Private Cloud Technical Concept and Overview
Driven by pressure to do more with less, many of your customers turn increasingly to virtualization when they need to add capacity or deliver new or scaled out http://blogs.technet.com/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-85-24-metablogapi/5658.image_5F00_64BCDD48.pngservices. And yet, simple consolidation of servers—what some have called virtualization 1.0—is no longer sufficient. Your customers want the efficiency, simplicity, and cost-effectiveness of a fully virtualized and highly automated infrastructure. Indeed, many organizations are on a declared trajectory toward a full infrastructure-as-a-service (IaaS) model enabled by their own on-premises or off-premises private cloud.
Note:
This document is part of a collection of documents that comprise the Reference Architecture for Private Cloud document set. The Reference Architecture for Private Cloud documentation is a community collaboration project. Please feel free to edit this document to improve its quality. If you would like to be recognized for your work on improving this article, please include your name and any contact information you wish to share at the bottom of this page.
This article is no longer being updated by the Microsoft team that originally published it. It remains online for the community to update, if desired. Current documents from Microsoft that help you plan for cloud solutions with Microsoft products are found at the TechNet Library Solutions or Cloud and Datacenter Solutions pages.
This document provides a technical overview for private cloud so that you can begin to take advantage of this trend toward cloud computing and educate your customers about its possibilities.
Private Cloud Core Architecture Principles
These principles, defined below, help power the cloud’s elasticity and also distinguish it from a traditional local area network (LAN) in which key pieces are virtualized. While that virtualized LAN delivers some of the benefits of virtualization, such as increased utilization, a private cloud includes automation and management capabilities that can mean revolutionary changes in how you deliver IT services and how your customers consume them.
Resource Pooling
A private cloud depends on the flexible pooling of computing (processor and memory), storage, networking, and software resources. This pooling helps deliver greater utilization and efficiency and is powered by Hyper-V virtualization, which abstracts the platform from the physical infrastructure. Multiple consumers—such as multiple customers or multiple organizational units within a business—can share pooled resources, resulting in higher resource utilization and economies of scale for both service providers and consumers.
Elasticity and Perception of Infinite Capacity
From your customer’s perspective, cloud services should appear to have infinite capacity. End users can consume as much or as little of the service as needed, just as they consume electricity. This perception is possible because, in contrast to a reactive approach that leads to inefficient resource use, the private cloud facilitates proactive capacity planning so that the infrastructure can satisfy peak requests on demand. This principle helps achieve greater balance between the cost of unused capacity and the desire for agility.
Perception of Continuous Availability
From your customer’s perspective, cloud services should always be available when needed. The consumer should never experience an interruption in IT services, even if failures occur within the cloud infrastructure. To achieve this continuous availability, the private cloud architecture delivers a highly automated environment in which infrastructure redundancies, such as failover clustering, are complemented by intelligent automation and management capabilities.
Predictability
Both service providers and consumers require predictability from a private cloud infrastructure. For consumers, cloud services should be consistent—they should have the same quality and functionality each time they are used.
To achieve this predictability, the private cloud standardizes functions across physical servers, network devices, and storage. This standardization helps to assure consistent treatment of hosted workloads, even during fluctuating demand. With the private cloud, you can also benefit from predictability on the service provider’s side of the console through its management and automation tools, which standardize service offerings and processes. This predictability is a fundamental requirement if service providers are to deliver on the promised potential of a private cloud infrastructure.
Service Provider’s Approach to IT
Historically, when businesses needed new or expanded IT services, they purchased the necessary components and then built an infrastructure specific to the service requirements. The result was often disappointing in terms of agility and also meant delays, duplicate infrastructure, increased costs, and poor utilization.
Businesses can transform this state of affairs when they look at IT as a set of services they consume rather than as a collection of hardware they deploy. The private cloud helps partners to provide infrastructure as a service so that customers can consume what they need when they need it, avoiding the pitfalls of underutilized, duplicate infrastructure. In addition, the shared resource model means you can take advantage of economies of scale and greater agility in providing additional services or expanding existing ones.
