Active Directory Certificate Services (AD CS) Clustering
Applies To
Applies to: Windows Server 2008, Windows Server 2008 R2, Windows Server 2012, Windows Server 2012 R2
Download
This document is available for download from the TechNet Gallery
The Failover Clustering feature starting in Windows Server 2008 provides a high grade of reliability that can now be leveraged by Microsoft Active Directory® Certificate Services.
With Microsoft Windows Server 2003 and earlier versions, multiple CAs had to be deployed into an infrastructure to achieve redundancy of certificate services.
While you can still have multiple CAs operating in your Active Directory forest, with failover clustering, there is no need to deploy more than one CA to protect certificate services from unexpected failure.
Scope
This guide describes the steps required to set up failover clustering starting with Windows Server 2008 and to deploy a CA on shared storage with or without a network hardware security module (HSM).
Shared storage is always a requirement for Failover Clustering. The network HSM ensures strong protection of the CA key material and represents a shared key store at the same time. The active node can always connect to the network HSM regardless of which physical node the cluster runs on.
Windows Versions That Support Certificate Services Clustering
Clustering support for certificate services is provided by the following versions of Windows.
- Windows Server 2008, Enterprise Edition
- Windows Server 2008, Datacenter Edition
- Windows Server 2008 R2, Enterprise Edition
- Windows Server 2008 R2, Datacenter Edition
- Windows Server 2012
- Windows Server 2012 R2
Cluster Requirements
To run certificate services in a clustered environment, you must understand the prerequisites and under what circumstances a CA cluster is supported.
- A Cluster can only run a single instance of Certificate Services. A failover cluster of any size can be used to provide a high availability environment for certificate services. However, Microsoft does not support more than one instance of certificate services on a cluster.
- Shared storage is required. To store the CA database and the log database for certificate services, a shared storage must be available to all cluster nodes that form the cluster.
Supported Deployment Scenarios
Deploying AD CS on a failover cluster can accomplish a number of goals for customer environments. These goals are often determined by existing certificate services servers in an environment. There are a number of ways in which a failover cluster can be deployed.
- A completely new Public Key Infrastructure. A new clustered certificate services CA can be deployed to provide services in a fault-tolerant configuration even if an existing PKI is already in place.
- A migration from an existing Windows 2003 or Windows 2008 Certificate Services CA. In this scenario, an environment has one or more CAs that need to be preserved and migrated to a Windows 2008 failover cluster. See AD CS Migration Guide.
- Clustering is only supported for the CA service*. Microsoft is supporting clustered configurations of the CA service. Clustering is not supported for other CA role services like Online Certificate Status Protocol (OCSP), or Microsoft Simple Certificate Enrollment Protocol (SCEP).
- * When CAs are clustered, it is recommended that you do not install the Certification Authority Web Enrollment service on the clustered CAs. If you want to configure Certification Authority Web Enrollment, you should install it computers that are not part of the cluster. Refer to the Troubleshooting section on configuring Web Enrollment to work properly in a clustered environment.
Preparing the CA Cluster Environment
This section focuses on the preparation of the environment for Certificate Services Cluster.
Installing the Operating System on Cluster Nodes
To prepare the cluster nodes, you have to install Windows Server 2008 or Windows Server 2008 R2, Enterprise Edition or Windows Server "8" Beta on all cluster nodes. Deploying a failover cluster requires all cluster nodes to run the same operating system version.
Setting Up a Shared Storage
Configuring shared storage can be a complex task. This guide does not provide detailed information about how to configure the shared storage. To set up a shared storage disk for certificate services, see the configuration procedures that apply for your shared storage solution.
Plan the size of the shared storage appropriately for the number of certificates you plan to enroll. 64 KB is a safe estimation for a single certificate, including the certificate request and possibly a recover key.
Configuring a Network HSM
The configuration of a network HSM is specific to the configuration guidelines of the vendor. Since no common setup procedure exists, it is not addressed in this guide.
To make a network HSM available to your CA cluster, follow the steps in the documentation provided by the network HSM vendor.
Installing and Configuring the CA Cluster
The following sections describe the installation and configuration of a CA on a failover cluster running on Windows Server 2008, or Windows Server 2008 R2, or Windows Server "8" Beta.
