Azure : Encrypt Azure Virtual Machine Disks Using Key Vault
Microsoft provides the ability to encrypt VMs VHD files. This can be achieved by the Azure Key Vault service. But, before we start, let's find an explanation about Azure Key Vault and what this can be done.
Azure Key Vault is a vault that contains keys, secrets and it is hosted in the Azure Cloud.
Important Terms & Definitions
| Term | Definition |
| KEK - Key Encryption Key | A cryptographic key that is used to encrypt other keys for transmission or storage but not application data. Source |
| Software Keys | Softwares keys are used basically in compute VMs and are most used from dev/test users. |
| HSM keys - Hardware Security Modules | HSM keys are used for production environments and are available in Premium Tier. |
| Service Principal | It's a service account with specific privileges which allow running several tasks on Azure. |
| Application ID | Application ID in all case is the Client ID in Azure Active Directory. |
Prerequisites
Bellow are the Azure Disk Encryption Prerequisites :
- AAD Enterprise Application
- Key Vault
- Virtual Machine: The solution is supported for specific Azure Standard VM tiers,A, D, DS, G, GS, F, and so forth series IaaS VMs
- Install Module AzureRM using the next script
Install-Module -Name AzureRM -Repository PSGallery -Force
Click here for more details.
Create AAD Enterprise Application
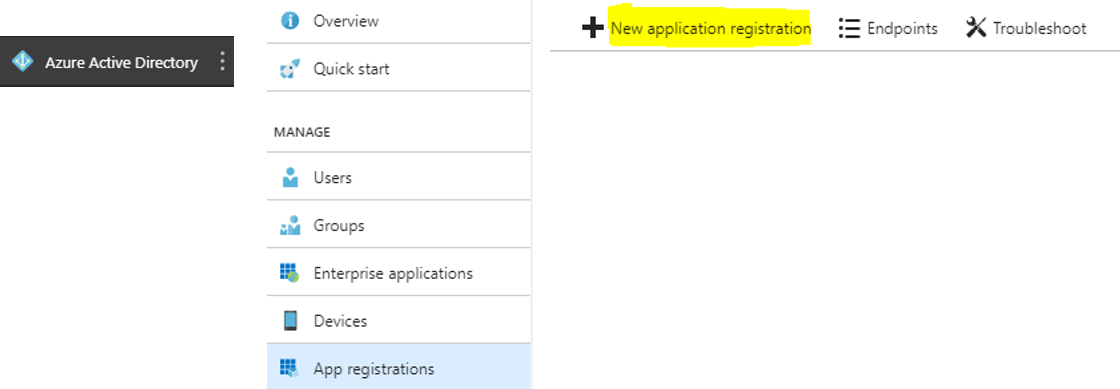
From the Azure Portal, Azure Active Directory - App registrations - New application registration
Next, on the Create blade, type Name of the application, select Application type, set any Sign-on URL (it's typical, it won't be used) and click Create.
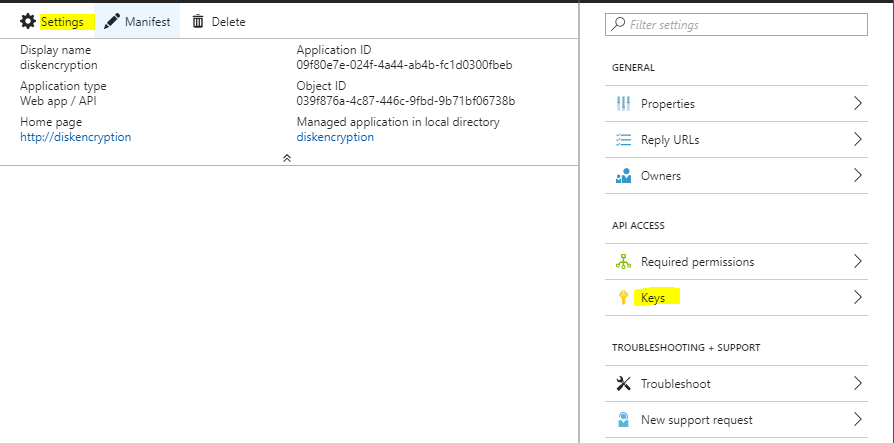
AAD Application is deployed and the next step is to create a Key. From Settings - Keys blade
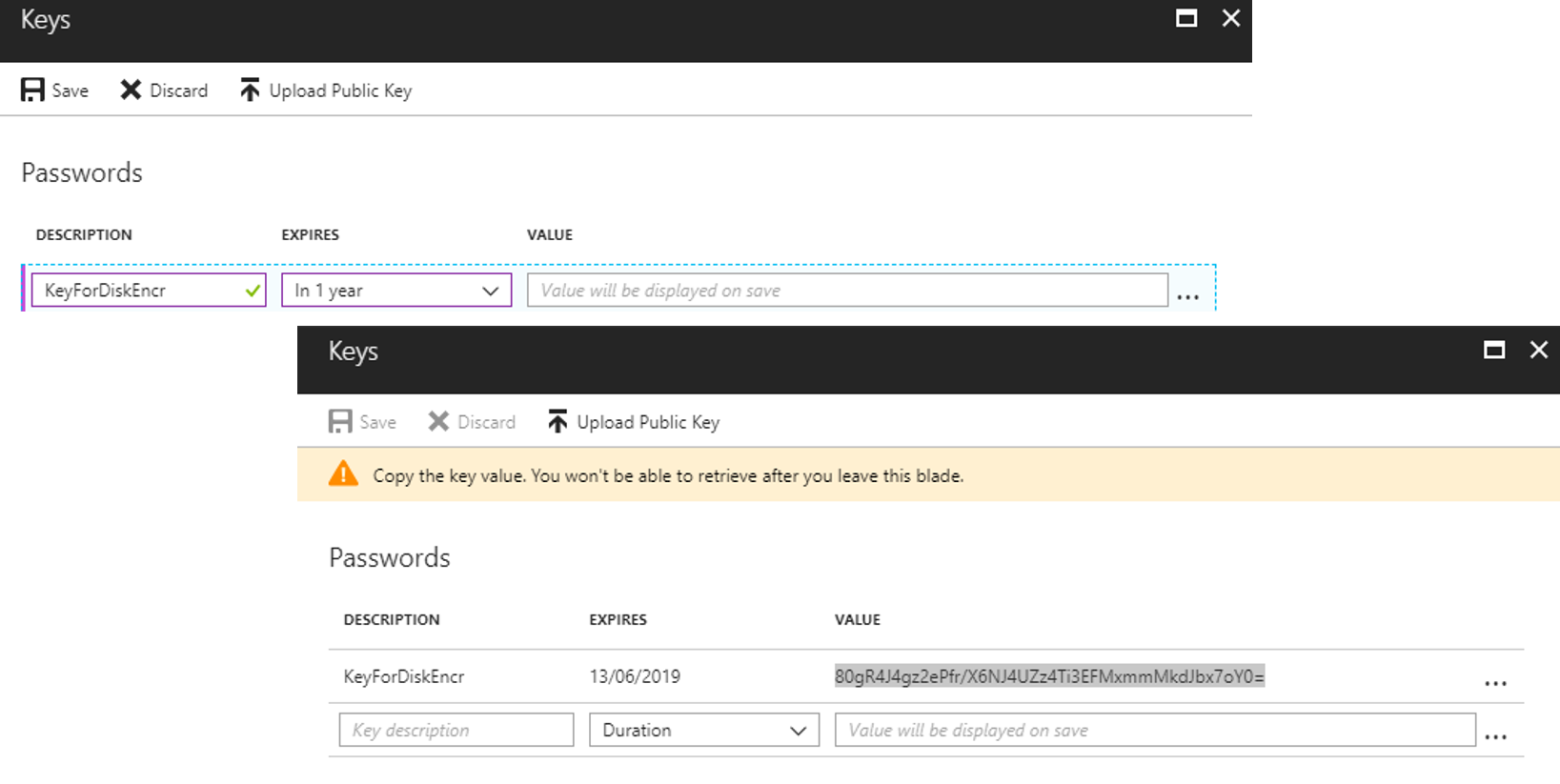
Type a DESCRIPTION set the EXPIRES field value and click Save.
Important Notice: Copy the value because this value will not be available after the blade close.
Create Key Vault
After the AAD Application is deployed, the next big thing is to create the Azure key vault.
