SharePoint Server 2019: Working with Microsoft Identity Manager 2016 SP1
Introduction
Microsoft Identity Manager (MIM) 2016 is built on the identity and access management capabilities of FIM 2010 R2. Like its predecessor, MIM helps us to manage the users, credentials, policies, and access within your organization. Additionally, MIM 2016 adds a hybrid experience, privileged access management capabilities and support for the new platforms.
User profile synchronization in versions prior to SharePoint 2016 relied on a built-in Forefront Identity Manager (FIM), which ran inside SharePoint Server. However, in SharePoint Server 2016 and SharePoint Server 2019, FIM has been removed. User profile synchronization will be done by Microsoft Identity Manager, which will act as the successor to FIM. MIM will reside in a separate Server other than the SharePoint 2019 Server. Thus, if we already have MIM Server, we can leverage it and use it with SharePoint 2019.
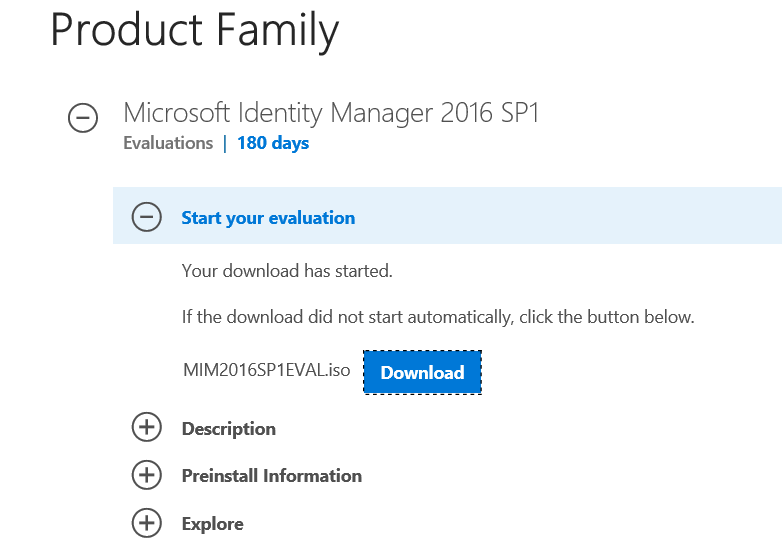
Download Microsoft Identity Manager SP1
MIM 2016 installation involved installation of separate hotfix to complete the installation successfully, however, MIM 2016 SP1 comes with the inbuilt hotfix, which makes the installation of MIM easier. Before getting started with the installation procedure, let's download the setup file from the evaluation center . This is a fully functional 180-day trial version. We can also download the production-ready version directly from Microsoft Volume Licensing Center.
