Gather important Virtual Machine (VM) console data
The article provides generic guidance on how to collect data necessary for diagnosing VM console-related issues.
Prerequisites to complete these procedures
In order to ssh to a virtual machine, you must have:
- Created a
Private endpointconnecting to the Cluster Manager'sPrivate link service - Virtual machine instance with a given name
- Created the corresponding Console with same name used for the virtual machine
Data collection
Data needed by the VM Console service team for troubleshooting
If there's a problem that needs to further investigation by the VM Console service team, collect the following information to help them get started:
- A detailed description of the problem and its effect to the end user.
- Screenshots. The Azure portal is obviously a visual component. Try to get as much visual data as possible to describe the problem happening. Screenshots are often the best way to show the problem or how to reproduce the problem.
- Private Endpoint IP
- Private Endpoint connectivity
- Collecting Console Data
Determine the private endpoint connectivity
- Navigate to the Azure portal where customer's work environment is located.
- Select the Private endpoint resource used for
sshto the virtual machine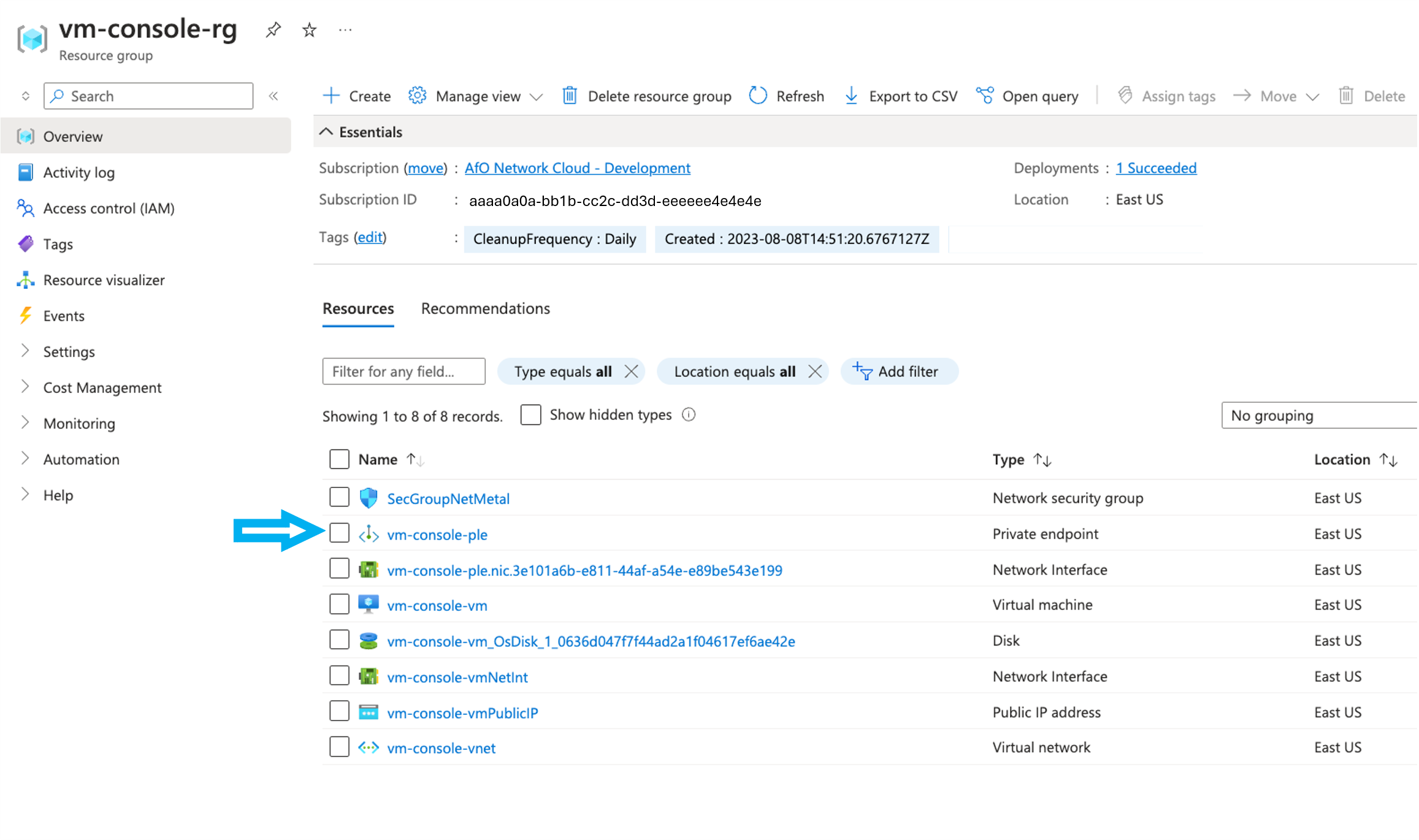
- In the Private endpoint screen, select the
Private link resource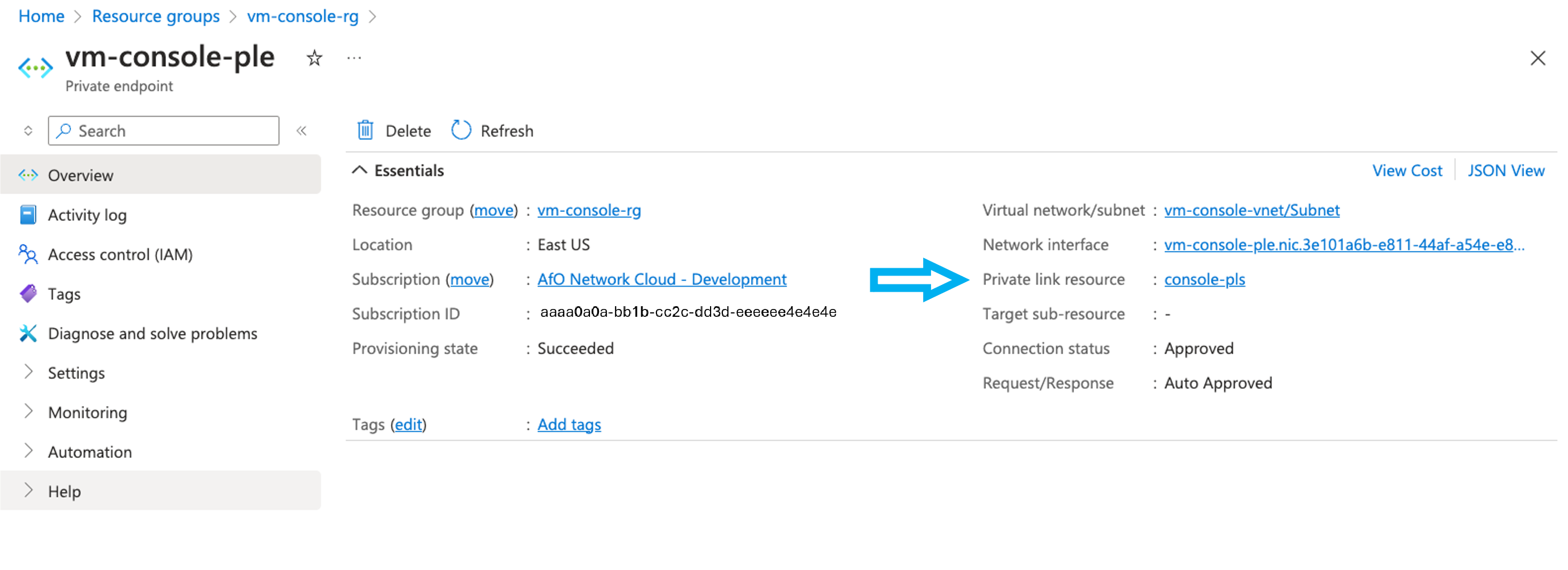
- Capture screenshot of
Private link resourcescreen. - Confirm with the customer that
Private endpointis referencing the correctPrivate Link Service, as it's possible that customer might be using the wrong PLE when trying tosshto a virtual machine.
