Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
One basic requirement for an identity management system is the ability to import and process identity data from an external system.
This guide walks you through the main building blocks that are involved in the process of populating Microsoft ForefrontT Identity Manager (FIM) 2010 with user data from Active Directoryr Domain Services (AD DS), outlines how you can verify whether your scenario works as expected, provides suggestions for managing Active Directory users by using FIM, and lists additional sources for information.
Before You Begin
In this section, you will find information about the scope of this document.
In general, "How Do I" guides are targeted at readers who already have basic experience with the process of synchronizing objects with FIM as covered in the related Getting Started Guides.
Audience
This guide is intended for information technology (IT) professionals who already have a basic understanding of how the FIM synchronization process works and are interested in getting hands-on experience and more conceptual information about specific scenarios.
Prerequisite knowledge
This document assumes that you have access to a running instance of FIM 2010 and that you have experience in configuring simple synchronization scenarios as outlined in the following documents:
The content in this document is scoped to function as an extension to these introductory documents.
Scope
The scenario outlined in this document has been simplified to address the requirements of a basic lab environment.
The focus is to give you an understanding of the concepts and technologies discussed.
This document helps you develop a solution that involves managing groups in AD DS by using FIM.
Time requirements
The procedures in this document require 60 to 90 minutes to complete.
These time estimates assume that the testing environment is already configured and does not include the time required to set up the test environment.
Getting support
If you have questions regarding the content of this document or if you have general feedback you would like to discuss, feel free to post a message to the Forefront Identity Manager 2010 forum.
Scenario Description
Fabrikam, a fictitious company, is planning to use FIM to manage the user in the corporation's AD DS by using FIM.
As part of this process, Fabrikam needs to synchronize users into FIM.
To start with the initial testing, Fabrikam has installed a basic lab environment that consists of FIM and AD DS.
In this lab environment, Fabrikam is testing a scenario that consists of a user that was manually created in the AD DS.
The objective of this scenario is to synchronize the sample user into FIM.
Scenario Design
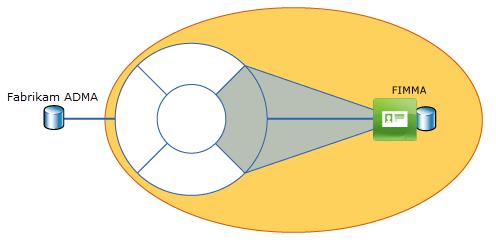
To use this guide, you need three architectural components:
- Active Directory domain controller
- FIM Synchronization Server
- FIM Portal Server
The following illustration outlines the required environment:
You can run all components on one computer.
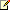 Note Note |
|
|---|---|
| For more information about how to set up FIM, see the FIM Installation Guide |
Scenario Components List
The following table lists the components that are part of this scenario in this guide.
Scenario Steps
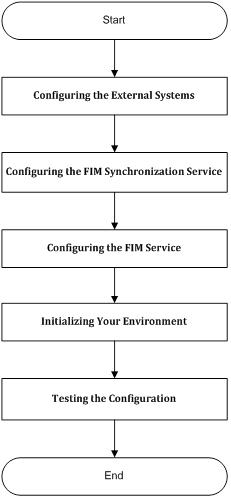
The scenario outlined in this guide consists of the following building blocks:
Configuring the External Systems
In this section, you will find instructions for the resources that you need to create that are outside of your FIM environment.
Creating the organizational unit
You need the organizational unit as a container for the sample user.
| Step 1 | |||
 |
Create an organizational unit called FIMObjects in your AD DS. | ||
| Note: | For more information about creating organizational units, see Create a new organizational unit. | ||
Creating the Active Directory user accounts
For the scenario in this guide, you need two Active Directory user accounts:
- Adma - User account used by the Active Directory management agent.
- Fimma - User account used by the FIM Service management agent.
In both cases, it is sufficient to create regular user accounts.
More information about the specific requirements of both accounts is found later in this document.
| Step 2 | |||
 |
Create two Active Directory user accounts based on the previous description. | ||
| Note: | For more information about creating organizational units, see Create a new user account. | ||
Configuring the FIM Synchronization Service
For the configuration steps in this section, you need to start the FIM Synchronization Service Manager.
Creating the management agents
For the scenario in this guide, you need to create two management agents:
- Fabrikam ADMA - management agent for AD DS.
