Create Arc virtual machines on Azure Local
Applies to: Azure Local 2311.2 and later
This article describes how to create an Arc virtual machine (VM) starting with the VM images that you created on your Azure Local instance. You can create Arc VMs using the Azure CLI, Azure portal, or Azure Resource Manager template.
About Azure Local resource
Use the Azure Local resource page for the following operations:
- Create and manage Arc VM resources such as VM images, disks, network interfaces.
- View and access Azure Arc Resource Bridge and Custom Location associated with the Azure Local instance.
- Provision and manage Arc VMs.
The procedure to create Arc VMs is described in the next section.
Prerequisites
Before you create an Azure Arc-enabled VM, make sure that the following prerequisites are completed.
- Access to an Azure subscription with the appropriate RBAC role and permissions assigned. For more information, see RBAC roles for Azure Local Arc VM management.
- Access to a resource group where you want to provision the VM.
- Access to one or more VM images on your Azure Local. These VM images could be created by one of the following procedures:
- A custom location for your Azure Local that you'll use to provision VMs. The custom location will also show up in the Overview page for Azure Local.
If using a client to connect to your Azure Local, see Connect to Azure Local via Azure CLI client.
Access to a network interface that you created on a logical network associated with your Azure Local. You can choose a network interface with static IP or one with a dynamic IP allocation. For more information, see how to Create network interfaces.
Create Arc VMs
Follow these steps to create an Arc VM on your Azure Local.
Follow these steps on the client running az CLI that is connected to your Azure Local.
Sign in and set subscription
Connect to a machine on your Azure Local.
Sign in. Type:
az login --use-device-codeSet your subscription.
az account set --subscription <Subscription ID>
Create a Windows VM
Depending on the type of the network interface that you created, you can create a VM that has network interface with static IP or one with a dynamic IP allocation.
Note
If you need more than one network interface with static IPs for your VM, create the interface(s) now before you create the VM. Adding a network interface with static IP, after the VM is provisioned, is not supported.
Here we create a VM that uses specific memory and processor counts on a specified storage path.
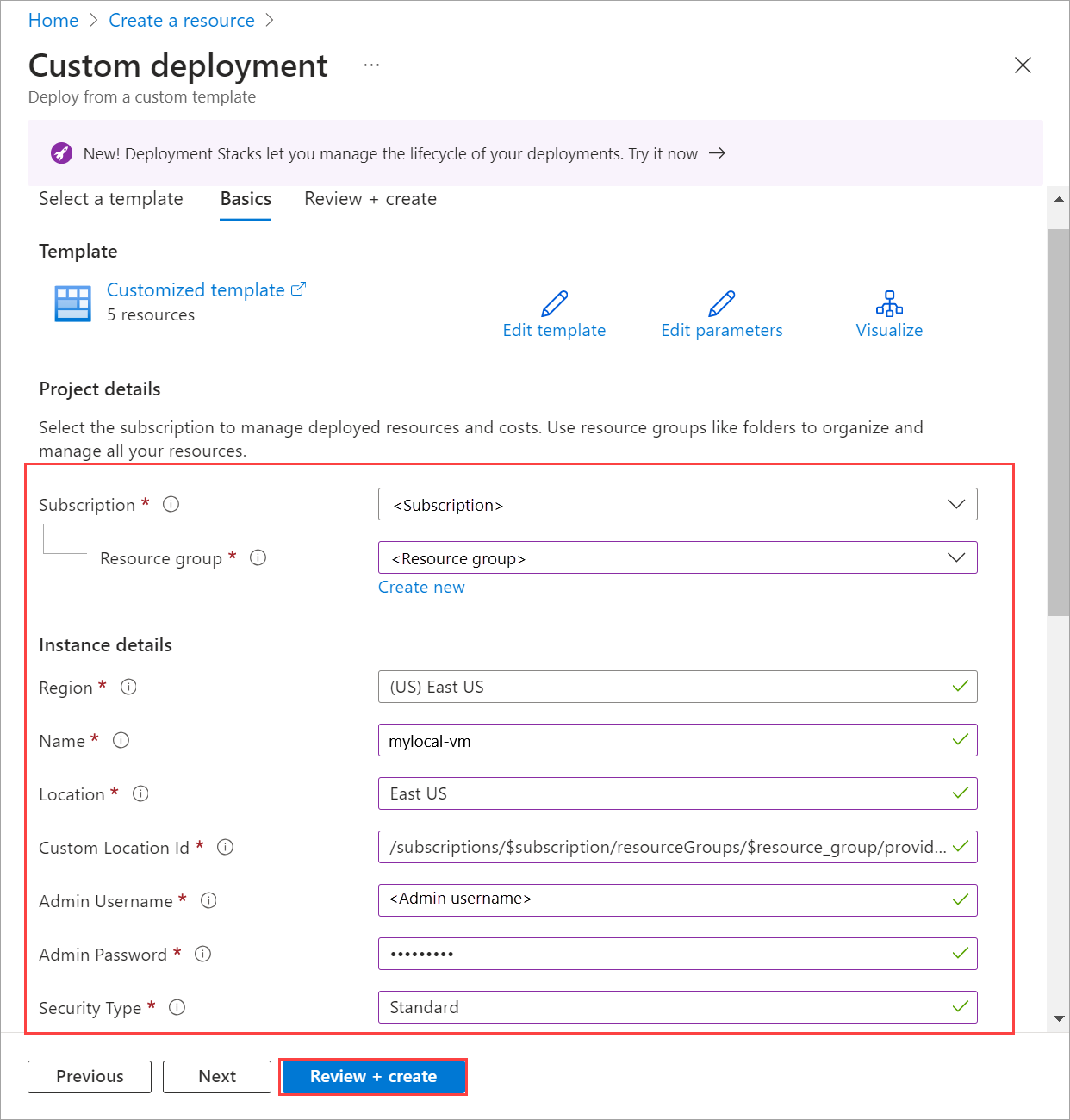
Set some parameters.
