Address oversharing concerns in Microsoft 365 Copilot deployment blueprint
Microsoft 365 Copilot works with different Microsoft services to help you get your data ready for Copilot.
For Copilot administrators, it can be overwhelming to know where to start. Existing administrators can also be unfamiliar with how some features can enhance their data security.
To address the need for shorter, actionable, and prescriptive guidance, you can use this deployment blueprint.
In this deployment blueprint, we provide a recommended approach to address oversharing concerns throughout a Microsoft 365 Copilot deployment.
The blueprint breaks the deployment into three phases:
- Pilot (optional)
- Deploy
- Operate
The blueprint provides:
- An overview of the most common causes of oversharing in Microsoft SharePoint
- A recommended, staged approach to avoid oversharing in a Microsoft 365 Copilot deployment
- Recommended actions specific to E3 or E5 licenses at each stage
- Detailed guidance for using the tools in the SharePoint Admin Center, SharePoint Advanced Management (SAM), and Microsoft Purview to identify and mitigate oversharing and ongoing governance concerns.
Download the blueprint and documentation
| Deployment model | Description |
|---|---|
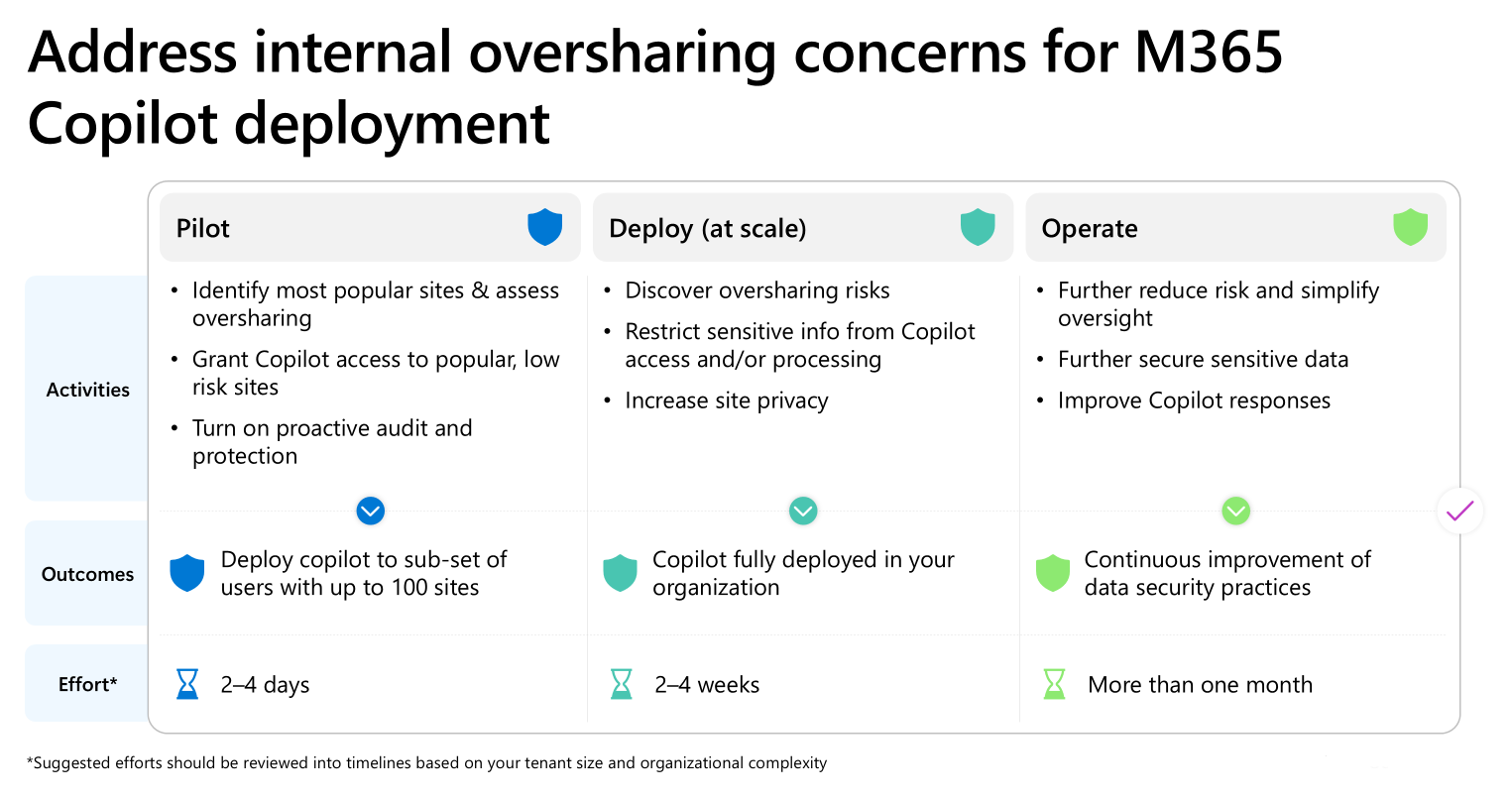 |
Use this deployment model to assist organizations in identifying and mitigating oversharing risks. This model includes
|
Documentation resources
E3 customers – prepare your data for Copilot
Learn how to use the features included in your E3 license to prepare your data for Microsoft 365 Copilot.
E5 customers – prepare your data for Copilot
Learn how to use the features included in your E5 license to prepare your data for Microsoft 365 Copilot.