Get answers to common questions about Microsoft Defender for Servers.
Pricing
What servers do I pay for in a subscription?
When you enable Defender for Servers on a subscription, you're charged for all machines based on their power states.
| State | Details | Billing |
|---|---|---|
| Azure VMs | ||
| Starting | VM starting up. | Not billed |
| Running | Normal working state. | Billed |
| Stopping | Transitional. Moves to Stopped state when finished. | Billed |
| Stopped | VM shut down from within guest OS or by using PowerOff APIs. Hardware is still allocated, and the machine remains on the host. | Billed |
| Deallocating | Transitional. Moves to Deallocated state when finished. | Not billed |
| Deallocated | VM stopped and removed from the host. | Not billed |
| Azure Arc machines | ||
| Connecting | Servers connected, but heartbeat not yet received. | Not billed |
| Connected | Receiving regular heartbeat from Connected Machine agent. | Billed |
| Offline/Disconnected | No heartbeat received in 15-30 minutes. | Not billed |
| Expired | If disconnected for 45 days, status might change to Expired. | Not billed |
What are the licensing requirements for Microsoft Defender for Endpoint?
Licenses for Defender for Endpoint for Servers are included with Defender for Servers.
Can I get a discount if I already have a Microsoft Defender for Endpoint license?
If you already have a license for Microsoft Defender for Endpoint for Servers, you don't pay for that part of your Microsoft Defender for Servers Plan 1 or 2 license.
To request your discount, in the Azure portal, select Support and Troubleshooting > Help + support. Select Create a support request and fill in the fields.
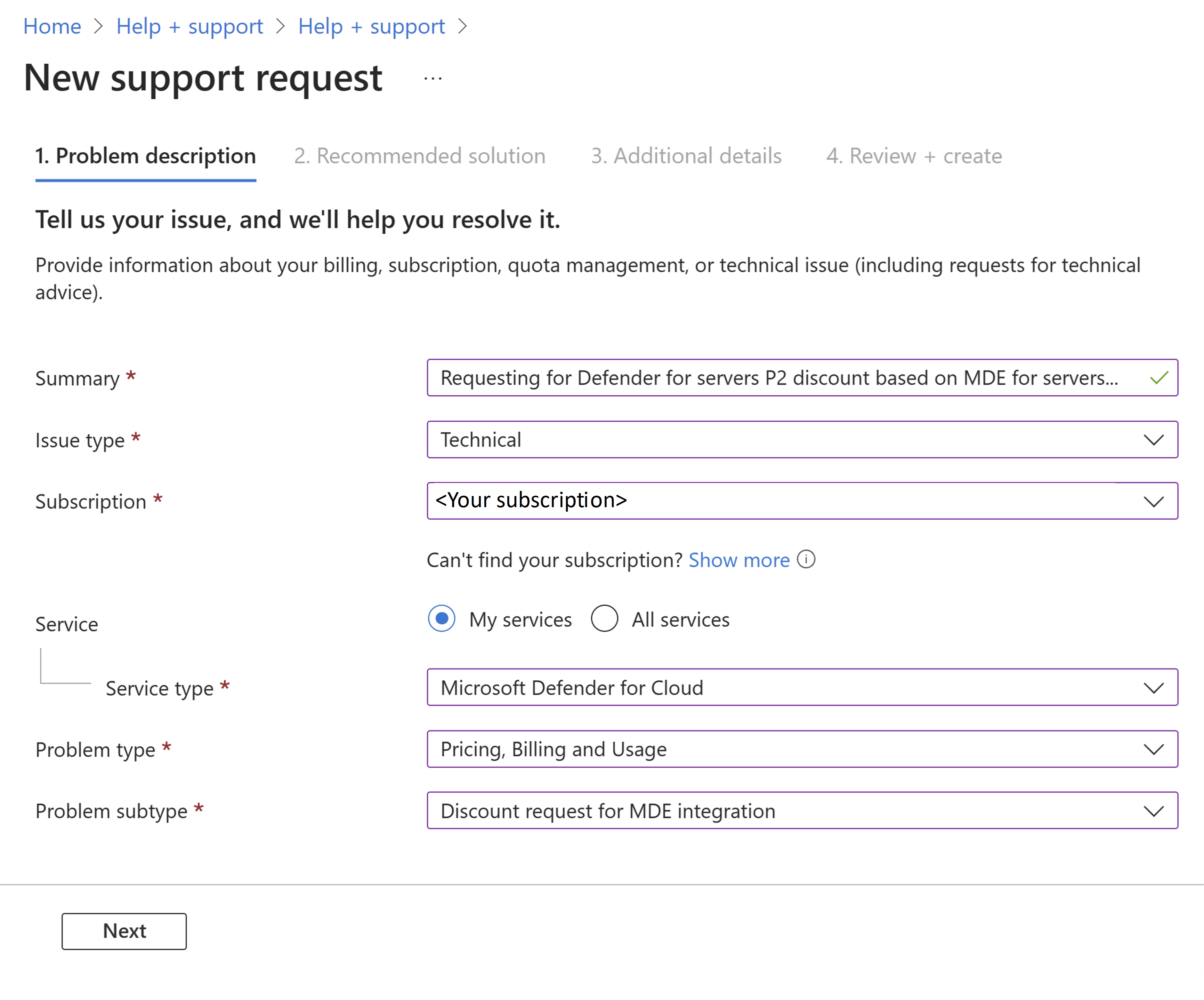
In Additional details, enter details, tenant ID, the number of Defender for Endpoint licenses that were purchased, the expiration date, and all other required fields.
Complete the process and select Create.
The discount becomes effective starting on the approval date. It isn't retroactive.
What's the free data ingestion allowance?
When Defender for Servers Plan 2 is enabled you get a free data ingestion allowance for specific data types. Learn more
Deployment