Determine the private endpoint IP address
- Navigate to the Azure portal where customer's work environment is located.
- Select the Private endpoint resource used for
sshto the virtual machine
- In the Private endpoint screen, select the
Network interface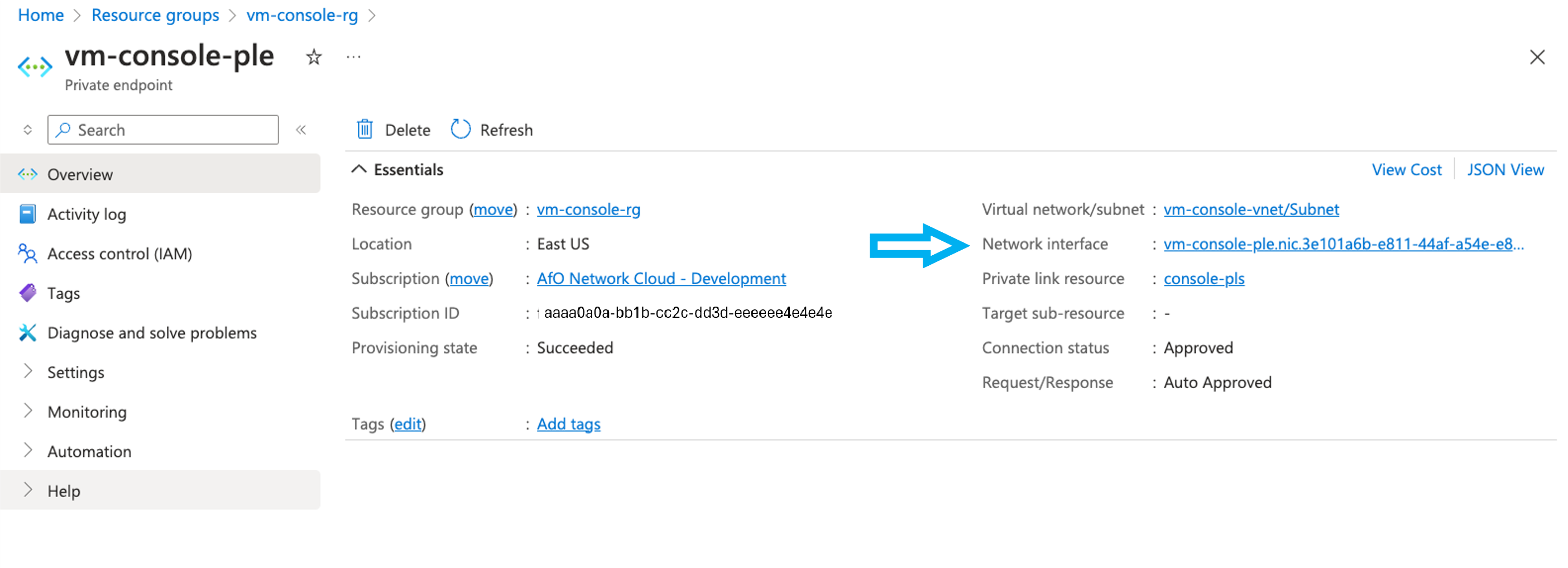
- In that screen, you find the
Private IPv4 address, for example,10.1.0.5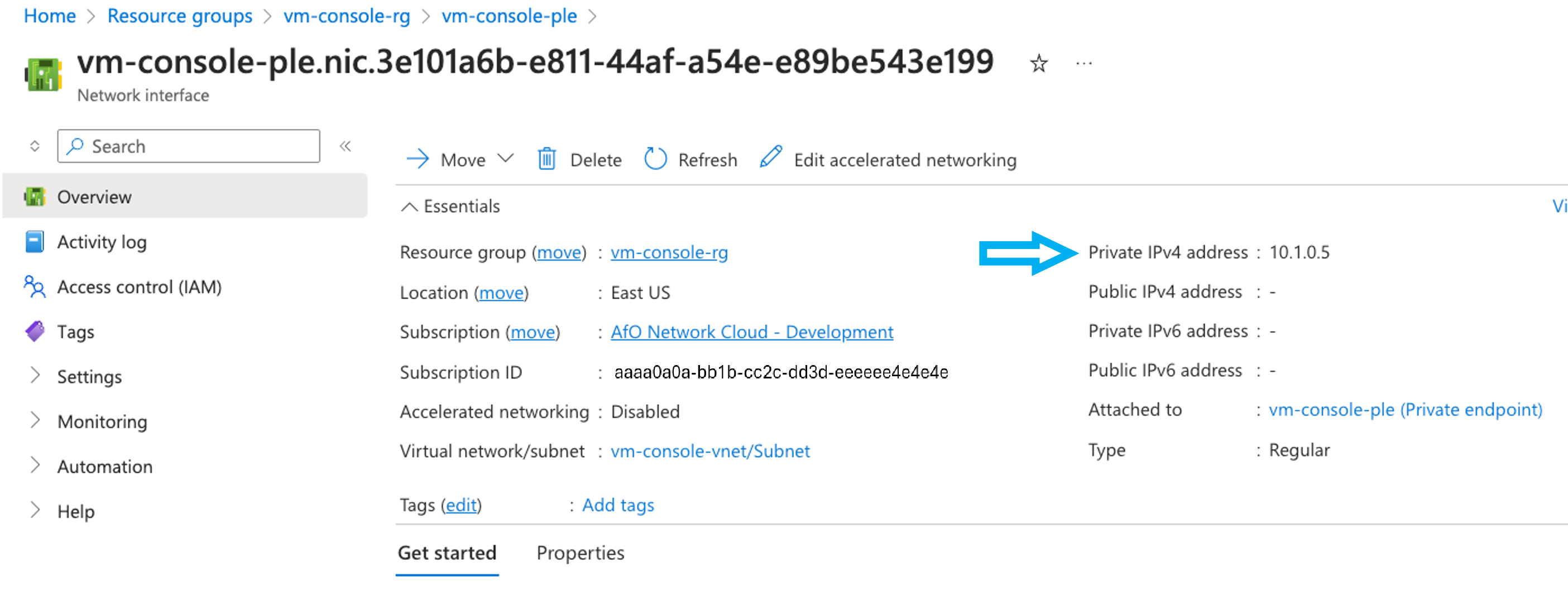
- Confirm with customer that whit IP address was in the
sshcommand, for example,ssh -p 2222 <virtual machine access id>@10.1.0.5
Another way to retrieve the Private endpoint IP addresses is using Azure CLI, as shown here.
ple_interface_ids=$(az network private-endpoint list --resource-group <ple resource group> --query "[].networkInterfaces[0].id" -o tsv)
for ple_interface_id in $ple_interface_ids; do
ple_name=$(echo $ple_interface_id | awk -F/ '{print $NF}'| awk -F. '{print $1}')
export sshmux_ple_ip=$(az network nic show --ids $ple_interface_id --query 'ipConfigurations[0].privateIPAddress' -o tsv)
echo "ple name: ${ple_name}, ple ip: ${sshmux_ple_ip}"
done
In case the script option is used, ask the customer which private endpoint ip address was used.
Collect the Console data
- Navigate to the Azure portal where the cluster manager is located.
