Tutorial: Configure Microsoft Dynamics 365 Fraud Protection with Azure Active Directory B2C
Organizations can use Microsoft Dynamics 365 Fraud Protection (DFP) to assess risk during attempts to create fraudulent accounts and sign-ins. Customers use Microsoft DFP assessment to block or challenge suspicious attempts to create new, fake accounts, or to compromise accounts.
In this tutorial, learn how to integrate Microsoft DFP with Azure Active Directory B2C (Azure AD B2C). There's guidance on how to incorporate the Microsoft DFP device fingerprinting and account creation, and sign-in assessment API endpoints, into an Azure AD B2C custom policy.
Learn more: Overview of Microsoft Dynamics 365 Fraud Protection
Prerequisites
To get started, you'll need:
- An Azure subscription
- If you don't have one, you can get an Azure free account
- An Azure AD B2C tenant linked to your Azure subscription
- A Microsoft DFP subscription
- See, Dynamics 365 pricing
- You can set up a trial client version
Scenario description
Microsoft DFP integration includes the following components:
- Azure AD B2C tenant: Authenticates the user and acts as a client of Microsoft DFP. Hosts a fingerprinting script collecting identification and diagnostic data of users who execute a target policy. It blocks or challenges sign-in or sign-up attempts based on the rule evaluation result returned by Microsoft DFP.
- Custom UI templates: Customizes HTML content of the pages rendered by Azure AD B2C. These pages include the JavaScript snippet required for Microsoft DFP fingerprinting.
- Microsoft DFP fingerprinting service: Dynamically embedded script that logs device telemetry and self-asserted user details to create a uniquely identifiable fingerprint for the user.
- Microsoft DFP API endpoints: Provides the decision result and accepts a final status reflecting the operation undertaken by the client application. Azure AD B2C communicates with the Microsoft DFP endpoints using REST API connectors. API authentication occurs with a client_credentials grant to the Microsoft Entra tenant in which Microsoft DFP is licensed and installed to obtain a bearer token.
The following architecture diagram shows the implementation.
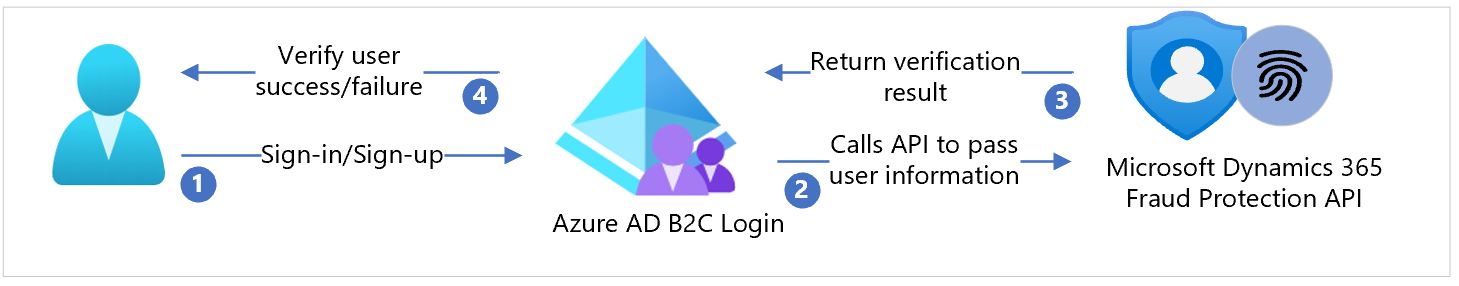
- The user arrives at a sign-in page, selects option to create a new account, and enters information. Azure AD B2C collects user attributes.
- Azure AD B2C calls the Microsoft DFP API and passes the user attributes.
- After Microsoft DFP API consumes the information and processes it, it returns the result to Azure AD B2C.
- Azure AD B2C receives information from the Microsoft DFP API. If failure occurs, an error message appears. With success, the user is authenticated and written into the directory.
Set up the solution
- Create a Facebook application configured to allow federation to Azure AD B2C.
- Add the Facebook secret you created as an Identity Experience Framework policy key.
Configure your application under Microsoft DFP
Set up your Microsoft Entra tenant to use Microsoft DFP.
Set up your custom domain
In a production environment, use a custom domain for Azure AD B2C and for the Microsoft DFP fingerprinting service. The domain for both services is in the same root DNS zone to prevent browser privacy settings from blocking cross-domain cookies. This configuration isn't necessary in a non-production environment.
See the following table for examples of environment, service, and domain.
| Environment | Service | Domain |
|---|---|---|
| Development | Azure AD B2C | contoso-dev.b2clogin.com |
| Development | Microsoft DFP Fingerprinting | fpt.dfp.microsoft-int.com |
| UAT | Azure AD B2C | contoso-uat.b2clogin.com |
| UAT | Microsoft DFP Fingerprinting | fpt.dfp.microsoft.com |
| Production | Azure AD B2C | login.contoso.com |
| Production | Microsoft DFP Fingerprinting | fpt.login.contoso.com |
Deploy the UI templates
- Deploy the provided Azure AD B2C UI templates to a public facing internet hosting service such as Azure Blob Storage.