Understanding Names Used in a Cluster Configuration
Before you begin, you should think about the names that are used during the installation procedure. It is important to have these names properly defined since they are used throughout the configuration.
The following table explains the names that are used in the subsequent sections. The step-by-step guidance refers to the underlined labels in the following list.
Cluster node name
- Description Every Windows computer has a name; therefore, computers acting as cluster nodes have a computer name.
- Configured where The computer name is configured in the computer’s properties of a Windows computer.
- Used by The computer names of the nodes are permitted on access control lists (ACLs) in the following Active Directory objects in the configuration naming context under Services – Public Key Services.
- Authority Information Access (AIA) – {CA name}
- CDP (CRL Distribution Point) – {Service name}
- Enrollment Services – {CA name}
- KRA (Key Recovery Agent) – {CA name}
Cluster name
- Description The failover cluster has a unique name that is registered in Active Directory.
- Configured where The cluster name is configured when the failover cluster is set up. See step 10 in “Creating a Failover Cluster”.
- Used by The name of the cluster is used to refer to a specific cluster in the Failover Cluster Management snap-in. There is no dependency in regards to the CA on this name.
Service name
- Description The service name represents the Domain Name System (DNS) name of the clustered CA service.
- Configured where The service name is configured when the CA is set up as a clustered service. See step 6 in “Configuring the Failover Cluster”.Used by The service name appears as part of the CA configuration string. The service name can be queried with certutil -caconfig dns at a command-line prompt. The service name is represented in the following Active Directory objects in the configuration naming context under Services – Public Key Services.
- Certificate Revocation List (CRL) Distribution Point (CDP) – {Service name}
CA name
- Description The CA is the actual name of the CA.
- Configured where The name of the CA is configured when the CA service is installed. See step 12 in “Setting Up the CA Server Role on the First Cluster Node”.
- Used by The CA name is part of the CA configuration string and is displayed as the node name in the Certification Authority Microsoft Management Console (MMC) Snap-in. The configuration string can be queried at a command line with certutil –cainfo dsname. The name is written into the Issuer attribute on every issued certificate and is also used in the following Active Directory objects in the configuration naming context under Services – Public Key Services.
- AIA – {CA name}
- CDP – {Service name} – {CA name}
- Certification Authorities – {CA name}
- Enrollment Services – {CA name}
- KRA – {CA name}
The following screenshots show where the names appear in the Failover Cluster Management Snap-in and in the Certification Authority Administration Snap-in. For illustration purposes, the objects are labeled according to the names described previously.
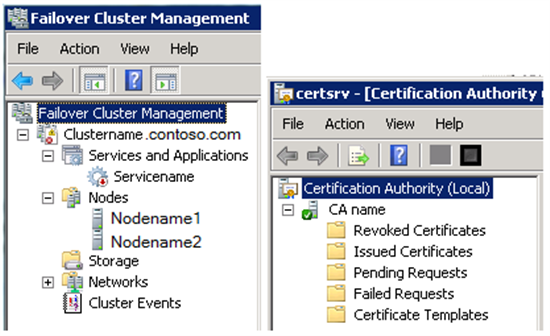
Setting Up the CA Server Role on the First Cluster Node
This section explains how to install certificate services on the first cluster node.
It is important to understand that the shared resources, like the disk storage that keeps the CA database and log file, must be available to the CA during setup. Releasing these resources for setting up the second node is also important after the setup of this node is finished.
Steps
Here are the steps to configure the first cluster node.
Logon with required permissions
- Log on to the cluster node with permissions to install the first cluster node. To install an enterprise CA, log on with enterprise permissions to the Active Directory domain. To install a stand-alone CA, you may log on with local administrator permissions if you do not want to register the CA in the Active Directory configuration container.
The next steps describe how to confirm that the shared disk is available to the node.
Shared disk configuration
- Click the Start button, point to Run, type servermanager.msc, and then click OK. Note: On Windows Server "8" Beta, run the command Windows PowerShell.
- The Server Manager MMC Snap-in opens. Expand the Storage node and select Disk Management.
