Remediate system update and patch recommendations
Microsoft Defender for Cloud provides security recommendations to improve your organizational security posture and reduce risk. An important element in risk reduction is to harden machines across your business environment.
As part of the hardening strategy, Defender for Cloud assesses machines to check that the latest system updates and patches are installed, and issues security recommendations if they're not. System updates and patches are crucial for keeping machines secure and healthy. Updates often contain security patches for vulnerabilities that, if left unfixed, are exploitable by attackers.
Defender for Servers Plan 2 automatically assesses updates and patches on machines and generates the following recommendations as needed:
- Machines should be configured to periodically check for missing system updates
- System updates should be installed on your machines (powered by Azure Update Manager)
These recommendations rely on Azure Update Manager, which uses a VM extension.
! [!NOTE] The older method for update assessment used the Log Analytics agent (also known as the Microsoft Monitoring Agent (MMA)) to gather data. Use of the MMA is now deprecated.
Prerequisites
- Defender for Servers Plan 2 must be enabled.
- To verify system updates machines must be supported by Azure Update Manager.
- On-premises machines must be connected as Azure Arc-enabled VMs.
- Multicloud (AWS/GCP machines) must be onboarded with Azure Arc when you connect AWS or GCP.
- If you're using Defender for Servers Plan 2, there's no additional cost for assessing, remediating, and patching system updates on supported Azure VMs and Azure Arc VMs.
- If Defender for Servers Plan 2 isn't enabled on your subscription or multicloud connector, assessments for Azure Arc-enabled machines VMs in the subscription are subject to Azure Update Manager charges.
Enable periodic assessment on machines
Defender for Cloud issues a recommendation that machines should be assessed periodically for system updates.
In Defender for Cloud, open the Recommendations page.
Select the recommendation
Machines should be configured to periodically check for missing system updates (powered by Azure Update Manager).- Under Remediation steps, review quick fix and manual fix details. If you follow the quick fix, the periodic assessment update setting is enabled on machines.
- In the Unhealthy resources list, drill down to see resource details.
Select the Fix option.
Select the relevant machine, and then select Fix 1 resource.
Periodic assessment can also be enabled at scale with Azure Policy.
Remediate update recommendations
In Defender for Cloud, open the Recommendations page.
Select the recommendation
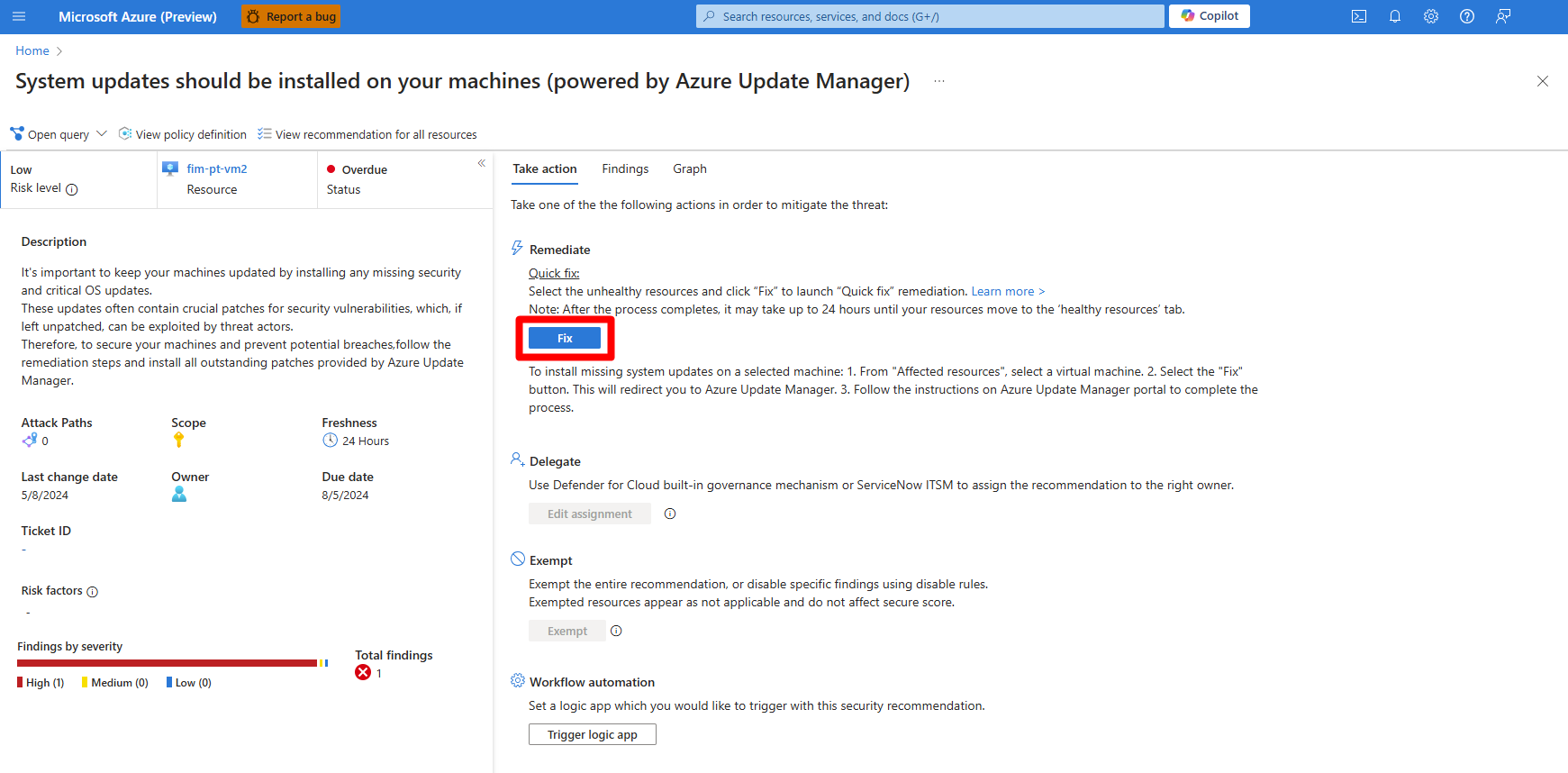
System updates should be installed on your machines (powered by Azure Update Manager).Review the recommendation.
Select the Fix option to do a one-time installation of missing updates through the Update Manager portal.
Remediate recommendations at scale
You can remediate recommendations on multiple machines.
In Defender for Cloud, open the Recommendations page.
Select the recommendation
System updates should be installed on your machines (powered by Azure Update Manager).Locate the relevant system update recommendation.
Review the recommendation.
In the recommendation details page, select View recommendation for all resources.
Select all machines you want to fix.
Select Fix.