Onboard Windows devices using Configuration Manager
Want to experience Defender for Endpoint? Sign up for a free trial.
You can use Configuration Manager to onboard endpoints to the Microsoft Defender for Endpoint service.
There are several options you can use to onboard devices using Configuration Manager:
Note
Defender for Endpoint doesn't support onboarding during the Out-Of-Box Experience (OOBE) phase. Make sure users complete OOBE after running Windows installation or upgrading.
You can create a detection rule on a Configuration Manager application to continuously check if a device has been onboarded. An application is a different type of object than a package and program. If a device is not yet onboarded (due to pending OOBE completion or any other reason), Configuration Manager reattempts to onboard the device until the rule detects the status change. For more information, see Configure Detection Methods in System Center 2012 R2 Configuration Manager.
Prerequisites
See Minimum requirements for Microsoft Defender for Endpoint.
Endpoint Protection point site system role. This role is required so that antivirus and attack surface reduction policies are properly deployed to the targeted endpoints. Without this role, endpoints in the device collection won't receive the configured antivirus and attack surface reduction policies.
Configure sample collection settings
For each device, you can set a configuration value to state whether samples can be collected from the device when a request is made through the Microsoft Defender portal to submit a file for deep analysis.
Note
These configuration settings are typically done through Configuration Manager.
You can set a compliance rule for configuration item in Configuration Manager to change the sample share setting on a device.
This rule should be a remediating compliance rule configuration item that sets the value of a registry key on targeted devices to make sure they're compliant.
The configuration is set through the following registry key entry:
Path: "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection"
Name: "AllowSampleCollection"
Value: 0 or 1
Where Key type is a D-WORD. Possible values are:
- 0: Doesn't allow sample sharing from this device
- 1: Allows sharing of all file types from this device
The default value in case the registry key doesn't exist is 1.
For more information about System Center Configuration Manager Compliance, see Introduction to compliance settings in System Center 2012 R2 Configuration Manager.
Create a collection
To onboard Windows devices with Microsoft Configuration Manager, the deployment can target an existing collection or a new collection can be created for testing.
Onboarding using tools such as Group Policy or a manual method doesn't install any agents on the system.
Within the Microsoft Configuration Manager console, the onboarding process will be configured as part of the compliance settings within the console.
Any system that receives this required configuration maintains that configuration for as long as the Configuration Manager client continues to receive this policy from the management point.
Follow these steps to onboard endpoints using Microsoft Configuration Manager:
In the Microsoft Configuration Manager console, navigate to Assets and Compliance > Overview > Device Collections.
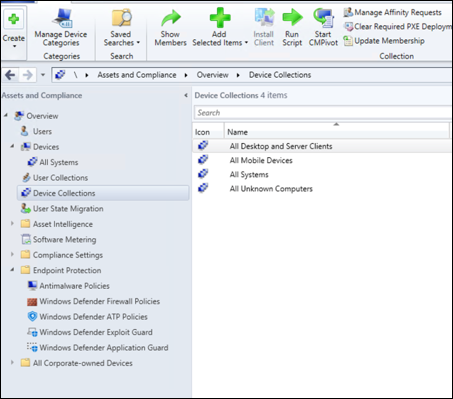
Select and hold (or right-click) Device Collection and select Create Device Collection.

Provide a Name and Limiting Collection, then select Next.
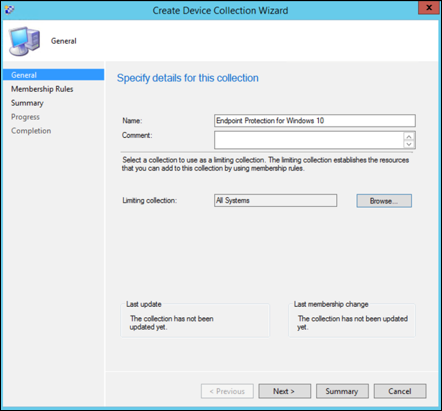
Select Add Rule and choose Query Rule.

Select Next on the Direct Membership Wizard and then select Edit Query Statement.

Select Criteria and then choose the star icon.