- Make sure that the shared disk that is used for the CA is online.
HSM
If you are using a network HSM, to confirm that a network HSM is available to the first node
- Expand the Diagnostics node in the left pane of the Server Manager Snap-in, and then click Services.
- Make sure that the service that connects to the network HSM is started. Refer to the HSM vendor for service information.
Install Certificate Services on the first node
Now, you are going to install the Certificate Services on the first node.
In the left pane of the Server Manager Snap-in, select the Roles node.
On the Action menu, click Add Roles.
On the Select Server Roles page, mark Active Directory Certificate Services, and then click Next twice.
On the Select Role Services page, make sure that only Certification Authority is marked, and then click Next. No CA service other than the CA is supported in a clustered environment.
Select the setup type for the CA and click Next.
Select the CA type for the CA and click Next
Select Create a new private key and click Next.
- If you are using a network HSM, select the cryptographic service provider (CSP) provided by the HSM vendor from the list and set the desired key length. Click Next. Note this CSP name as you will need it in the next section when using the certutil –repairstore command.
Enter the CA name and click Next. For more information about the CA name, see “Understanding Names Used in a Cluster Configuration”.
If you are configuring a root CA, define the validity period. If using a subordinate CA, choose whether to submit the request online or save it to a file. Click Next
Change the default paths for the database and log files to the desired location on the shared storage drive setup in “Setting Up a Shared Storage”. Click Next.
Click Install
As a next step, the CA certificate must be exported.
Click the Start button, point to Run, type certsrv.msc, and then click OK. Note: On Windows Server "8" Beta, run the command in Windows PowerShell.
Select the CA node in the left pane.
On the Action menu, click All Tasks, and then click Backup CA.
On the Welcome page of the CA backup wizard, click Next.
Select Private key and CA certificate and provide a directory name where you want to temporarily store the CA certificate and optionally the key. Click Next.
Provide a password to protect the CA key and click Next.
Click Finish.
On the Action menu, click All Tasks, and then click Backup CA.
On the Welcome page of the CA backup wizard, click Next.
Select Private key and CA certificate and provide a directory name where you want to temporarily store the CA certificate and optionally the key. Click Next.
Provide a password to protect the CA key and click Next.
Click Finish.
If you are using a network HSM, a warning message will display telling you that the private key cannot be exported. This is expected behavior because the private key will never leave the HSM. Click OK to continue. |
Shut down CA to unlock disk resources
The CA service must be shut down to unlock the disk resources.
- While the CA is selected in the left pane, on the Action menu, click All Tasks, and then click Stop Service.
- Close the Certification Authority MMC Snap in.
Detach the shared storage from the cluster node.
- Go to the Server Manager MMC Snap-in, expand the Storage node, and then select Disk Management.
- Change the state of the disk keeping the CA database to offline.
Release the HSM from the cluster node.
- Expand the Diagnostics node in the left pane of the Server Manager view and click Services.
- Select the service that works with the HSM. On the Action menu, click Stop.
Log off Cluster node one
Log off Cluster node one.
The installation of the Certification Authority on the first node is now complete.** **
Setting Up the CA Server Role on additional Cluster Nodes
This section explains how to set up any additional cluster nodes.
The configuration of the additional nodes is slightly different from the first node. Some configuration settings are already defined on the first node so they only need to be applied on the other nodes.
Install the CA on another cluster node
- Log on to the cluster node with permissions to install the cluster node as previously explained.
- Confirm the shared disk available to the cluster node.
- Click the Start button, point to Run, type servermanager.msc, and then click OK. Note: On Windows Server "8" Beta, run the command in Windows PowerShell.
- The Server Manager MMC Snap-in opens. Expand the Storage node and select Disk Management.
- Make sure that the shared disk that is used for the CA is online.
If you are using a network HSM, to confirm that a network HSM is available to the node
- Expand the Diagnostics node in the left pane of the Server Manager Snap-in, and then click Services.
- Make sure that the service that connects to the network HSM is started. Refer to the HSM vendor for service information.
Importing the CA certificate into the local machine certificate store
- Copy the previously exported CA certificate to the second cluster node.
