Microsoft Security Copilot integration in Defender EASM
Microsoft Defender External Attack Surface Management (Defender EASM) continuously discovers and maps your digital attack surface to provide an external view of your online infrastructure. This visibility helps security and IT teams identify unknowns, prioritize risk, eliminate threats, and extend vulnerability and exposure control beyond the firewall. Attack surface insights are generated by analyzing vulnerability and infrastructure data to showcase the key areas of concern for your organization.
Microsoft Security Copilot (Security Copilot) integration in Defender EASM helps you interact with Microsoft-discovered attack surfaces. Identifying attack surfaces helps your organization quickly understand its externally facing infrastructure and relevant, critical risks. It provides insight into specific areas of risk, including vulnerabilities, compliance, and security hygiene.
For more information about Security Copilot, see What is Security Copilot?. For information about the embedded Security Copilot experience, see Query your attack surface with Defender EASM by using Microsoft Copilot in Azure.
Know before you begin
If you're new to Security Copilot, it's a good idea to familiarize yourself with the solution by reading these articles:
- What is Microsoft Security Copilot?
- Security Copilot experiences
- Get started with Security Copilot
- Understand authentication in Security Copilot
- Prompting in Security Copilot
Security Copilot in Defender EASM
Security Copilot can surface insights from Defender EASM about your organization's attack surface. You can use Security Copilot built-in features. To get more information, use prompts in Security Copilot. The information can help you understand your security posture and mitigate vulnerabilities.
This article introduces you to Security Copilot and includes sample prompts that can help Defender EASM users.
Key features
The EASM Security Copilot integration can help you:
Get a snapshot of your external attack surface and generate insights into potential risks.
You can get a quick view of your external attack surface by analyzing internet-available information combined with the Defender EASM proprietary discovery algorithm. It provides an easy-to-understand natural language explanation of the organization's externally facing assets, such as hosts, domains, webpages, and IP addresses. It highlights the critical risks associated with each.
Prioritize remediation efforts based on asset risk and Common Vulnerabilities and Exposures (CVEs) list items.
Defender EASM helps security teams prioritize their remediation efforts by helping them understand which assets and CVEs pose the greatest risk in their environment. It analyzes vulnerability and infrastructure data to showcase key areas of concern, providing a natural language explanation of the risks and recommended actions.
Use Security Copilot to surface insights.
