Azure Disk Encryption: Configure for Azure Windows VMs
Introduction
To configure data Encryption at rest, Azure offers below two solutions :
- Storage Service Encryption: This is enabled by default and cannot be disabled.
- Azure Disk Encryption : This is not enabled by default, but can be enabled on Windows and Linux Azure VMs.
**In this article, we will explore Azure Windows VM Disk Encryption. We will use PowerShell for Disk Encryption. **
For the rest of the article, we will refer Azure Disk Encryption by its acronym ADE.
Important Points
- Azure Disk Encryption is not available on Basic, A-series VMs, or on virtual machines with a less than 2 GB of memory. It is also not available on Generation 2 Azure VMs and Lsv2 series VM. For more details on unsupported scenarios, please refer this link.
- There's no additional charge associated with encrypting VM disks with Azure Disk Encryption, but there are charges associated with the use of Azure Key Vault. For more details, refer Key Vault Pricing.
For Windows VMs, Encryption works on volume level, not the disk level. It is volume which is encrypted, not the disk.
**For Windows VMs, ADE uses Bitlocker for Windows to encrypt OS and Data volumes. **
- To store Encryption Keys and Secrets , ADE uses Azure Key Vault.
- When you enable ADE on an Windows VM, the ADE Extension is deployed on the Azure VM, and you can check the status in the VM Extension section.
- For Windows VMs, the OS Disk must be encrypted before enabling encryption on Data Disks.
- In order to encrypt a Data Disk, it must first be mounted with the VM. It is recommended that you initialize and format the disk within the OS, before you try to encrypt the data disk.
- For Windows 2012 / Windows 10 OS (>=1511) , the Encryption Method which is used is XTS-AES 256 bit.
Disk Encryption Keys & Secrets
Azure Disk Encryption uses secret for disk encryption. You do not need to specify any secret, ADE will create one during the encryption. The secret will be unique for each VM and will be stored in the Key Vault Secrets repository.
For Windows VM, this secret is generated by Bitlocker.
To add one more layer of security, we can use a Key Encryption Key (KEK) which will encrypt the ADE Secret stored in the Key Vault. When you generate a KEK, ADE will automatically encrypt all encryption secrets before storing in the Key Vault. So using KEK is not mandatory, but a best practice which most organizations follow.
KEK also serves another purpose. Many organizations need to rotate all Keys and Secrets periodically, to comply with their security policy. If you do not use KEK, you need to rotate all disk encryption secrets periodically, which is not an easy task, This also requires new Key Vault every time you rotate secrets. However, if you use KEK, all you need to do is to rotate the KEK which is much easier. We will discuss this in detail in the Key and Secret Rotation section of this article.
Prerequisites
Before we try to encrypt Azure Windows VM Disk, it is important to know prerequisites.
1) Latest PowerShell with AZ Module : Since we will perform entire activity using PowerShell, please verify that latest PowerShell module is available in your base system, along with Azure AZ module installed.
2) Azure Key Vault : You can create a new Key Vault, or configure an existing one to use for Azure Disk Encryption. The Key Vault and Azure VMs must be in the same regions, to enable disk encryption.
In our lab, we have created a new Key Vault in East US2 region, because our VMs are in this region.
**3) Key Vault Access Policy : **
**
**
a) Add your ID to Access Policy : Before performing any operation on the Key Vault, it is important that your account is added in Key Vault Access Policy. In this case, we have configured Create, Import, delete and List Access Policies in our Key Vault.
***Set-AzKeyVaultAccessPolicy-VaultName'<Key Vault Name>'-UserPrincipalName<Azure AD UPN>'-PermissionsToKeyscreate,import,delete,list-PassThru **
**
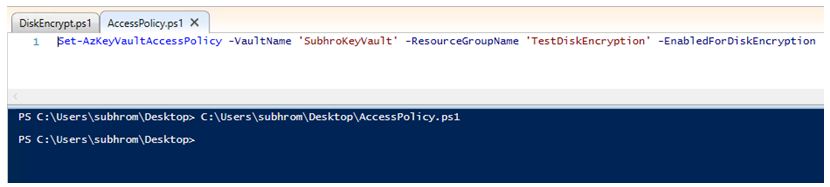
b) Enable Access to Azure Disk Encryption.