- Click the Start button, point to Run, type mmc, and then click OK. Note: On Windows Server "8" Beta, run the command Windows PowerShell.
- On the File menu, click Add/remove MMC Snap-in.
- Select Certificates from the list of available snap-ins and click Add.
- Select Computer account, click Finish twice, and then, click OK.
- In the Certificate Manager MMC Snap-in, expand the Certificates (Local Computer) node and select the Personal store.
- On the Action menu, click All Tasks, and then click Import.
- In the Certificate Import Wizard, click Next.
- Enter the file name of the CA certificate that was previously created on the first node and click Next. If you use the Browse button to find the certificate, change the file type to Personal Information Exchange (*.pfx,*.p12).
- Type the password that you have previously used to protect the private key. The password is required even if there is no private key in the PFX file. Do not mark this key as exportable. Click Next.
- Place the certificate in the Personal certificate store and click Next.
- To import the certificate, click Finish.
- To confirm the successful import, click OK.
- If you are using a network HSM, you must repair the association between the certificate and the private key that is stored in the HSM.
- In the Certificate Manager MMC Snap-in, expand the Personal store and select the Certificates container.
- Select the imported certificate. On the Action menu, click Open.
- Go to the Details tab.
- Select the field Serial Number, copy the serial number to the Clipboard, and then click OK.
- At a command-line prompt, type
certutil –repairstore –csp “{CSP Providername}” My "{Serialnumber}"
and then press ENTER.
For example: certutil –repairstore My "629bdaba68590bbd488c78e0ac57bc2b"
Installing Certificate Services on the node
- Return to Server Manager.
- In the left pane, select the Roles node.
- On the Action menu, click Add Roles.
- On the Select Server Roles page, mark Active Directory Certificate Services and click Next twice.
- On the Select Role Services page, make sure that only Certification Authority is marked and click Next. No CA service other than the CA is supported in a clustered environment.
- Select the exact same setup type for the CA that you used for the first node and click Next.
- Select the exact same CA type for the CA that you used for the first node and click Next.
- Select Use existing private key, choose Select a certificate and use its associated private key, then click Next.
- Select the CA certificate that was generated on the first node and click Next.
- Change the default paths for the database. In the dialog box stating that an existing database was found, select Yes to overwrite it.
- Change the default paths for the database log location. In the dialog box stating that an existing database was found, select Yes to overwrite it. Click Next to continue.
- Click Install.
- To finish the Role installation, click Close.
- Log off from the cluster node.** **
Setting Up the Failover Cluster Feature on Cluster Nodes
The Failover Cluster support is a feature in Windows Server 2008 Enterprise and Datacenter Edition.
Repeat the following steps on all cluster nodes that will potentially run the Active Directory Certificate Services.
- Log on to one of the cluster nodes with local administrator permissions.
- Click the Start button, point to Run, type servermanager.msc, and then click OK. Note: On Windows Server "8" Beta, run the command in Windows PowerShell.
- The Server Manager MMC Snap-in opens. In the left pane, select the Features node.
- On the Action menu, click Add Features.
- In the list of available features, mark Failover Clustering and click Next.
- Click Install.
- Click Close.
- Log on to the cluster node that is still attached to the shared storage drive.
- Click the Start button, point to Run, type Cluadmin.msc, and then click OK.
- If the Before you begin page appears, click Next.
- Enter the cluster node name (computer name) of the first cluster node and click Add. For more information about the cluster node name, see “Understanding Names Used in a Cluster Configuration”.
- Enter the cluster node name of the other cluster nodes and click Add.
- Click Next to continue.
- To perform the validation tests, chose Yes and click Next twice.
- Keep the default option to Run all tests and click Next twice.
- Verify the cluster test report and click Finish.
Creating a Failover Cluster
- Provide the cluster name. This name is not relevant for the later CA configuration. For more information about the CA name, see “Understanding Names Used in a Cluster Configuration”.
- View the cluster creating report and click Finish.
Configuring the Failover Cluster
Certificate services must be configured as a cluster resource.
- In the Failover Cluster Management Snap-in, select the Services and Applications node in the left pane.