Prerequisites
Once we have downloaded the Installation file, prior to starting the installation we have to ensure that the below components are in place.
- Active Directory
- Windows Server 2019
- SQL Server 2017
- SharePoint Server 2019
We can have other combinations of hardware. Detailed hardware requirements information can be obtained from here .
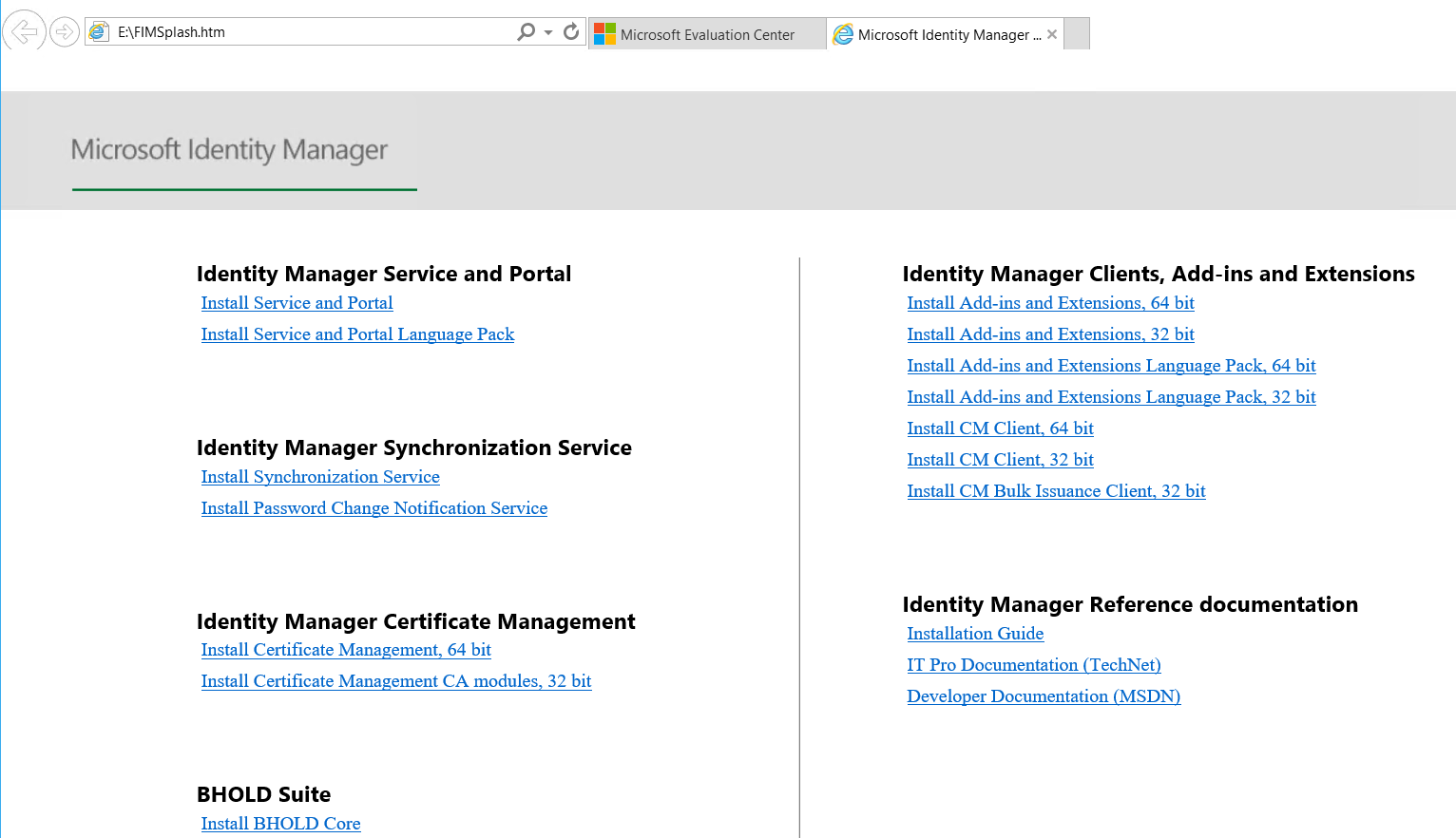
Install Identity Manager
From the downloaded installation media, go to the Synchronization Service folder path and run the splash file.
This will start Identity Manager Synchronization Service Setup Wizard.
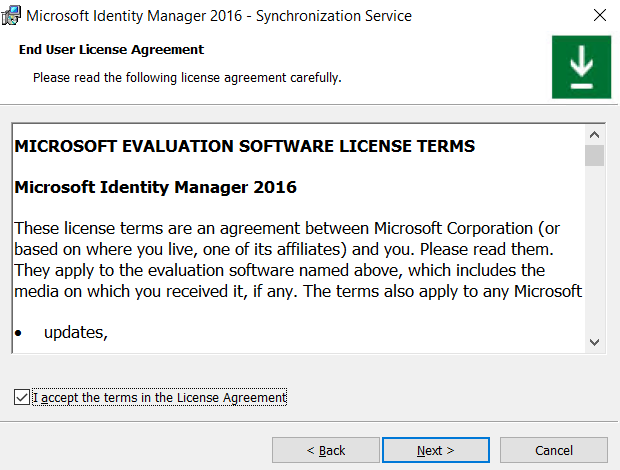
Accept the license agreement and proceed.
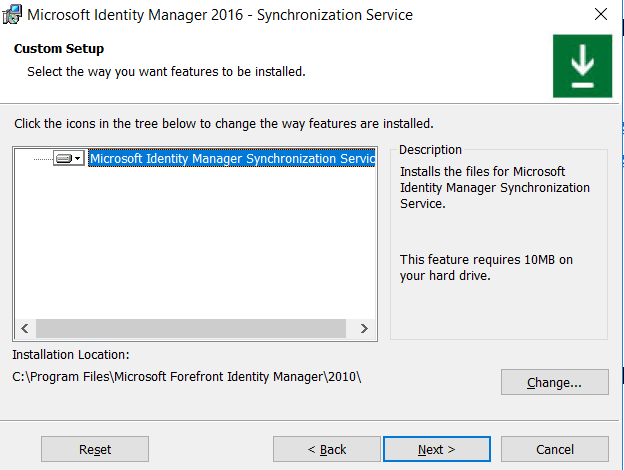
Select Microsoft Identity Manager Synchronization and click Next.
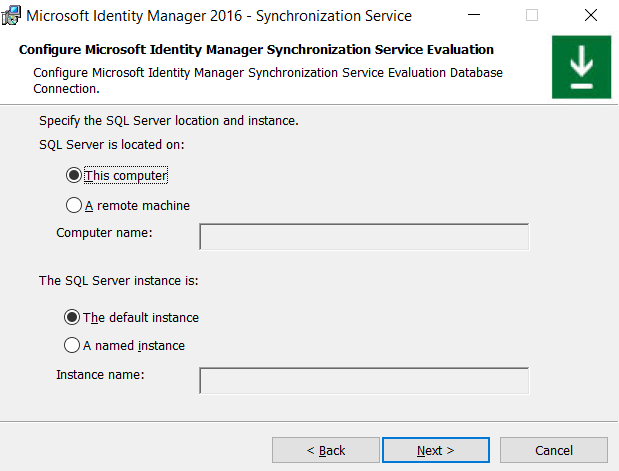
The next screen in the wizard will ask you to supply some information about the instance of SQL Server, which we want MIM to use. Choose This Computer, if SQL Server is local or type the name of the remote SQL Server instance. We are installing MIM Server in SQL Server, so we will go with the configuration given below.