Multi-tenancy
Partners can subdivide the private cloud and provision logically isolated resources to different customers. Customers can also benefit from the multitenant capabilities of an on-premises private cloud infrastructure because resources can be provisioned for distinct organizational units within the business, which facilitates usage metering and chargeback.
Security and Identity
The private cloud delivers strong security for cloud computing through three pillars:
- Protected infrastructure
- Application access
- Network access
The private cloud uses security and identity technologies to protect both physical and virtual hosts, information, and applications in the data center. These technologies take advantage of the least-privileged user account access principle—an approach that ensures that users always log on with limited user accounts until they are granted additional privileges.
The private cloud secures application access through integration of the identities and relationships that are part of the cloud infrastructure. This identity foundation ensures that users have secure access to IT resources using numerous devices, which helps customers maintain productivity.
Network access in the private cloud is secured at the perimeter through host based and network firewalls which combines a firewall with IP Security (IPSec) network layer encryption and authentication—and through endpoint protection software. IPsec also enables the private cloud to support logical isolation of server and domain resources so that administrators can limit access to authenticated and authorized computers.
For comprehensive coverage of cloud and private cloud security please see Cloud Computing Security Architecture and A Solution for Private Cloud Security.
Conceptual Architecture
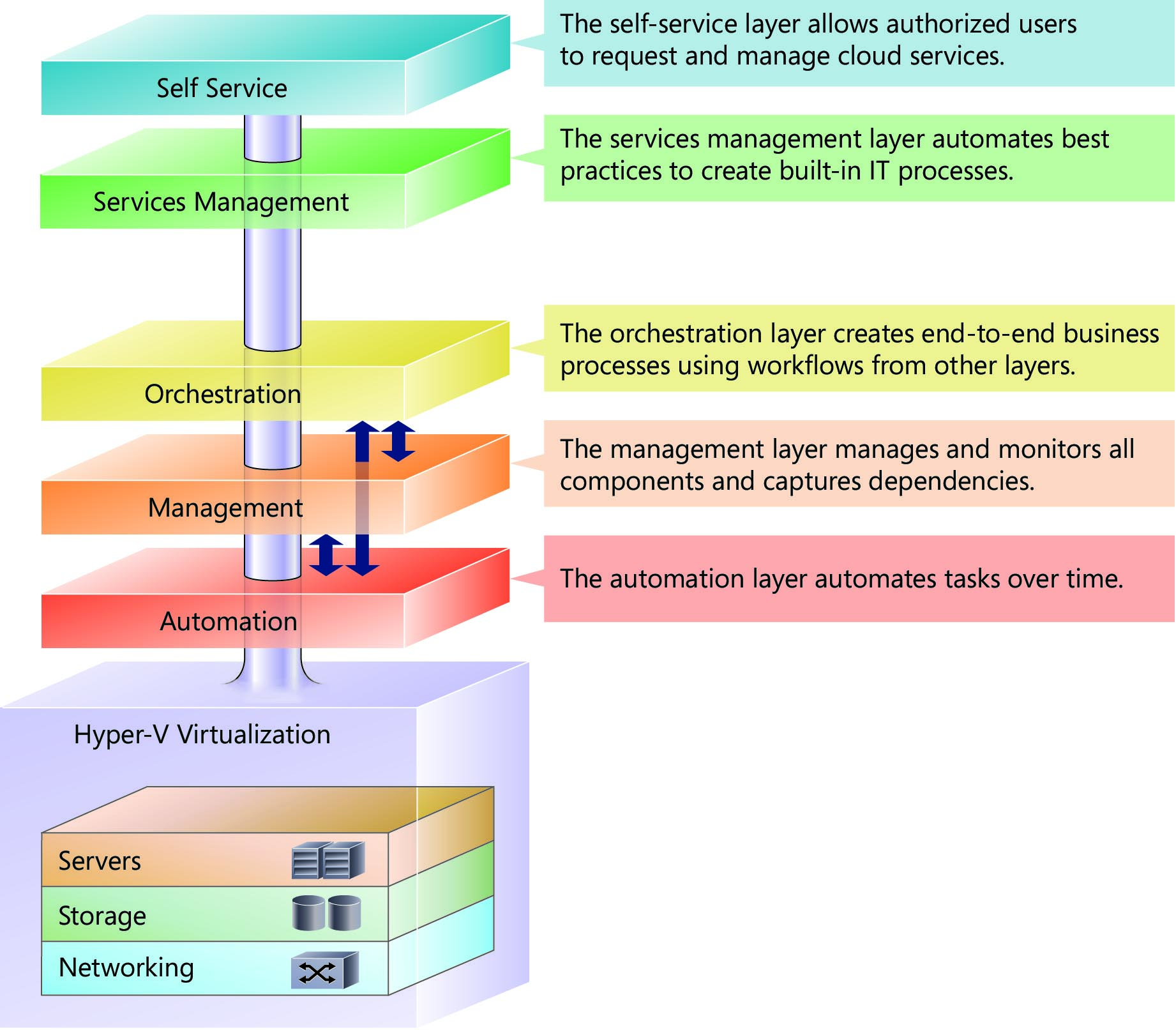
The private cloud features a layered architecture in which Hyper-V virtualization abstracts operating systems, data, applications, and user state from the underlying hardware (see figure 1). This virtualization layer enables the wide range of automation and management capabilities that differentiate a cloud infrastructure from a highly virtualized LAN. The layered architecture develops complex workflow and automation over time as various software pieces:
- Create a collection of simple automation tasks.
- Assemble those tasks into procedures that are managed by the management layer.
- Create workflows and process automation that are controlled by the orchestration layer.
A Closer Look at Private Cloud