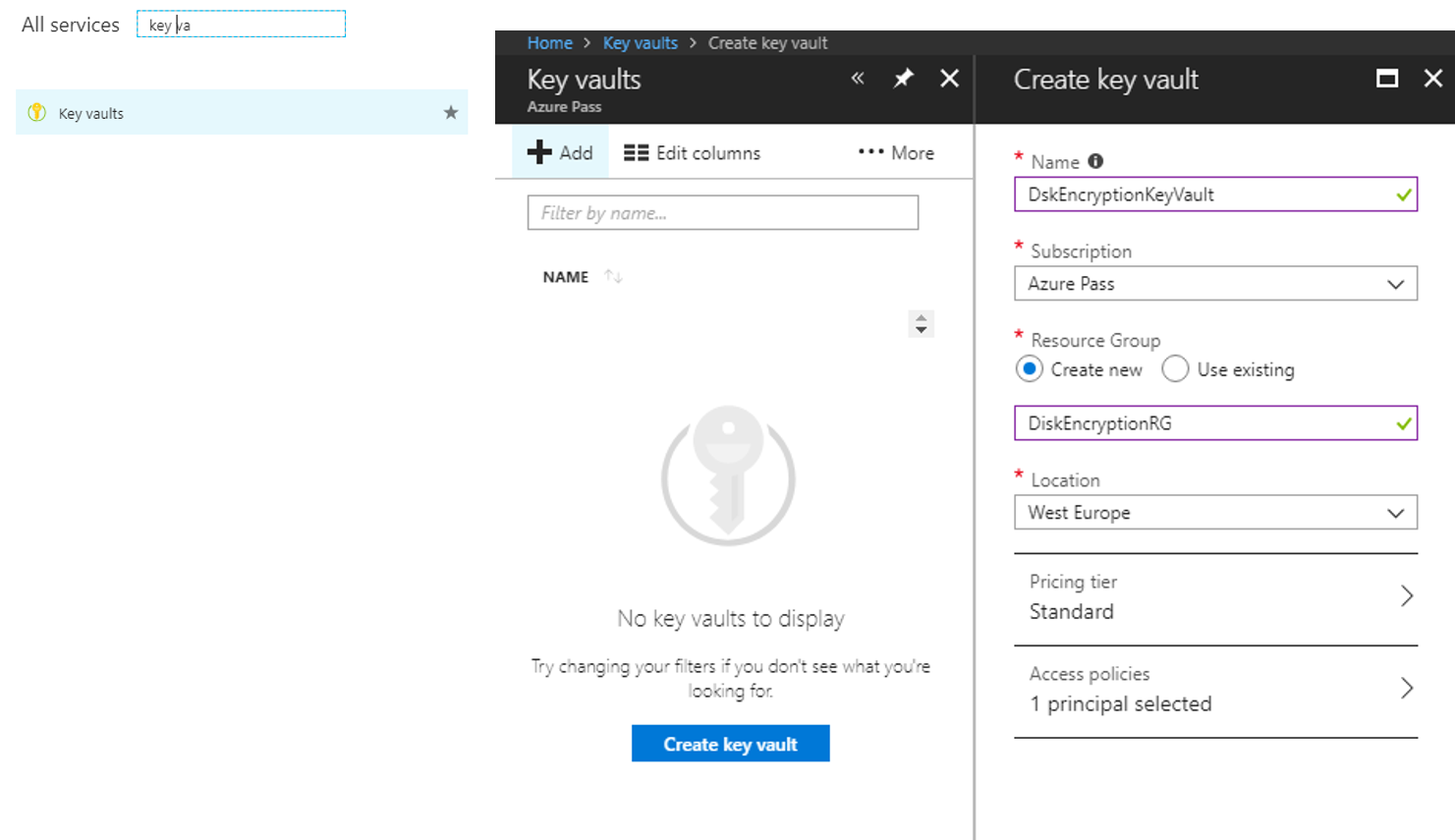
First, search for {key vault} service and next click button Create key vault.
Type key vault Name, select Subscription, if not exists create Resource Group, select a Location a Pricing tier (Standard for this scenario) and create a NEW principal in Access Policies.
Create Key Vault Key
Next, create the key Vault Key from the main key vault blade, select Settings - Keys - [+Generate/Import], type the Name and click Create.
