Achieve ACSC Essential Eight MFA Maturity Level 3 with Microsoft Entra
MFA Maturity Level 3 ACSC definition
- Multifactor authentication is used to authenticate users to their organization’s online services that process, store, or communicate their organization’s sensitive data.
- Multifactor authentication is used to authenticate users to third-party online services that process, store, or communicate their organization’s sensitive data.
- Multifactor authentication (where available) is used to authenticate users to third-party online services that process, store, or communicate their organization’s non-sensitive data.
- Multifactor authentication is used to authenticate users to their organization’s online customer services that process, store, or communicate their organization’s sensitive customer data.
- Multifactor authentication is used to authenticate users to third-party online customer services that process, store, or communicate their organization’s sensitive customer data.
- Multifactor authentication is used to authenticate privileged users of systems.
- Multifactor authentication is used to authenticate unprivileged users of systems.
- Multifactor authentication is used to authenticate users of data repositories.
- Multifactor authentication uses either: something users have and something users know, or something users have that is unlocked by something users know or are.
- Multifactor authentication used for authenticating users of online services is phishing-resistant.
- Multifactor authentication used for authenticating users of systems is phishing-resistant.
- Multifactor authentication used for authenticating users of data repositories is phishing-resistant.
- Successful and unsuccessful multifactor authentication events are centrally logged.
- Event logs are protected from unauthorized modification and deletion.
Out of scope
Customer services
The following ACSC requirements for maturity level 2 are related to customer identities and are out of scope for this guide on Microsoft Entra.
- Multifactor authentication is used to authenticate customers to online customer services that process, store, or communicate sensitive customer data.
- Multifactor authentication used for authenticating customers of online customer services is phishing-resistant.
Organization processes
The following ACSC requirements for maturity level 2 are organization processes and are out of scope for this guide on Microsoft Entra workforce identities.
- Event logs from internet-facing servers are analyzed in a timely manner to detect cyber security events.
- Event logs from non-internet-facing servers are analyzed in a timely manner to detect cyber security events.
- Event logs from workstations are analyzed in a timely manner to detect cyber security events.
- Cyber security events are analyzed in a timely manner to identify cyber security incidents.
- Cyber security incidents are reported to the Chief Information Security Officer, or one of their delegates, as soon as possible after they occur or are discovered.
