Azure Front Door in simple words
The Azure Front Door is a global OSI layer 7 service (Application Layer, i.e., HTTP/HTTPS) that provides reliability, resiliency, scalability, availability, and great performance to web-based services. Three tiers are available in Azure Front Door: Standard, Premium, and Classic. For more details we can check Feature comparison between tiers.
Comparing some key features between tiers
Standard, Premium, and Classic tiers are all support:
- Custom domains (Standard, Premium support DNS TXT record-based domain validation and Classic CNAME-based validation )
- Caching (AFD is a modern Content Delivery Network (CDN) that accelerates and balances sites dynamically.)
- Traffic Acceleration (There are more than 150 Front Door points of presence (PoPs) globally located in many countries and regions. Traffic can be served by any Front Door PoP.)
- URL Rewrite (The Azure Front Door supports URL rewrites, so you can change a request's path before routing it to your origin server.)
- Health Probes (Each Azure Front Door environment periodically sends a synthetic HTTP/HTTPS request to each configured origin in order to determine backend health and proximity.)
Origin load balancing (The Azure Front Door allows you to integrate with either Azure-hosted applications or on-premises applications.)
SSL Offloading (Front Door TLS/SSL offload ends the TLS connection, decrypts the traffic at the Azure Front Door, and then re-encrypts the communication before sending it to the backend.)
Some key features are only supported in the Standard and Premium tiers.
- Bot protection (To distinguish between good and harmful bots, Azure WAF for Front Door offers bot rules.)
- Private link support (Azure Front Door Premium can be used by Azure Front Door to connect to your origin.)
- Security reports (A built-in and comprehensive picture of your Azure Front Door's behavior is provided through its analytics reports, together with any related Web Application Firewall data.)
Azure Services that AFD Integrates
Azure Front Door integrates with several Azure services, i.e., DNS, Web Apps, Storage, Azure Monitor, Web Application Firewall, DevOps, etc.
Azure Front Door Demo
For demo purposes, we have deployed an Azure Front Door instance and two Web App services in different regions (West and North Europe).
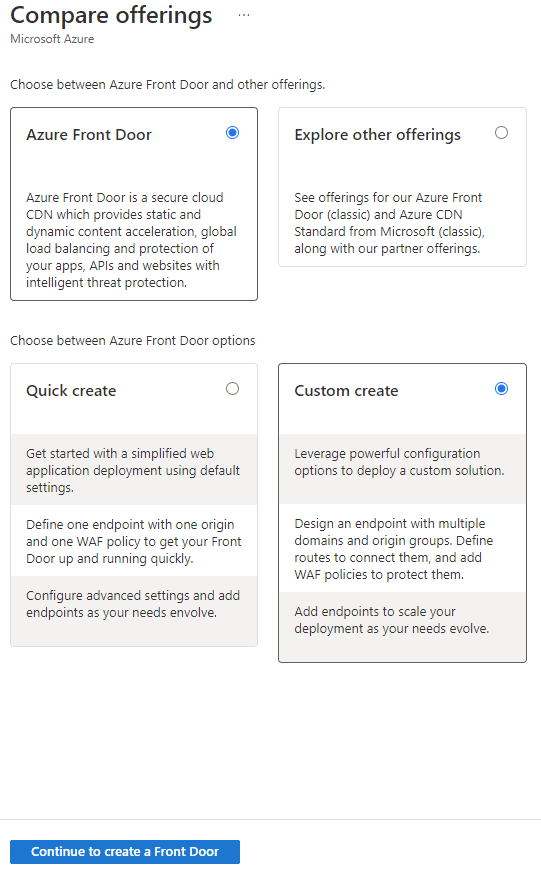
Step 1. On the Compare offerings page, we select Custom create and click Continue to create a front door.
** Step 2.** On the Basics tab, enter the necessary values and click the button **Next: Secrets > *** **This step requires no action. Move on to the next one.
