Active Directory Forest Recovery
Here is an article with an Active Directory recovery scenario. You can play as what this scenario on a model for you become familiar with the procedure for Recovery of AD (pending to have a true crash). The original article language was French and I translated into English.
Existing infrastructure
Active Directory
This procedure is very dependent on the Active Directory infrastructure in place. In the context of the demo, AD Windows 2008 R2 architecture in place is composed of the following elements:
- 1 Domain, 1 forest: intra.domain.local
- 2 Domain (DC1, DC2) controllers
- 2 Servers DNS (DC1, DC2)
- 2 Global Catalog (DC1, DC2)
- Distribution of FSMO roles
- Schema master (DC1)
- Domain naming master (DC1)
- RID master (DC1)
- PDC emulator (DC1)
- Infrastructure master (DC1)
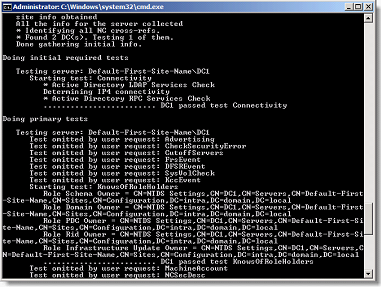
Result of a dcdiag/test: knowsofroleholders
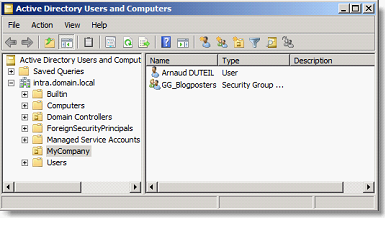
Some objects are created in the AD for the test:
Overview
Prerequisites
To achieve this recovery procedure, it is necessary to have a backup "System State" of a DC in the domain. In the case of a multi-domaine infrastructure, you need to have a CD by area. The best Backup will be the one that has the greatest number of FSMO roles. In our case, it will be better to use a Backup of the DC1. This evaluators us stages of recovery of FSMO roles missing (16)
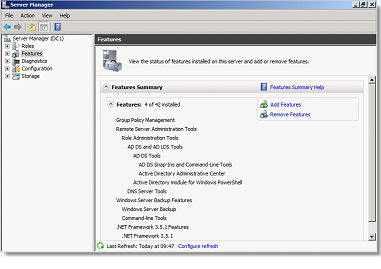
Info: The Windows Server 2008 environments, integrated backup tools are called "Windows Server Backup" and settled via the console Features
To restore AD DS, it is necessary to have the password to restore Active Directory. This password was positioned at the initial installation, it may has not been retained. If this is the case, follow the detailed here KB322672 today.
Decision
This procedure must - be carried out in the following cases:
- All DC it suffered a software or physical corruption that makes the impossible business
- The Active Directory environment has been sabotaged
- A risky action triggered a corruption of data through the forest
- None of the domain controllers cannot replicate with partners
- No change cannot be performed on AD DS from the DC
- New DC can be added to the existing fields
Retrieve an an Active Directory forest is to recreate "from scratch" AD DS on all DC or restore the forest from a Backup. As a result, the AD recovery operation causes data loss where changes has been made since the last Backup execution
Macro Steps
The recovery steps are following:
- Backup AD DS
- Extinction of all DC
- Restore the System State of DC1
- Recovery of the FSMO roles (if required)
- Cleaning of AD (Metadata CleanUp) replication partners
- Installation of new domain controllers
Each is detailed in the following section
Backup
Before the recovery procedure, it is important to know the backup in place strategy to identify the good backups.
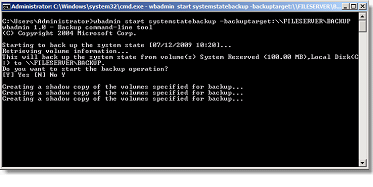
The Backup of the domain controller operation is done via Windows Backup (Wbadmin.exe). Ideally, the Backup files are then outsourced.
To back up the System State of a domain controller, this is the command to use:
WBADMIN start systemstatebackup - backuptarget: \FILESERVER\BACKUP
Once the Backup is completed, the command ends with the message:
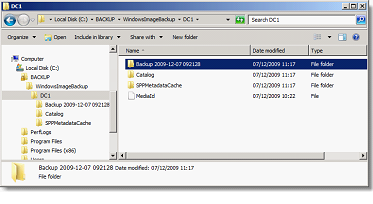
By default, the backup files generated are identifiable as follows in the target directory:
Recovery AD DS
At this moment, we are putting an AD crash. From this moment, the decision is made to restore the directory by following the procedure detailed below.
