Achieve ACSC Essential Eight MFA Maturity Level 1 with Microsoft Entra
MFA Maturity Level 1 ACSC definition
- Multifactor authentication is used to authenticate users to their organization’s online services that process, store, or communicate their organization’s sensitive data.
- Multifactor authentication is used to authenticate users to third-party online services that process, store, or communicate their organization’s sensitive data.
- Multifactor authentication (where available) is used to authenticate users to third-party online services that process, store, or communicate their organization’s non-sensitive data.
- Multifactor authentication uses either: something users have and something users know, or something users have that is unlocked by something users know or are.
Out of scope
The following ACSC requirements for maturity level 1 are related to customer identities and are out of scope for this guide on Microsoft Entra for workforce identities.
- Multifactor authentication is used to authenticate users to third-party online customer services that process, store, or communicate their organization’s sensitive customer data.
- Multifactor authentication is used to authenticate customers to online customer services that process, store, or communicate sensitive customer data.
MFA Maturity Level 1 overview
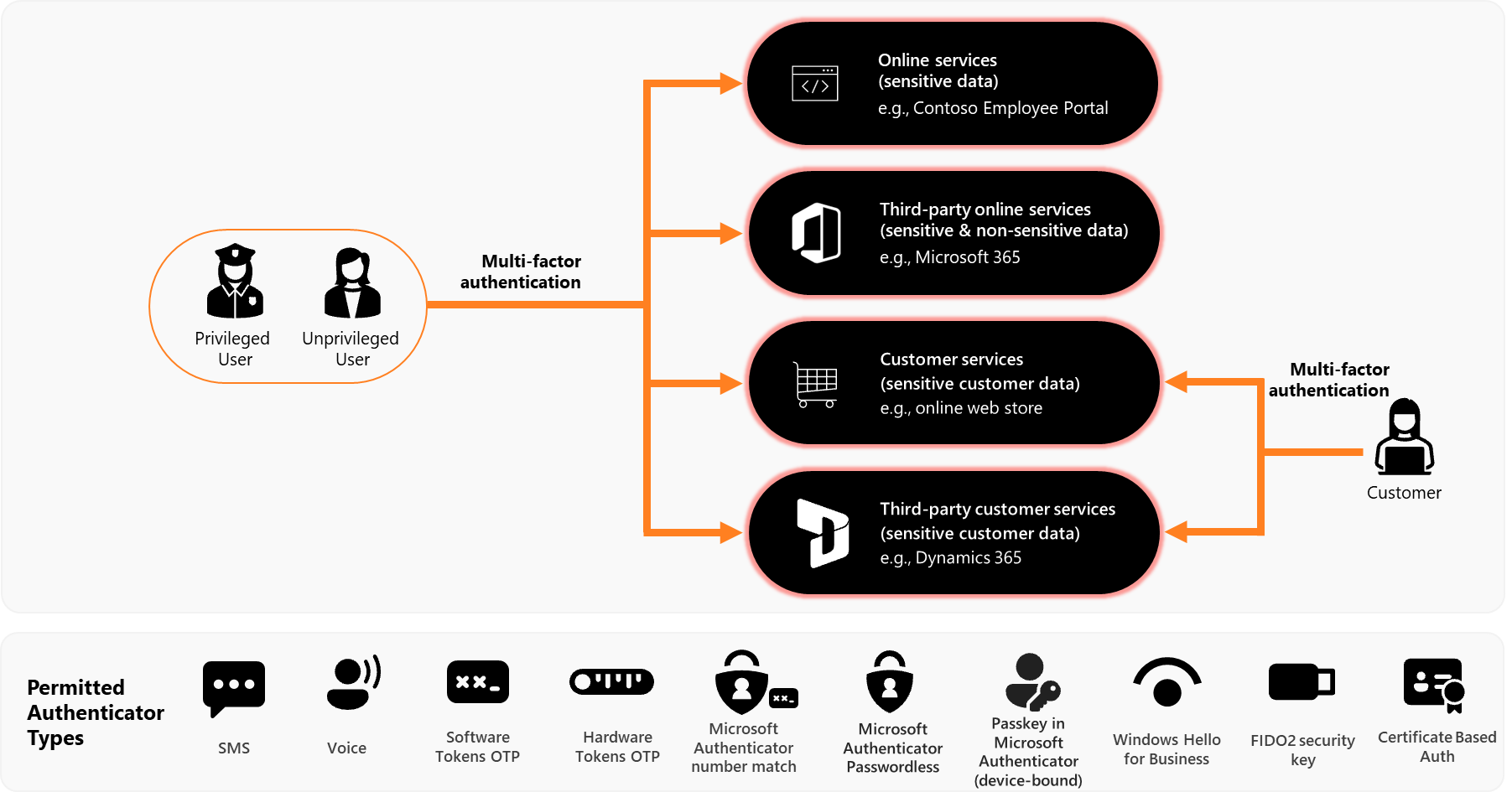
- Users include all users that have access to an organization’s data. These users can be employees, contractors, and guests from partner organizations.
- Users should be prompted for MFA regardless of the location they sign in from.
- Conditional access policies that implement MFA shouldn't have exclusions based on the location of the user. (for example, excluding MFA for users signing in from the corporate local area network).
Permitted authenticator types
Any ISM permitted multi-factor authenticator can be used to achieve maturity level 1.
| Microsoft Entra authentication method | Authenticator type |
|---|---|
| Recommended methods | |
| Multi-factor crypto software | |
-> -> -> |
Multi-factor crypto hardware |
| Multi-factor out-of-band | |
| Additional methods | |
| Password AND - Microsoft Authenticator app (Push Notification) - OR - Phone (SMS) |
Memorized secret AND Single-factor out-of-band |
| Password AND - OATH hardware tokens (preview) - OR - Microsoft Authenticator app (OTP) - OR - OATH software tokens |
Memorized secret AND Single-factor OTP |
| Password AND - Single-factor software certificate - OR - Microsoft Entra joined with software TPM - OR - Microsoft Entra hybrid joined with software TPM - OR - Compliant mobile device |
Memorized secret AND Single-factor crypto software |
| Password AND - Microsoft Entra joined with hardware TPM - OR - Microsoft Entra hybrid joined with hardware TPM |
Memorized secret AND Single-factor crypto hardware |
Microsoft Entra authentication methods not permitted by Maturity Level 1
- SMS Sign in
- Email OTP
Integrate organization and third party apps with Microsoft Entra ID
To integrate organization apps your developers build, with Microsoft Entra ID, see.
To integrate third party apps with Microsoft Entra ID, see.