- On the Action menu, click Configure a service or Application.
- If the Before you begin page appears, click Next.
- In the list of services and applications, select Generic Service and click Next.
- In the list of services, select Active Directory Certificate Services and click Next.
- Understanding Names Used in a Cluster Configuration ”.
- Mark the disk storage that is still mounted to the node and click Next.
- To configure a shared registry hive, click Add, type SYSTEM\CurrentControlSet\Services\CertSvc and then click OK.
- Click Next twice.
- Click Finish to complete the failover configuration for certificate services.
- In the left pane, expand the Services and Applications node and select the newly created clustered service.
- In the middle pane, select Generic Service. On the Action menu, click Properties.
- Change the Resource Name to Certification Authority and click OK.
At this stage, you can move the certification authority between all nodes.
If you have installed a service to access the network HSM, it is recommended that you create a dependency between the CA and the network HSM service. To configure this dependency, follow these optional steps:
- In the Failover Cluster Management Snap-in, select the Services and Applications node and select the previously created name of the clustered service in the middle pane. On the Action menu, select Add a resource and then Generic Service.
- The new resource wizard appears. In the list of available services, select the name of the service that was installed to connect to your network HSM. Click Next twice.
- Click Finish.
- Under the Services and Applications node in the left pane, click the name of the clustered services.
- Select the newly created Generic Service in the middle pane. On the Action menu, click Properties.
- On the General tab, rename the service name if desired and click OK.
- Make sure that the service is Online.
- Select the service previously named Certification Authority in the middle pane.
- On the Action menu, click Properties.
- On the Dependencies tab, click Insert, select the network HSM service from the list, and then click OK.
Configuring the CRL Distribution Point
The CA configuration tasks should always be performed on the active cluster node.
In the default CA configuration, the server’s short name is used as part of the CRL and AIA path. When a CA is running on a failover cluster, the server’s short name must be replaced with the cluster’s name in the CRL and AIA Uniform Resource Locator (URL).
You must restart the CA service after changing the CRL and AIA.
Follow these steps to make changes to the CRL and AIA URLs:
- Log on to the active cluster node with local administrator permissions.
- Click the Start button, point to Run, type regedit, and then click OK.
- Expand the following containers in the registry. HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration
- Select the name of the CA in the Configuration container.
- In the right pane, open CRLPublicationURLs for editing.
- Replace all occurrences of %2 with the service name that was defined in step 6 in “Configuring the Failover Cluster”. The service name also appears in the Failover Cluster Management under the Services and Applications node.
- Click the Start button, point to Run, type cmd, and then click OK.
- At the command-line prompt, type
net stop certsvc && net start certsvc
and press ENTER to restart the CA service.
- At the command-line prompt, type
certutil -CRL
and press ENTER to update the CRL with the new settings applied previously.
Creating the CRL Objects in Active Directory
The CRL container has to be created in Active Directory manually, and the CRL must be published manually.
To create the CRL container, use the certutil command with the –f option and execute the command as Enterprise Admin.
- Log on to the active cluster node with enterprise permissions.
- Click the Start button, point to Run, type cmd, and then click OK.
- At the command-line prompt, type
cd %WINDIR%\System32\CertSrv\CertEnroll
and press ENTER.
- To publish the CRL to Active Directory, type
certutil -f -dspublish {CRLfile}
and press ENTER.
For example: certutil -f -dspublish "CA Cluster.crl"
Configuring the CA in Active Directory
You can perform the following tasks using any computer in your Active Directory forest where the Active Directory Sites and Services MMC Snap-in and ADSI Edit are installed. To install both tools on Windows Server 2008, add the Active Directory Domain Services feature from the Remote Server Administration Tools to your server with Server Manager. The AIA object in Active Directory stores the CA’s certificate.
To enable all cluster nodes to update the CA certificate when required, perform the following steps:
- Log on to the computer with enterprise permissions.
- Click the Start button, point to Run, type dssite.msc, and then click OK.
- Select the top node in the left pane.
- On the View menu, select Show services node.
- In the left pane, expand the Services and Public Key Services, and then select AIA.
- In the middle pane, select the CA name as it shows in the Certification Authority MMC Snap-in.
