Multi-Tenant Azure Application With Federated Authentication - Building SaaS
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario you are developing multi-tenant web application to be deployed on Azure. It requires that the application's tenants will be able to provide authentication to their users. When the tenant signs up for the application he should be able to select authentication method such as Facebook, Google, LiveID, Yahoo!, OpenID 2.0, or AD FS for corporate accounts. When finished with the sign up process the tenant's end users are readily able to use selected authentication method to log on to the application.
- Multi-tenant Software as a Service (SaaS) web application deployed to Windows Azure.
- The application requires authentication.
- Authentication method should be configured during the sign up process.
Solution Approach
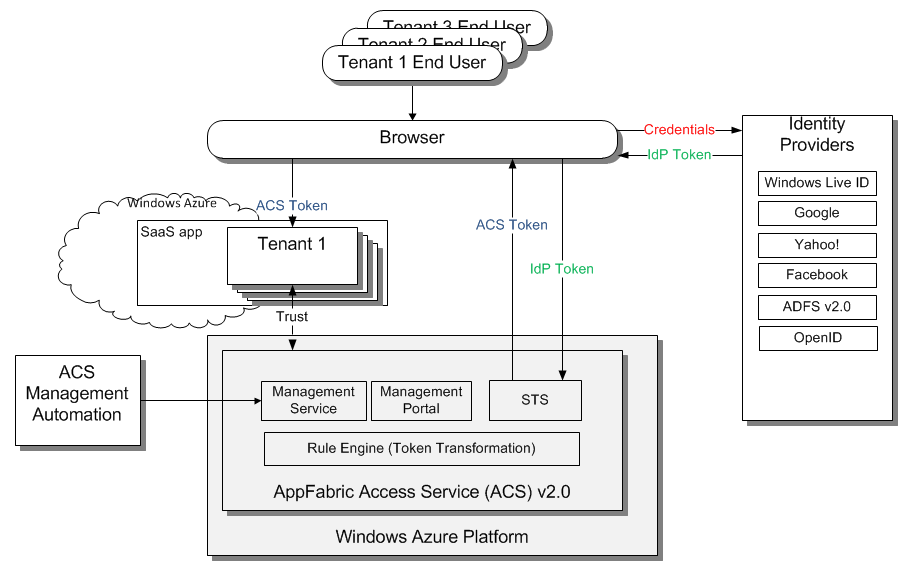
ACS is used to solve this scenario. ACS provides federation with Internet and enterprise identity providers. ACS Management Service is used during sign-up (on-boarding) process for automating the configuration for each tenant and its authentication method.
- ACS used for federation with Internet identity providers (IdP's) such as LiveID, Google, Facebook, Yahoo!, and OpenID 2.0 IdP's
- ACS used for federation via AD FS with enterprise identity providers that manage identities in Active Directory (AD)
- ACS Management Service used for automation during on-boarding process when configuring a tenant for specific IdP.
Analysis
ACS Management Service is the key enabling component in this scenario. ACS Management Service allows to perform management and administrative tasks for your ACS namespace programmatically. For more details read ACS Management Service.
How To's
- How To: Use Management Service to Configure an OpenID Identity Provider
- How To: Use Management Service to Configure Facebook as an Internet Identity Provider
- How To: Use Management Service to Configure AD FS 2.0 as an Enterprise Identity Provider
- How To: Use the ACS Management Service to Configure Rules and Rule Groups
- How To: Use ACS Management Service to Configure Certificates and Keys
- How To: Use ACS Management Service to Configure Service Identities
- How To: Use ACS Management Service to Configure Relying Party Applications