This is required, so that Azure Platform can access the Key Vault to retrieve the encryption key, and same it available for Azure VMs. Use below PowerShell command.
Set-AzKeyVaultAccessPolicy -VaultName "<your-unique-keyvault-name>" -ResourceGroupName "MyResourceGroup" –EnabledForDiskEncryption
Once you configure above two steps, you can see below Access Policies configured in Key Vault.
4) Ensure Azure VM can reach Azure Key Vault Endpoint and Azure Active Directory Endpoint. For more details on Network Configuration, please refer this page.
5) Azure Disk Encryption will fail if domain level group policy blocks the AES-CBC algorithm, which is used by BitLocker. For more details on Group Policy requirement, please refer this page.
Create Key Encryption Key (KEK)
This is an optional step, only if you want to encrypt your encryption secret using a Key Encryption Key (KEK). As mentioned above, KEK adds one extra layer of security.
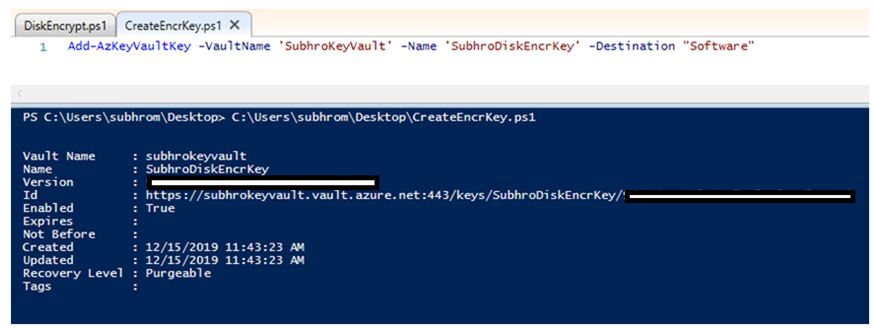
Following command creates a Key Encryption Key (KEK)
Add-AzKeyVaultKey - VaultName <KeyVaultName> -Name <EncryptionKeyName> -Destination "Software"
Here, the value of Destination parameter is Software, which means the Key will be software protected. To create a HSM protected Key, the Destination parameter value will be HSM.
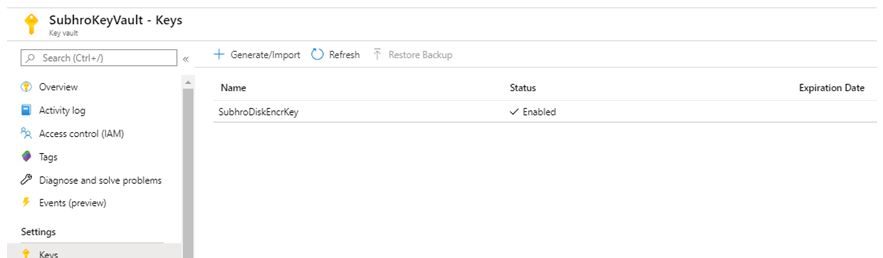
If you now check the portal, you will see that the Disk Encryption Key has been created in Key Vault.
For more details on creating KEK, please visit this link.
Create an Azure VM
We have created a new Azure VM in our lab, with Windows Server 2016 Datacenter Edition. Both Key Vault and Azure VM are in the same region.
The Azure VM has two disks, one OS Disk and one Data Disk. None of the disks are currently encrypted.
**Make sure the data disk is mounted and formatted before you encrypt data disk. **
Also, check disk encryption status from the Operating System. Run manage-bde –status command to check that.
