WCF (SOAP) Service With Federated Authentication
Back to [[Windows Azure Active Directory Solutions For Developers]]
Scenario
In this scenario you have WCF service that exposes SOAP endpoint. It needs to authenticate requests based on issued SAML tokens.

- WCF Services exposes SOAP endpoint.
- Authenticates requests based on issued tokens.
- Tokens are of SAML format.
- Credentials could be either UID/PWD pair or X.509 client certificates
- Identities are not managed in corporate Active Directory (AD)
Solution Approach
Windows Azure AppFabrice Access Control Service (ACS) is used to solve this scenario.
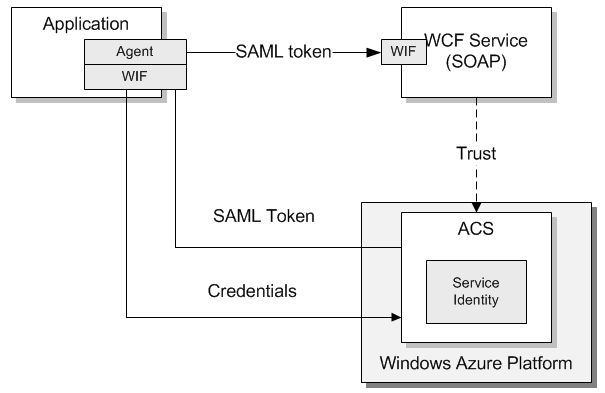
- ACS manages Service Identities (SI)
- ACS manages SI's credentials - UID/PWD pair or/and X.509 client certificates.
- WIF is used on the agent (WCF client) end to request the token from ACS and send it to the WCF service.
- WIF is used on the WCF service end to validate and parse the token issued by ACS
Analysis
In this solution an agent (WCF client) uses WIF to send request directly to ACS requesting a SAML token based on the credentials which could be a UID/PWD pair or X.509 client certificate. For more details on tokens read Token Formats Supported in ACS. ACS issues the SAML token upon successful authentication based on the credentials. The agent sends the token to the WCF service where it is validated and parsed using WIF. For more info read Web Services and ACS. ACS manages WCF service identities and their credentials using Service Identities entities.
How-To's
- How To: Add Service Identities with an X.509 Certificate, Password, or Symmetric Key
- How To: Authenticate with a Client Certificate to a WCF Service Protected by ACS
- How To: Authenticate with a Username and Password to a WCF Service Protected by ACS