Keep criterion type as simple value, choose whereas Operating System - build number, operator as is greater than or equal to and value 14393, and select OK.
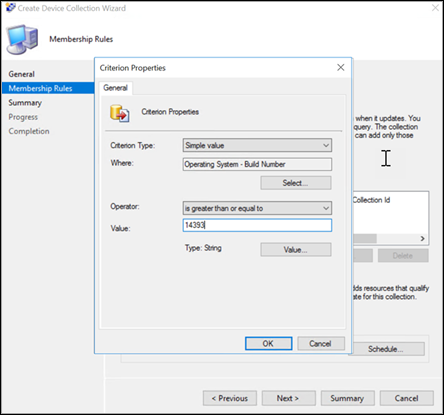
Select Next and Close.

Select Next.
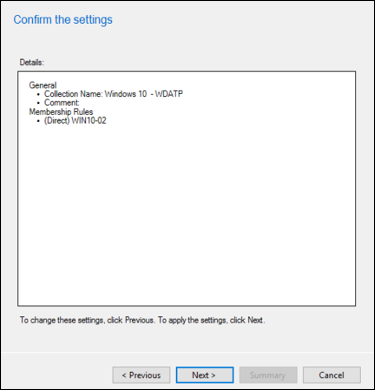
After completing this task you have a device collection with all the Windows endpoints in the environment.
Configure next generation protection
The configuration settings listed in the following table are recommended:
| Setting | Description |
|---|---|
| Scan | Scan removable storage devices such as USB drives: Yes |
| Real-time Protection | Enable Behavioral Monitoring: Yes Enable protection against Potentially Unwanted Applications at download and prior to installation: Yes |
| Cloud Protection Service | Cloud Protection Service membership type: Advanced membership |
| Attack surface reduction | Configure all available rules to Audit. Blocking these activities may interrupt legitimate business processes. The best approach is setting everything to audit, identifying which ones are safe to turn on, and then enabling those settings on endpoints which do not have false positive detections. |
To deploy Microsoft Defender Antivirus and attack surface reduction policies through Microsoft Configuration Manager (SCCM) follow the steps:
- Enable Endpoint Protection and configure custom client settings.
- Install the Endpoint Protection client from a command prompt.
- Verify the Endpoint Protection client installation.
Enable Endpoint Protection and configure custom client settings
Follow the steps to enable endpoint protection and configuration of custom client settings:
In the Configuration Manager console, click Administration.
In the Administration workspace, click Client Settings.
On the Home tab, in the Create group, click Create Custom Client Device Settings.
In the Create Custom Client Device Settings dialog box, provide a name and a description for the group of settings, and then select Endpoint Protection.
Configure the Endpoint Protection client settings that you require. For a full list of Endpoint Protection client settings that you can configure, see the Endpoint Protection section in About client settings.
Important
Install the Endpoint Protection site system role before you configure client settings for Endpoint Protection.
Click OK to close the Create Custom Client Device Settings dialog box. The new client settings are displayed in the Client Settings node of the Administration workspace.
Next, deploy the custom client settings to a collection. Select the custom client settings you want to deploy. In the Home tab, in the Client Settings group, click Deploy.
In the Select Collection dialog box, choose the collection to which you want to deploy the client settings and then click OK.The new deployment is shown in the Deployments tab of the details pane.
Clients are configured with these settings when they next download client policy. For more information, see Initiate policy retrieval for a Configuration Manager client.
Note
For Windows Server 2012 R2 and Windows Server 2016 managed by Configuration Manager 2207 and later versions, onboard using the Microsoft Defender for Endpoint (MDE) Client (recommended) setting. Alternatively, you can use older versions of Configuration Manager to perform a migration. For more information, see Migrating servers from Microsoft Monitoring Agent to the unified solution.
Install the Endpoint Protection client using Command Prompt
Follow the steps to complete installation of endpoint protection client from the command prompt.
Copy scepinstall.exe from the Client folder of the Configuration Manager installation folder to the computer on which you want to install the Endpoint Protection client software.
Open Command Prompt as an administrator. Change directory to the folder with the installer. Then run
scepinstall.exe, adding any extra command-line properties that you require:Property Description /sRun the installer silently /qExtract the setup files silently /iRun the installer normally /policySpecify an antimalware policy file to configure the client during installation /sqmoptinOpt-in to the Microsoft Customer Experience Improvement Program (CEIP) Follow the on-screen instructions to complete the client installation.
If you downloaded the latest update definition package, copy the package to the client computer, and then double-click the definition package to install it.
Note
After the Endpoint Protection client install completes, the client automatically performs a definition update check. If this update check succeeds, you don't have to manually install the latest definition update package.
Example: install the client with an antimalware policy
scepinstall.exe /policy <full path>\<policy file>
Verify the Endpoint Protection client installation
After you install the Endpoint Protection client on your reference computer, verify that the client is working correctly.
