Outbound firewall rules for Azure SQL Database and Azure Synapse Analytics
Applies to:
Azure SQL Database
Azure Synapse Analytics (dedicated SQL pools only)
Outbound firewall rules limit network traffic from the Azure SQL logical server to a customer defined list of Azure Storage accounts and Azure SQL logical servers. Any attempt to access storage accounts or databases not in this list is denied. The following Azure SQL Database features support this feature:
- Auditing
- Vulnerability assessment
- Import/Export service
- OPENROWSET
- Bulk Insert
- sp_invoke_external_rest_endpoint
Important
- This article applies to both Azure SQL Database and dedicated SQL pool (formerly SQL DW) in Azure Synapse Analytics. These settings apply to all SQL Database and dedicated SQL pool (formerly SQL DW) databases associated with the server. For simplicity, the term 'database' refers to both databases in Azure SQL Database and Azure Synapse Analytics. Likewise, any references to 'server' is referring to the logical SQL server that hosts Azure SQL Database and dedicated SQL pool (formerly SQL DW) in Azure Synapse Analytics. This article does not apply to Azure SQL Managed Instance or dedicated SQL pools in Azure Synapse Analytics workspaces.
- Outbound firewall rules are defined at the logical server. Geo-replication and failover groups require the same set of rules to be defined on the primary and all secondaries.
Set outbound firewall rules in the Azure portal
Browse to the Outbound networking section in the Firewalls and virtual networks pane for your Azure SQL Database and select Configure outbound networking restrictions.
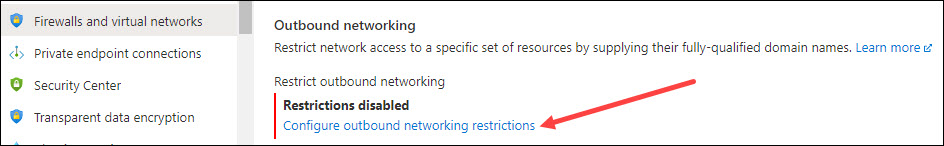
This will open up the following pane on the right-hand side:
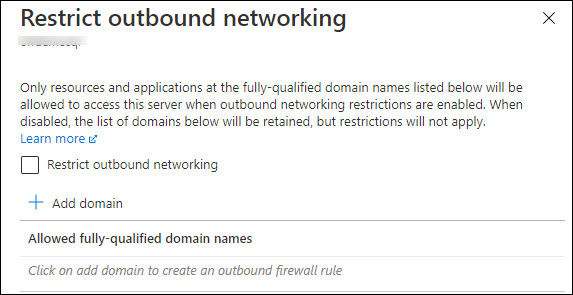
Select the check box titled Restrict outbound networking and then add the FQDN for the Storage accounts (or SQL Databases) using the Add domain button.
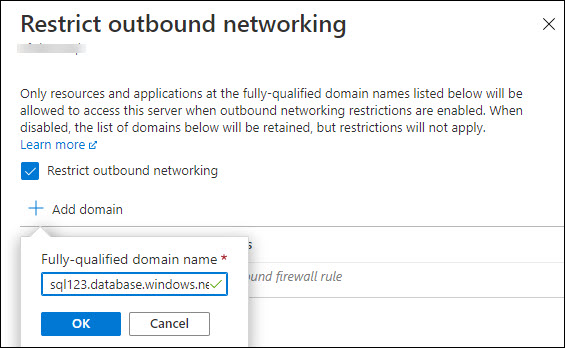
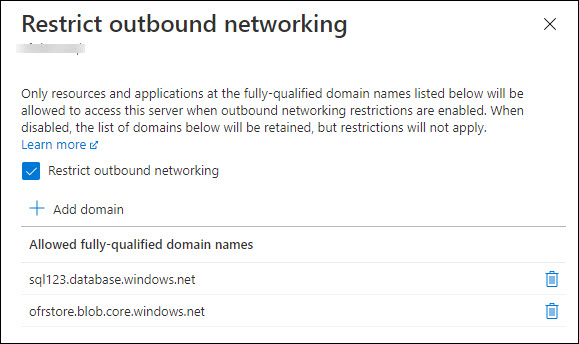
After you're done, you should see a screen similar to the one below. Select OK to apply these settings.
Set outbound firewall rules using PowerShell
Important
The PowerShell Azure Resource Manager (AzureRM) module was deprecated on February 29, 2024. All future development should use the Az.Sql module. Users are advised to migrate from AzureRM to the Az PowerShell module to ensure continued support and updates. The AzureRM module is no longer maintained or supported. The arguments for the commands in the Az PowerShell module and in the AzureRM modules are substantially identical. For more about their compatibility, see Introducing the new Az PowerShell module.
The following script requires the Azure PowerShell module.
The following PowerShell script shows how to change the outbound networking setting (using the RestrictOutboundNetworkAccess property):
# Get current settings for Outbound Networking
(Get-AzSqlServer -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName>).RestrictOutboundNetworkAccess
# Update setting for Outbound Networking
$SecureString = ConvertTo-SecureString "<ServerAdminPassword>" -AsPlainText -Force
Set-AzSqlServer -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName> -SqlAdministratorPassword $SecureString -RestrictOutboundNetworkAccess "Enabled"
Use these PowerShell cmdlets to configure outbound firewall rules
# List all Outbound Firewall Rules
Get-AzSqlServerOutboundFirewallRule -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName>
# Add an Outbound Firewall Rule
New-AzSqlServerOutboundFirewallRule -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName> -AllowedFQDN testOBFR1
# List a specific Outbound Firewall Rule
Get-AzSqlServerOutboundFirewallRule -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName> -AllowedFQDN <StorageAccountFQDN>
#Delete an Outbound Firewall Rule
Remove-AzSqlServerOutboundFirewallRule -ServerName <SqlServerName> -ResourceGroupName <ResourceGroupName> -AllowedFQDN <StorageAccountFQDN>
Set outbound firewall rules using the Azure CLI
Important
All scripts in this section require the Azure CLI.
Azure CLI in a bash shell
The following CLI script shows how to change the outbound networking setting (using the restrictOutboundNetworkAccess property) in a bash shell:
# Get current setting for Outbound Networking
az sql server show -n sql-server-name -g sql-server-group --query "restrictOutboundNetworkAccess"
# Update setting for Outbound Networking
az sql server update -n sql-server-name -g sql-server-group --set restrictOutboundNetworkAccess="Enabled"
Use these CLI commands to configure outbound firewall rules
# List a server's outbound firewall rules.
az sql server outbound-firewall-rule list -g sql-server-group -s sql-server-name
# Create a new outbound firewall rule
az sql server outbound-firewall-rule create -g sql-server-group -s sql-server-name --outbound-rule-fqdn allowedFQDN
# Show the details for an outbound firewall rule.
az sql server outbound-firewall-rule show -g sql-server-group -s sql-server-name --outbound-rule-fqdn allowedFQDN
# Delete the outbound firewall rule.
az sql server outbound-firewall-rule delete -g sql-server-group -s sql-server-name --outbound-rule-fqdn allowedFQDN
Next steps
- For an overview of Azure SQL Database security, see Securing your database.
- For an overview of Azure SQL Database connectivity, see Azure SQL Connectivity Architecture.
- Learn more about Azure SQL Database and Azure Synapse Analytics network access controls.
- Learn about Azure Private Link for Azure SQL Database and Azure Synapse Analytics.