You can use Security Copilot to ask about insights by using natural language and extract insights from Defender EASM about your organization's attack surface. Query details like the number of Secure Sockets Layer (SSL) certificates that aren't secure, ports that are detected, and specific vulnerabilities that affect the attack surface.
Expedite attack surface curation.
Use Security Copilot to curate your attack surface by using labels, external IDs, and state modifications for a set of assets. This process speeds up curation, so you can organize your inventory faster and more efficiently.
Enable Security Copilot integration
To set up Security Copilot integration in Defender EASM, complete the steps described in the next sections.
Prerequisites
To enable integration, you need to have these prerequisites:
- Access to Microsoft Security Copilot
- Permissions to activate new connections
Connect Security Copilot to Defender EASM
Access Security Copilot and ensure that you're authenticated.
Select the Security Copilot plugin icon on the upper-right side of the prompt input bar.

Under Microsoft, locate Defender External Attack Surface Management. Select On to connect.
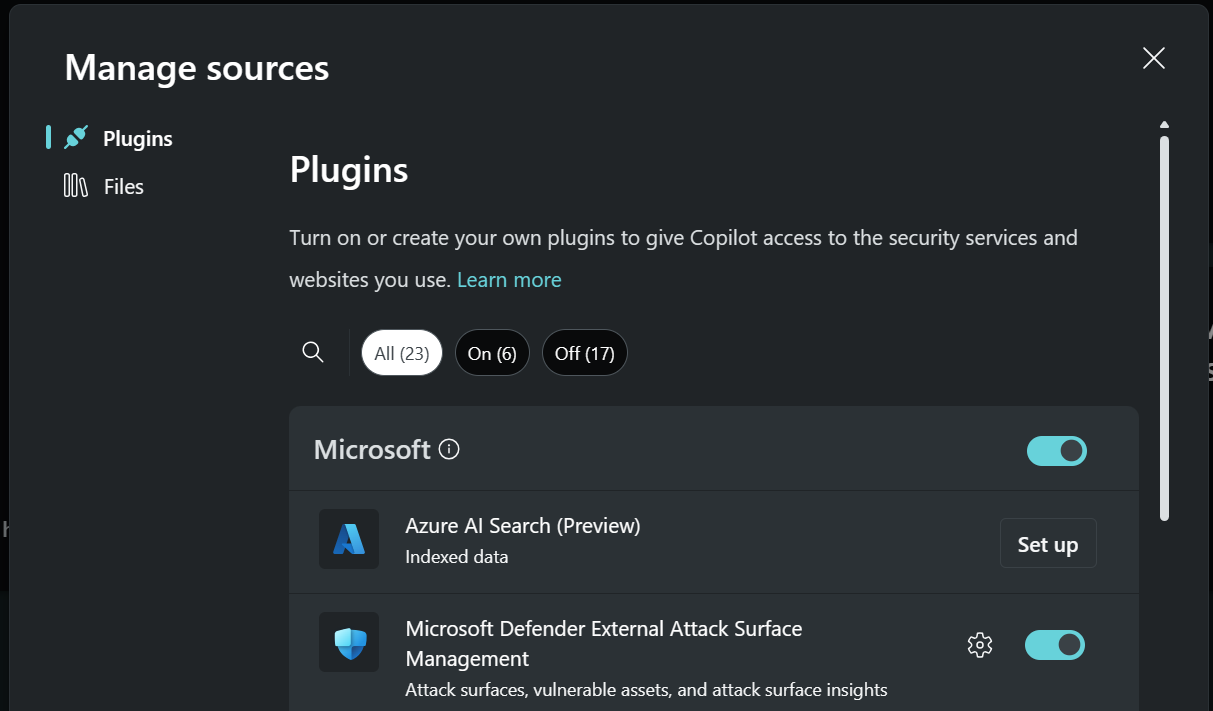
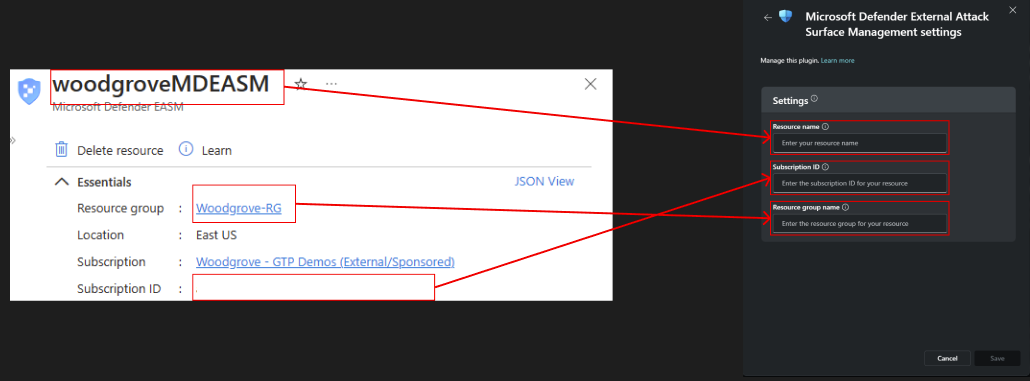
If you want Security Copilot to pull data from your Defender EASM resource, select the gear icon to open the plugin settings. Enter or select values by using the values from your resource's Essentials section on the Overview pane.
Note
You can use your Defender EASM skills even if you haven't purchased Defender EASM. For more information, see Plugin capabilities reference.
Sample Defender EASM prompts
Security Copilot primarily uses natural language prompts. When you query information from Defender EASM, you submit a prompt that guides Security Copilot to select the Defender EASM plugin and invoke the relevant capability.
For success with Security Copilot prompts, we recommend the following approaches:
Ensure that you reference the company name in your first prompt. Unless otherwise specified, all future prompts then provide data about the initially specified company.
Be clear and specific with your prompts. You might get better results if you include specific asset names or metadata values (for example, CVE IDs) in your prompts.
It might also help to add Defender EASM to your prompt, like in these examples:
- According to Defender EASM, what are my expired domains?
- Tell me about Defender EASM high-priority attack surface insights.
Experiment with different prompts and variations to see what works best for your use case. Chat AI models vary, so iterate and refine your prompts based on the results you receive.
Security Copilot saves your prompt sessions. To see previous sessions, in Security Copilot, on the menu, select My sessions.
For a walkthrough of Security Copilot, including the pin and share features, see Navigate Security Copilot.
For more information on writing Security Copilot prompts, see Security Copilot prompting tips.
