Windows 10: Troubleshooting Telemetry Configuration and Cumulative Updates
Overview
Windows 10 has multiple options to handle telemetry data and are explained in this article:
/en-us/windows/privacy/configure-windows-diagnostic-data-in-your-organization
The diagnostic data is categorized into four levels:
- Security: Information that’s required to help keep Windows, Windows Server, and System Center secure, including data about the Connected User Experiences and Telemetry component settings, the Malicious Software Removal Tool, and Windows Defender.
- Basic; Basic device info, including: quality-related data, app compatibility, and data from the Security level.
- Enhanced: Additional insights, including: how Windows, Windows Server, System Center, and apps are used, how they perform, advanced reliability data, and data from both the Basic and the Security levels.
- Full: All data necessary to identify and help to fix problems, plus data from the Security, Basic, and Enhanced levels.
Configuration
These levels can be configured by Group Policy Object which is available in Windows 10 ADMX Templates: https://www.microsoft.com/en-us/download/details.aspx?id=56880
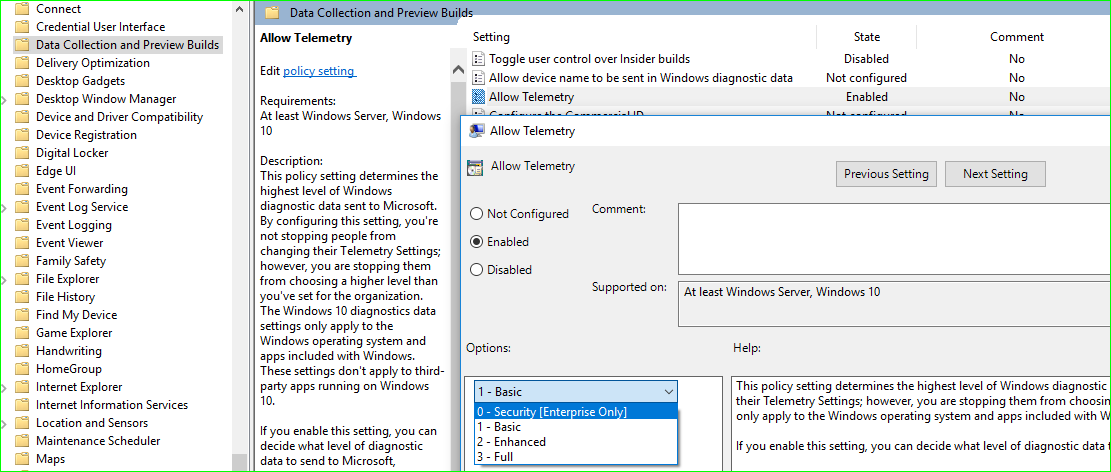
Location : Administrative Templates >> Windows Components >> Data Collection Preview Builds.
Policy : Allow Telemetry
Configuration Options :
- 0 - Security [Enterprise Only]
- 1 - Basic
- 2 - Enhanced
- 3 - Full
Issue
The one which we will discuss is 1st one 0-Security [Enterprise Only]
So if you have option 1 configuration (0-Security [Enterprise Only]) enabled in your environment only update mechanism is either Windows Server Update Service (WSUS) or ConfigMgr / SCCM and you have Windows 10 - 1703 / 1709 or 1803 clients then you will see that there is NO Cumulative Update installed. Windows 10 - 1607 build is not affected with this.
This affects security updates released by Microsoft for Adobe Flash as well.
However only Office related updates get installed successfully.
If you will check compliance report in ConfigMgr / SCCM that will show you COMPLIANT which is not correct.
Quick way to check if you are affected is to run these PowerShell commands :
Commands:
$MSMU = New-Object -ComObject "Microsoft.Update.ServiceManager"
$MSMU.Services | select Name, IsDefaultAUService
Results:
Name IsDefaultAUService
---- ------------------
DCat Flighting Prod False
Windows Store (DCat Prod) False
Windows Server Update Service False
Windows Update True
With option 1 configuration (0-Security [Enterprise Only] enabled you will see Windows Server Update Service -WSUS Set to False and Windows Update is set to True
So in order get Windows 10 Cumulative Updates and Adobe Security Updates installed as some of you may have been vulnerable since a long time as Cumulative updates are missing , although compliance data shows you are compliant , you need to do this :
Change Telemetry configuration to 1- Basic or set it to Not Configured
After configuration is changes , run PowerShell command again and it should show results like this:
Results:
Name IsDefaultAUService
---- ------------------
DCat Flighting Prod False
Windows Store (DCat Prod) False
Windows Server Update Service True
Windows Update False
https://docs.microsoft.com/en-us/windows/deployment/update/windows-update-sources
This has been reported to Microsoft and fix is supposed to be released in September 2018 Cumulative Update. I will update this blog post after testing.
Also seeing current scenario it seems affected environments need to keep GPO setting set to 1-Basic or Not Configured till all the clients are actually fully compliant (Really Compliant ) with September 2018 CU (Deployable via WSUS/ConfigMgr-SCCM) OR MS releases some additional fix which doesn't need GPO configuration change.
Don't wait: update asap.
Additional Details about Dual Scans
- https://blogs.technet.microsoft.com/swisspfe/2018/04/13/win10-updates-store-gpos-dualscandisabled-sup-wsus/
- https://blogs.technet.microsoft.com/wsus/2017/05/05/demystifying-dual-scan/
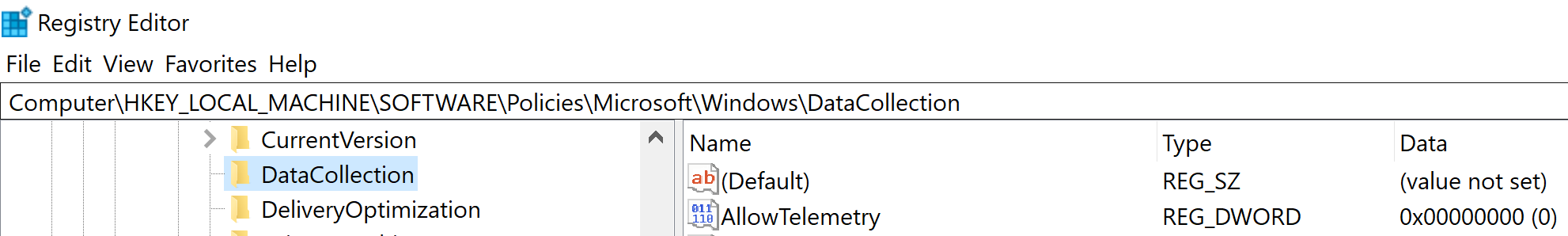
Registry Location :
**