Windows Troubleshooting: Account Lock Out - EventCombMT
Introduction
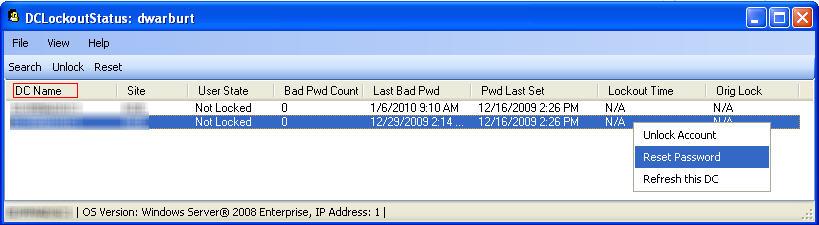
You can use LOCKOUTSTATUS.EXE (a free Microsoft tool) to help you troubleshoot locked out accounts. This tool will help you find the DC (Domain Controller) name where that account is locked out.
Download the Account Lockout and Management Tools
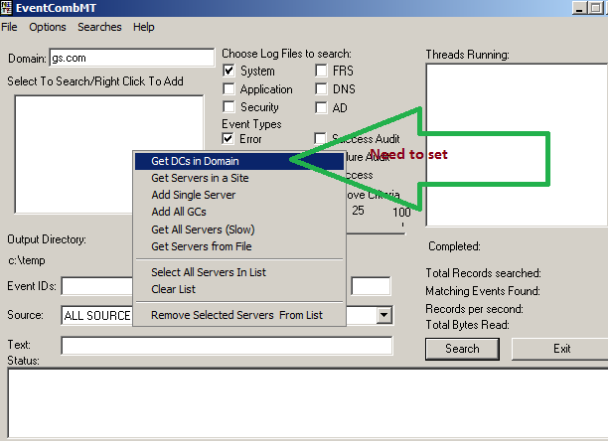
The Account Lockout and Management tools contains a utility called EVENTCOMBMT.EXE. There is a builtin search for searching for ACCOUNT LOCKED OUT events.
Using EventCombMT
In EventcombMT's events are for 2003; you need to add the 2008 event if your DCs are 2008.
- Windows Server 2008 log the event with ID 4740 for user account locked out
- Windows Server 2003 log the event with ID 644 for user account locked out
Finding Locked Out Accounts using PowerShell
search-adaccount -u -l | ft name,lastlogondate -auto
Search the Windows Event Logs for the Lockout Event using PowerShell
#Windows 2008
Get-EventLog -log Security | ? EventID -EQ 4740 ows 2008
Get-EventLog -log Security | ? EventID -EQ 4740
Get-EventLog -log Security | ? EventID -EQ 4740 ows 2008
Get-EventLog -log Security | ? EventID -EQ 4740
#Windows 2003
Get-EventLog -log Security | ? EventID -EQ 644
Use Repadmin for getting the lockout location & lockout time
repadmin /showobjmeta <dc_Name> "CN=test1,OU=win7,DC=Jaihanuman,DC=net"
32 entries.
Loc.USN Originating DSA Org.USN Org.Time/Date Ver Attribute
======= =============== ========= ============= === =========
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 objectClass
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 cn
45219 Default-First-Site-Name\TESTMAC01 45219 2013-11-27 13:44:00 2 description
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 givenName
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 instanceType
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 whenCreated
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 displayName
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 nTSecurityDescriptor
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 name
57741 Default-First-Site-Name\TESTMAC01 57741 2013-12-07 15:23:06 8 userAccountControl
45100 Default-First-Site-Name\TESTMAC01 45100 2013-11-26 12:26:00 1 codePage
45100 Default-First-Site-Name\TESTMAC01 45100 2013-11-26 12:26:00 1 countryCode
53312 Default-First-Site-Name\TESTMAC01 53312 2013-11-28 11:51:43 17 homeDirectory
57377 Default-First-Site-Name\TESTMAC01 57377 2013-11-28 12:00:38 16 homeDrive
57885 Default-First-Site-Name\TESTMAC01 57885 2013-12-17 13:22:47 3 dBCSPwd
45100 Default-First-Site-Name\TESTMAC01 45100 2013-11-26 12:26:00 1 logonHours
57885 Default-First-Site-Name\TESTMAC01 57885 2013-12-17 13:22:47 3 unicodePwd
57885 Default-First-Site-Name\TESTMAC01 57885 2013-12-17 13:22:47 3 ntPwdHistory
57885 Default-First-Site-Name\TESTMAC01 57885 2013-12-17 13:22:47 4 pwdLastSet
45100 Default-First-Site-Name\TESTMAC01 45100 2013-11-26 12:26:00 1 primaryGroupID
57886 Default-First-Site-Name\TESTMAC01 57886 2013-12-17 13:22:47 2 supplementalCredentials
45172 Default-First-Site-Name\TESTMAC01 45172 2013-11-27 10:05:21 8 profilePath
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 objectSid
45227 Default-First-Site-Name\TESTMAC01 45227 2013-11-27 13:56:43 6 comment
45100 Default-First-Site-Name\TESTMAC01 45100 2013-11-26 12:26:00 1 accountExpires
57885 Default-First-Site-Name\TESTMAC01 57885 2013-12-17 13:22:47 3 lmPwdHistory
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 sAMAccountName
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 sAMAccountType
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 userPrincipalName
57915 Default-First-Site-Name\TESTMAC01 57915 2013-12-17 13:29:09 1 lockoutTime
45099 Default-First-Site-Name\TESTMAC01 45099 2013-11-26 12:26:00 1 objectCategory
57716 Default-First-Site-Name\TESTMAC01 57716 2013-12-07 09:57:44 1 mail
1 entries.
Type Attribute Last Mod Time Originating DSA Loc.USN Org.USN Ver
======= ============ ============= ================= ======= ======= ===
Distinguished Name
=============================
PRESENT manager 2013-11-27 13:15:04 Default-First-Site-Name\TESTMAC01 45203 45203 1
CN=test2,OU=win7,DC=Jaihanuman,DC=net
Unlock an Account using PowerShell.
Unlock-ADAccount -Identity biswajit
Audit Events for Disabled User Accounts
- Event ID: 629 for 2003
- Event ID's 4725 (629+4096) for 2008
See Also
- Account Lockout Tools
- Maintaining and Monitoring Account Lockout
- Troubleshooting Account Lockout
- http://blogs.technet.com/b/askds/archive/tags/account+lockout/
- http://www.windowstricks.in/2009/07/account-lockout.html Tools for Troubleshooting Locked-Out Accounts –Windows ITPro
- Locked or not? Demystifying the UI behavior for account lockouts
- ADDS Audit