The elasticity and other features of the private cloud shown in figure 1 are made possible through Hyper-V virtualization, which decouples operating systems, data, and applications from the underlying hardware. This abstraction powers the following layers and elements that define an elastic cloud infrastructure:
- Automation
- Management
- Orchestration
- Services Management
- Self Service
The Automation Layer
The ability to automate all expected operations over the lifetime of a hardware or software component is critical. Without this capability being threaded throughout all layers of the infrastructure, dynamic processes stop as soon as user intervention or other manual processing is required.
Windows PowerShell and several other foundational technologies, including Windows Management Instrumentation (WMI) and WS-Management, provide a robust automation layer across the private cloud. The integrated solution is a single automation framework and scripting language that can be used across the entire infrastructure.
The automation layer is made up of the foundational automation technology plus a series of single-purpose commands and scripts that perform operations such as starting or stopping a virtual machine (VM), rebooting a server, or applying a software update. These atomic units of automation are combined and executed by higher-level management systems. The modularity of this layered approach dramatically simplifies development, debugging, and maintenance.
The Management Layer
The management layer consists of the tools and systems used to deploy and operate the infrastructure. In most cases, this consists of a variety of different toolsets for managing hardware, software, and applications. Ideally, all components of the management system would take advantage of the automation layer and not introduce their own protocols, scripting languages, or other technologies (as it increases complexity and may require additional staff expertise).
The management layer is used to perform activities such as provisioning the storage area network (SAN), deploying an operating system, or monitoring an application. A key attribute is its abilities to manage and monitor every single component of the infrastructure remotely and to capture the dependencies among all of the infrastructure components.
The Orchestration Layer
The orchestration layer takes advantage of the management and automation layers. In much the same way that an enterprise resource planning (ERP) system manages a business process such as order fulfillment and handles exceptions such as inventory shortages, the orchestration layer provides an engine for IT-process automation and workflow. The orchestration layer is the critical interface between the IT organization and its infrastructure. It is the layer at which intent is transformed into workflow and automation.