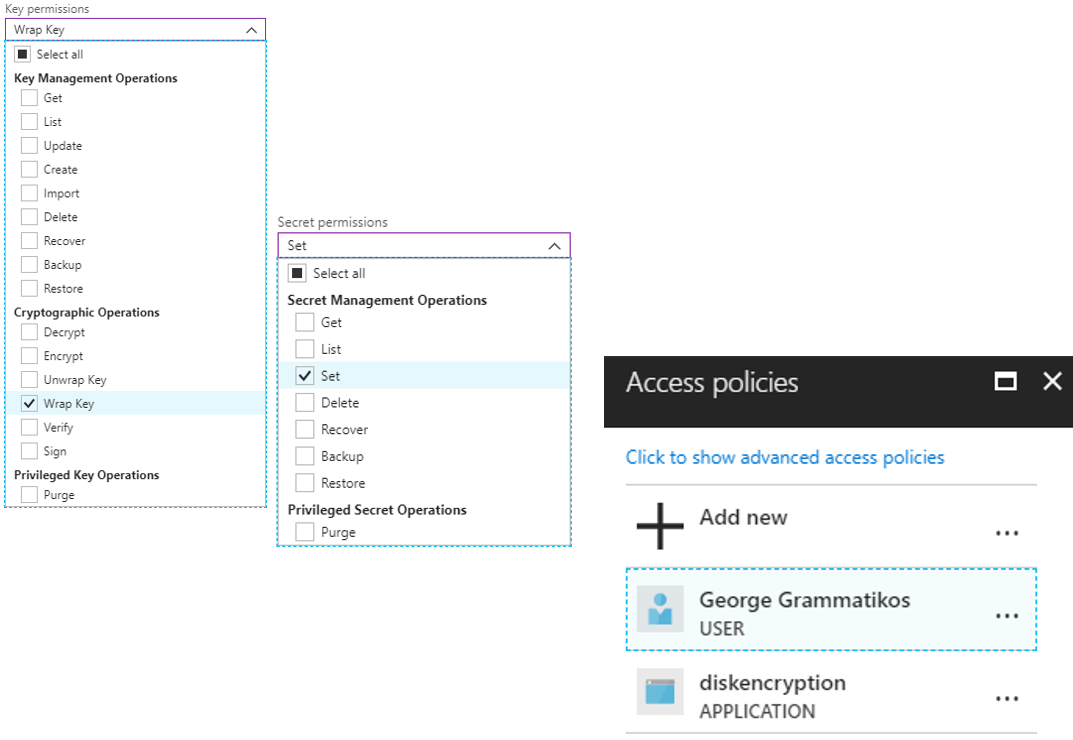
Create New principal in Access Policies blade.
This is an important step because we add permission to the key vault for the newly registered application. Firstly, expand key permissions and select Wrap Key value, next expand Secret permissions and select Set value. Since we chose the necessary permissions we need to add the AAD application to the key vault Access policies.
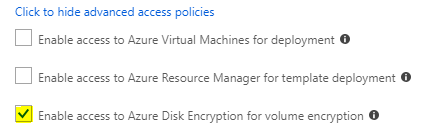
Key Vault Advanced Access Policies
From the main Key Vault blade select Access Policies, click {show advanced access policies} link - check option [Enable access to Azure Disk Encryption for volume encryption] and click Save.
Powershell Commands For Encryption
Important Notice: Before run anything, we must be sure that the disks are backed up!!!
The first stage was about AAD App registration, Azure Key Vault creation, and configuration. Now, we are ready to move forward to the next steps which are the Powershell command for disk encryption with BitLocker.
Before executing the Powershell script must be sure that know all the necessary variables which are :
$ResourceGroupName = 'Resource Group Name'
$vmName = 'Virtual Machine Name'
$AADApplicationID = 'Application ID'
$AADApplicationSecret = 'Application Secret'
$KeyVaultName = 'Key Vault Name'
$keyVaultKeyName = 'Key Vault Key Name'
$KeyVault = Get-AzureRmKeyVault -VaultName $KeyVaultName -ResourceGroupName $ResourceGroupName
$DiskEncryptionKeyVaultURI = $KeyVault.VaultUri
$DiskKeyVaultResourceId = $KeyVault.ResourceId
$DiskkeyEncryptionKeyUrl = (Get-AzureKeyVaultKey -VaultName $keyVaultName -Name $KeyVaultKeyName).Key.kid;
Set-AzureRmVMDiskEncryptionExtension -ResourceGroupName $ResourceGroupName -VMName $vmName `
-AadClientID $AADApplicationID `
-AadClientSecret $AADApplicationSecret `
-DiskEncryptionKeyVaultUrl $DiskEncryptionKeyVaultURI `
-DiskEncryptionKeyVaultId $DiskKeyVaultResourceId `
-KeyEncryptionKeyUrl $DiskkeyEncryptionKeyUrl `
-KeyEncryptionKeyVaultId $DiskKeyVaultResourceId `
-VolumeType All
Conclusion
Azure Virtual Machines disk can now be encrypted with bitlocker. That's great news because the disks on Azure have an extra level of security. Even if someone manages to gain access to storage disks, he will never be able to see data.
See Also
Microsoft docs
GitHub
| Softwares keys are used basically in compute VMs and are most used from dev/test users. |
| It's a service account with specific privileges which allow running several tasks on Azure. |
| It's a service account with specific privileges which allow running several tasks on Azure. |