Extinction of all domain controllers
To avoid replication of corrupted or obsolete data with the directory that we will go back, it is essential to make inactive all domain controllers in the forest, in particular the FSMO role holders.
The first DC restoration
In our case, the DC to restore is unquestionably the DC1.intra.domain.local server. There roles DNS, and all forest and domain FSMO roles.
In a multidomain, a domain controller in the domain context root of the forest should be chosen because it contains both the structure of the forest (trusts) and the root DNS integrated with the AD and the AD resource records.
On a new machine DC-RESTO installed in WorkGroup, we will restore the Backup of System State of the DC1 server. This new server in Directory restore mode
Bcdedit/set safeboot dsrepair

On the reboot, the server goes directly into mode restoration directory (instead of having to press F8 through the console)
The Backup file may contain different Backup files. It is necessary for the restoration of the most suitable file (careful, this is not necessarily the most recent!).
To find the "Version Identifier" of the backup file that we want to use, it runs:
WBADMIN get versions - backuptarget: \FILESERVER\Backup
The name ID for my backup file preferred is "12/07/2009-09: 21″"
The restoration of the SYSVOL directory must - be "Authoritarian" type for this DC will be the first directory. Here is the command is run on the new server:
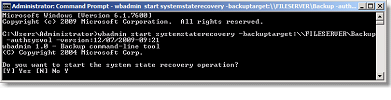
wbadmin start systemstaterecovery –backuptarget:\FILESERVER\backup –authsysvol –versions:12/07/2009-09:21
Respond YES to 5 warnings:
- Do you want to start the system state recovery operation?
- Do you want to continue?
- …
The command ends with the message:
On the restart, connect local administrator of the machine. Attention, the password of the account is the recovery password (DSRM)
When the machine restarts, the message appears:
Disable the boot in Directory restore mode:
Bcdedit /deletevalue safeboot
Configure the server to be used as a preferred DNS. Change the IP configuration. The restored server is then the first DNS of the "new forest".
Restart the server to connect in the domain administrator (the password is always the same as before)
Validation / Test
Once restored, the first CD "supports" the new forest. It is therefore essential to carry out some tests to validate the relevance of the restoration.
- The name of the machine is consistent (DC1.intra.domain.local)
- The IP configuration is valid
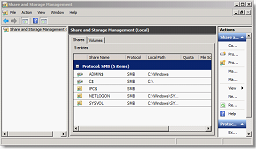
- The SYSVOL and NETLOGON directories are present and shared
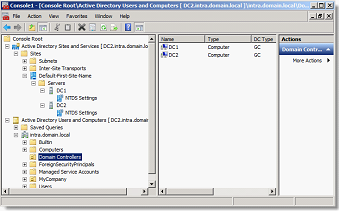
- The ADUC Console contains the existing objects in the directory before the Backup
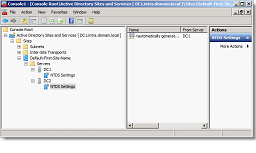
- Replication partners are always visible in the console "Sites and Services".
- Service records are present in DNS Zone
- ADSI Edit to view the entire Partitions AD DS
Initial configuration
Some actions are required to initialize the AD, escape corrupt DC elders and prepare for the integration of new servers.
Global catalog (optional)
In the case of the restoration of a Multi-domaine forest, several GC are potentially recovered. It is therefore necessary to ensure first that no GC replica non-existent objects. Uncheck the box "Global Catalog" of the DC1 server NTDS settings in the console "Sites and Services". The GC roles will be reapplied when the complete recovery operation will be completed.
RID pool
Between the time of the Backup and recovery, it may be that a "Security Principals" have been created in the AD. Therefore, these objects recovered a SID in their creation. They no longer exist because the prior to their creation backup has been restored. To avoid that new created users retrieve the same SID, it is essential to increase the beginning of the range of the RID Pool.