On the reference computer, open System Center Endpoint Protection from the Windows notification area.
On the Home tab of the System Center Endpoint Protection dialog box, verify that Real-time protection is set to On.
Verify that up to date is displayed for Virus and spyware definitions.
To make sure that your reference computer is ready for imaging, under Scan options, select Full, and then click Scan now.
Configure network protection
Prior to enabling network protection in audit or block mode, ensure that you've installed the antimalware platform update, which can be obtained from the support page.
Configure controlled folder access
Enable the feature in audit mode for at least 30 days. After this period, review detections and create a list of applications that are allowed to write to protected directories.
For more information, see Evaluate controlled folder access.
Run a detection test to verify onboarding
After onboarding the device, you can choose to run a detection test to verify that a device is properly onboarded to the service. For more information, see Run a detection test on a newly onboarded Microsoft Defender for Endpoint device.
Offboard devices using Configuration Manager
For security reasons, the package used to Offboard devices will expire 7 days after the date it was downloaded. Expired offboarding packages sent to a device will be rejected. When downloading an offboarding package, you will be notified of the packages expiry date and it will also be included in the package name.
Note
Onboarding and offboarding policies must not be deployed on the same device at the same time, otherwise this will cause unpredictable collisions.
Offboard devices using Microsoft Configuration Manager current branch
If you use Microsoft Configuration Manager current branch, see Create an offboarding configuration file.
Offboard devices using System Center 2012 R2 Configuration Manager
Get the offboarding package from Microsoft Defender portal:
- In the navigation pane, select Settings > Endpoints > Device management > Offboarding.
- Select Windows 10 or Windows 11 as the operating system.
- In the Deployment method field, select System Center Configuration Manager 2012/2012 R2/1511/1602.
- Select Download package, and save the .zip file.
Extract the contents of the .zip file to a shared, read-only location that can be accessed by the network administrators who will deploy the package. You should have a file named WindowsDefenderATPOffboardingScript_valid_until_YYYY-MM-DD.cmd.
Deploy the package by following the steps in the Packages and Programs in System Center 2012 R2 Configuration Manager article.
Choose a predefined device collection to deploy the package to.
Important
Offboarding causes the device to stop sending sensor data to the portal but data from the device, including reference to any alerts it has had will be retained for up to 6 months.
Monitor device configuration
If you're using Microsoft Configuration Manager current branch, use the built-in Defender for Endpoint dashboard in the Configuration Manager console. For more information, see Defender for Endpoint - Monitor.
If you're using System Center 2012 R2 Configuration Manager, monitoring consists of two parts:
Confirming the configuration package has been correctly deployed and is running (or has successfully run) on the devices in your network.
Checking that the devices are compliant with the Defender for Endpoint service (this ensures the device can complete the onboarding process and can continue to report data to the service).
Confirm the configuration package has been correctly deployed
In the Configuration Manager console, click Monitoring at the bottom of the navigation pane.
Select Overview and then Deployments.
Select on the deployment with the package name.
Review the status indicators under Completion Statistics and Content Status.
If there are failed deployments (devices with Error, Requirements Not Met, or Failed statuses), you may need to troubleshoot the devices. For more information, see, Troubleshoot Microsoft Defender for Endpoint onboarding issues.

Check that the devices are compliant with the Microsoft Defender for Endpoint service
You can set a compliance rule for configuration item in System Center 2012 R2 Configuration Manager to monitor your deployment.
This rule should be a non-remediating compliance rule configuration item that monitors the value of a registry key on targeted devices.
Monitor the following registry key entry:
Path: "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status"
Name: "OnboardingState"
Value: "1"
For more information, see Introduction to compliance settings in System Center 2012 R2 Configuration Manager.
Related articles
- Onboard servers to Microsoft Defender for Endpoint
- Onboard Windows and Mac client devices to Microsoft Defender for Endpoint
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.