Sensitivity labels and security classification metadata requirements for Australian Government compliance with PSPF
This article provides guidance for Australian Government organizations on Microsoft Purview sensitivity labeling and label metadata alignment with requirements outlined in the Protective Security Policy Framework (PSPF) and Australian Government Recordkeeping Metadata standard (AGRkMS).
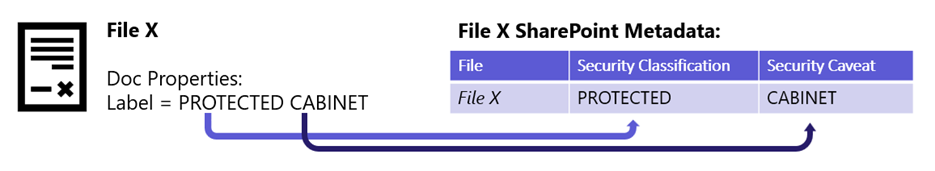
AGRkMS lists optional metadata properties that are configured in systems to align with security markings. These properties are a lower priority by government organizations starting their compliance journey. However, metadata management is an important part of mature records management and includes organizations who are seeking to meet their records requirements via in-place records management in Microsoft 365.
Properties included in AGRkMS that government organizations should index are:
- Security Classification, and
- Security Caveat.
As mentioned in SharePoint Location and Item Sensitivity, information on the sensitivity labels applied to items is indexed by SharePoint in a Sensitivity column. The sensitivity labels present in this column includes either the protective marking, Dissemination Limiting Marker (DLM), or security classification along with any applied Information Management Markers (IMM) or Caveats.
The Australian Government Recordkeeping Metadata Standard should be consulted when planning configurations. The stated intent of these requirements can be met natively in the Microsoft Purview solution using this guide.
Organizations wanting to implement processes to reindex classification and caveat metadata to populate fields that fully align with the AGRkMS standard can do so via a process that populates managed properties, based on existing label properties.
Due to the intent of these requirements already being met by the platform, the configuration to index extra metadata hasn't been included in this guide.
Compliance boundaries
AGRkMS requirements refer to one of the uses of Security Classification and Security Caveat metadata as to prevent discovery of the nature of the information or activity covered by particular security compartments. To put this into context, consider the risk of highly sensitive or security classified information being surfaced and inappropriately disclosed through a reporting process.
Compliance boundaries are established to create logical boundaries within a Microsoft 365 environment. These boundaries are based on user properties such as user department attributes or based on SharePoint site properties. Compliance boundaries limit the search activities of eDiscovery administrators to allocated scopes.
A typical use of compliance boundaries is to establish organisation-based boundaries for use within multitenant environments. This use case is useful to Australian Government organizations subject to Machinery of Government (MoG) changes.
In order to help protect security classified or caveated information from unintended disclosure, compliance boundaries are established to restrict eDiscovery manager's ability to search security classified locations. To achieve this, compliance security filters are established based on SharePoint managed properties for sensitivity label.
Note
For security classification-based compliance boundaries to be effective, sensitivity labels are applied to all relevant locations.