$vmName ="local-vm" $subscription = "<Subscription ID>" $resource_group = "local-rg" $customLocationName = "local-cl" $customLocationID ="/subscriptions/$subscription/resourceGroups/$resource_group/providers/Microsoft.ExtendedLocation/customLocations/$customLocationName" $location = "eastus" $computerName = "mycomputer" $userName = "local-user" $password = "<Password for the VM>" $imageName ="ws22server" $nicName ="local-vnic" $storagePathName = "local-sp" $storagePathId = "/subscriptions/<Subscription ID>/resourceGroups/local-rg/providers/Microsoft.AzureStackHCI/storagecontainers/local-sp"The parameters for VM creation are tabulated as follows:
Parameters Description name Name for the VM that you create for your Azure Local. Make sure to provide a name that follows the Rules for Azure resources. admin-username Username for the user on the VM you're deploying on your Azure Local. admin-password Password for the user on the VM you're deploying on your Azure Local. image-name Name of the VM image used to provision the VM. location Azure regions as specified by az locations. For example, this could beeastus,westeurope.resource-group Name of the resource group where you create the VM. For ease of management, we recommend that you use the same resource group as your Azure Local. subscription Name or ID of the subscription where your Azure Local is deployed. This could be another subscription you use for VM on your Azure Local. custom-location Use this to provide the custom location associated with your Azure Local where you're creating this VM. authentication-type Type of authentication to use with the VM. The accepted values are all,password, andssh. Default is password for Windows and SSH public key for Linux. Useallto enable bothsshandpasswordauthentication.nics Names or the IDs of the network interfaces associated with your VM. You must have atleast one network interface when you create a VM, to enable guest management. memory-mb Memory in Megabytes allocated to your VM. If not specified, defaults are used. processors The number of processors allocated to your VM. If not specified, defaults are used. storage-path-id The associated storage path where the VM configuration and the data are saved. proxy-configuration Use this optional parameter to configure a proxy server for your VM. For more information, see Create a VM with proxy configured. Run the following command to create a VM.
az stack-hci-vm create --name $vmName --resource-group $resource_group --admin-username $userName --admin-password $password --computer-name $computerName --image $imageName --location $location --authentication-type all --nics $nicName --custom-location $customLocationID --hardware-profile memory-mb="8192" processors="4" --storage-path-id $storagePathId
The VM is successfully created when the provisioningState shows as succeededin the output.
Note
The VM created has guest management enabled by default. If for any reason guest management fails during VM creation, you can follow the steps in Enable guest management on Arc VM to enable it after the VM creation.
