Configure Arc proxy manually for Azure gateway on Azure Local (preview)
Applies to: Azure Local 2411.1 and later
After creating the Arc gateway resource in your Azure subscription, you can enable the new Arc gateway preview features. This article details how to manually configure the Arc proxy before Arc registration.
Important
This feature is currently in PREVIEW. See the Supplemental Terms of Use for Microsoft Azure Previews for legal terms that apply to Azure features that are in beta, preview, or otherwise not yet released into general availability.
Prerequisites
Make sure the following prerequisites are met before proceeding:
You've access to an Azure Local instance running release 2411.1 or later. Prior versions do not support this scenario.
An Arc gateway resource created in the same subscription as used to deploy Azure Local. For more information, see Create the Arc gateway resource in Azure.
Step 1: Manually configure the proxy
If you need to configure the Arc proxy on your Azure Local machines before starting the Arc registration process, follow the instructions at Configure proxy settings for Azure Local.
Ensure that you configure the proxy and the bypass list for all the machines on your system.
Step 2: Get the ArcGatewayID
You need the proxy and the Arc gateway ID (ArcGatewayID) from Azure to run the registration script on Azure Local machines. You can find the Arc gateway ID on the Azure portal overview page of the resource.
Step 3: Register new machines in Azure Arc
To register new version 2408 or version 2411 machines in Azure Arc, you run the initialization script by passing the ArcGatewayID parameter and the proxy server parameters. Here's an example of how you should change the Invoke-AzStackHciArcInitialization parameters on the initialization script:
#Define the subscription where you want to register your server as Arc device.
$Subscription = "yoursubscription>"
#Define the resource group where you want to register your server as Arc device.
$RG = "yourresourcegroupname"
#Define the tenant you will use to register your server as Arc device.
$Tenant = "yourtenant"
#Define Proxy Server if necessary
$ProxyServer = "http://x.x.x.x:port"
#Define the Arc gateway resource ID from Azure
$ArcgwId = "/subscriptions/yoursubscription/resourceGroups/yourresourcegroupname/providers/Microsoft.HybridCompute/gateways/yourarcgatewayname"
#Connect to your Azure account and subscription
Connect-AzAccount -SubscriptionId $Subscription -TenantId $Tenant -DeviceCode
#Get the Access Token and Account ID for the registration