Can I enable Defender for Servers on a subset of machines in a subscription?
Yes you can enable Defender for Servers on specific resources in a subscription. Learn more about planning deployment scope.
How does Defender for Servers collect data?
Learn about data collection methods in Defender for Servers.
Where does Defender for Servers store my data?
Learn about data residency for Defender for Cloud.
Does Defender for Servers need a Log Analytics workspace?
Defender for Servers Plan 1 doesn't depend on Log Analytics. In Defender for Servers Plan 2, you need a Log Analytics workspace to take advantage of the free data ingestion benefit. You also need a workspace to use file integrity monitoring in Plan 2. If you do set up a Log Analytics workspace for the free data ingestion benefit, you need to enable Defender for Servers Plan 2 directly on it.
What if I have Defender for Servers enabled on a workspace but not on a subscription?
The legacy method for onboarding servers to Defender for Servers Plan 2 using a workspace and the Log Analytics agent is no longer supported or available in the portal. To ensure that machines that are currently connected to the workspace remain protected, do the following:
- On-premises and multicloud machines: If you previously onboarded on-premises and AWS/GCP machines using the legacy method, connect these machines to Azure as Azure Arc-enabled servers to the subscription with Defender for Servers Plan 2 enabled.
- Selected machines: If you used the legacy method to enable Defender for Servers Plan 2 on individual machines, we recommend that you enable Defender for Server Plan 2 on the entire subscription. Then you can exclude specific machines using resource-level configuration.
Defender for Endpoint integration
Which Microsoft Defender for Endpoint plan is supported in Defender for Servers?
Defender for Servers Plan 1 and Plan 2 provides the capabilities of Microsoft Defender for Endpoint Plan 2, including endpoint detection and response (EDR).
Do I need to buy a separate anti-malware solution for my machines?
No. With Defender for Endpoint integration in Defender for Servers, you'll also get malware protection on your machines. In addition, Defender for Servers Plan 2 provides agentless malware scanning.