In this example, the storage path was specified using the --storage-path-id flag and that ensured that the workload data (including the VM, VM image, non-OS data disk) is placed in the specified storage path.
If the flag isn't specified, the workload (VM, VM image, non-OS data disk) is automatically placed in a high availability storage path.
Additional parameters for Windows Server 2012 and Windows Server 2012 R2 images
When creating an Arc VM using Windows Server 2012 and Windows Server 2012 R2 images, specify the following additional parameters to create the VM:
--enable-agent: Set this parameter totrueto onboard the Azure Connected Machine agent on Arc VMs.--enable-vm-config-agent: Set this parameter tofalseto prevent the onboarding of the VM agent on the VM from the host via Hyper-V sockets channel. Windows Server 2012 and Windows Server 2012 R2 do not support Hyper-V sockets. In the newer image versions that support Hyper-V sockets, the VM agent is used to onboard the Azure Connected Machine agent on Arc VMs. For more information on Hyper-V sockets, see Make your own integration services.
Create a Linux VM
To create a Linux VM, use the same command that you used to create the Windows VM.
- The gallery image specified should be a Linux image.
- The username and password works with the
authentication-type-allparameter. - For SSH keys, you need to pass the
ssh-key-valuesparameters along with theauthentication-type-all.
Important
Setting the proxy server during VM creation is supported for Ubuntu Server VMs.
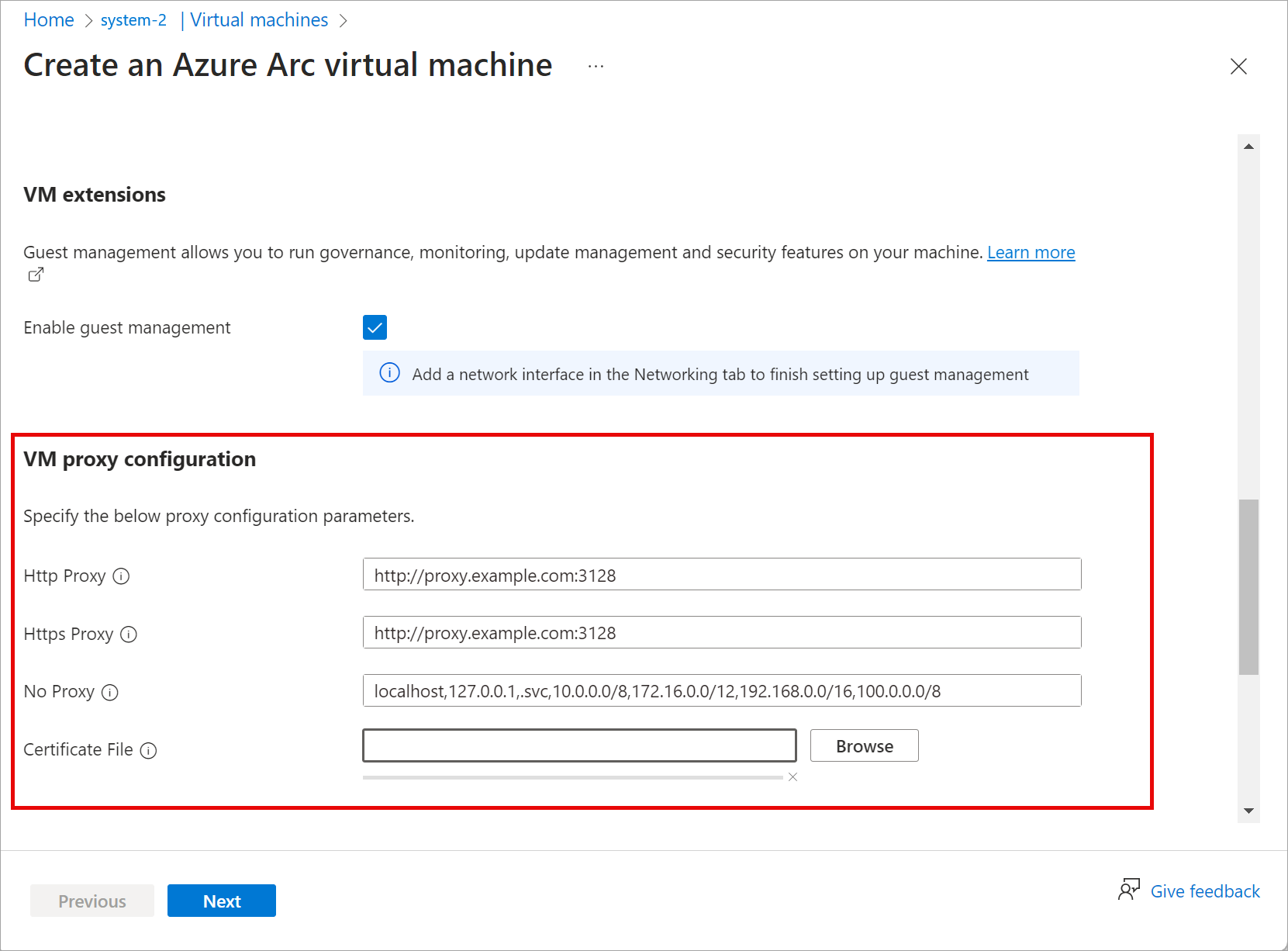
Create a VM with proxy configured
Use this optional parameter proxy-configuration to configure a proxy server for your VM.