If we are installing MIM to a remote instance of SQL Server, SQL Server Native client must already be installed on MIM Server before installing MIM Synchronization Service.
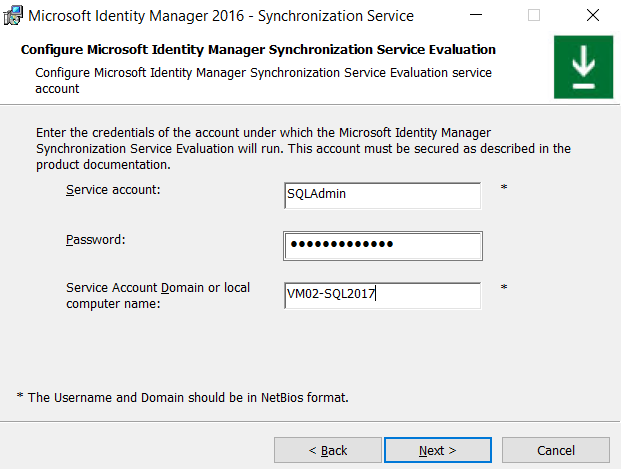
In the next screen, specify the Service Account credentials.
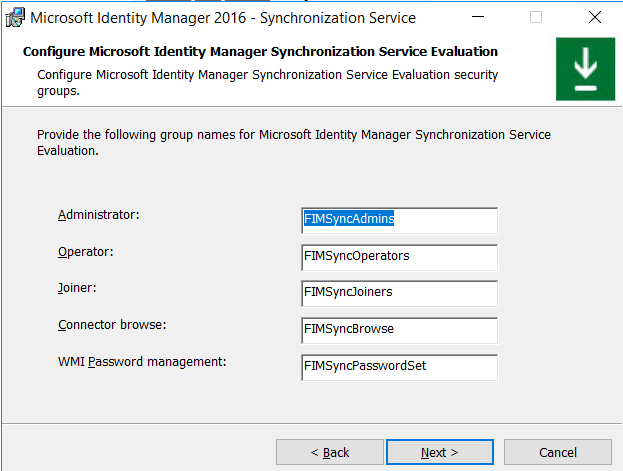
Now, we have to set up the security groups, which are required for MIM to function. We can leave it with the default values.
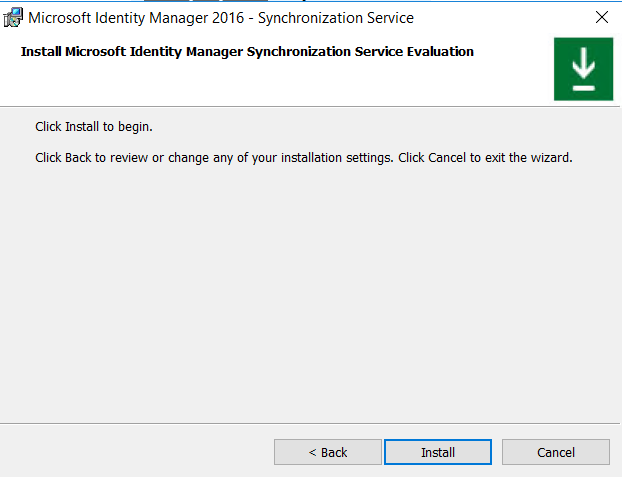
Click Install to proceed with the installation.
Thus, we are done with installing MIM 2016 in the SQL 2017 server.
Restart the system, so that the security group membership comes to effect.
Install the SharePoint Management Agent
Now, we have to install SharePoint Management Agent (SPMA) , which will be used to connect MIM to SharePoint 2019. It can be downloaded here  .
.
Once the executable has been downloaded, proceed with the installation, using SharePoint Connector Setup Wizard.
Click Install to start the installation process.
After some time, SharePoint Connector installation will be complete.
To complete SharePoint Connector installation, we can restart Forefront Identity Manager Service from Services.msc.