- Cyber security incidents are reported to ASD as soon as possible after they occur or are discovered.
- Following the identification of a cyber security incident, the cyber security incident response plan is enacted.
MFA Maturity Level 3 overview
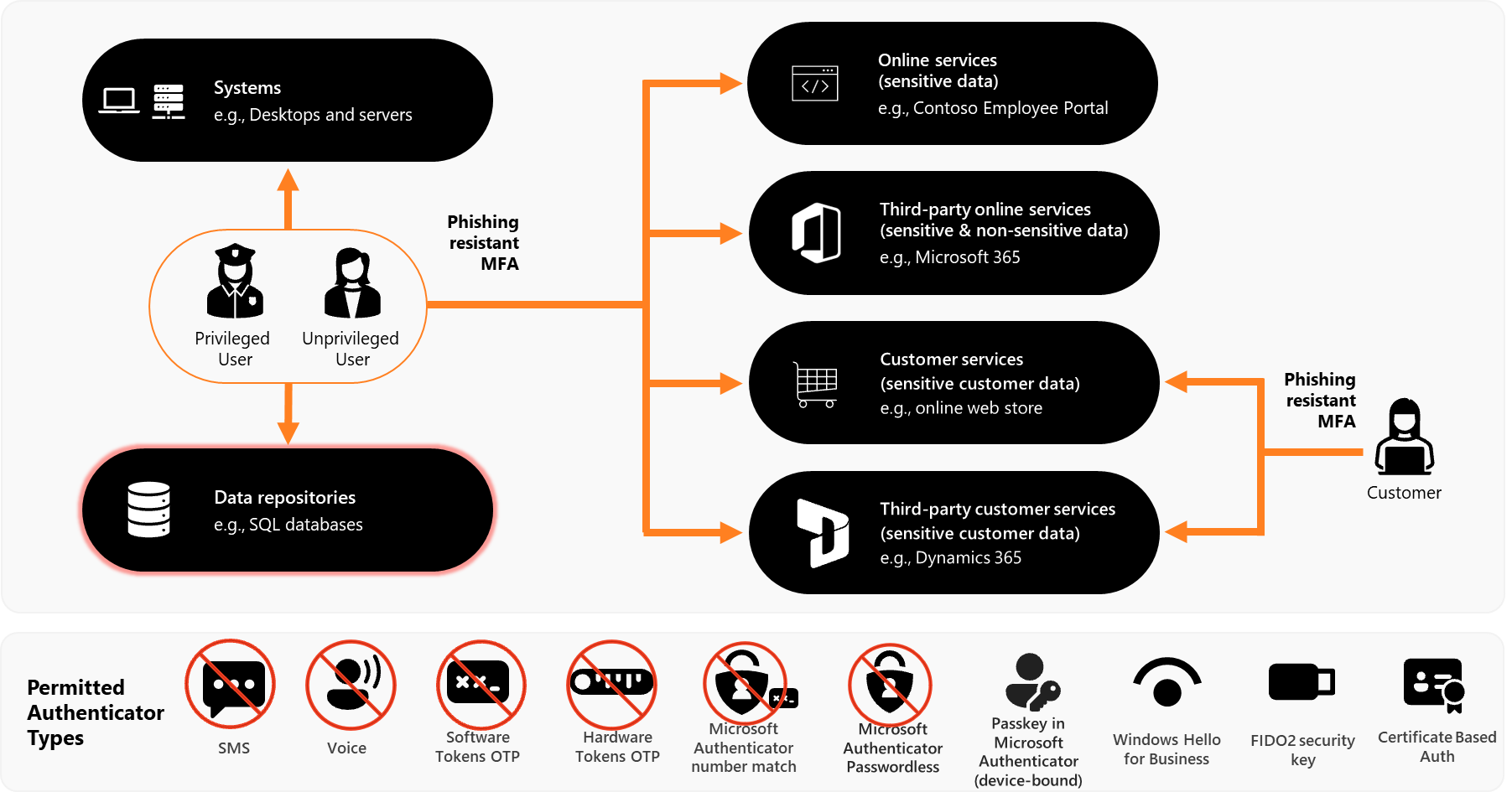
Permitted authenticator types
Any ISM permitted phishing resistant multi-factor authenticator can be used to achieve maturity level 3.
| Microsoft Entra authentication methods | Authenticator type |
|---|---|
-> -> -> |
Multi-factor crypto hardware |
Our recommendations
For guidance on passwordless authentication that eliminates the greatest attack surface, the password, see Plan a passwordless authentication deployment in Microsoft Entra.
For more information on implementing Windows Hello for Business, see the Windows Hello for Business deployment guide.
Microsoft Entra authentication methods not permitted by Maturity Level 3
- SMS Sign in
- Email OTP
- Microsoft Authenticator app (Phone sign in)
- Password plus Phone (SMS)
- Password plus Phone (Voice call)
- Password plus Email OTP
- Password plus Microsoft Authenticator app (OTP)
- Password plus single-factor OTP
- Password plus Microsoft Entra joined with software TPM
- Password plus Compliant mobile device
- Password plus Microsoft Entra hybrid joined with software TPM
- Password plus Microsoft Authenticator App (Notification)
- Password plus Microsoft Entra joined with hardware TPM
- Password plus Microsoft Entra hybrid joined with hardware TPM
Phishing resistant multifactor authentication for guests
Microsoft Entra ID doesn't support guests registering for phishing resistant multifactor authentication options in the resource tenant.
To enforce phishing resistant multifactor authentication for guests in your tenant, cross-tenant access must be configured to enable inbound trust for MFA.
Inbound trust for MFA allows guests to perform phishing resistant multifactor authentication in their home tenant and satisfy the conditional access policy requirement for phishing resistant authentication in your tenant.
To learn more, see Configure cross-tenant access settings for B2B collaboration - change inbound trust settings for MFA and device claims.
Multifactor authentication for systems (desktops and servers)
See Multifactor authentication for access to desktops and servers.
Integrate organization and third party apps with Microsoft Entra ID
To integrate organization apps your developers build, with Microsoft Entra ID, see Integrate apps your developers build.
To integrate third party apps with Microsoft Entra ID, see Five steps to integrate your apps with Microsoft Entra ID.
Next steps
- Configure Essential Eight MFA authentication methods
- Configure Essential Eight MFA authentication strengths
- Configure Essential Eight MFA conditional access policies
- Configure Essential Eight MFA logging
- Phishing resistant multifactor authentication for access to desktops, servers, and data repositories