- Select on
Extended locationto view its extended locations.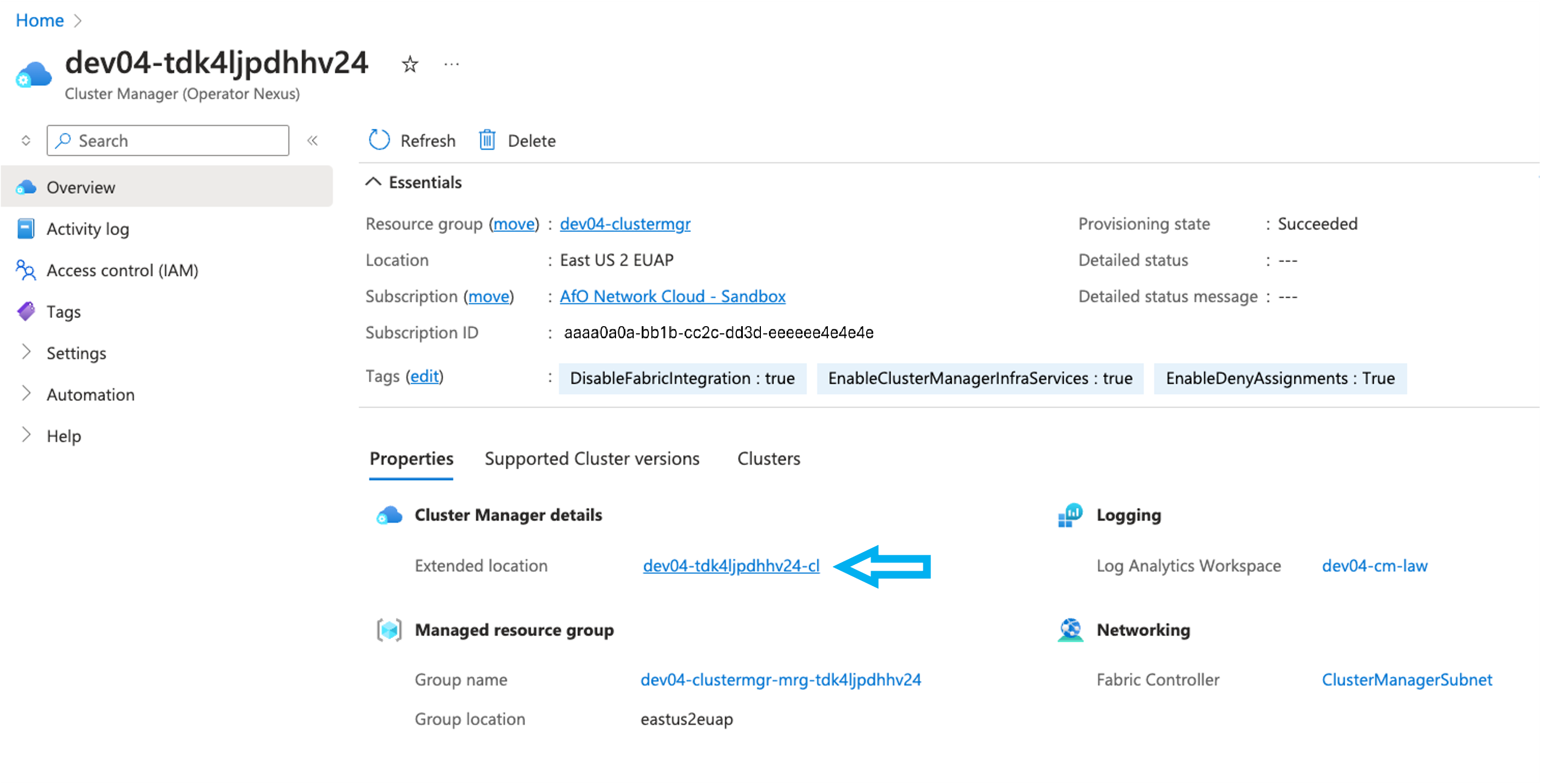
- Select the Console resource in question.