Enable Disk Encryption
Now that we have set the access policies and created the encryption key , let’s proceed with enabling disk encryption.
To enable Disk Encryption, we will use the PowerShell Command Set-AzVMDiskEncryptionExtension.
Use this script to enable Disk Encryption. Change parameters before you run this script.
You might have observed that while enabling encryption in the above script, we have used two arguments -KeyEncryptionKeyUrl and **-KeyEncryptionKeyVaultId. **
This is where we are defining the Key Encryption Key (KEK) to add one additional layer of security.
If we do not specify Key Encryption Key parameters, the disk will still be encrypted using unique secret which is generated by Bitlocker at the time of encryption, and the secret will be stored in the Key Vault. However, if we specify the KEK parameters, the secret will be wrapped by the KEK, adding one extra layer of security.
Validate Disk Encryption Status
There are several ways to ensure that volumes have been encrypted.
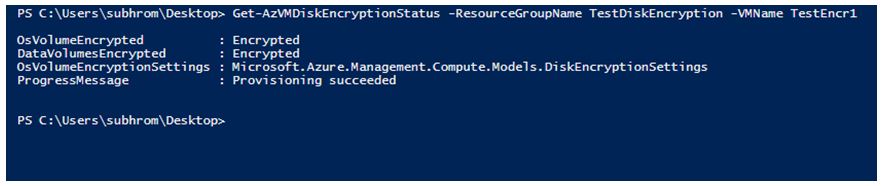
1) Azure PowerShell
Check the Disk Encryption Status using the command ***Get-AzVMDiskEncryptionStatus
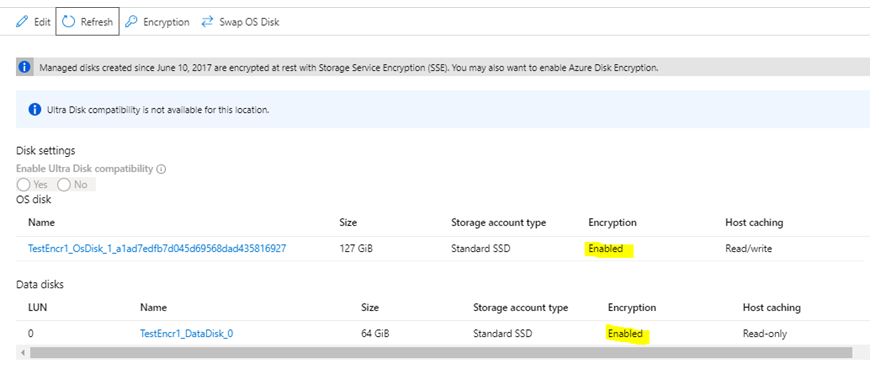
**2) Azure Portal **
Note: Sometimes Data Disk encryption status shows as Not Enabled in the portal, even if it is enabled. In that case, validate the disk encryption status using PowerShell and within the OS. To reflect the data disk encryption status Enabled in the portal, you might need to stop and start the Azure VM.
3) OS Command Line
You can also validate the Disk Encryption Status within the OS, using manage-bde –status command.
4) Disk Management
You can also see the encryption status from the Disk management console. All encrypted volumes will be displayed as “BitLocker Encrypted”.
It is important to note that when you encrypt the disk and disk status shows as Encrypted, that does not mean that encryption is complete for the whole volume. If you login to the system, you might see that the encryption is still in progress for OS and data disks.
You can declare the volume as secure and encrypted only when encryption is completed for the entire volume, which you have to check from the OS.
Data Disk Encryption
As mentioned before, you need to first encrypt OS Disk in Azure Windows VM, if you want to encrypt data disks.
For Azure Windows VM, it is not possible to encrypt data disk, without encrypting OS Disk. However, it is possible for Linux VMs.
The command Set-AzVMDiskEncryptionExtension has a parameter named –VolumeType. This parameter has below options :
- Omitted : If VolumeType parameter is omitted while running the command, both OS and Data volumes will be encrypted . Any data disk which will be added later to this VM will also be encrypted.
