WCF (REST) Service With Federated Authentication
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario application consumes REST service that requires SWT token for authentication. Review the diagram below that schematically depicts the scenario:
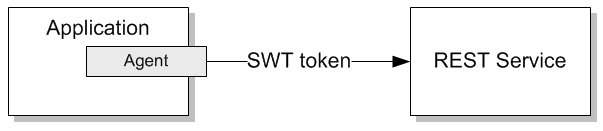
- Service exposing REST endpoint.
- Service requires SWT token.
- Credentials can be either/or UID/PWD pair, credentials, symmetric key.
- Identities are not managed by corporate Active Directory (AD)
Refer Additional Info at
http://blogs.msdn.com/b/endpoint/archive/2010/01/06/introducing-wcf-webhttp-services-in-net-4.aspx
Solution Approach
Windows Azure AppFabric Access Control Service (ACS) is used to solve this scenario.
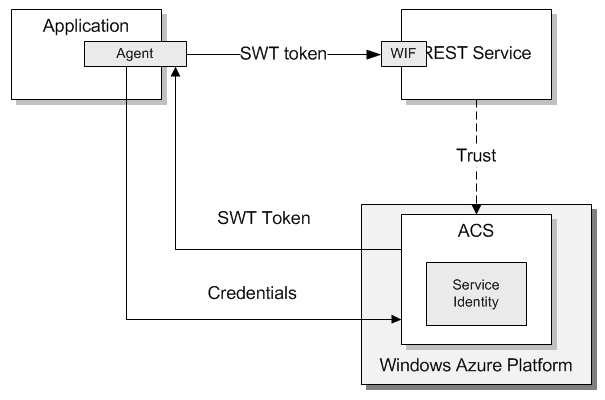
- ACS manages Service Identities (SI)
- ACS manages SI's credentials - UID/PWD pair or/and X.509 client certificates.
- WIF can be optionally used on the service side
Analysis
In this solution an agent (WCF client) send request directly to ACS requesting a SWT token based on the credentials which could be a UID/PWD pair, X.509 client certificate, or symmetric key. For more details on tokens read Token Formats Supported in ACS. ACS issues the SWT token upon successful authentication based on the credentials. The agent sends the token to the WCF service where it is validated and parsed. WIF is not used neither on client nor on the service side. At the time of this writing WIF does not provide SWT token handler. For detailed step-by-step procedure refer to How To: Authenticate to a REST WCF Service Deployed to Windows Azure Using ACS. Alternatively WIF can be used to write custom SWT token handler to be plugged into the WIF pipeline. Consult the following sample - Code Sample: Windows Phone 7 Application - for how to write SWT token handler that plugs into the WIF's pipeline. For more info read Web Services and ACS. ACS manages WCF service identities and their credentials using Service Identities entities.
How-To's
- How To: Configure Trust Between ACS and WCF Service Using Symmetric Keys
- How To: Authenticate to a REST WCF Service Deployed to Windows Azure Using ACS