$ARMtoken = (Get-AzAccessToken).Token
#Get the Account ID for the registration
$id = (Get-AzContext).Account.Id
#Invoke the registration script with Proxy and ArcgatewayID
Invoke-AzStackHciArcInitialization -SubscriptionID $Subscription -ResourceGroup $RG -TenantID $Tenant -Region australiaeast -Cloud "AzureCloud" -ArmAccessToken $ARMtoken -AccountID $id -Proxy $ProxyServer -ArcGatewayID $ArcgwId
Step 4: Start Azure Local cloud deployment
Once the Azure Local machines are registered in Azure Arc and all the extensions are installed, you can start deployment from Azure portal or using the ARM templates that are documented in these articles:
Step 5: Verify that the setup succeeded
Once the deployment validation starts, you can connect to the first Azure Local machine from your system and open the Arc gateway log to monitor which endpoints are redirected to the Arc gateway and which ones continue using your firewall or proxy.
You can find the Arc gateway log at: c:\programdata\AzureConnectedMAchineAgent\Log\arcproxy.log.
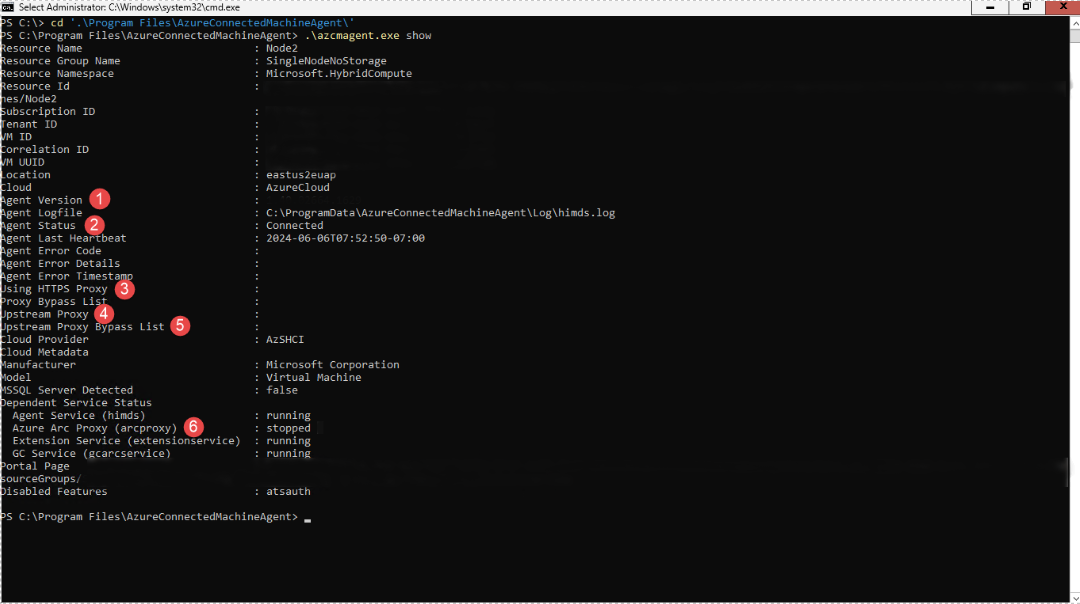
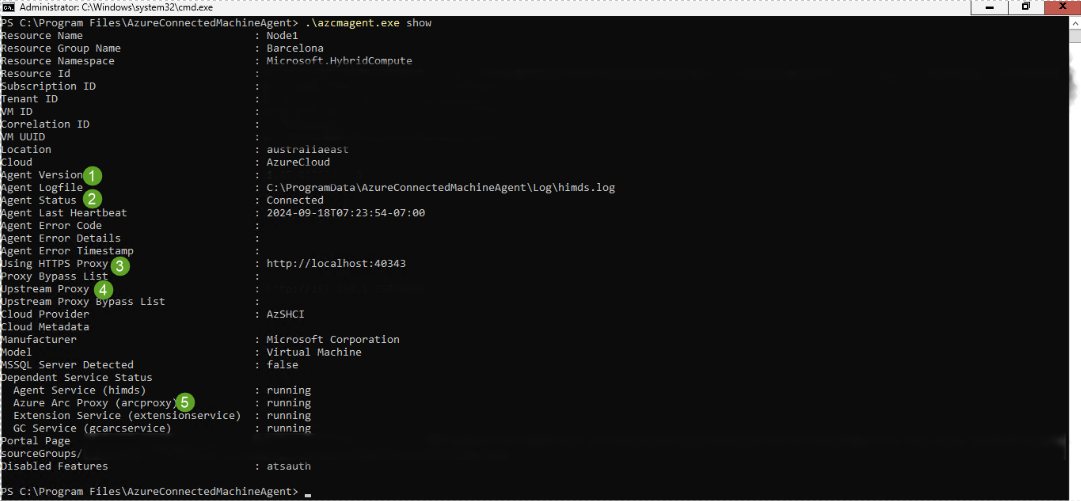
To check the Arc agent configuration and verify that it is using the Arc gateway, run the following command: c:\program files\AzureConnectedMachineAgent>.\azcmagent show
The result should show the following values:
Agent version is 1.45 or above.
Agent Status is Connected.
Using HTTPS Proxy is empty when Arc gateway isn't in use. It should show as
http://localhost:40343when the Arc gateway is enabled.Upstream Proxy shows your enterprise proxy server and port.
Azure Arc Proxy shows as stopped when Arc gateway isn't in use, and running when the Arc gateway is enabled.
The Arc agent without the Arc gateway:
The Arc agent using the Arc gateway:
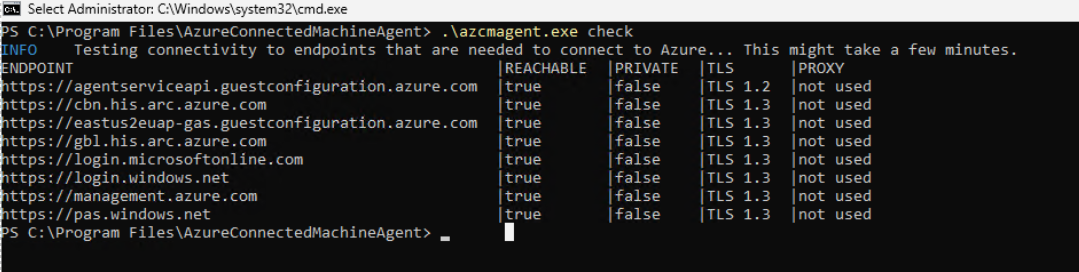
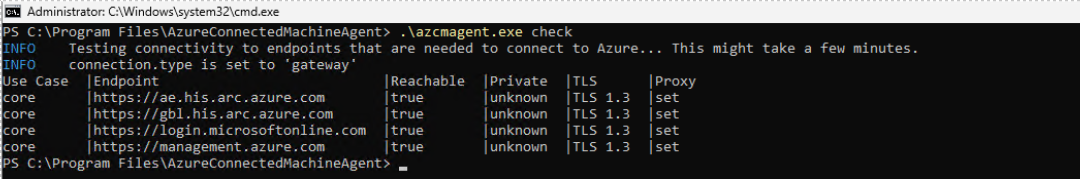
Additionally, to verify that the setup successful, you can run the following command: c:\program files\AzureConnectedMachineAgent>.\azcmagent check.
The response should indicate that connection.type is set to gateway, and the Reachable column should indicate true for all URLs, as shown:
The Arc agent without the Arc gateway:
The Arc agent with the Arc gateway enabled:
You can also audit your gateway traffic by viewing the gateway router logs.
To view gateway router logs on Windows, run the azcmagent logs command in PowerShell. In the resulting .zip file, the logs are located in the C:\ProgramData\Microsoft\ArcGatewayRouter folder.
Next steps
This feature is available only in Azure Local 2411.1 or later.