- Fabrikam FIMMA - management agent for FIM Service Management Agent.
Configuring the Fabrikam ADMA
When you configure a management agent for AD DS, you need to specify an account that is used by the management agent in the data exchange with AD DS.
You should use a regular user account.
However, to import data from AD DS, the account must have the right to poll changes from the DirSync control.
If you want your management agent to export data to AD DS, you need to grant the account sufficient rights on the target organizational units.
For more information about this topic, see Configuring the ADMA Account.
To synchronize user data from AD DS, there are no technical requirements for specific attributes to be populated.
By design, the FIM management agent already has the attribute flow mappings that are required by the FIM schema for the object type user configured.
However, there are logical requirements from a scenario perspective.
This includes the first name, last name and display name attribute of a user.
You should populate these values to ensure that your objects are recognizable in the FIM user interface.
In addition, it is a good practice to populate the userSid and the domain attribute.
The following table lists the most important scenario specific settings you need to configure:
| Management Agent Designer Page | Configuration |
| Create Management Agent |
|
| Connect to Active Directory Forest |
|
| Select Object Types |
|
| Select Attributes |
|
| Step 3 | |||
 |
Create the management agent based on the previous description. | ||
| Note: | For more information, see the following topics in Help:
|
||
| Important: | Ensure that you have an import attribute flow rule configured for the ExpectedRulesList attribute. | ||
Configuring the Fabrikam FIMMA
When you configure a FIM Service management agent, you need to specify an account that is used by the management agent in the data exchange with the FIM Service.
You should use a regular user account.
The account must be the same account as the one you specified during the installation of FIM.
Using Windows PowerShell to Do a FIM MA Account Configuration Quick Test contains a script that you can use to determine the name of the FIMMA account name that you specified during setup and to test whether this account is still valid.
The following table lists the most important scenario specific settings you need to configure.:
| Management Agent Designer Page | Configuration | ||||||
| Create Management Agent |
|
||||||
| Connect to Database |
|
||||||
| Select Object Types |
|
||||||
| Configure Object Type Mappings |
|
||||||
| Configure Attribute Flow |
|
| Step 4 | |||
 |
Create the management agent based on the previous description. | ||
| Note: | For more information, see the following topics in Help:
|
||
Creating the run profiles
The following table lists the run profiles you need to create for the scenario in this guide:
| Management agent | Run profile |
| Fabrikam ADMA |
|
| Fabrikam FIMMA |
|
| Step 5 | |||
 |
Create for each management agent run profiles according to the previous table.
To create run profiles for a management agent, select the management agent, and on the Actions menu, click Configure Run Profiles. |
||
| Note: | For more information, see the Create a Management Agent Run Profile in FIM Help | ||
| Important: | Verify that provisioning is enabled in your environment.
You can do this by running the script: Using Windows PowerShell to Enable Provisioning. |
||
Configuring the FIM Service
For the scenario in this guide, you only need to configure an inbound synchronization rule.
The following section provides information about the configuration of the synchronization rule.
Creating the synchronization rule
When you create the inbound synchronization rule for your Active Directory users, you need to add a flow mapping for the domain attribute.
Populating the domain attribute is a challenge because domain is not an attribute of a user.
When this attribute is required in AD DS, the directory service has to look up the value from the configuration container.
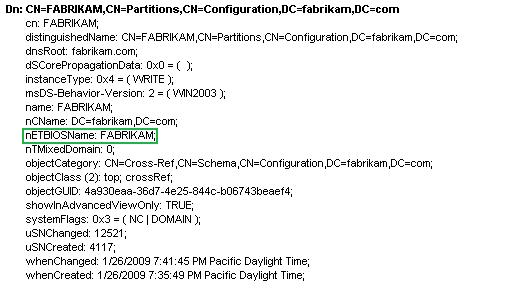
The following illustration shows an example of a domain partition in the configuration container.
One method used to populate the domain attribute is to implement a lookup table that determines the attribute value based on the current SID of an object.
The SID attribute is a good attribute for this purpose because the value of this attribute only changes when the domain membership of an object changes.
The SID attribute of an object in AD DS consists of the domain SID plus an extension called relative identifier (RID), the unique identifier of an object within the domain database.
