Restrict Wireless Access to Domain Joined Machines
Restrict Wireless Access to Domain Joined Machines
Prerequisite
- Active Directory Domain Services
- Active Directory Certificate Service
- Network Policy Server (NPS)
- Supported Access Points
Prepare and configure AD Certificate Services
From server manager dashboard select add roles and features.
In the Add roles and features wizard click Next.
In the server role window select Active Directory Certificate Service.
In the new window select Add Features.
in the Role service window select certification authority and press next to finish installation
Upon successful installation go to server manager dashboard again to start ADCS configuration.
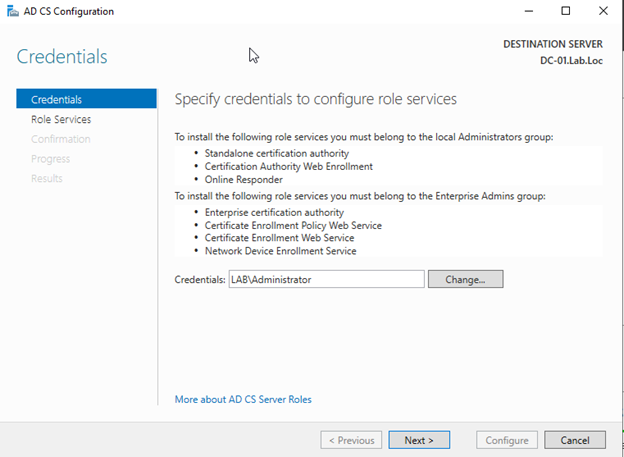
[
In the Credentials window make assure using Enterprise admin account and press next](resources/4118.03.png).
Select Certification authority in the “Select role service to configure” window and press next.
Then select Enterprise CA and press next.

Select Root CA and press next.
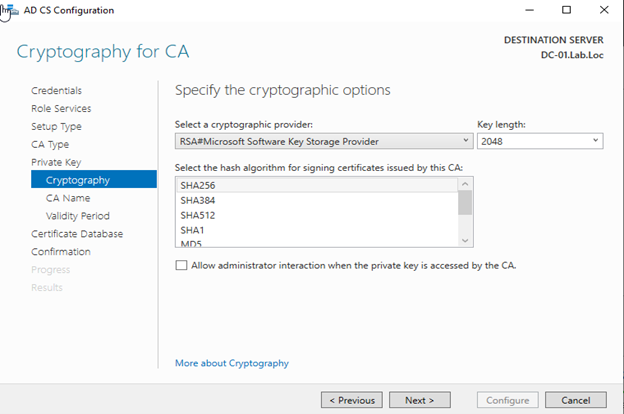
Create new Private Key and press next.
In the Cryptographic Window make sure that key Length 2048 and Hash algorithm SHA 256 then press next.
Click next and configure then finish.
**Configure CA to Allow RDS server to Enroll Certificate.
**
In the CA Server go to Administrative tools à Certification authority
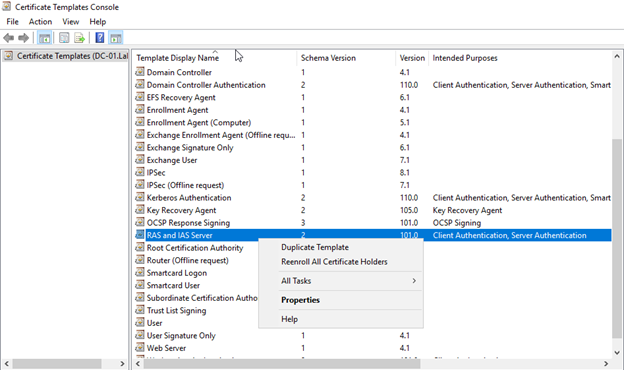
In the Certification authority window right click “Certificate Template” and select Manage

In the “Certificate Template Console” right click “RAS and IAS Server” and select duplicate template
In the new template properties select the proper CA version and windows client version.

