Azure Benefits on Azure Stack HCI (22H2 and earlier)
Applies to: Azure Stack HCI, version 22H2
Important
Azure Stack HCI is now part of Azure Local. However, older versions of Azure Stack HCI, for example 22H2 will continue to reference Azure Stack HCI and won't reflect the name change. Learn more.
Note
This article is only for Azure Stack HCI version 22H2 and earlier. For a list of benefits associated with version 23H2 and later, see Azure verification for VMs.
Microsoft Azure offers a range of differentiated workloads and capabilities that are designed to run only on Azure. Azure Stack HCI extends many of the same benefits you get from Azure, while running on the same familiar and high-performance on-premises or edge environments.
Azure Benefits makes it possible for supported Azure-exclusive workloads to work outside of the cloud. You can enable Azure Benefits on Azure Stack HCI at no extra cost. If you have Windows Server workloads, we recommend turning it on.
Take a few minutes to watch the introductory video on Azure Benefits:
Azure Benefits available on Azure Stack HCI
Turning on Azure Benefits enables you to use these Azure-exclusive workloads on Azure Stack HCI:
| Workload | Versions supported | What it is |
|---|---|---|
| Windows Server Datacenter: Azure Edition | 2022 edition or later | An Azure-only guest operating system that includes all the latest Windows Server innovations and other exclusive features. Learn more: Automanage for Windows Server |
| Extended Security Update (ESUs) | October 12, 2021 security updates or later | A program that allows customers to continue to get security updates for End-of-Support SQL Server and Windows Server VMs, now free when running on Azure Stack HCI. For more information, see Extended security updates (ESU) on Azure Stack HCI. |
| Azure Policy guest configuration | Arc agent version 1.13 or later | A feature that can audit or configure OS settings as code, for both host and guest machines. Learn more: Understand the guest configuration feature of Azure Policy |
| Azure Virtual Desktop | For multi-session editions only. Windows 10 Enterprise multi-session or later. | A service that enables you to deploy Azure Virtual Desktop session hosts on your Azure Stack HCI infrastructure. For more information, see the Azure Virtual Desktop for Azure Stack HCI overview. |
How it works
This section is optional reading, and explains more about how Azure Benefits on HCI works "under the hood."
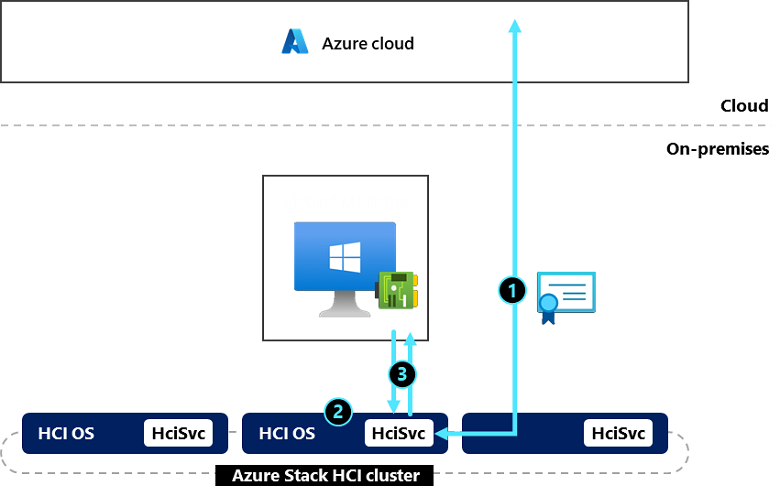
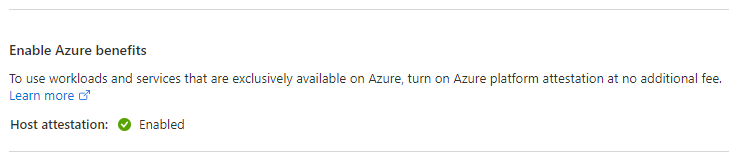
Azure Benefits relies on a built-in platform attestation service on Azure Stack HCI, and helps to provide assurance that VMs are indeed running on Azure environments.