*

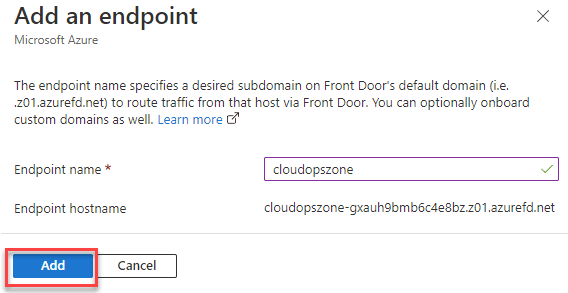
Step 3. In the next step, type the name for the endpoint, i.e., {cloudopszone}
| Info |
|---|
| Endpoint name is a globally unique name |
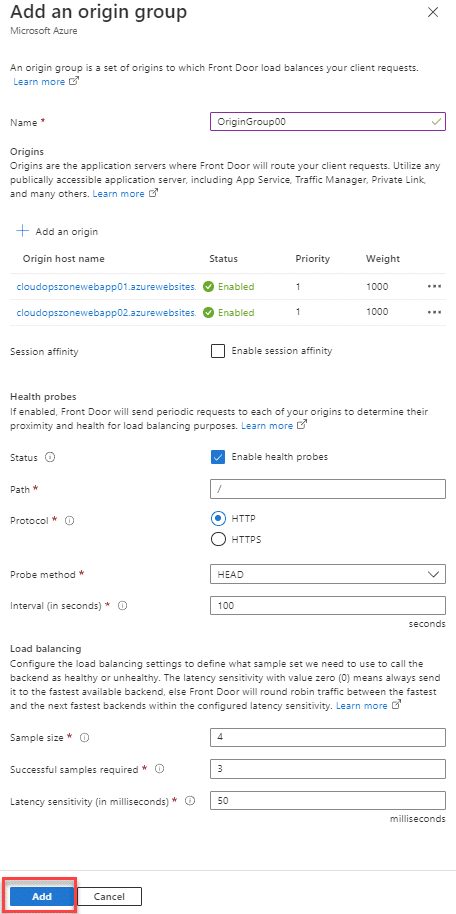
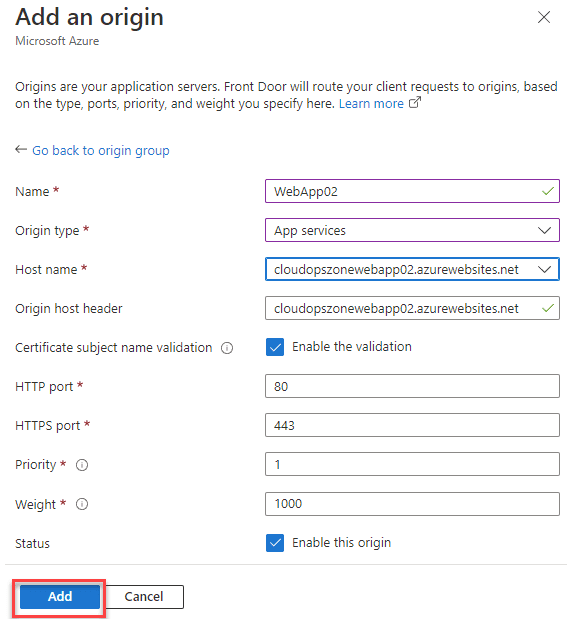
Step 4. To configure the Web app origin, click the button + Add a route.
then add the route to the endpoint configuration, type a name for the origin group and add the two Azure Web Apps.
