Mitgations for Speculative execution side-channel vulnerabilities-Meltdown & Spectre
One-Stop-Shop for mitigating CVE-2017-5753, CVE-2017-5715, and CVE-2017-5754. (Speculative execution side-channel vulnerabilities / Meltdown and Spectre on Windows Platform.)
Most of the Intel - AMD and ARM processors are affected with vulnerabilities which are abusing CPU Data Cache timing to leak information out of misconfigured speculated execution.
Here is what needs to be done before Windows Security Fix is deployed:
- Make sure Anti-Virus is compatible with windows patch:
Thanks to kevin.beaumont@gmail.com for sharing the spreadsheet with updated information regarding AV Vendor compatibility.
If AV is not compatible and the patch is deployed without proper testing, users can face Blue Screen issues. It is advisable to get an official response from AV Vendor.
More Information: https://support.microsoft.com/en-us/help/4072699/important-information-regarding-the-windows-security-updates-released
Registry Tweaks: https://www.kb.cert.org/vuls/id/AAMN-AUP5VG (Make sure this is checked with AV vendor before executing.)
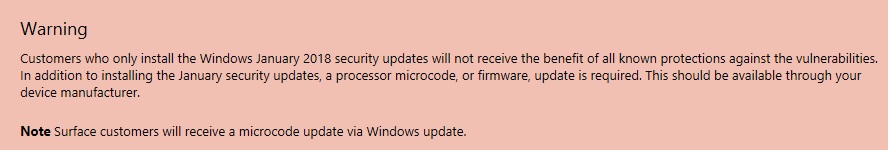
- Install appropriate Windows Patch. (+ Firmware Update is needed to fix the vulnerabilities)
Windows Client OS:
Windows Server OS: (Registry configuration changes are needed, below link has details)
MS Advisory:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180002
This advisory addresses the following vulnerabilities:
CVE-2017-5753 - Bounds check bypass
CVE-2017-5715 - Branch target injection
CVE-2017-5754 - Rogue data cache load
Guidance for SQL Server against Speculative execution side-channel vulnerabilities:
https://support.microsoft.com/en-us/help/4073225/guidance-for-sql-server
- Install Firmware Update:
Contact appropriate Hardware Vendor to get a firmware update. ***As mentioned by Microsoft, installing OS patch only is not enough to fix this vulnerability and Firmware update is mandatory.
Enterprises should connect with their Account Managers in order to get proper updated information from the hardware vendor.
- Lenovo has released advisory and have mentioned providing updates in next 24 Hours or so: (Updated 1/4- Affected Models + Fix release Date)
https://support.lenovo.com/sa/en/solutions/len-18282
- Intel advisory is available here:
https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00088&languageid=en-fr
https://newsroom.intel.com/news/intel-responds-to-security-research-findings/
- Deep Dive Technical Analysis:
https://googleprojectzero.blogspot.com/2018/01/reading-privileged-memory-with-side.html
- PowerShell Commands for Protection Verification:
Install-Module SpeculationControl
Get-SpeculationControlSettings
More Details: https://support.microsoft.com/en-hk/help/4073119/windows-client-guidance-for-it-pros-to-protect-against-speculative-exe
**
Nessus Plugin Details:**
https://www.tenable.com/blog/the-first-major-security-logos-of-2018-spectre-and-meltdown-vulnerabilities
Apple is expected to release fix:
https://support.apple.com/en-us/HT208394
There are chances of performance degradation after updates are installed.