This service is modeled after the same IMDS Attestation service that runs in Azure, in order to enable some of the same workloads and benefits available to customers in Azure. Azure Benefits returns an almost identical payload. The main difference is that it runs on-premises, and therefore guarantees that VMs are running on Azure Stack HCI instead of Azure.
Turning on Azure Benefits starts the service running on your Azure Stack HCI cluster:
On every server, HciSvc obtains a certificate from Azure, and securely stores it within an enclave on the server.
Note
Certificates are renewed every time the Azure Stack HCI cluster syncs with Azure, and each renewal is valid for 30 days. As long as you maintain the usual 30 day connectivity requirements for Azure Stack HCI, no user action is required.
HciSvc exposes a private and non-routable REST endpoint, accessible only to VMs on the same server. To enable this endpoint, an internal vSwitch is configured on the Azure Stack HCI host (named AZSHCI_HOST-IMDS_DO_NOT_MODIFY). VMs then must have a NIC configured and attached to the same vSwitch (AZSHCI_GUEST-IMDS_DO_NOT_MODIFY).
Note
Modifying or deleting this switch and NIC prevents Azure Benefits from working properly. If errors occur, disable Azure Benefits using Windows Admin Center or the PowerShell instructions that follow, and then try again.
Consumer workloads (for example, Windows Server Azure Edition guests) request attestation. HciSvc then signs the response with an Azure certificate.
Note
You must manually enable access for each VM that needs Azure Benefits.
Enable Azure Benefits
Before you begin, you'll need the following prerequisites:
An Azure Stack HCI cluster:
- Install updates: Version 21H2, with at least the December 14, 2021 security update KB5008223 or later.
- Register Azure Stack HCI: All servers must be online and registered to Azure.
- Install Hyper-V and RSAT-Hyper-V-Tools.
If you're using Windows Admin Center:
- Windows Admin Center (version 2103 or later) with Cluster Manager extension (version 2.41.0 or later).
You can enable Azure Benefits on Azure Stack HCI using Windows Admin Center, PowerShell, Azure CLI, or Azure portal. The following sections describe each option.
Note
To successfully enable Azure Benefits on Generation 1 VMs, the VM must first be powered off to enable the NIC to be added.
Manage Azure Benefits
In Windows Admin Center, select Cluster Manager from the top drop-down menu, navigate to the cluster that you want to activate, then under Settings, select Azure Benefits.
In the Azure Benefits pane, select Turn on. By default, the checkbox to turn on for all existing VMs is selected. You can deselect it and manually add VMs later.
Select Turn on again to confirm setup. It may take a few minutes for servers to reflect the changes.
