Information security has always been a complex subject, and it evolves quickly with the creative ideas and implementations of attackers and security researchers.
Security is one of the most important aspects of any architecture. Good security provides confidentiality, integrity, and availability assurances against deliberate attacks and abuse of your valuable data and systems. Losing these assurances can harm your business operations and revenue, and your organization's reputation.
Note
Learn how cloud security is an ongoing journey of incremental progress and maturity, in Security in the Microsoft Cloud Adoption Framework for Azure. Learn how to build security into your solution, in the Azure Well-Architected Framework Overview of the security pillar.
Here are some broad categories to consider when you design a security system:
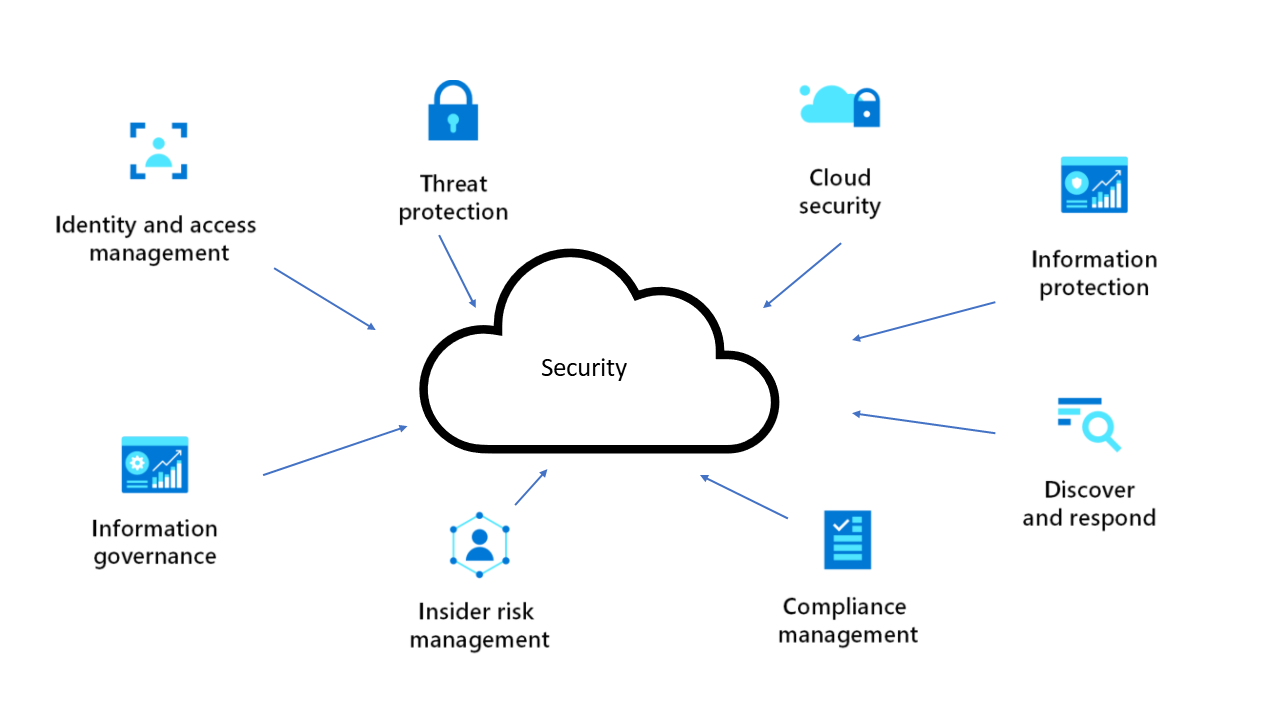
Azure provides a wide range of security tools and capabilities. These are just some of the key security services available in Azure:
- Microsoft Defender for Cloud. A unified infrastructure security management system that strengthens the security posture of your datacenters. It also provides advanced threat protection across your hybrid workloads in the cloud and on-premises.
- Microsoft Entra ID. The Microsoft cloud-based identity and access management service.
- Azure Front Door. A global, scalable entry-point that uses the Microsoft global edge network to create fast, highly secure, and widely scalable web applications.
- Azure Firewall. A cloud-native, intelligent network firewall security service that provides threat protection for your cloud workloads that run in Azure.
- Azure Key Vault. A high-security secret store for tokens, passwords, certificates, API keys, and other secrets. You can also use Key Vault to create and control the encryption keys used to encrypt your data.
- Azure Private Link. A service that enables you to access Azure PaaS services, Azure-hosted services that you own, or partner services over a private endpoint in your virtual network.
- Azure Application Gateway. An advanced web traffic load balancer that enables you to manage traffic to your web applications.
- Azure Policy. A service that helps you enforce organizational standards and assess compliance.
For a more comprehensive description of Azure security tools and capabilities, see End-to-end security in Azure.
Introduction to security on Azure
If you're new to security on Azure, the best way to learn more is with Microsoft Learn training. This free online platform provides interactive training for Microsoft products and more.
Here are two learning paths to get you started:
Path to production
- To secure Azure application workloads, you use protective measures like authentication and encryption in the applications themselves. You can also add security layers to the virtual machine (VM) networks that host the applications. See Firewall and Application Gateway for virtual networks for an overview.
- Zero Trust is a proactive, integrated approach to security across all layers of the digital estate. It explicitly and continuously verifies every transaction, asserts least privilege, and relies on intelligence, advanced detection, and real-time response to threats.
- For an implementation strategy for web apps, see Zero Trust network for web applications with Azure Firewall and Application Gateway.
- Azure governance establishes the tooling needed to support cloud governance, compliance auditing, and automated guardrails. See Azure governance design area guidance for information about governing your Azure environment.
Best practices
The Azure Well-Architected Framework is a set of guiding tenets, based on five pillars, that you can use to improve the quality of your architectures. For information, see Overview of the security pillar and Security design principles in Azure.
The Well-Architected Framework also provides these checklists:
- Azure identity and access management considerations
- Network security
- Data protection considerations
- Governance, risk, and compliance
Security architectures
Identity and access management
Threat protection
Stay current with security
Get the latest updates on Azure security services and features.
Additional resources
Example solutions
- Improved-security access to multitenant web apps from an on-premises network
- Restrict interservice communications
- Securely managed web applications
- Secure your Microsoft Teams channel bot and web app behind a firewall
- Web app private connectivity to Azure SQL database
Browse all our security architectures.
AWS or Google Cloud professionals
- Security and identity with Azure and AWS
- AWS to Azure services comparison - Security
- Google Cloud to Azure services comparison - Security
Next steps
Security architecture is part of a comprehensive set of security guidance that also includes:
- Security in the Microsoft Cloud Adoption Framework for Azure: A high-level overview of a cloud security end state.
- Azure Well-Architected Framework: Guidance on securing your workloads on Azure.
- Azure security benchmarks: Prescriptive best practices and controls for Azure security.
- End-to-end security in Azure: Documentation that introduces you to the security services in Azure.
- Top 10 security best practices for Azure: Top Azure security best practices that Microsoft recommends based on lessons learned across customers and our own environments.
- Microsoft Cybersecurity Architectures: The diagrams describe how Microsoft security capabilities integrate with Microsoft platforms and 3rd-party platforms.