Start ldp.exe
Click Connection and then Connect
Find out the name of the local server FQDN
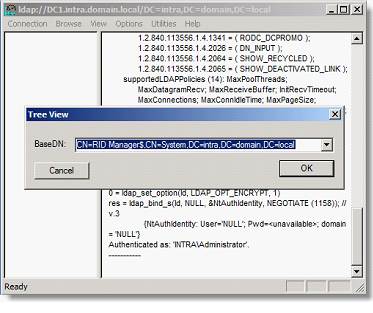
Click Connection and then Bind and OK
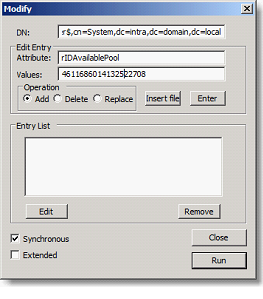
Click on View / Tree and enter the DN of the RID Manager: CN=RID Manager$,CN=System,DC=intra,DC=domain,dc=local
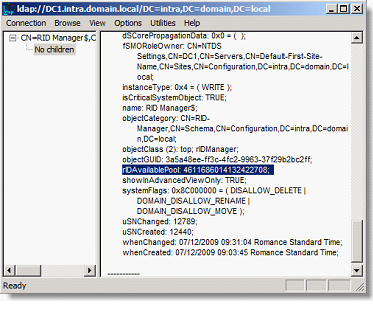
Identify the value of the attribute rIDAvailablePool and copy
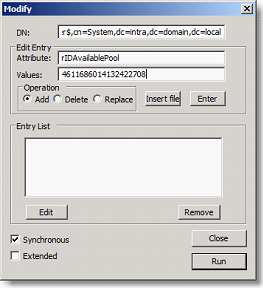
Click on Browse and then Modify
In the DN field, type
cn=RID Manager$,cn=System,dc=intra,dc=domain,dc=local
In the Attribute field, type rIDAvailablePool.
Paste the value identified above and add the value 100000. If we take all5 last figures, 422 708 becomes 522 708 and click Replace, Enter and Run
(Optional) FSMO roles
In the case of the restoration of a CD is not all FSMO roles, it is necessary to restore to be all present in the new forest.
In a command prompt, run NTDSUtil.exe
Type roles
At the prompt "fsmo maintenance", type connections
At the prompt "server connections", type connect to server dc1.intra.domain.local
Type quit
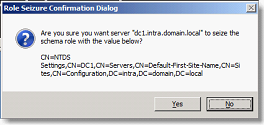
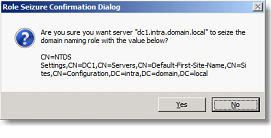
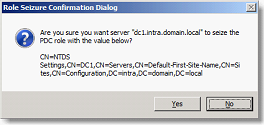
Then type the following commands to retrieve each of the forest and the domain FSMO roles:
- seize Schema master
- seize Naming master
- seize Infrastructure master
- seize PDC
- seize RID master
We now have a new forest consisting of a DC, DNS which has all FSMO roles.
Cleaning of the AD (Metadata CleanUp)
In an AD DS 2008 or 2008 R2, the cleaning of the metabase Active Directory is done automatically when it deletes an object of type Domain Controller.
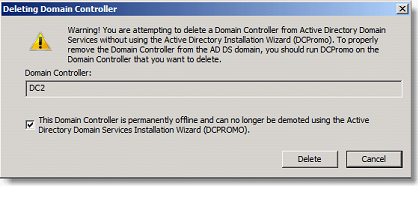
In the ADUC console, open the or Domain Controllers
Delete all except DC1 DC objects
Check the box and click on Delete
The account password Machine and krbtgt
In the case of DC that would possibly be still online despite the previous steps of the procedure, we need to reset the machine and the account krbtgt account. We make sure to not respond with "old" DC
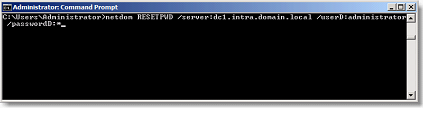
In a command prompt, type:
netdom resetpwd /server :DC1.intra.domain.local /userD:administrator /password :*
The command must be run 2x
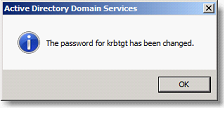
To reset the password on the krbtgt account, connect to the ADUC console and do a right click / change password on the account in question
The action must be carried out 2x
The Active Directory environment is now ready to receive new DC.
The DC1 server can be re-promoted as a Global catalog
Relocation of the former DC in the new forest
In our case, DC2 will be reinstalled and join to the forest via DCPROMO:
Remaining shares
Once the AD stable environment, your organization and the reasons for the break, some actions and developments can be carried out if necessary:
- Addition of domain controllers
- DNS reconfiguration
- Distribution of FSMO roles (today on DC01)
- Recreation of objects that could be deleted from the Backup and restoration
- Add to Global Catalogs
- Change the words of passes of Auditors to senior privileges (Enterprise Admins, Schema Admins), especially in the case of sabotage
- On client machines, reconnect them to the domain, or with an "I" or by recreating a Secure Channel
- Rebuild trust relationships to the external forest