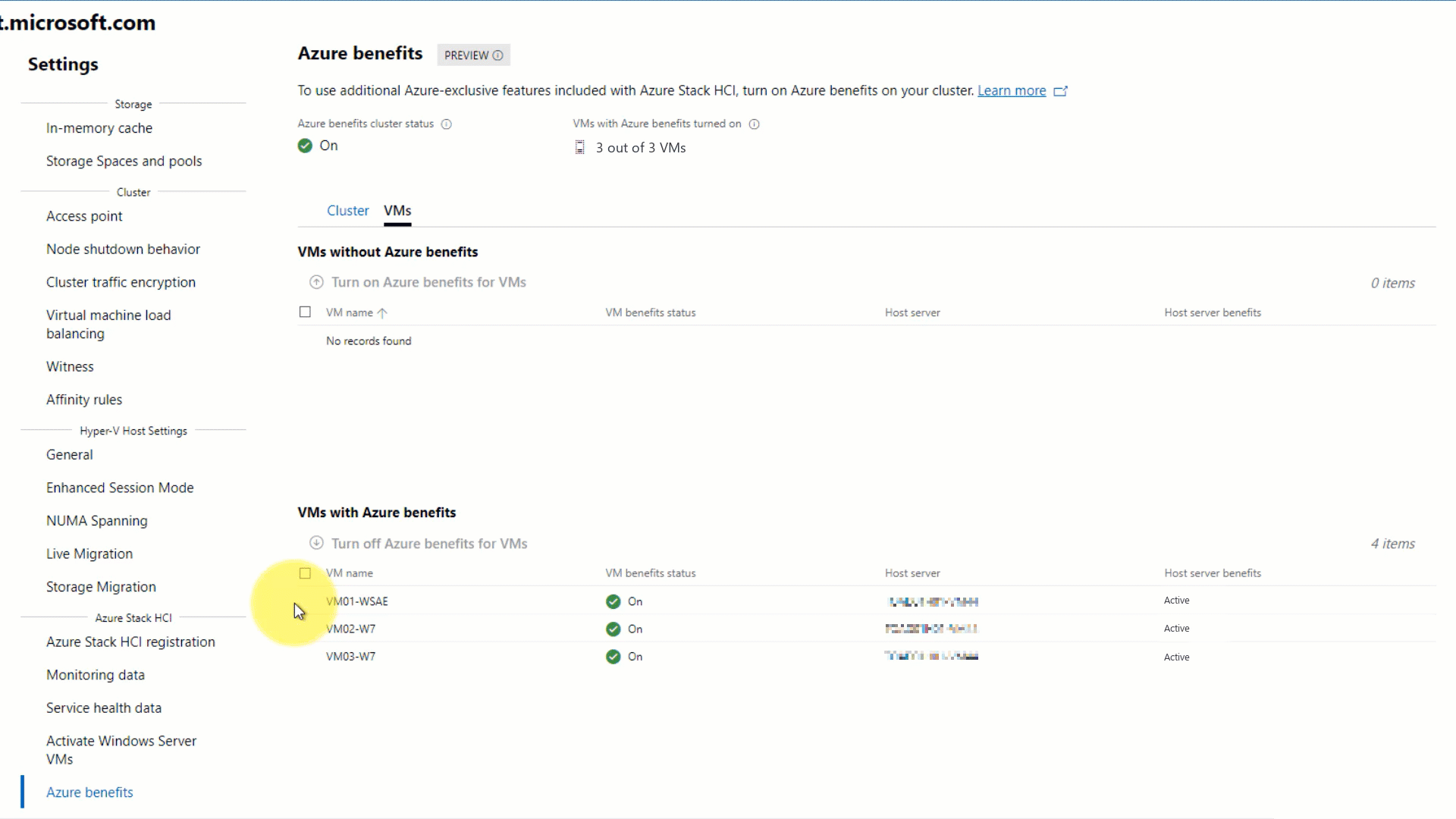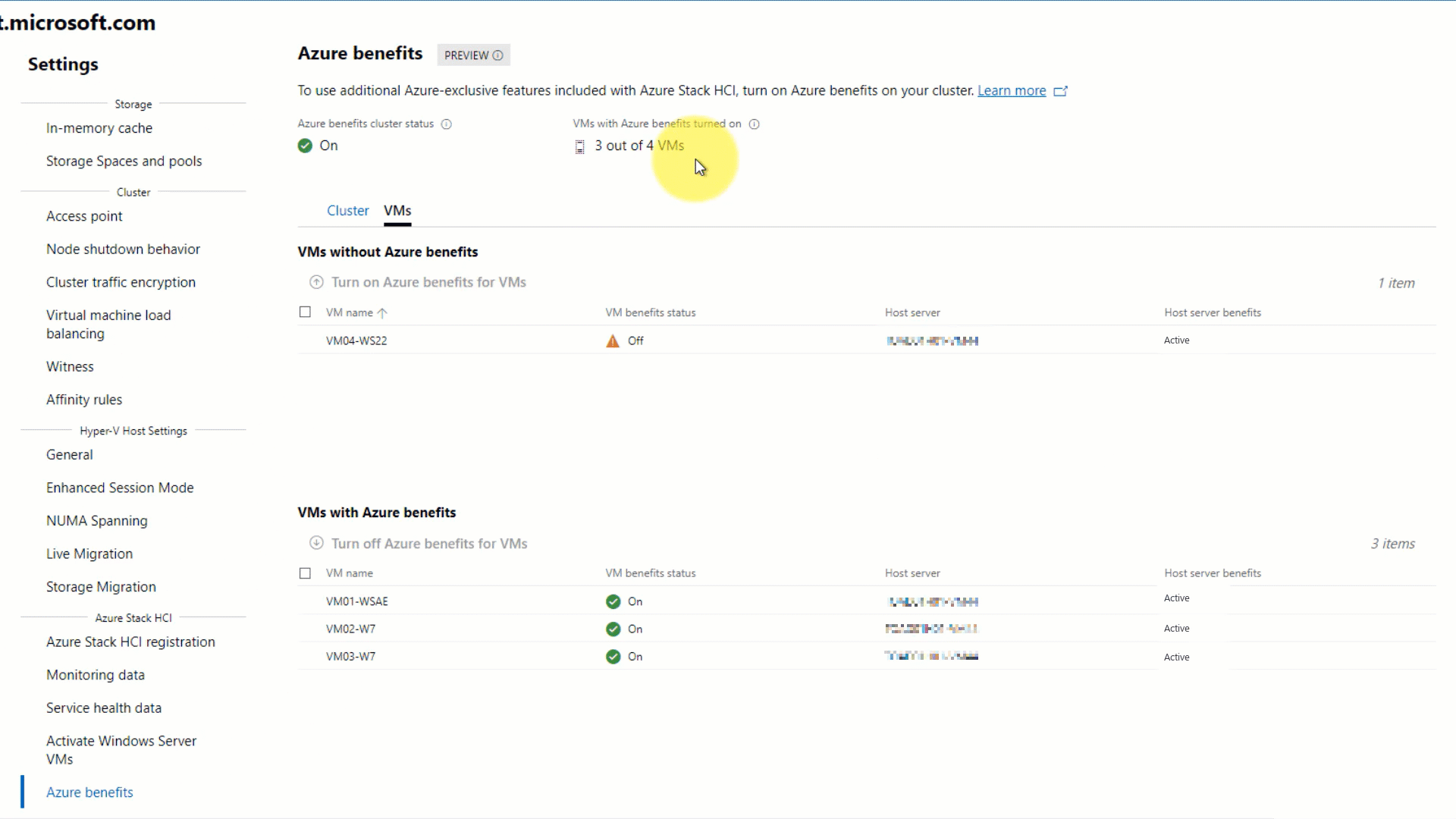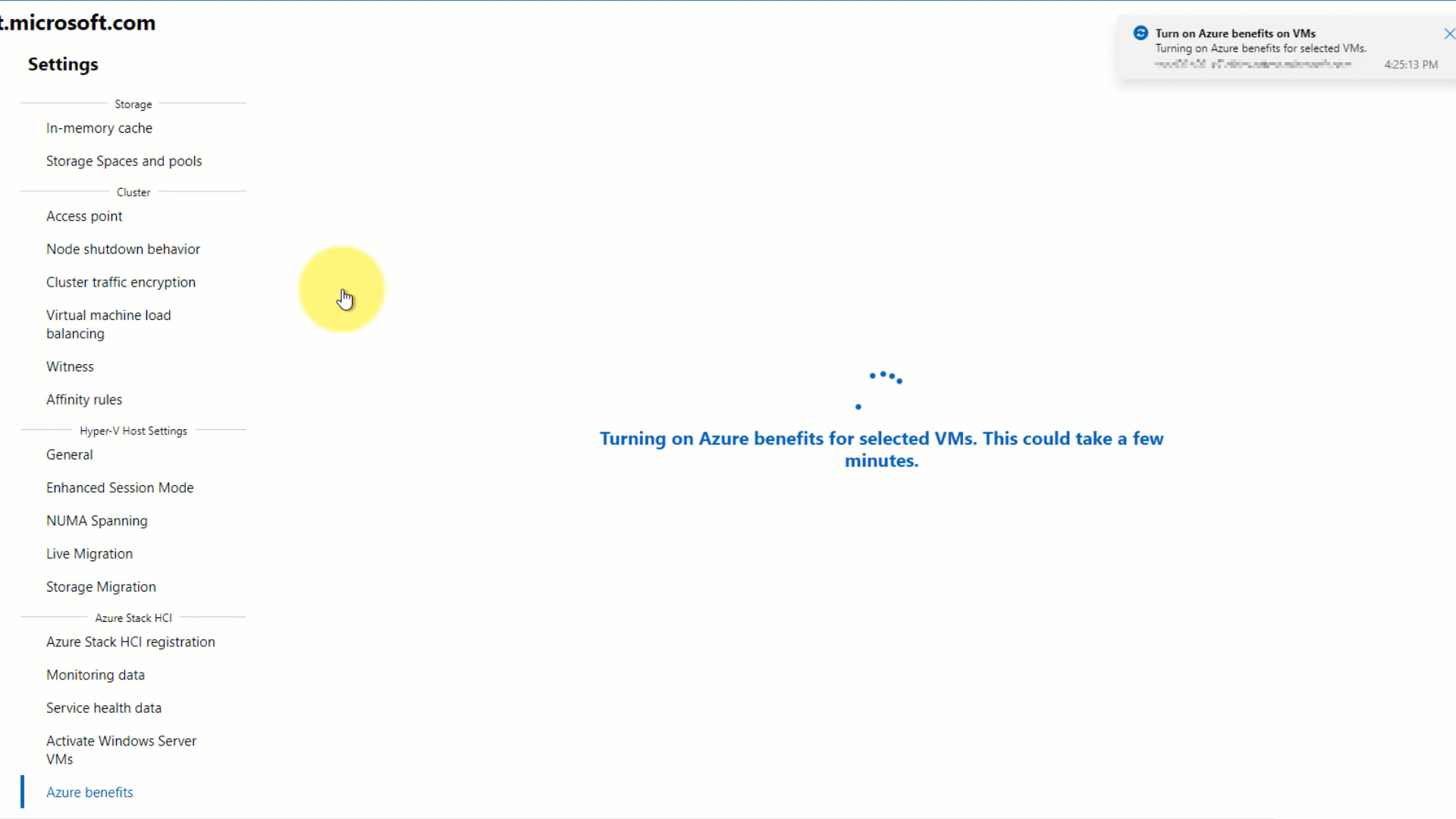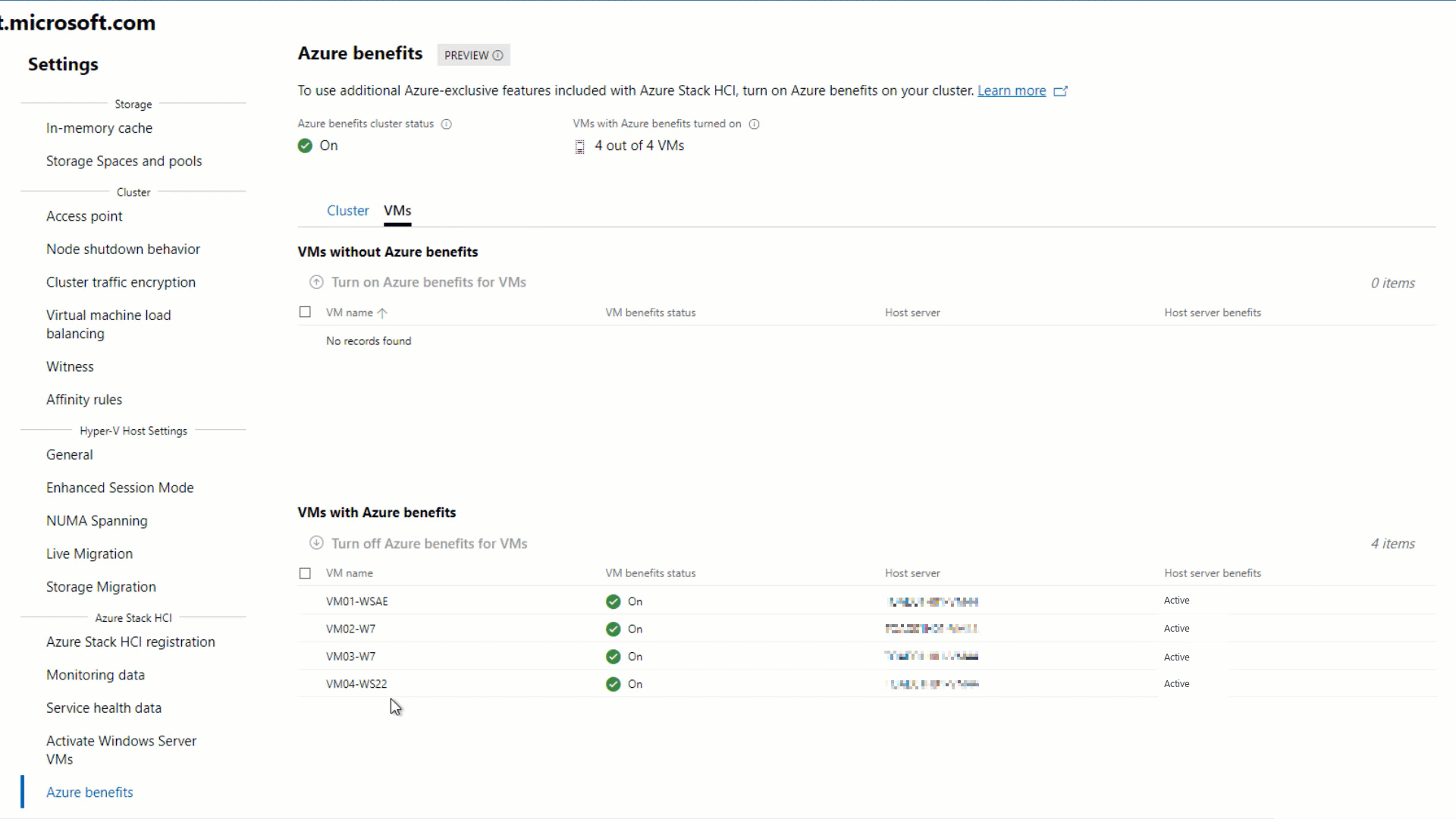
When Azure Benefits setup is successful, the page updates to show the Azure Benefits dashboard. To check Azure Benefits for the host:
- Check that Azure Benefits cluster status appears as On.
- Under the Cluster tab in the dashboard, check that Azure Benefits for every server shows as Active in the table.
To check access to Azure Benefits for VMs: Check the status for VMs with Azure Benefits turned on. It's recommended that all of your existing VMs have Azure Benefits turned on; for example, 3 out of 3 VMs.
Manage access to Azure Benefits for your VMs - Windows Admin Center
To turn on Azure Benefits for VMs, select the VMs tab, then select the VM(s) in the top table VMs without Azure Benefits, and then select Turn on Azure Benefits for VMs.