In the general Tab select a proper template name like “Wireless Access” then configure validity period and assure selecting “publish CA in active directory”

In the security tab assure that “RAS and IAS server” have enroll and auto enroll permission selected then press apply.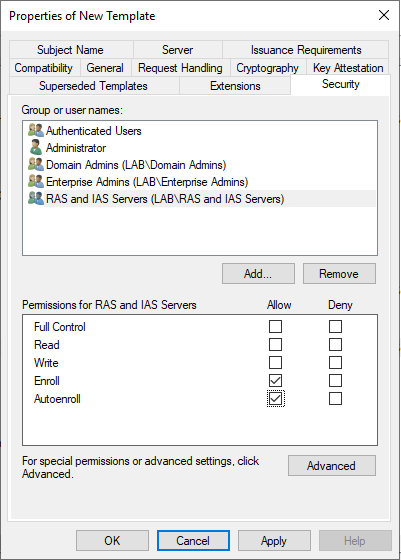
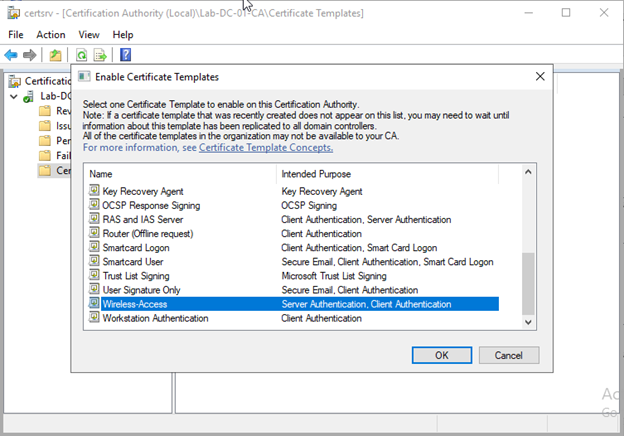
In the certification authority window right click certificate template à new à certificate template to issue.
Select the template you have created in above steps and click ok.
Go to domain controller and group policy management.
Edit default domain policy- go to computer configuration à windows setting à Security settings à public key policies.

Double click “Certificate Service Client -Auto Enrollment” select enabled and select check boxes below.
-Renew expired certificates, update pending certificates, and remove revoked certificates.
-Update Certificates that use certificate template.

**
**
Install and Configure NPS server
In the server dashboard add role and select “network policy and access services” add feature then next
Click next and install.
After successful installation go to Administrative tools à network policy sever
In the NPS server console right click NPS Local and select register in active directory

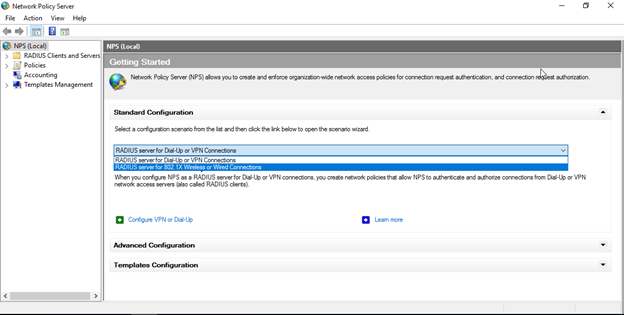
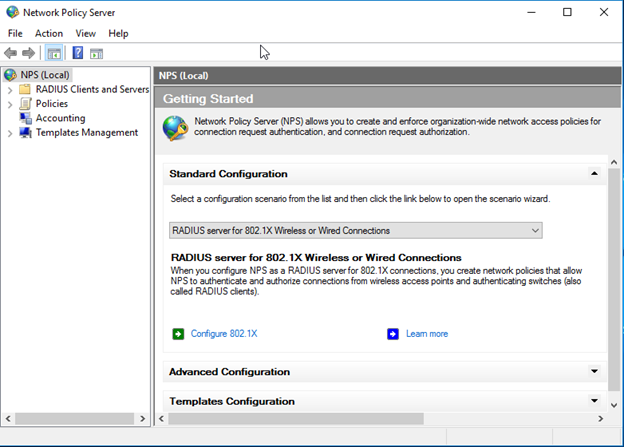
In the getting started window select “RADUIS server for 802 1X Wireless or Wired connections”
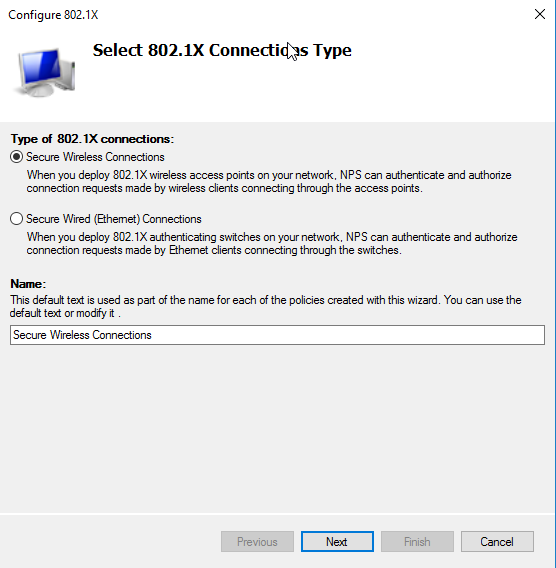
Select secure wireless and type name for the configuration.
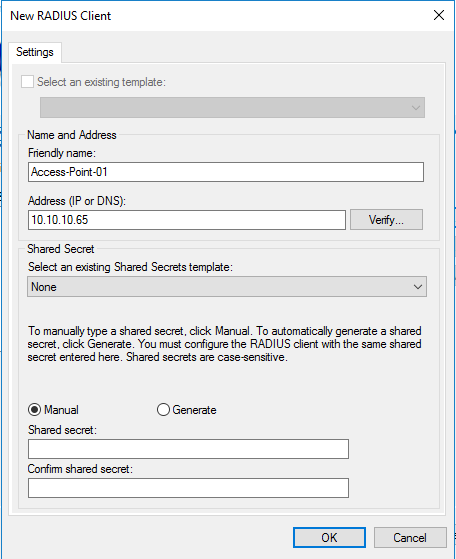
In the RADUIS Client window click add and type friendly name for access point and access point IP then type Shared secret “use Password that will be used in the access point”
Note: RADUIS authentication request will be send to RADUIS server from Access point IP as client not the user machine IP.
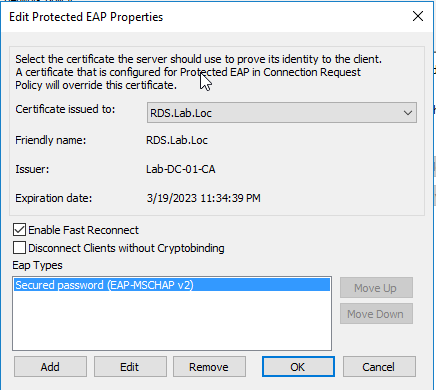
in the authentication method select “Microsoft: Protected EAP (PEAP)” then click configure. To assure that RDS server enrolled the certificate from CA

