Search Results Threshold"=dword:00000001
"Inefficient Search Results Threshold"=dword:00000001
"Search Time Threshold (msecs)"=dword:00000001
Related content
For more information, see:
- Event collection with Microsoft Defender for Identity
- Windows security auditing
- Advanced security audit policies