- OS: If VolumeType attribute is set to OS, only OS volume will be encrypted.
- All: Same as omitting the parameter, which covers all volumes. However, in our lab, this option did not encrypt data disk. So we recommend not to use the All option.
- Data: Encrypts only data volume. This option is not applicable for Windows VMs.
If you want to encrypt OS volume and all data volumes, do not specify –VolumeType parameter while running the command Set-AzVMDiskEncryptionExtension.
If you add a new disk in an encrypted VM, you have to initialize and format the new volume to enable encryption. You do not need to enable encryption, as it is already encrypted for data disk. You can use manage-bde –status within the OS, to ensure that the new disk is encrypted.
However, to correctly reflect the encryption status for the new disk in Azure Portal, you may need to stop and start the Azure VM.
Backing up Encrypted VMs
Azure Backup Supports backing up Windows and Linux Azure VMs, which are encrypted using Azure Disk Encryption.
However, there are few limitations associated with backing up and restoring encrypted VMs, which are mentioned here. So when you design your backup solution for encrypted VMs, you have to consider these limitations.
Some of the notable limitations are :
1) Backup and Restoration of Azure Encrypted VMs would work within the same subscription and region. The Recovery Services Vault must reside on the same subscription and region.
2) File/Folder level restoration is not possible for encrypted VMs, only disk level restoration is supported. This is true for both Windows and Linux VMs.
In order to backup and restore encrypted VMs, Azure Backup Management Service needs access to the Key Vault. Follow this link to know, how to do that.
For more details on this topic, please refer this article.
Disaster Recovery of Encrypted VMs
Microsoft has published an article, where it has mentioned all the points which need to be considered while enabling ASR Replication for encrypted Azure VMs.
To facilitate replication for encrypted VMs, the encryption key(s) needs to be present within the DR Key Vault.
If the user (who is enabling VM replication) have required access, Site Recovery creates a Key Vault in DR region when replication is enabled, and copies the encryption key from primary key vault to DR key vault.
However, if the user (who is enabling VM replication) does not have key vault access, then the Key Vault admin can copy the encryption key to DR Key Vault using a script which Microsoft has provided.
Disable Disk Encryption
To Disable Disk Encryption for Windows Azure VM, you have to use Disable-AzureRmVMDiskEncryption or Disable-AzVMDiskEncryption.
As per Microsoft, these commands are only supported for Azure Windows VM and will not work in Linux VMs. once you run any of the above two cmdlets, it will install an extension to disable disk encryption.
There is one more command called Remove-AzVMDiskEncryptionExtension, but this command does not disable encryption. This command removes the disk encryption extension from Azure VM, which was installed when you have enabled disk encryption. However, the disks still remain encrypted. So if your goal is to disable disk encryption, do not use this command.
Key and Secret Rotation
Some organizations have security policy to rotate all the Keys, Secrets and Passwords periodically.
If you need to rotate the disk encryption secret or the Key Encryption Key, you have to follow below procedure :
1) To rotate secret, run the same command (Set-AzVMDiskEncryptionExtension), but this time mention a different Key Vault. This is because your original Key vault already has the old secret stored for this VM disk, which it will use every time. But once you mention a new Key Vault, a new secret will be generated, which will be used going forward.
2) To rotate the Key Encryption Key (KEK), you can use same command (Set-AzVMDiskEncryptionExtension) with same Key Vault, but this time mention a new Key Encryptin Key.
Normally, it is recommended to rotate the Key Encryption Key periodically. You do not need to use new Key Vault every time you rotate the KEK, all you need is to create a new KEK and run the command again with new KEK. This is a better approach of Key Rotation, rather than rotating all secrets.
For more information, please visit this link.
See Also
Azure Disk Encryption for virtual machines and virtual machine scale sets
Azure Disk Encryption scenarios on Windows VMs
If you find this article useful, please visit my other articles here.