- On the Action menu, select Properties.
- Click the Security tab.
- Click Add.
- Click Object Types, select Computers, and then click OK.
- Type the computer name(s) of the other cluster node(s) as the object name and click OK.
- Make sure that the computer accounts of all cluster nodes have Full Control permissions.
- Click OK.
- All cluster nodes also have to be permitted on the Enrollment Services container.
- In the left pane, select Enrollment Services.
- In the middle pane, select the CA name.
- On the Action menu, select Properties.
- Click the Security tab.
- Click Add.
- Click Object Types, select Computers, and click OK.
- Type the computer name(s) of the other cluster node(s) as the object name and click OK.
- Make sure that the computer accounts of all cluster nodes have Full Control permissions.
- Click OK.
Finally, you must permit all cluster nodes on the KRA container.
- In the left pane, select KRA.
- In the middle pane, select the CA name.
- On the Action menu, select Properties.
- Click the Security tab.
- Click Add.
- Click Object Types, select Computers, and then click OK.
- Type the computer name of another cluster node as object name and click OK. Repeat for all other nodes in the cluster.
- Make sure that the computer accounts of all cluster nodes have Full Control permissions.
- Click OK.
- Close the Sites and Services MMC Snap-in.
Adjusting the DNS Name for the CA in Active Directory
When the CA service was installed on the first cluster node, it created the Enrollment Services object and put its own fully qualified domain name (FQDN) into that object. Since the CA can operate on any of the cluster nodes, the dNSHostName of the Enrollment Services object needs to be changed to the service name of the CA.
Follow these steps to change the dnsHostName.
- Log on to the computer with enterprise permissions.
- Click the Start button, point to Run, type adsiedit.msc, and then click OK.
- Select ADSI Edit in the left pane, select the Action menu, and then chose Connect to.
- In the list of well-known Naming Contexts, select Configuration and click OK.
- Expand the Configuration, Services, and Public Key Services container in the left pane and select Enrollment Services.
- In the middle pane, select the name of the cluster CA. On the Action menu, click Properties.
- Select the attribute dNSHostName and click Edit.
- Enter the service name of the CA as shown in the Failover Cluster Manager under Failover Cluster Management and click OK twice.
- Close ADSIedit.
Certification Authority Renewals
When the clustered Certification Authority renews its own certificate, all nodes in the cluster must be updated with the renew certificate information. This will occur as part of the regular maintenance process of the Certification Authorities as well as when any infrastructure or security requirements dictate the renewal.
Follow these steps to renew the CA certificate and update the cluster nodes with the new CA key.
Renew the CA Certificate and export the Certificate and Private key.
- Locate the node that is currently running Active Directory Certificate Services and log on with local administrator permissions.
- Click the Start button, point to Run, type Cluadmin.msc, and then click OK
- Use the Cluster Administration tool to take the ADCS service resource offline.
- Click the Start button, point to Run, type certsrv.msc, and then click OK.
- Select the CA node in the left pane.
- On the Action menu, click All Tasks, and then click Renew CA Certificate. Press OK to acknowledge ADCS will be stopped during the renewal.
- Complete the renewal wizard and if necessary, submit your renewal to a parent CA.
- Once the CA renewal is complete, ensure the ADCS service is running and the ADCS cluster resource is online.
- In the Certification Authority tool select the CA node in the left pane.
- On the Action menu click Properties.
- On the General tab select the newest certificate which is at the bottom of the list with the largest number. Click View Certificate.
- In the Certificate window, select the Details tab, select the Thumbprint field and copy the value.
- Click the Start button, point to Run, type regedit, and then click OK.
- Expand the following containers in the registry. HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration
- Select the name of the CA in the Configuration container.
- In the right pane, open CACertHash for editing.
- Add the certificate thumbprint to the bottom of the existing values in the key.
- Use the Cluster Administration tool to take the ADCS service resource offline and then back online to commit changes to the shared storage.
- Click the Start button, point to Run, type certsrv.msc, and then click OK.
- Select the CA node in the left pane.
- On the Action menu, click All Tasks, click Backup CA.