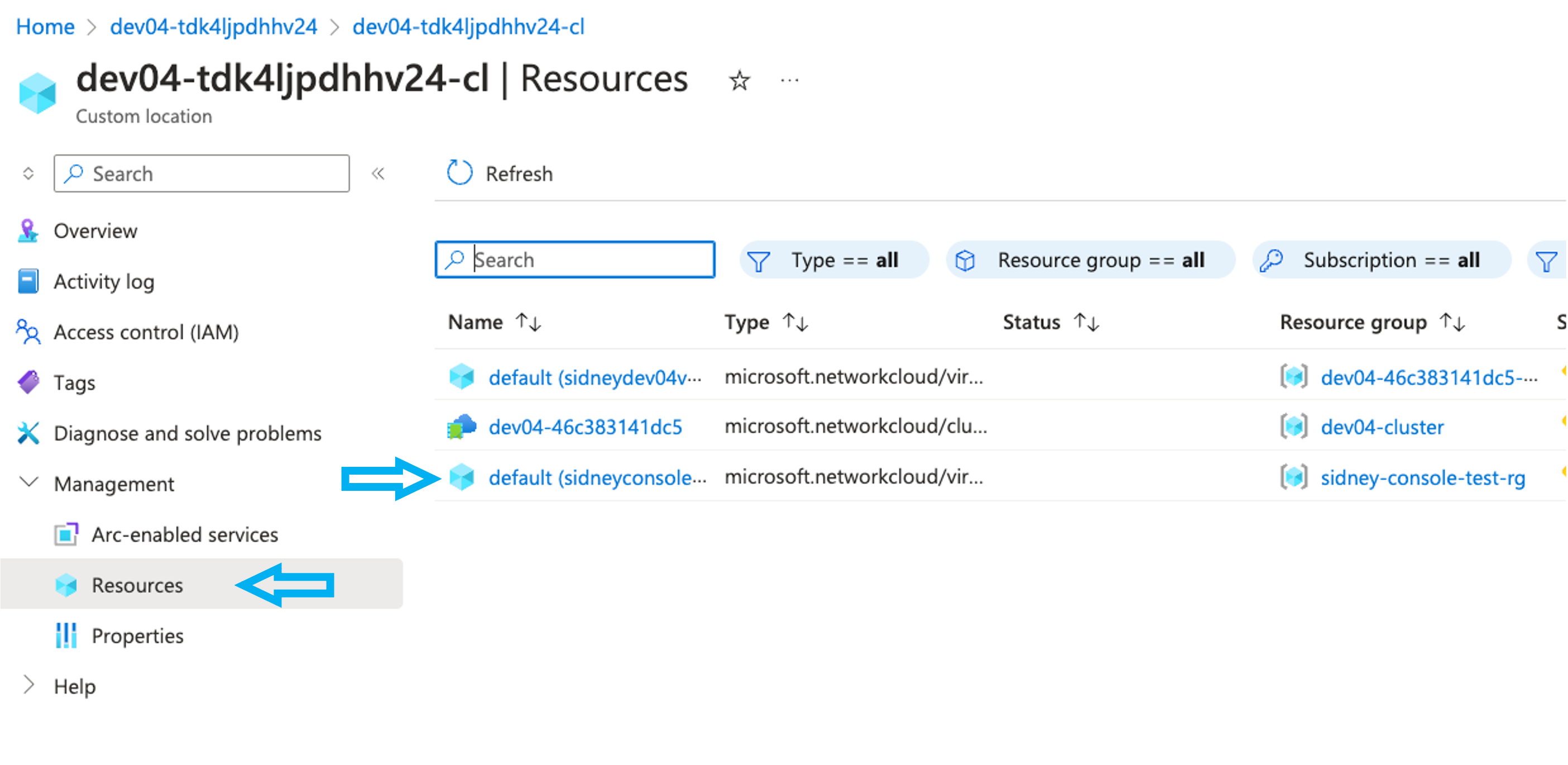
- Collect the data for the console resource to be investigated.
