Data Loss Prevention (DLP) scenarios for Australian Government compliance with PSPF
This article provides an overview on the use of Microsoft Purview Data Loss Prevention (DLP) for the the marking and protection of Australian Government information. Its purpose is to help government organizations to increase their security and compliance maturity while adhering with requirements outlined in the Protective Security Policy Framework (PSPF) and Information Security Manual (ISM).
Data Loss Prevention (DLP) is a service primarily used to reduce information risk by helping to prevent sensitive information from leaving an environment. DLP policies can be configured based on:
- A location or service: For example, SharePoint or Exchange.
- A condition or set of conditions: For example, contains a label or sensitive information.
- An action: For example, block transmission or sharing of the item.
Readers should review this information before exploring the advice provided here that relates more specifically to configuration for Australian government organizations.
DLP use cases relevant to government requirements
Within the context of Australian Government requirements, the Microsoft Purview DLP service is used to:
- To apply required metadata to email (x-protective-marking x-headers).
- To apply subject markings to email.
- To block transmission of inappropriately labeled email.
- To block transmission or prevent inappropriate distribution of security classified information.
- To block or warn against email distribution or sharing of items to users who don’t have need-to-know.
- To implement operational controls to prevent loss of information that could result in damage to an individual, organization, or government.
DLP strategy
The Protective Security Policy Framework (PSPF) is a framework that assists Australian Government organizations to protect their people, information, and assets. PSPF policies most relevant to DLP configuration are PSPF Policy 8: Classification system and PSPF Policy 9: Access to information.
Australian Government organizational nuances that affect the DLP strategy include:
- Organizational specific legislative instruments.
- Type of Australian Government Body and associated legislative requirements.
- Other frequently contacted organizations.
- The organization's tenants and maximum level of security for each tenant.
- Non-Australian Public Servant (APS), guest, and contractor requirements.
The following sections are relevant to DLP approach across all DLP integrated services. Government organizations should decide on their strategy for user feedback and the management of DLP events. Strategies decided on can then be applied across DLP configurations further explored in:
- Preventing inappropriate distribution of security classified information
- Preventing inappropriate distribution of sensitive information
- Preventing data spillage via receipt of inappropriate classifications
Decisions regarding user feedback for DLP policy violation
Providing that organizations align with the advice provided in this guide, when a user attempts to send information, there are four reasons why a DLP policy is triggered:
- The user has the wrong recipient for their email (accidental).
- The configuration is incorrect, and another domain needs to be added to the exception list.
- The external organization in question could be appropriate for receiving the information but the business process to establish formal agreements and associated configuration is yet to be completed.
- The user is attempting to exfiltrate classified information (malicious).
When DLP policies are triggered due to action aligning with one of the first three scenarios, feedback to the user is valuable. Feedback allows the user to correct their mistake, your organization to fix the configuration, or to enact the required business process. If the policy is triggered due to malicious activities, then user feedback alerts the user that their action was noticed. Organizations need to consider the risk versus benefit of user feedback and decide on the best approach for their situation.
DLP policy tips ahead of violation
If opting to provide user feedback, policy tips are a great way of helping users as they trigger directly in Outlook clients. They alert users to issues before sending an email and triggering a policy violation, potentially avoiding discipline, or an embarrassing situation. Policy tips are configured via the policy tips option in DLP rule configuration. When applied to email scenarios, the end user experience of this configuration is that they receive a warning tip at the top of the email that they're drafting:
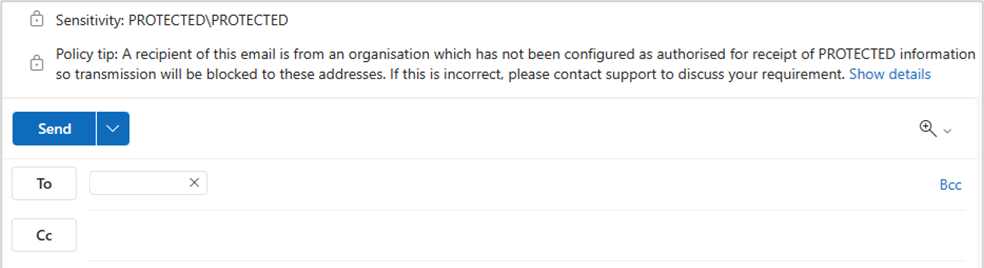
When users ignore the policy tip, other DLP policy actions trigger, such as a block action. A range of notification options are also available, including notifications that display in real-time, advising the user that their email was blocked.
The benefit of policy tips to DLP event workload should also be considered. DLP risk events are reduced with the use of policy tips, before a block action and associated alerting being triggered. The benefit is security teams have fewer incidents to manage.
For more information about DLP notifications and policy tips, see send email notifications and show policy tips for DLP policies.
DLP event management
Organizations implementing DLP should consider their approach to the management of DLP events, including:
- What tool to use for the management of DLP events?
- What DLP event severities warrant administrator action and what is the desired time to resolution?
- Which team is responsible for the management of DLP events (for example, security, data, or privacy teams)?
- What resourcing is required?
There are four Microsoft solutions available to assist with the monitoring and management of DLP events:
- Microsoft Defender XDR
- DLP alerts dashboard
- Activity explorer
- Microsoft Sentinel
Microsoft Defender XDR
Microsoft Defender XDR is a comprehensive security solution that provides cross-domain threat protection and response across endpoints, email, identities, cloud apps, and infrastructure. It offers simplified and efficient defense against advanced attacks by providing security teams with a complete view of the threat landscape, enabling more effective investigations and automated remediation. Microsoft Defender XDR is the recommended method for DLP incident management within Microsoft 365.
For more information on DLP incident management with Microsoft Defender XDR, see investigate data loss prevention alerts with Microsoft Defender XDR.
DLP alerts dashboard
The Microsoft Purview alerts dashboard is visible from within the Microsoft Purview compliance portal. The dashboard provides administrators with visibility of DLP incidents. For information on how to configure alerts in your DLP policies and use the DLP alert management dashboard, see getting started with DLP alerts dashboard.
Activity explorer
Activity Explorer is a dashboard available from within the Microsoft Purview compliance portal and offers a different view into DLP events. This tool is intended not for the management of events but instead to provide administrators with deeper insights and wider filters, and longitudinal behavior. For more information on Activity Explorer, see Activity Explorer.
Microsoft Sentinel
Microsoft Sentinel is a scalable, cloud-native security information and event management (SIEM) that delivers an intelligent and comprehensive solution for SIEM and security orchestration, automation, and response (SOAR). Connectors can be configured to import DLP incident information from Microsoft Defender XDR into Microsoft Sentinel. Establishing this connectivity allows for more Sentinel's more advanced investigation and automation capabilities to be utilized for DLP incident management. For more information on using Sentinel for DLP event management, see investigate data loss prevention alerts with Microsoft Sentinel.