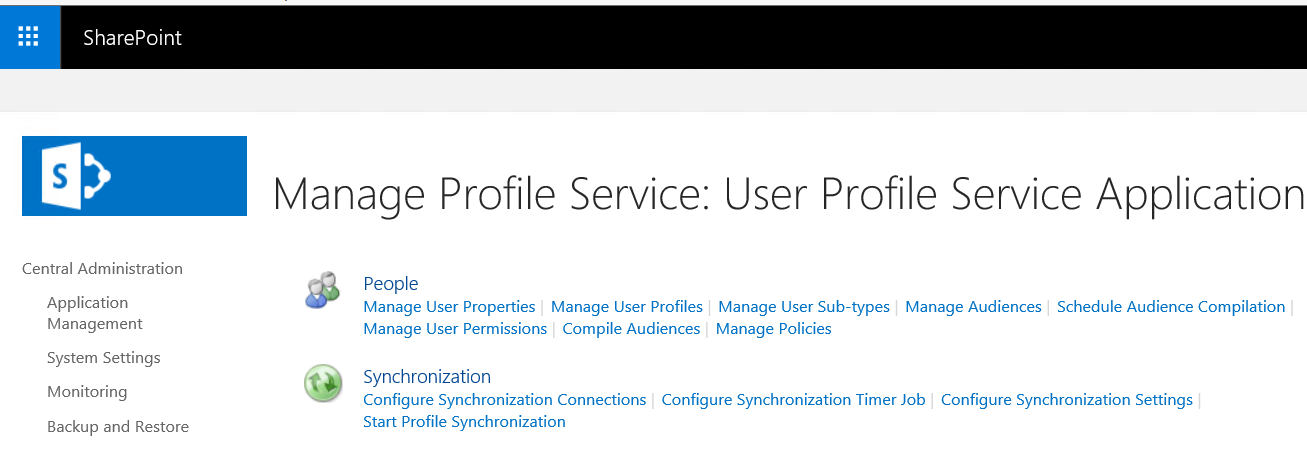
Configure Synchronization Settings
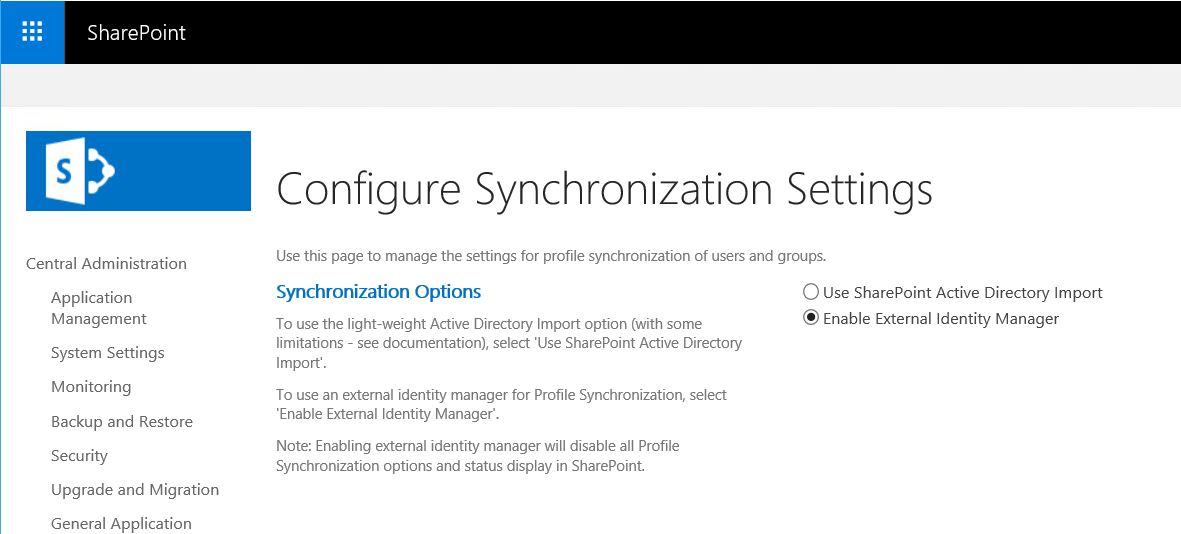
In order to enable User Profile Synchronization, using MIM, we have to set up synchronization settings.
Select Enable External Identity Manager and click OK.
Install the solution files for SharePoint Synchronization
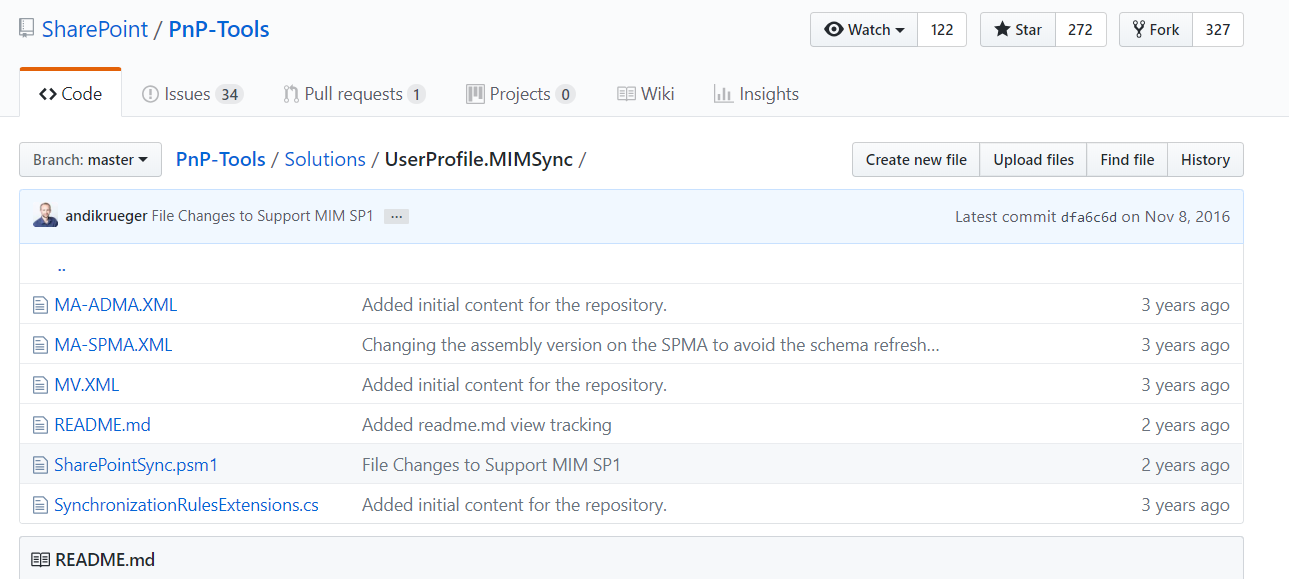
We can download the entire solution files, which we will use to set up SharePoint Synchronization here. We can get the entire files as a zip by going to the root location.