 |
 |
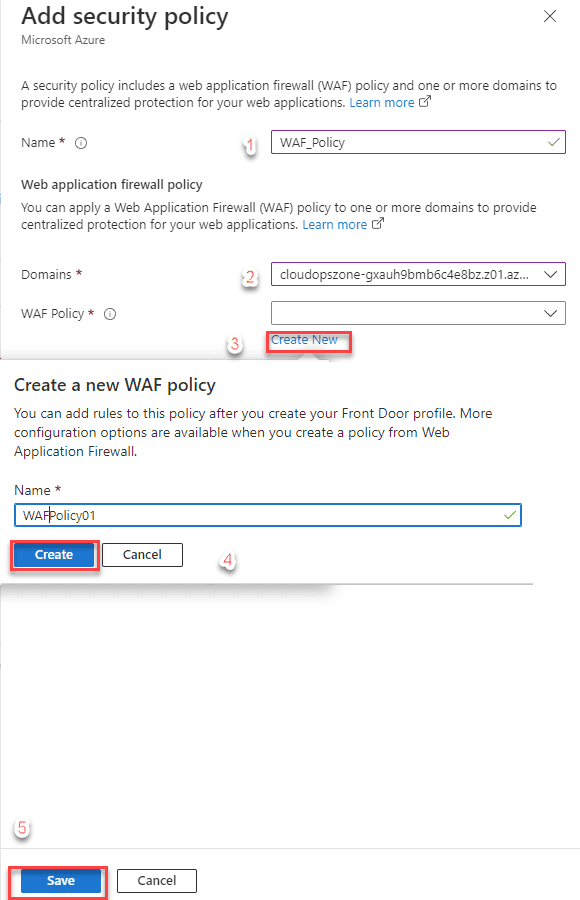
** Step 5.** In the next step we add a WAF policy to the Azure Front Door profile for one or more domains. As the steps to the images below show.
Step 6. To deploy the AFD profile, select Review + Create and then Create.
| Info |
|---|
| Configurations should propagate to all edge locations within a few minutes following deployment. |
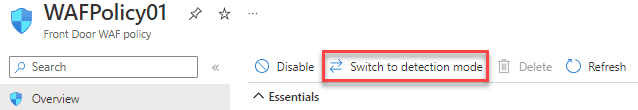
Front Door WAF policy
Listed below are some settings for the Front Door WAF policy that can be updated.
Prevention modes
WAF policy has two modes, prevention and detection. In prevention mode, the WAF performs the specified action if a match is found.
In detection mode, WAF monitors the web requests that are matched to WAF rules. In order to store these logs for a possible diagnosis, Log Diagnostics must be enabled.
Policy settings
Change the Block response body when the status code is 403, i.e., it should display "403 Forbidden".
The error message that will appear on the page will be like the one in the image below.
For more details about WAF policy settings on Azure Front Door, please access this link: Policy settings for Web Application Firewall on Azure Front Door
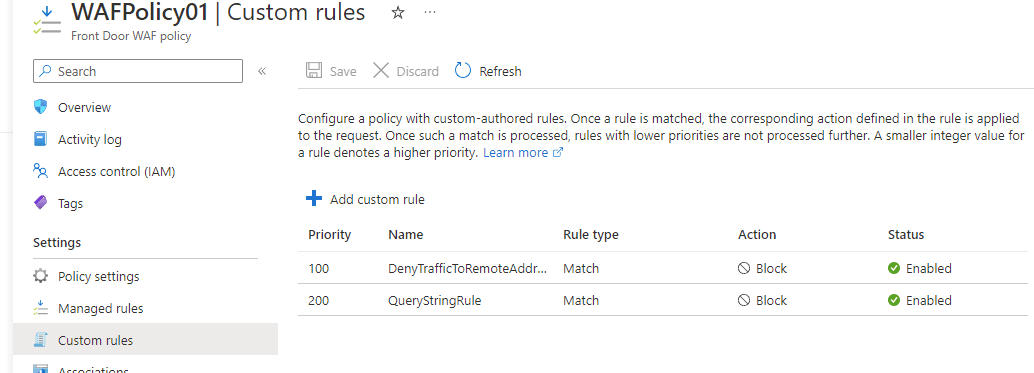
Custom rules
Listed below are two custom rules that will control access to Web Apps based on defined conditions. One custom rule matches with a remote address IP and another with a match type String that matches with a specific Query string.
 |
 |
The image below displays the two custom rules' status and other useful details such as Action, Priority, Rule type, and Name.
Related Links :
- Create an Azure Front Door profile - Azure portal
- Create Front Door profile - Custom Create
- Policy settings for Web Application Firewall on Azure Front Door
- Web Application Firewall DRS rule groups and rules
- Best practices for Web Application Firewall (WAF) on Azure Front Door