Windows Azure Application With Active Directory - PaaS
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario you are developing a web application to be deployed to Windows Azure. It should serve corporate users whose identities and credentials are managed in corporate Active Directory (AD). The users should be provided with Single Sign-On (SSO) capability so they could use their corporate credentials to log on to the Windows Azure deployed web application when they are inside the corporate walls and when outside.
- Web Application to be deployed to Windows Azure.
- Corporate end users whose identities are managed in corporate AD.
- Need to provide SSO so that the end users could use same credentials managed in corporate AD when accessing the Windows Azure deployed web application.
Solution Approach
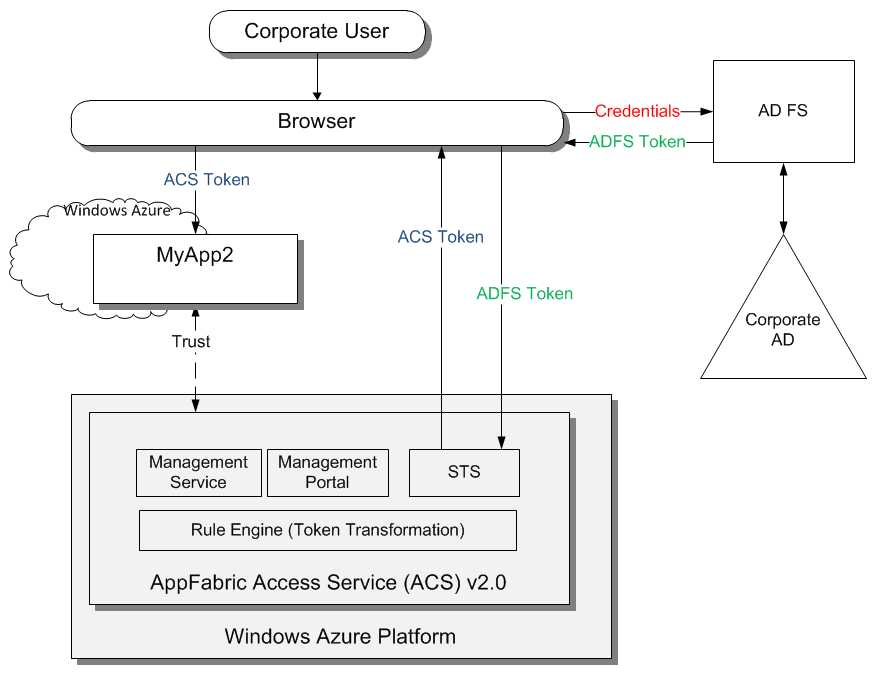
ACS and AD FS used to solve this scenario. ACS provides federation capability so it can integrate with WS-Federation compliant identity provider such as AD FS. AD FS provides Security Token Service using Active Directory as identity provider.
- ACS used to provide federation with AD FS that uses corporate AD as identity provider.
- AD FS issues tokens upon successful authentication.
- Application uses WIF to manage trust and validate and parse incoming tokens issued by AD FS and transformed by ACS.
- When accessing the web application from corporate walls the end user's request tot he application goes through series of redirects without requiring the user to provide his credentials. When accessing the application from outside of the corporate walls the user is required to provide his corporate credentials first through web form provided by AD FS.
Analysis
There is a possibility to configure SSO for Windows Azure deployed web application without use of ACS but directly to AD FS. This is outlined in details in Single Sign-On from Active Directory to a Windows Azure Application Whitepaper.
How To's
- Single Sign-On from Active Directory to a Windows Azure Application Whitepaper [not using ACS]
- How To: Configure AD FS 2.0 as an Identity Provider [using ACS]