The solutions scripts from UserProfile.MIMSync have been copied to the working directory.
Get Configuration Values for SharePoint Synchronization Script
To enable SharePoint Synchronization, we will be running the SharePointMIMSync.ps1 file in MIM Server. Prior to running it, we will have to update the script with our environment variables.
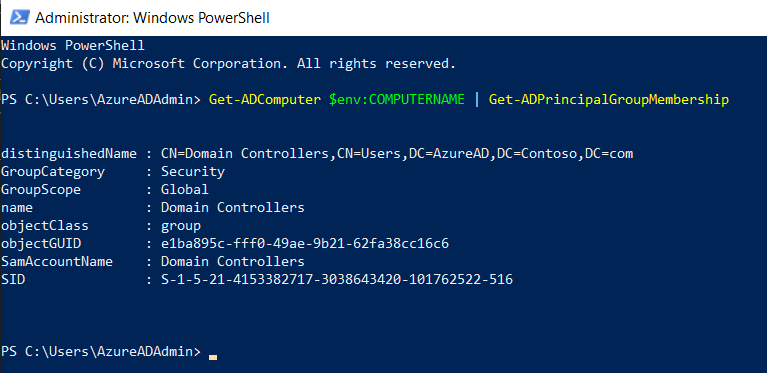
We will need OrganizationalUnit and ForestDnsName parameters, which will have to be updated in the script. We can get the organizational unit by running the command given below. The distinguished name (DC=AzureAD,DC=Contoso,DC=com) will correspond to the Organizational Unit.
Get-ADComputer $env:COMPUTERNAME | Get-ADPrincipalGroupMembership
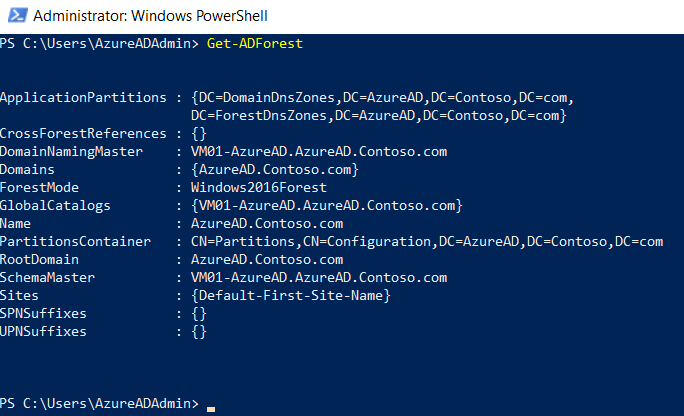
We can get AD forest name by running the command given below.
Get-ADForest
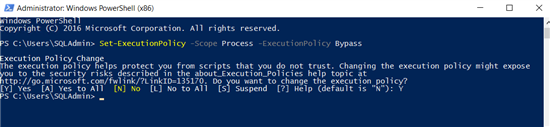
Prior to running the Synchronization script, ensure that Set-ExecutionPolicy script given below has been run, else we may get the error File is not digitally signed.
Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass
Run SharePoint Synchronization script
Now, we are ready to run SharePoint Sync Script. The running of the script involves two steps, which are given below.
- Import SharePointSync Module
- Run ‘Install-SharePointSyncConfiguration’ Command
After navigating to the directory, where the script is present, let’s load SharePointSync.psm1 module, as given below.
Import-Module .\SharePointSync.psm``1
Now, we can finally run the ‘Install-SharePointSyncConfiguration’ command, which will enable MIM Synchronization with SharePoint. It needs the parameters given below to be filled.
- -Path - Location where the sync script is located.
- -ForestDnsName - AzureAD.Contoso.com (we got this earlier by running Get-ADForest command).
- -ForestCredential - Account that will be used to read objects from Active Directory. This account must have Replicate-Directory-Changes permissions in the Active Directory that is to be synchronized. We are using an AD administrator account here.
- -OrganizationalUnit - This is the distinguished name of the Active Directory container to be synchronized.We can get it by running the command “Get-ADComputer $env - COMPUTERNAME | Get-ADPrincipalGroupMembership”.
