Windows 2008 R2: A Malware and Firewall Protection Solution for the Private Cloud
Applies To
This article is based on Hyper-V 2.0, this might not apply to Hyper-V 3.0 (Server 2012)
Introduction
Private clouds are becoming increasingly necessary and common in both large and small environments due to the significant benefits delivered by a private cloud. However, administrators often struggle with the application of basic security policies in a private cloud deployment. These include firewall, antivirus and antispyware policies.
An example is a Private Cloud infrastructure containing multiple virtual machines for different types of networks, services or even clients – this infrastructure needs to have strong security policies applied. Each of these elements needs isolation, individual policies and rules that are in accordance with business requirements. Even if you have a private cloud only for your local VMs, sometimes we need different security configuration settings for lab networks, production networks, externals servers, etc. Host-based firewalls and antivirus will not help you to protect all virtual machines in your private cloud.
I’ve identified a potentially useful solution to many of these security issues in the Microsoft Private Cloud: V-Firewall for Microsoft Hyper-V. This tool consists of a management console and one agent per host that helps enable you to apply important security policies based on your requirements. It also includes others features such as a Heartbeat Service and Bandwidth Throttling.
With a single and easy to use console and intuitive installation, the V-Firewall offers centralized management of your entire virtual environment to implement such policies, as you can see in figure 1.
Figure 1 – V-Firewall Console
Firewall
As I mentioned earlier, in large private cloud deployments it can be challenging to manage the firewall for virtual machines with different network configuration requirements. However, with the V-Firewall, this job is easy! At the time that I write this, the V-Firewall is the only solution available that provides a dedicated firewall tool for virtual machines in Hyper-V.
The firewall rules include the following configuration options:
- ARP Rule
- IP Rule
- Broadcast Rule
- Default Gateway Rule
Figure 2 – Rules Type
With these rules, it is possible to create and apply policies to block or allow almost everything through inbound, outbound or vice versa.
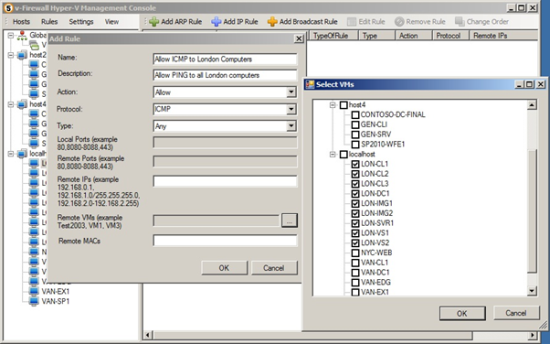
All rules can be applied to a single virtual machine, a group of VMs, or to all VMs (Global Configuration). This last option is great for administrators who want to create a firewall rule for multiple VMs with a few clicks, as shown in figure 3.
In addition to the rules is also possible to monitor the policies that have been allowed or denied in real time (figure 1).
Figure 3 displays a rule to allow ICMP for a group of VMs from a certain location.
Figure 3 – New ICMP Rule
For those who like automation and command line configuration, the V-Firewall support a number of commands through PowerShell. For the most common configuration tasks, you can perform them through the GUI or use PowerShell commandlets.
To use PowerShell cmdlets, simply import the V-Firewall Snap in with the command Add-PSSnapinRulesAPI and then several commands will be available, such as:
- Add-ARP-Rule
- Add-BroadcastIP-Rule
- Add-IP-Rule
- Set-Heartbeat
- Set-VMMonitoring
- Get-Heartbeat
- Get-LogRecords
- Get-Rules
- Get-VMIPMAC
- Get-VMMonitoring
- Remove-Rule
- Reset-Rules
- Set-Rule
Figure 4 shows how to add a rule to allow RDP protocol to a specific VM:
Figure 4 – Command let to allow RDP
In figure 5, you can see how to create an ARP rule to another VM.
Figure 5 – Command let to allow ARP
Antivirus/Antispyware
The antivirus and antispyware protection uses the Sophos engine and can scan the VMs at random, based on their workload and resource utilization to ensure that the AV/AS does not create any problems in the VM’s performance.
Figure 6 – Antivirus Option
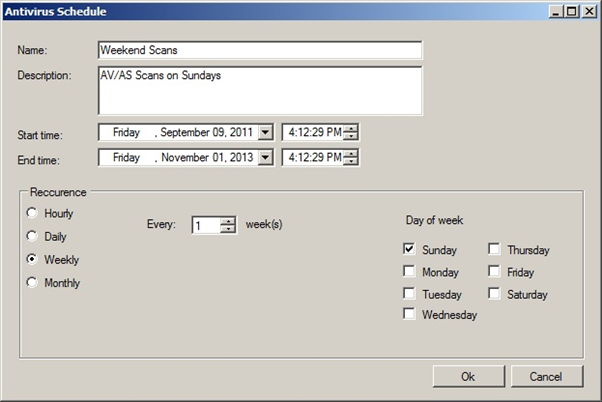
The options offered by antivirus are somewhat limited, but it is possible to do some basic customization. In figure 7 you can see an antivirus schedule configuration:
Figure 7 – Antivirus Schedule
Heartbeat Service
Heartbeat Service checks the VMs according to the rules specified to make sure the firewall and other policies are being applied. If the service finds any problems in applying these rules it may stop or pause the VM to ensure that their safety is not compromised. This is consistent with a “fail closed” approach to security.
Figure 8 – Heartbeat Service Parameters
Bandwidth Throttling
In scenarios where virtual machines share the same physical network card or maybe you have a VM that needs limited network bandwidth, you can apply rules to limit the network bandwidth available to the VM ensure that there is no network bottlenecks.
Figure 9 – Bandwidth Policy
So if you have a group of host computers running Hyper-V and you need to apply some antivirus updates, firewall policies and other configuration you have seen that V-Firewall may help you to address these policies.
Reference
For more information, access the website http://www.5nine.com/hyper-v-virtual-firewall2.aspx