If you know what the value of the domain SID is, you can use this value in comparison with the SID value of an object to determine the value of the domain attribute as a custom expression.
FIM provides a built-in function you can use to translate a binary SID into a string representation.
The name of this function is ConvertSidToString.
This function returns the string representation of a SID as domain SID + RID.
For an equality comparison (Eq) of a user's SID and the domain SID, you need to remove the RID part from the user's SID.
Because you know the value of the domain SID, you also know the domain SID length .
You can use the length of the domain SID to calculate the part of a user's SID that you need for an equality comparison.
The following example outlines how you can use the domain SID and the user's SID to calculate the domain value with a custom expression in FIM.
A lookup of Fabrikam's SID returns a value of "S-1-5-21-4220550486-1538840966-3184992408".
The SID string has a length of 41.
The first step in your custom expression is to translate the object's SID into a string representation by using the ConvertSidToString method:
ConvertSidToString(objectSid)
From this string, you only need the first 41 characters from the left:
Left(ConvertSidToString(objectSid), 41)
The question is whether this string is equal to the domain SID:
Eq(Left(ConvertSidToString(objectSid), 41)
If both values match, you can flow "FABRIKAM" as the domain name into the metaverse. If the values do not match, you should flow something like "Unknown":
IIF(Eq(Left(ConvertSidToString(objectSid),41),"S-1-5-21-4220550486-1538840966-3184992408"),"FABRIKAM","Unknown")
The FIM ScriptBox provides a script that automatically calculates the required custom expression string for the domain attribute value calculation.
You can find this script here: Using PowerShell To Generate The Custom Expression For The Domain Attribute Flow
The script requests the required information from a target domain controller, translates the domain information into a CustomExpression and stores the result in the clipboard.
The following table shows the configuration of the required Fabrikam Provisioning Synchronization Rule:
| Synchronization Rule Configuration | ||||||||||||||
|
||||||||||||||
| Scope | ||||||||||||||
|
||||||||||||||
| Relationship | ||||||||||||||
|
||||||||||||||
| Relationship Criteria | ||||||||||||||
|
||||||||||||||
| Inbound Attribute Flows | ||||||||||||||
|
| Step 6 | |||
 |
Create a synchronization rule according to the data in the previous table. | ||
| Important: | Verify, that you have selected Initial Flow Only for the attribute flow that has the DN as the destination. | ||
Initializing Your Environment
The objective of the initialization phase is to bring your:
- Synchronization rule into the metaverse.
- Active Directory structure into the Active Directory connector space.
The following table lists the run profiles that are part of the initialization phase.
| Run | Management agen | Run profile |
| 1 | Fabrikam FIMMA | Full Import |
| 2 | Full Synchronization | |
| 3 | Export | |
| 4 | Delta Import | |
| 5 | Fabrikam ADMA | Full Import |
| 6 | Full Synchronization |
| Step 7 | |||
 |
Run the run profiles according to the previous table. | ||
| Note: | You should verify that your outbound synchronization rule has been successfully projected into the metaverse. | ||
Testing the Configuration
The objective of this section is to test your actual configuration. To test the configuration, you:
- Create the sample user in AD DS
- Synchronize the Active Directory user into FIM
Creating a sample user in AD DS
The following table lists the properties of the sample user:
| Attribute | Value |
| First Name | Britta |
| Last Name | Simon |
| Display Name | Britta Simon |
| AccountName | BSimon |
| Step 8 | |||
 |
Create a sample user according the data in the previous table. | ||
Synchronizing the Active Directory User into FIM
Before you start a first synchronization cycle for a test object, you should track the expected state of your object after each run profile that you run in a test plan.
Your test plan should include next to the general state of your object (created, updated, or deleted) also the attribute values that you expect.
Use your test plan to verify your test plan expectations.
If a step does not return the expected results, do not proceed with to the next step until you have resolved the discrepancy between your expected result and the actual result.
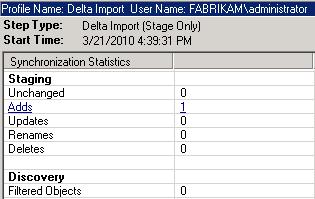
To verify your expectations, you can use the synchronization statistics as a first indicator.
For example, if you expect new objects to be staged in a connector space, but the import statistics returns no "Adds", there is obviously something in your environment that does not work as expected.