- -SharePointUrl - SharePoint Central Admin URL
- -SharePointCredential - SharePoint Farm Account.
Synchronization Script given below can be saved to a PS1 file say ‘SharePointMIMSync.ps1’ and we can run it from the console as ‘.\ SharePointMIMSync.ps1’.
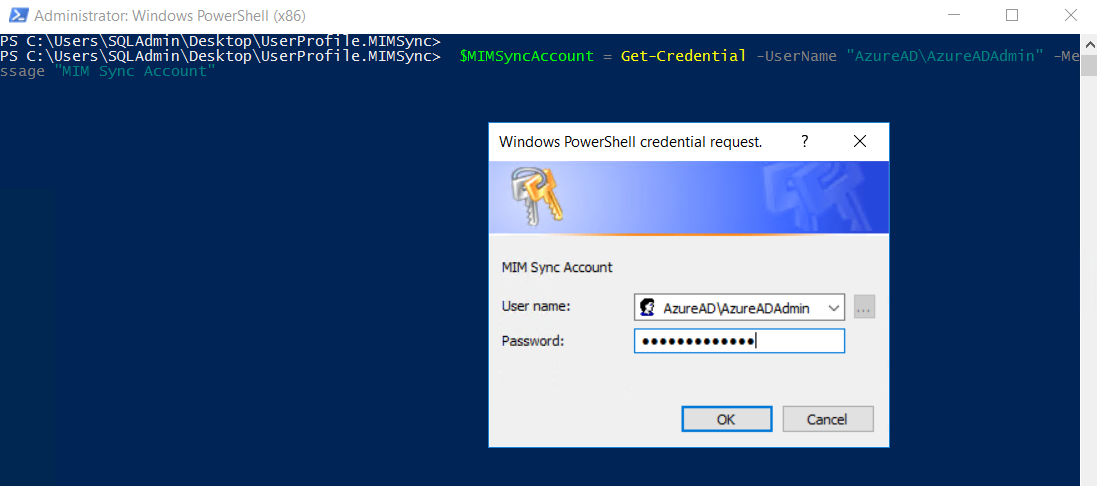
$MIMSyncAccount = Get-Credential -UserName ``"AzureAD\AzureADAdmin" -Message ``"MIM Sync Account"
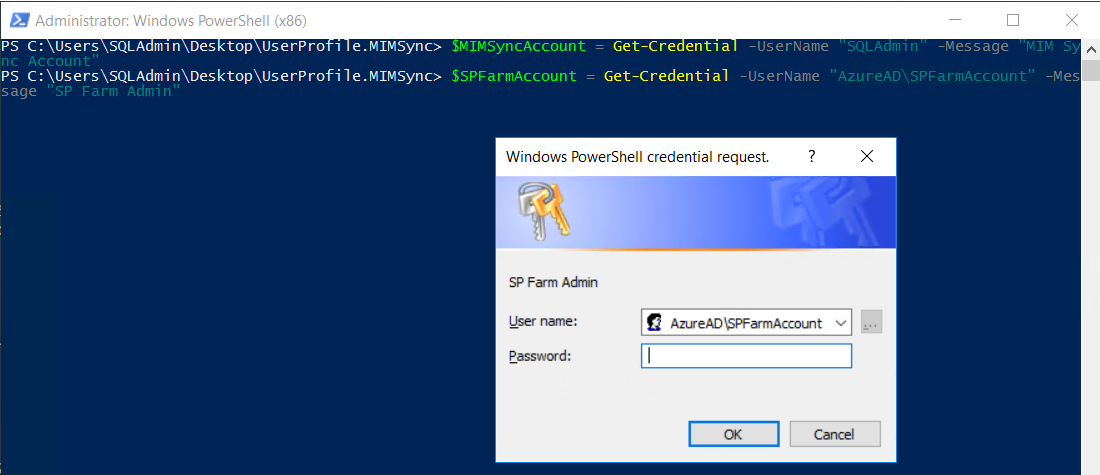
$SPFarmAccount = Get-Credential -UserName ``"AzureAD\SPFarmAccount" -Message ``"SP Farm Admin"
Install-SharePointSyncConfiguration -Path C:\SharePointMIMSync -ForestDnsName AzureAD.Contoso.com -ForestCredential $MIMSyncAccount -OrganizationalUnit ``"DC=AzureAD,DC=Contoso,DC=com" -SharePointUrl "Https://CentralAdminURL"`` -SharePointCredential $SPFarmAccount
On running Synchronization Script, it will ask for Sync Account, which we can input, as shown below.
It will also ask for SharePoint Farm account, which we can enter and click OK.