Ideally, the orchestration layer provides a graphical interface in which complex workflows that consist of events and activities across multiple management-system components can be combined, so as to form an end-to-end IT business process such as automated patch management or automatic power management. The orchestration layer must provide the ability to design, test, implement, and monitor these IT workflows.
The Services Management Layer
The Service Management layer provides the means for automating and adapting IT service management best practices, such as those found in the IT Infrastructure Library (ITIL), to provide built-in processes for incident resolution, problem resolution, and change control. By providing an integrated service management platform IT can reduce costly downtime and improve the quality of the services in the data center.
The Self-Service Layer
The Self-Service layer provides an interface for private cloud tenants or authorized users to request, manage, and access the services, such as virtual machines, provided by the cloud architecture. Using role-based access control and authorization, the Self-Service layer provides the ability to delegate certain aspects of administration (such as starting/stopping VMs) to designated “tenant administrators.”
Security
Security for the private cloud is founded on the following three pillars:
- Protect the infrastructure with coordinated security technologies and controls at each layer of the architecture. These controls follow a defense-in-depth strategy, which assigns users, processes, and IT components a level of trust that governs review priority. The controls also follow the principle of least privilege for user account access. With this strategy, users always log on with the minimum privileges required to function, and administrator credentials are used only by authorized users for administrative functions. When additional privileges become necessary, automated workflows make change control simple and secure.
- Protect application access using Active Directory. Integrated with Windows Server 2008 R2, Active Directory provides out-of-the-box functionality needed to centrally configure and administer system, user, and application settings.
- Protect network access. The private cloud supports tools such as Windows Firewall with Advanced Security, Network Access Protection, and logical isolation of server and domain resources.
These server-side technologies are complemented by client security technologies such as antimalware applications and other endpoint protections.
For comprehensive coverage of cloud and private cloud security please see Cloud Computing Security Architecture and A Solution for Private Cloud Security.
What It Means for Your Business
Working together, these layers combine to form a private cloud solution that drives agility and flexibility deep into the infrastructure. This approach has real impact on specific business scenarios that you and your customers face every day.
VM Provisioning and Deprovisioning
One of the primary attributes of a cloud infrastructure—indeed, one thing that makes it a cloud infrastructure—is user self-service. When an infrastructure has this capability, the consumer of a service can request that service and the cloud infrastructure follows automated processes to rapidly provision the needed service and make it available to the requestor. This approach is in stark contrast to a hands-on, labor-intensive method that relies on manual workflows and error-prone processes that introduce delay and risk.
In the private cloud solution, user self-service also takes the form of automated VM provisioning and deprovisioning. Users can request one or more VMs or to delete their existing VMs from the Self-Service Portal or tenant user interface. The request triggers an automated workflow to either create or delete a VM based on the authorized settings input by the user or tenant.
The provisioning could be based on templates, such as when a user requests a standard VM configuration, or the user could make a series of selections (such as vCPUs and RAM) to cause a custom VM to be provisioned following established and automated procedures to gain any necessary authorization. If the request is authorized, the provisioning process should create a new VM per the user’s request, add the VM to any relevant management products in the private cloud and enable access to the VM by the requestor.
Infrastructure Monitoring
The private cloud helps IT administrators to monitor every major component of the solution and to generate alerts based on performance, capacity, and availability metrics. To effectively monitor cloud components requires checking for problems with hosts, host groups, guests, services, server resources, and system resources. Automated monitoring:
- Helps to ensure that the performance requirements of service level agreements (SLAs) are being met.
- Helps to ensure that specific administrative tasks, such as performing daily backup operations and checking server health, are being successfully completed.
- Helps to detect and address issues, such as a bottleneck in server performance or a need to add resources, before productivity is affected.
For example, administrators can use a management console to define metrics for server availability, or CPU and storage utilization, and to send an alert when one of the metrics is outside of an acceptable range. Operations Manager can also use agents to report performance and health data about guest and host operating systems. This information helps IT managers make informed decisions, reduce the costs of services, and improve the overall productivity of the infrastructure.