- On the Welcome page of the CA backup wizard, click Next.
- Select Private key and CA certificate and provide a directory name where you want to temporarily store the CA certificate and optionally the key. Click Next.
- Provide a password to protect the CA key and click Next.
- Click Finish.
If you are using a network HSM, a warning message will display telling you that the private key cannot be exported. This is expected behavior because the private key will never leave the HSM. Click OK to continue.
|
Importing the CA certificate into the local machine certificate store on other cluster nodes.
If you are using a network HSM, to confirm that a network HSM is available to the node
- Expand the Diagnostics node in the left pane of the Server Manager Snap-in, and then click Services.
- Make sure that the service that connects to the network HSM is started. Refer to the HSM vendor for service information.
- Copy the previously exported CA certificate to the cluster node.
- Click the Start button, point to Run, type mmc, and then click OK.
- On the File menu, click Add/remove MMC Snap-in.
- Select Certificates from the list of available snap-ins and click Add.
- Select Computer account, click Finish twice, and then, click OK.
- In the Certificate Manager MMC Snap-in, expand the Certificates (Local Computer) node and select the Personal store.
- On the Action menu, click All Tasks, and then click Import.
- In the Certificate Import Wizard, click Next.
- Enter the file name of the CA certificate that was previously created on the first node and click Next. If you use the Browse button to find the certificate, change the file type to Personal Information Exchange (*.pfx,*.p12).
- Type the password that you have previously used to protect the private key. The password is required even if there is no private key in the PFX file. Do not mark this key as exportable. Click Next.
- Place the certificate in the Personal certificate store and click Next.
- To import the certificate, click Finish.
- To confirm the successful import, click OK.
If you are using a network HSM, you must repair the association between the certificate and the private key that is stored in the HSM.
- In the Certificate Manager MMC Snap-in, expand the Personal store and select the Certificates container.
- Select the imported certificate. On the Action menu, click Open.
- Go to the Details tab.
- Select the field Serial Number, copy the serial number to the Clipboard, and then click OK.
- At a command-line prompt, type
certutil –repairstore –csp “{CSP Providername}” My "{Serialnumber}"
and then press ENTER.
For example: certutil –repairstore My "629bdaba68590bbd488c78e0ac57bc2b"
** **
Detach the shared storage from the cluster node.
- Go to the Server Manager MMC Snap-in, expand the Storage node, and then select Disk Management.
- Change the state of the disk keeping the CA database to offline.
Repeat as needed for all nodes in the cluster that could potentially run the ADCS resource.
Troubleshooting
Event ID 17
Following the migration of a Windows Server 2003 Certification Authority to a Windows Server 2008 Failover cluster, Active Directory Certificate Services fails to start and the event log shows Event ID 17 – CertificationAuthority.
This error can be caused when the ADCS database is marked for restore operations. Verify that the RestoreInProgress does not exist in the Registry Key HKLM\SYSTEM\CurrentControlSet\Services\CertSvc\Configuration. If it does, note the cluster node owning the ADCS resource in the Cluster Administrator tool, remove the RestoreInProgress key on the node owning the service, and restart the cluster ADCS resource.
CA Web Enrollment does not work properly
Certification Authority Web Enrollment does not work properly on a Windows Server 2008 Failover cluster if the ADCS service is also installed on the same cluster node.
If the Certification Authority is on the same node that the Web Enrollment feature is installed on, the node’s DNS name is used in the Web Enrollment certdat.inc file. If the CA is not on the same node, the problem does not occur.
The issue is resolved by modifying the %systemroot%\system32\certsrv\certdat.inc file to change the value of sServerConfig to “<Service name>\CA name>”
Example - Certdat.inc file entry.
The two cluster nodes: NODE****117 and NODE****118
The certdat.inc files has the entries of
sServerConfig="NODE****117.contoso.com\CONTOSOENTCA1" and sServerConfig="NODE****118.contoso.com\CONTOSOENTCA1"
Remove all but one sServerConfig line and change the remaining line to:
sServerConfig=”CLUSTER1.contoso.com\CONTOSOENTCA1” where CLUSTER1.contoso.com is the FQDN of the virtual ADCS cluster name.