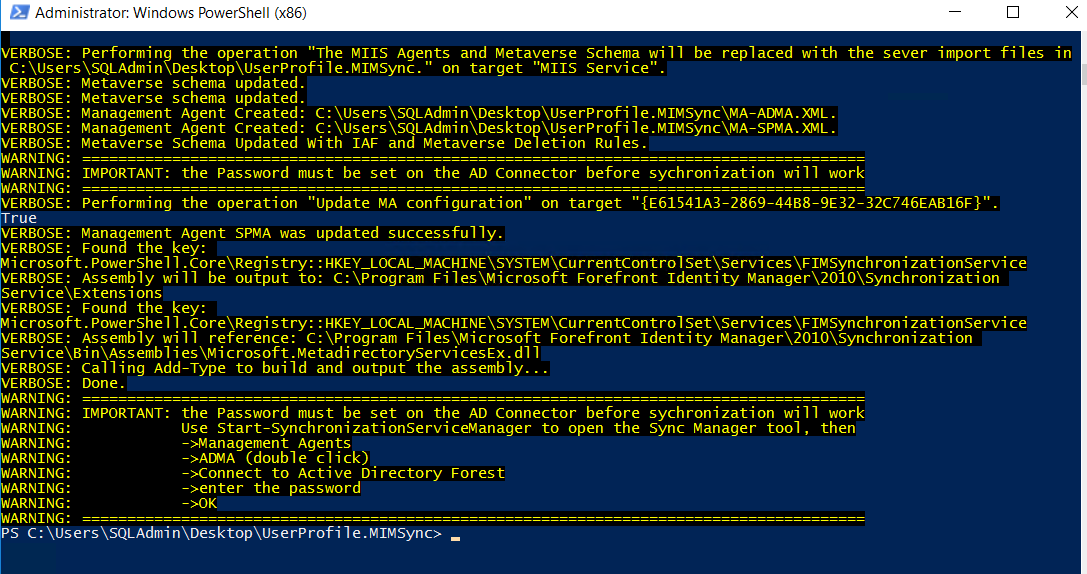
This will complete SharePoint Synchronization configuration and we will get the message given below. It has specifically said that before we start the synchronization, we should set the AD account password in the AD connector, which we will see in the coming section.
Run Synchronization Service Manager
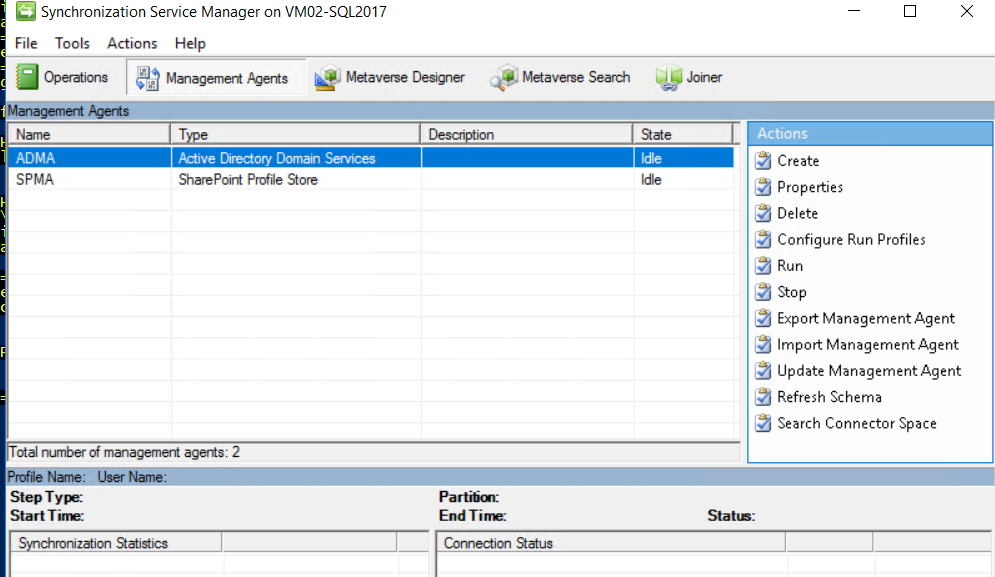
Now, we can start Synchronization Service Manager to start the Synchronization of User Profiles.We can see two management agents in Service Manager, which are given below.