Manage access to Azure Benefits for your VMs - Azure PowerShell
To turn on benefits for selected VMs, run the following command on your Azure Stack HCI cluster:
Add-AzStackHCIVMAttestation [-VMName]Or, to add all existing VMs, run the following command:
Add-AzStackHCIVMAttestation -AddAllOptionally, to check that the VMs can access Azure Benefits on the host, run the following command on the VM:
Invoke-RestMethod -Headers @{"Metadata"="true"} -Method GET -Uri "http://169.254.169.253:80/metadata/attested/document?api-version=2018-10-01"
Troubleshoot via Windows Admin Center
- To turn off and reset Azure Benefits on your cluster:
- On the Cluster tab, select Turn off Azure Benefits.
- To remove access to Azure Benefits for VMs:
- On the VM tab, select the VM(s) in the top table VMs without Azure Benefits, and then select Turn on Azure Benefits for VMs.
- Under the Cluster tab, one or more servers appear as Expired:
- If Azure Benefits for one or more servers hasn't synced with Azure for more than 30 days, it appears as Expired or Inactive. Select Sync with Azure to schedule a manual sync.
- Under the VM tab, host server benefits appear as Unknown or Inactive:
- You won't be able to add or remove Azure Benefits for VMs on these host servers. Go to the Cluster tab to fix Azure Benefits for host servers with errors, then try to manage VMs again.
Troubleshoot via PowerShell
To turn off and reset Azure Benefits on your cluster, run the following command:
Disable-AzStackHCIAttestation -RemoveVMTo remove access to Azure Benefits for selected VMs:
Remove-AzStackHCIVMAttestation -VMName <string>Or, to remove access for all existing VMs:
Remove-AzStackHCIVMAttestation -RemoveAllIf Azure Benefits for one or more servers isn't yet synced and renewed with Azure, it may appear as Expired or Inactive. Schedule a manual sync:
Sync-AzureStackHCIIf a server is newly added and hasn't yet been set up with Azure Benefits, it may appear as Inactive. To add the new server, run setup again:
Enable-AzStackHCIAttestation
FAQ
This FAQ provides answers to some questions about using Azure Benefits.
What Azure-exclusive workloads can I enable with Azure Benefits?
See the full list here.
Does it cost anything to turn on Azure Benefits?
No, turning on Azure Benefits incurs no extra fees.
Can I use Azure Benefits on environments other than Azure Stack HCI?
No, Azure Benefits is a feature built into the Azure Stack HCI OS, and can only be used on Azure Stack HCI.
I have set up Azure Benefits on my cluster. How do I ensure that Azure Benefits stays active?
- In most cases, there's no user action required. Azure Stack HCI automatically renews Azure Benefits when it syncs with Azure.
- However, if the cluster disconnects for more than 30 days and Azure Benefits shows as Expired, you can manually sync using PowerShell and Windows Admin Center. For more information, see syncing Azure Stack HCI.
What happens when I deploy new VMs, or delete VMs?
- When you deploy new VMs that require Azure Benefits, you can manually add new VMs to access Azure Benefits using Windows Admin Center or PowerShell, using the preceding instructions.
- You can still delete and migrate VMs as usual. The NIC AZSHCI_GUEST-IMDS_DO_NOT_MODIFY will still exist on the VM after migration. To clean up the NIC before migration, you can remove VMs from Azure Benefits using Windows Admin Center or PowerShell using the preceding instructions, or you can migrate first and manually delete NICs afterwards.
What happens when I add or remove servers?
- When you add a server, you can navigate to the Azure Benefits page in Windows Admin Center, and a banner will appear with a link to Enable inactive server.
- Or, you can run
Enable-AzStackHCIAttestation [[-ComputerName] <String>]in PowerShell. - You can still delete servers or remove them from the cluster as usual. The vSwitch AZSHCI_HOST-IMDS_DO_NOT_MODIFY will still exist on the server after removal from the cluster. You can leave it if you're planning to add the server back to the cluster later, or you can remove it manually.