Proxy configuration for Arc VMs is applied only to the onboarding of the Azure connected machine agent and set as environment variables within the guest VM operating system. Browsers and applications on the VM are not necessarily all enabled with this proxy configuration.
As such, you may need to specifically set the proxy configuration for your applications if they don't reference the environment variables set within the VM.
If creating a VM behind a proxy server, run the following command:
az stack-hci-vm create --name $vmName --resource-group $resource_group --admin-username $userName --admin-password $password --computer-name $computerName --image $imageName --location $location --authentication-type all --nics $nicName --custom-location $customLocationID --hardware-profile memory-mb="8192" processors="4" --storage-path-id $storagePathId --proxy-configuration http_proxy="<Http URL of proxy server>" https_proxy="<Https URL of proxy server>" no_proxy="<URLs which bypass proxy>" cert_file_path="<Certificate file path for your machine>"
You can input the following parameters for proxy-server-configuration:
| Parameters | Description |
|---|---|
| http_proxy | HTTP URLs for proxy server. An example URL is:http://proxy.example.com:3128. |
| https_proxy | HTTPS URLs for proxy server. The server may still use an HTTP address as shown in this example: http://proxy.example.com:3128. |
| no_proxy | URLs, which can bypass proxy. Typical examples would be localhost,127.0.0.1,.svc,10.0.0.0/8,172.16.0.0/12,192.168.0.0/16,100.0.0.0/8. |
| cert_file_path | Select the certificate file used to establish trust with your proxy server. An example is: C:\Users\Palomino\proxycert.crt. |
Here's a sample command:
az stack-hci-vm create --name $vmName --resource-group $resource_group --admin-username $userName --admin-password $password --computer-name $computerName --image $imageName --location $location --authentication-type all --nics $nicName --custom-location $customLocationID --hardware-profile memory-mb="8192" processors="4" --storage-path-id $storagePathId --proxy-configuration http_proxy="http://ubuntu:ubuntu@192.168.200.200:3128" https_proxy="http://ubuntu:ubuntu@192.168.200.200:3128" no_proxy="localhost,127.0.0.1,.svc,10.0.0.0/8,172.16.0.0/12,192.168.0.0/16,100.0.0.0/8,s-cluster.test.contoso.com" cert_file_path="C:\ClusterStorage\UserStorage_1\server.crt"
For proxy authentication, you can pass the username and password combined in a URL as follows:"http://username:password@proxyserver.contoso.com:3128".
Use managed identity to authenticate Arc VMs
When the Arc VMs are created on your Azure Local via Azure CLI or Azure portal, a system-assigned managed identity is also created that lasts for the lifetime of the Arc VMs.
The Arc VMs on Azure Local are extended from Arc-enabled servers and can use system-assigned managed identity to access other Azure resources that support Microsoft Entra ID-based authentication. For example, the Arc VMs can use a system-assigned managed identity to access the Azure Key Vault.
For more information, see system-assigned managed identities and Authenticate against Azure resource with Azure Arc-enabled servers.