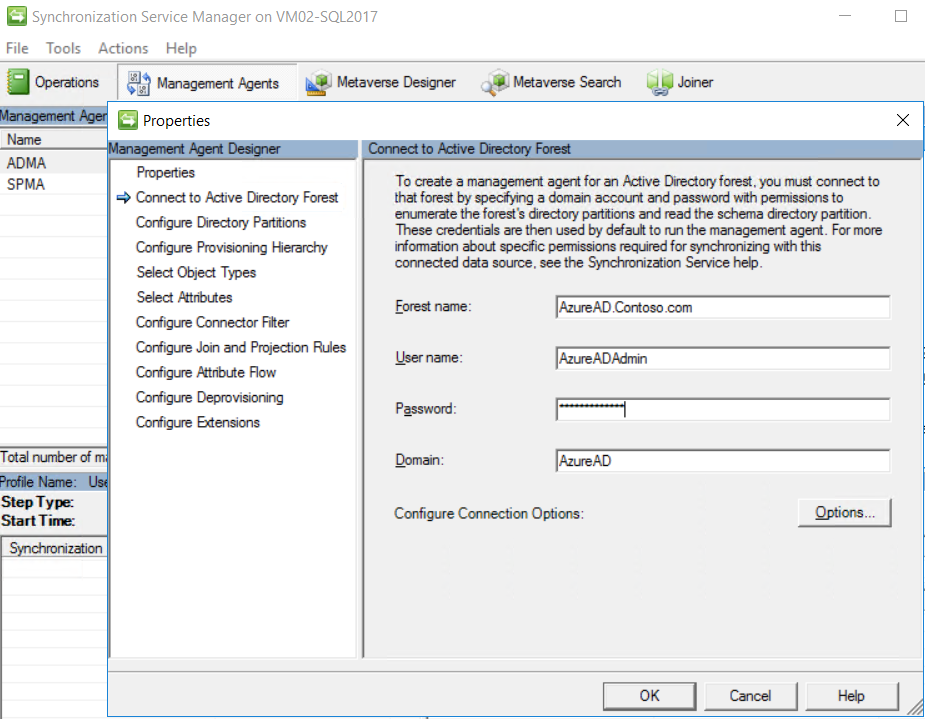
Click ADMA and go to Connect to Active Directory Forest tab. Here, we have to specify the password for the SyncAccount that has Replicate-Directory-Changes permissions in Active Directory.
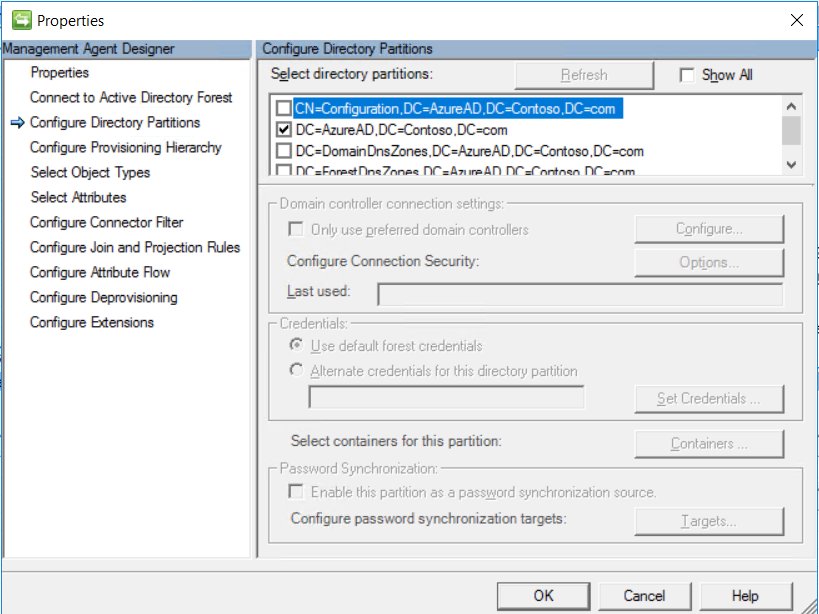
Also, ensure that we have selected AD partitions correctly, so that synchronization runs correctly.
Before running synchronization command, let's restart Forefront Identity Manager Service.Finally, we can run SharePoint Synchronization Service.
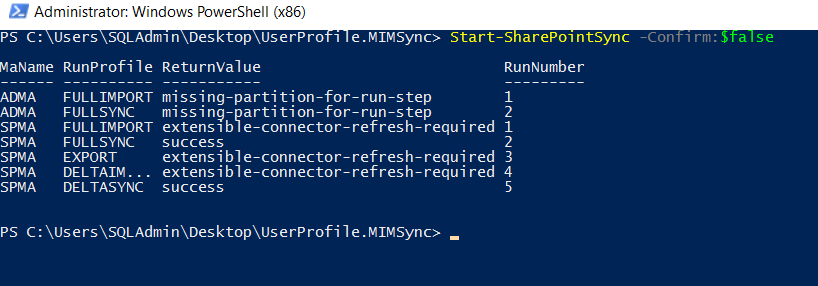
Start-SharePointSync -Confirm:$false
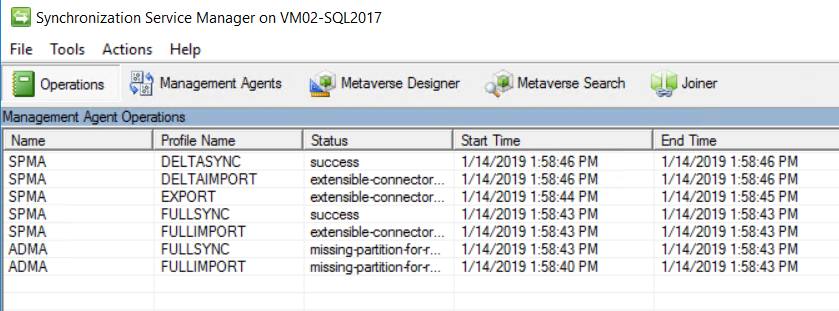
It will perform the import of user profiles and we can see the success and details in Service Manager, as shown below.
Summary
Thus, we saw how to install and configure Microsoft Identity Manager 2016 SP1 for SharePoint Server 2019.