- Replace the value
https://<YOUR-UI-BASE-URL>/with the root URL for your deployment location.
Note
Later, you'll need the base URL to configure Azure AD B2C policies.
- In the
ui-templates/js/dfp.jsfile, replace<YOUR-DFP-INSTANCE-ID>with your Microsoft DFP instance ID. - Ensure CORS is enabled for your Azure AD B2C domain name
https://{your_tenant_name}.b2clogin.comoryour custom domain.
Learn more: UI customization documentation
Azure AD B2C configuration
Add policy keys for your Microsoft DFP client app ID and secret
- In the Microsoft Entra tenant where Microsoft DFP is set up, create an Microsoft Entra application and grant admin consent.
- Create a secret value for this application registration. Note the application client ID and client secret value.
- Save the client ID and client secret values as policy keys in your Azure AD B2C tenant.
Note
Later, you'll need the policy keys to configure Azure AD B2C policies.
Replace the configuration values
In the provided custom policies, find the following placeholders and replace them with the corresponding values from your instance.
| Placeholder | Replace with | Notes |
|---|---|---|
| {Settings:Production} | Whether to deploy the policies in production mode | true or false |
| {Settings:Tenant} | Your tenant short name | your-tenant - from your-tenant.onmicrosoft.com |
| {Settings:DeploymentMode} | Application Insights deployment mode to use | Production or Development |
| {Settings:DeveloperMode} | Whether to deploy the policies in Application Insights developer mode | true or false |
| {Settings:AppInsightsInstrumentationKey} | Instrumentation key of your Application Insights instance* | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {Settings:IdentityExperienceFrameworkAppId}App ID of the IdentityExperienceFramework app configured in your Azure AD B2C tenant | 00001111-aaaa-2222-bbbb-3333cccc4444 |
|
| {Settings:ProxyIdentityExperienceFrameworkAppId} | App ID of the ProxyIdentityExperienceFramework app configured in your Azure AD B2C tenant | 00001111-aaaa-2222-bbbb-3333cccc4444 |
| {Settings:FacebookClientId} | App ID of the Facebook app you configured for federation with B2C | 000000000000000 |
| {Settings:FacebookClientSecretKeyContainer} | Name of the policy key, in which you saved Facebook's app secret | B2C_1A_FacebookAppSecret |
| {Settings:ContentDefinitionBaseUri} | Endpoint in where you deployed the UI files | https://<my-storage-account>.blob.core.windows.net/<my-storage-container> |
| {Settings:DfpApiBaseUrl} | The base path for your DFP API instance, found in the DFP portal | https://tenantname-00001111-aaaa-2222-bbbb-3333cccc4444.api.dfp.dynamics.com/v1.0/ |
| {Settings:DfpApiAuthScope} | The client_credentials scope for the DFP API service | https://api.dfp.dynamics-int.com/.default or https://api.dfp.dynamics.com/.default |
| {Settings:DfpTenantId} | The ID of the Microsoft Entra tenant (not B2C) where DFP is licensed and installed | 00001111-aaaa-2222-bbbb-3333cccc4444 or contoso.onmicrosoft.com |
| {Settings:DfpAppClientIdKeyContainer} | Name of the policy key-in which you save the DFP client ID | B2C_1A_DFPClientId |
| {Settings:DfpAppClientSecretKeyContainer} | Name of the policy key-in which you save the DFP client secret | B2C_1A_DFPClientSecret |
| {Settings:DfpEnvironment} | The ID of the DFP environment. | Environment ID is a global unique identifier of the DFP environment that you send the data to. Your custom policy should call the API endpoint, including the query string parameter x-ms-dfpenvid=your-env-id> |
*You can set up application insights in a Microsoft Entra tenant or subscription. This value is optional but recommended to assist with debugging.
Note
Add consent notification to the attribute collection page. Include notification that user telemetry and identity information is recorded for account protection.
Configure the Azure AD B2C policy
- Go to the Azure AD B2C policy in the Policies folder.
- Follow the instructions in custom policy starter pack to download the LocalAccounts starter pack.
- Configure the policy for the Azure AD B2C tenant.
Note
Update the provided policies to relate to your tenant.
Test the user flow
- Open the Azure AD B2C tenant and under Policies select Identity Experience Framework.
- Select your previously created SignUpSignIn.
- Select Run user flow.
- Application: The registered app (example is JWT).
- Reply URL: redirect URL.
- Select Run user flow.
- Complete the sign-up flow and create an account.
Tip
Microsoft DFP is called during the flow. If the flow is incomplete, confirm the user isn't saved in the directory.
Note
If using Microsoft DFP rule engine, update rules in the Microsoft DFP portal.