While the synchronization statistics can give you a first indication of whether your scenario works as expected, you should use the Search Connector Space and the Metaverse Search feature of the Synchronization Service Manager to verify the expected attribute values.
To synchronize the user to AD DS, follow the steps below:
- Import the user into the ADMA connector space.
- Project the user into the metaverse.
- Provision the user to the FIMMA connector space.
- Export the user to FIM.
- Confirm the creation of the user.
To accomplish these tasks, you run the following run profiles.:
| Management agent | Run profile |
| Fabrikam ADMA |
|
| Fabrikam FIMMA |
|
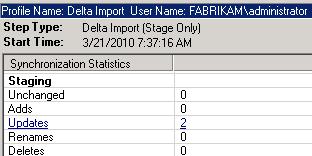
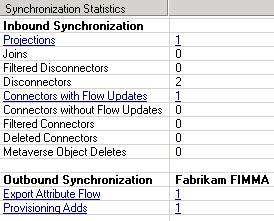
After the delta import from AD DS, the synchronization statistics report one new object.
The objective of the delta synchronization run on your Fabrikam ADMA is to perform several operations:
- Projection - The new user object is projected into the metaverse.
- Provisioning - The newly projected Britta Simon object is provisioned into the connector space of the Fabrikam FIMMA.
- Export Attribute Flows - The export attribute flows populate the newly staged user with the configured attribute values.
| Step 9 | |||
 |
Run the run profiles according to the previous table. | ||
| Caution: | Each run profile run must succeed without an error. | ||
Verify the provisioned user in FIM
To verify that your sample user has been synchronized to FIM, open the related object in the FIM Portal.
| Step 10 | |||
 |
Verify that your sample user exists in the FIM Portal. | ||
Summary
Synchronizing user objects from AD DS into FIM is a relatively simple task from the configuration perspective.
The only bigger challenge is the population of the domain attribute because this attribute is not directly associated with an object in AD DS and needs to be calculated.
In this document, you have been introduced to a method that uses an object's SID attribute value and a lookup table for the calculation of the value.
When using this method, keep in mind that a change to your domain infrastructure such as renaming existing domains or adding new domains requires an update to the calculation logic in your inbound synchronization rule.
Updates to synchronization rules require full synchronization runs that can be time consuming to process in your environment.
An alternative to populating the domain attribute in a synchronization rule is the implementation of workflows to do this task.
However, initializing attribute values by using workflows impacts the performance of your system.
The performance impact of bulk imports from AD DS can be significant.
In general, when implementing inbound synchronization rules in your environment, you need to differentiate between two scenarios:
- Initialization of objects from AD DS
- Regular imports from Active Directory objects
The initialization phase requires special care in your planning.
In this phase, FIM is populated by a bulk import with existing objects from AD DS.
This scenario can have a significant impact on both the servers in your external systems and your servers running FIM.
If you have a large number of objects that you need to synchronize from AD DS into FIM, you should investigate ways to limit this process such as:
- Limiting the number of objects that are processed during one import run from AD DS. This is a recommended best practice.
- Modifying the partitions and container filters to decrease the number of objects that are processed in one run.
- Exporting your Active Directory objects by using, for example, LDIF and import them into FIM by using the FIM Windows PowerShell cmdlets.
Each method has pros and cons.
You need to determine the method that works best for you in your test environment.
Another aspect of handling the initialization phase is the subject of attribute flow precedence.
During the initialization phase, you may need to make AD DS authoritative for attributes for which you want FIM to be authoritative after the initialization phase.
This means that, you need to configure the attribute flow precedence in a way that enables your Active Directory management agent to flow attribute values into FIM that, later in your deployment, will be controlled by FIM.
In general, you should develop a plan that includes a solution for the initialization phase for your environment.
Recommended Reading
- Design Concepts: Using FIM to enable or disable accounts in Active Directory
- Design Concepts: About Reference Attributes
- How can I manage my FIM MA account?
- Detecting Non-authoritative Accounts - Part 1: Envisioning
- Design Concepts: The poor man's version of a connector detection mechanism
- Design Concepts: Configuring the ADMA Account
- A method to remove orphaned ExpectedRuleEntry objects from your environment
- About Attribute Flow Precedence
- About Exports