Plugin capabilities reference
| Capability | Description | Inputs | Behaviors |
|---|---|---|---|
| Get attack surface summary | Returns the attack surface summary for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • Get attack surface for LinkedIn. • Get my attack surface. • What is the attack surface for Microsoft? • What is my attack surface? • What are the externally facing assets for Azure? • What are my externally facing assets? Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • Returns an attack surface summary for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the attack surface summary for the company name. |
| Get attack surface insights | Returns the attack surface insights for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • Get high-priority attack surface insights for LinkedIn. • Get my high-priority attack surface insights. • Get low priority attack surface insights for Microsoft. • Get low priority attack surface insights. • Do I have high-priority vulnerabilities in my external attack surface for Azure? Required inputs: • PriorityLevel (the priority level must be high, medium, or low; if not provided, it defaults to high) Optional inputs: • CompanyName (the company name) |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • Returns attack surface insights for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the attack surface insights for the company name. |
| Get assets affected by a CVE | Returns the assets affected by a CVE for either the customer's Defender EASM resource or a specific company name. | Example inputs: • Get assets affected by CVE-2023-0012 for LinkedIn. • Which assets are affected by CVE-2023-0012 for Microsoft? • Is Azure's external attack surface impacted by CVE-2023-0012? • Get assets affected by CVE-2023-0012 for my attack surface. • Which of my assets are affected by CVE-2023-0012? • Is my external attack surface impacted by CVE-2023-0012? Required inputs: • CveId Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • If plugin settings aren't filled out, fail graciously and remind customers. • If plugin settings are filled out, returns the assets affected by a CVE for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the assets affected by a CVE for the specific company name. |
| Get assets affected by a CVSS | Returns the assets affected by a Common Vulnerability Scoring System (CVSS) score for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • Get assets affected by high-priority CVSS scores in LinkedIn’s attack surface. • How many assets have critical CVSS score for Microsoft? • Which assets have critical CVSS scores for Azure? • Get assets affected by high-priority CVSS scores in my attack surface. • How many of my assets have critical CVSS scores? • Which of my assets have critical CVSS scores? Required inputs: • CvssPriority (the CVSS priority must be critical, high, medium, or low) Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • If plugin settings aren't filled out, fail graciously and remind customers. • If plugin settings are filled out, returns the assets affected by a CVSS score for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the assets affected by a CVSS score for the specific company name. |
| Get expired domains | Returns the number of expired domains for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • How many domains are expired in LinkedIn’s attack surface? • How many assets are using expired domains for Microsoft? • How many domains are expired in my attack surface? • How many of my assets are using expired domains for Microsoft? Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • Returns the number of expired domains for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the number of expired domains for the specific company name. |
| Get expired certificates | Returns the number of expired SSL certificates for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • How many SSL certificates are expired for LinkedIn? • How many assets are using expired SSL certificates for Microsoft? • How many SSL certificates are expired for my attack surface? • What are my expired SSL certificates? Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • Returns the number of SSL certificates for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the number of SSL certificates for the specific company name. |
| Get SHA1 certificates | Returns the number of SHA1 SSL certificates for either the customer’s Defender EASM resource or a specific company name. | Example inputs: • How many SSL SHA1 certificates are present for LinkedIn? • How many assets are using SSL SHA1 for Microsoft? • How many SSL SHA1 certificates are present for my attack surface? • How many of my assets are using SSL SHA1? Optional inputs: • CompanyName |
If your plugin is configured to an active Defender EASM resource and no other company is specified: • Returns the number of SHA1 SSL certificates for the customer’s Defender EASM resource. If another company name is provided: • If no exact for match for company name is found, returns a list of possible matches. • If there's an exact match, returns the number of SHA1 SSL certificates for the specific company name. |
| Translate natural language to a Defender EASM query | Translates any natural language question into a Defender EASM query and returns the assets that match the query. | Example inputs: • What assets are using jQuery version 3.1.0? • Get the hosts with port 80 open in my attack surface. • Find all the page, host, and ASN assets in my inventory that have an IP address that is IP X, IP Y, or IP Z. • Which of my assets have a registrant email of <name@example.com>? |
If your plugin is configured to an active Defender EASM resource: • Returns the assets matching with the translated query. |
Switch between resource data and company data
Even though we added resource integration for our skills, we still support pulling data from prebuilt attack surfaces for specific companies. To improve the Security Copilot accuracy in determining when a customer wants to pull from their attack surface or from a prebuilt, company attack surface, we recommend using my, my attack surface, and so on, to convey that you want to use your resource. Use their, specific company name, and so on, to convey that you want to use a prebuilt attack surface. Although this approach does improve the experience in a single session, we strongly recommend using two separate sessions to avoid any confusion.
Provide feedback
Your feedback on Security Copilot generally, and the Defender EASM plugin specifically, is vital to guide current and planned development of the product. The optimal way to provide this feedback is directly in the product, using the feedback buttons at the bottom of each completed prompt. Select Looks right, Needs improvement, or Inappropriate. We recommend that you choose Looks right when the result matches expectations, Needs improvement when it doesn't, and Inappropriate when the result is harmful in some way.
Whenever possible, and especially when the result you select is Needs improvement, please write a few words to explain what we can do to improve the outcome. This request also applies when you expect Security Copilot to invoke the Defender EASM plugin, but a different plugin is engaged instead.
Privacy and data security in Security Copilot
When you interact with Security Copilot to get Defender EASM data, Copilot pulls that data from Defender EASM. The prompts, the data that's retrieved, and the output that's shown in the prompt results are processed and stored in the Security Copilot service.
For more information about data privacy in Security Copilot, see Privacy and data security in Security Copilot.