If you receive the below error. This mean that the server did not enroll the certificate yet. Make sure that you followed above steps to configure CA and groups policy.

You can ignore the above error and continue by clicking ok then next. But you need to make sure that RDS server registered in AD and domain policies are applied.
If all configurations are correct you will see the below message just press ok.
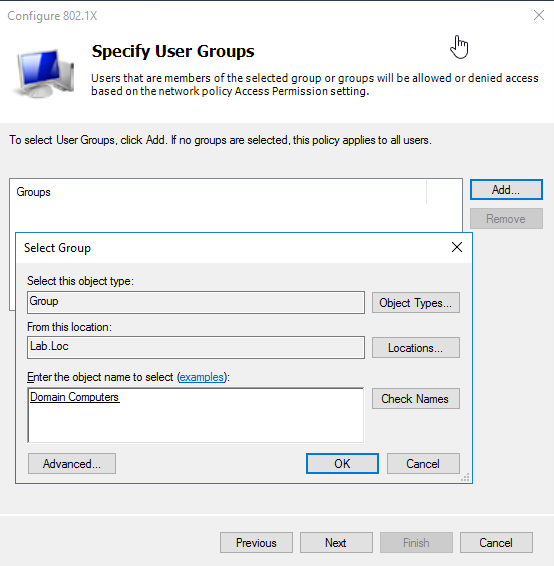
In the specify user group window click add to add domain group as connection condition
Note: if you need to restrict access to domain joined computers only select “Domain Computers” group.
If you need to restrict access to domain users or specific security group, select “Domain Users or name of procreated security group.”
Press next and finish.
Now the NPS server has been installed and configured and you can add more RADUIS client “access points” from NPS server console à RADUIS Client.
Note: you need to assign static IPs for all access point.
Configure access point for RADUIS authentication.
In the access point controller in the Wireless network setting go to select “WPA-Enterprise” as security setting.
In the authentication settings create RADUIS profile or add RADUIS authentication details this will defer based on your access controller version and vendor
In the RADUIS configuration type NPS server IP and default port 1812 and secret key you created in NPS server for RADUIS Client.

The configuration done and you need to test connection from domain joined machine.