On new Windows Server operating systems, Microsoft Defender Antivirus is part of the operating system and will be enabled in active mode. For machines running Windows Server with the Defender for Endpoint unified solution integration enabled, Defender for Servers deploys Defender Antivirus in active mode. On Linux, Defender for Servers deploys Defender for Endpoint including the anti-malware component, and set the component in passive mode.
How do I switch from a non-Microsoft EDR tool?
Full instructions for switching from a non-Microsoft endpoint solution are available in the Microsoft Defender for Endpoint documentation: Migration overview.
What's the "MDE.Windows" / "MDE.Linux" extension running on my machines?
When you turn on the Defender for Servers plan in a subscription, the native Defender for Endpoint integration in Defender for Cloud automatically deploys the Defender for Endpoint agent on supported machines in the subscription as needed. Automatic onboarding installs the MDE.Windows/MDE.Linux extension.
If the extension isn't showing, check that the machine meets the prerequisites, and that Defender for Servers is enabled.
Important
If you delete the MDE.Windows/MDE.Linux extension, it won't remove Microsoft Defender for Endpoint. Learn about offboard Windows servers from Defender for Endpoint.
Machine support and scanning
What types of virtual machines do Defender for Servers support?
How often does Defender for Cloud scan for operating system vulnerabilities, system updates, and endpoint protection issues?
Operating system: data is updated within 48 hours System updates: data is updated within 24 hours Endpoint protection: data is updated within 8 hours
Defender for Cloud typically scans for new data every hour, and refreshes security recommendations accordingly.
How are VM snapshots collected by agentless scanning secured?
Agentless scanning protects disk snapshots according to Microsoft's highest security standards. Security measures include:
- Data is encrypted at rest and in-transit.
- Snapshots are immediately deleted when the analysis process is complete.
- Snapshots remain within their original AWS or Azure region. EC2 snapshots aren't copied to Azure.
- Isolation of environments per customer account/subscription.
- Only metadata containing scan results is sent outside the isolated scanning environment.
- All operations are audited.
What is the auto-provisioning feature for vulnerability scanning with a "bring your own license" (BYOL) solution? Can it be applied on multiple solutions?
Defender for Servers can scan machines to see if they have an EDR solution enabled. If they don't, you can use Microsoft Defender Vulnerability Management that's integrated by default into Defender for Cloud. As an alternative, Defender for Cloud can deploy a supported non-Microsoft BYOL vulnerability scanner. You can only use a single BYOL scanner. Multiple non-Microsoft scanners aren't supported.
Does the integrated Defender for Vulnerability Management scanner find network vulnerabilities?
No, it only finds vulnerabilities on the machine itself.
Why do I get the message "Missing scan data" for my VM?
This message appears when there's no scan data for a VM. It takes around an hour or less to scan data after a data collection method is enabled. After the initial scan, you might receive this message because there's no scan data available. For example, scans don't populate for a VM that's stopped. This message might also appear if scan data hasn't populated recently.
Why is a machine shown as not applicable?
The list of resources in the Not applicable tab includes a Reason column
| Reason | Details |
|---|---|
| No scan data available on the machine | There aren't any compliance results for this machine in Azure Resource Graph. All compliance results are written to Azure Resource Graph by the Azure machine configuration extension. You can check the data in Azure Resource Graph using the [sample Resource Graph queries][(/azure/governance/policy/samples/resource-graph-samples?tabs=azure-cli#azure-policy-guest-configuration). |
| Azure machine configuration extension isn't installed on the machine | The machine is missing the extension, which is a prerequisite for assessing compliance against the Microsoft Cloud Security Baseline. |
| System managed identity isn't configured on the machine | A system-assigned, managed identity must be deployed on the machine. |
| The recommendation is disabled in policy | The policy definition that assesses the OS baseline is disabled on the scope that includes the |