- Console
Enabled - Console
Expiration - Console
Ssh public key - Console
Virtual machine access ID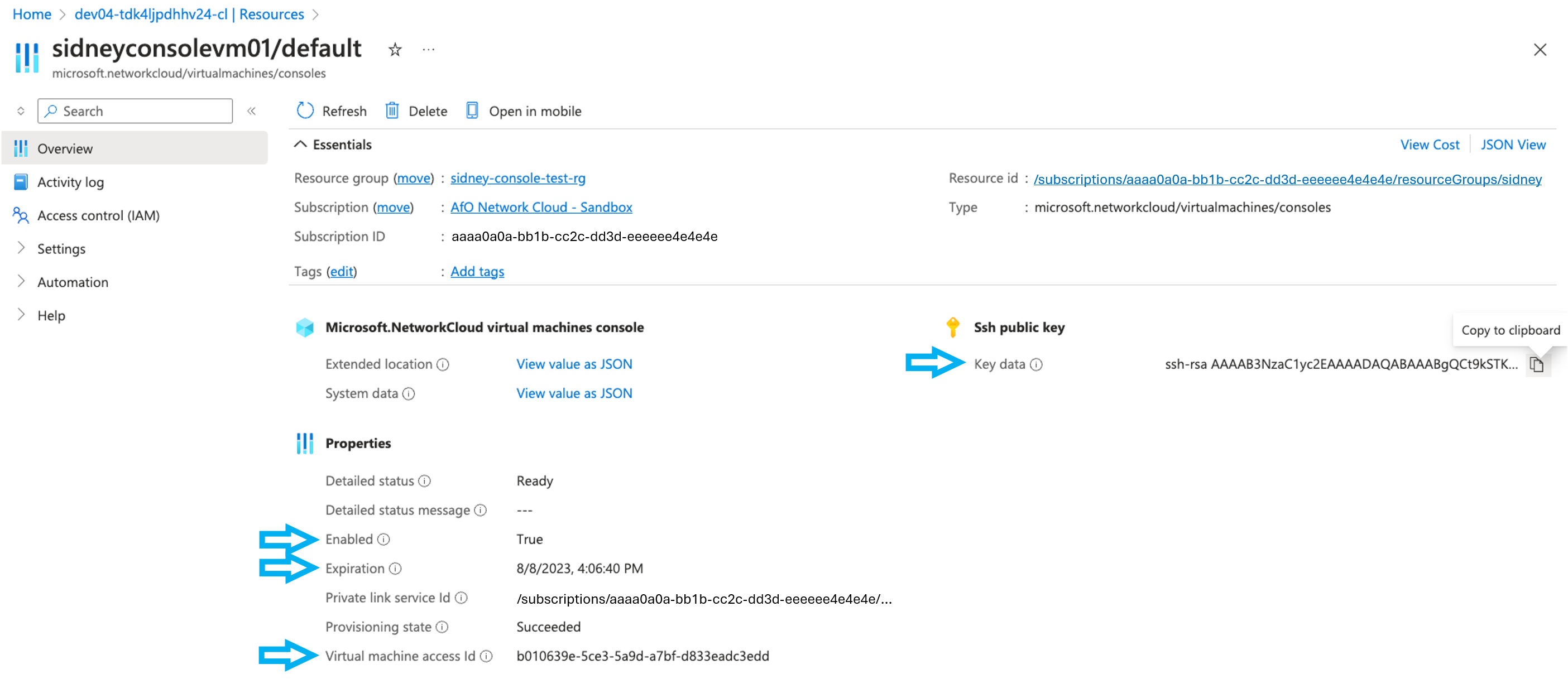
- Console
If the access to Azure portal isn't available, you're also able to retrieve the Console data with az networkcloud virtualmachine console show command.
az networkcloud virtualmachine console show \
--resource-group "${TARGET_RESOURCE_GROUP}" \
--virtual-machine-name "${VM_NAME}"
Where:
- TARGET_RESOURCE_GROUP is the resource group where the customer's virtual machine was created
- VM_NAME is the name of the customer's virtual machine name