Infrastructure Maintenance
With the private cloud, administrators can perform maintenance on any component of the infrastructure without negatively affecting its availability. This “hot maintenance” capability allows a preventive approach that helps identify potential errors before they disrupt performance.
For example, patch management is a critical maintenance operation in a cloud infrastructure just as in a physical infrastructure. The private cloud must support a number of patch management tools and approaches. Ideally patch management in the private cloud can proceed with full visibility into infrastructure components and dependencies. This visibility also gives administrators greater control over patching in a virtual environment, which entails some special considerations such as the following:
- Host updates. A host that requires a restart after update installation affects the availability of all of its guests.
- Isolated guests. VMs might be connected to an internal network and inaccessible to the patch management solution.
- Powered-off guests. A VM that is either used for testing or stored in the library might be powered off for extended periods of time.
- Performance. Updating all the guests on a particular host can have a significant performance impact on all the machines.
Resource Optimization
Several of the private cloud core architecture principles—elasticity, perception of infinite capacity, and perception of continuous availability—depend directly on resource optimization. When it effectively optimizes pooled IT resources, the Microsoft private cloud can move workloads around the infrastructure based on need and performance, capacity, and availability metrics.
One key to this optimization of resources is Performance and Resource Optimization (PRO), PRO helps optimize resources, in part, through intelligent placement. During intelligent placement, Virtual Machine Manager chooses the most suitable host for each VM based on the VM’s configuration and the placement preference (load balancing or resource maximization) that is in effect. Virtual Machine Manager then migrates the VM.
This and other optimization capabilities can have remarkable impact. For example, workloads can be distributed across the infrastructure for maximum performance. Or, if needs or priorities change, the infrastructure can consolidate as many workloads as possible to the smallest number of hosts for dramatic reductions in power consumption.
Backup and Disaster Recovery
The private cloud provides a variety of backup and data recovery options, including host-based, guest-based, and SAN snapshots (depending upon the storage vendor’s level of Hyper-V integration). Any backup plan should protect not only VM files, but also database files and host data. The backup plan should also include a disaster recovery plan.
Backup and Recovery tools can provide continuous data protection for VMs in the private cloud. This protection includes:
- Online backup of supported guest VMs hosted on clustered or standalone systems
- Protection of VMs during the migration process
- Item-level recovery from host-level backup
Reporting
The private cloud provides a centralized reporting capability that serves as the foundation for capacity-based or utilization-based billing and chargeback to tenants. Comprehensive reports can also help reduce the amount of time required to manage data center resources. Reporting capability in the private cloud is provided through integration of several software components. The solution must provide standard reports that detail capacity, utilization, and other system metrics.
For example, one report that is helpful in optimizing the virtual environment is the Virtualization Candidates report. This report helps to identify the physical computers that are good candidates for conversion to VMs. Administrators can also use the report to identify little-used servers and to display the average values for a common set of performance counters for CPU, memory, and disk usage along with hardware configuration information, including processor speed, number of processors, and RAM. The report can be limited to computers that meet the specified CPU and RAM requirements, and it can sort the results.
Explore the Private Cloud for Your Customers
Many of your customers are ready for private cloud solutions, and Microsoft partners are well positioned to meet their needs. With trusted Microsoft products your customers already know, you can:
- Build or host a private cloud to more quickly deliver cloud benefits to customers.
- Offer indispensable services at exceptional value due to economies of scale.
- Remain competitive as the industry shifts toward a cloud model.
REFERENCES:
ACKNOWLEDGEMENTS LIST:
If you edit this page and would like acknowledgement of your participation in the v1 version of this document set, please include your name below:
[Enter your name here and include any contact information you would like to share]
**Return to **Reference Architecture for Private Cloud
TRANSLATIONS:
Resumen y concepto técnico de nube privada (es-ES)