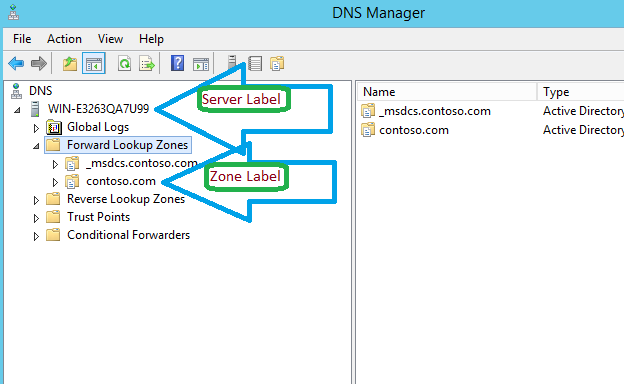
Windows Server: DNS Read-Only Console on Multi Domain Environment
Read-Only
For read-only permission, you need to grant the below three permissions.
- 1. Read all properties.
- 2. List Contents.
- 3. Read Permission.
Deny all
Please note you have to modify the ACL on server label and DNS Zone label as well.
If you have a multi-domain environment (Parent-Child) you have to modify the server label permission on each domain but for DNS Zones you have to modify the ACL once.
You should modify the each zone's ACL(Forward lookup and reverse lookup as well).
The best practice is to create a security group and assign the read-only permission.
Add the members to that group.
2. Follow the AGUDLP guideline for providing the permission.
Add users to a global group, add the global group to a Universal, add the Universal to a Domain Local Group, add the Domain Local Group to the resource, then provide permissions for the Domain Local Group to access the resource.
This can be expanded to AGGUUDLDLP.
Changing group scope
When you create a new group, by default the new group is configured as a security group with global scope, regardless of the current domain functional level. Although changing a group scope is not allowed in domains with a domain functional level of Windows 2000 mixed, the following conversions are allowed in domains with the domain functional level of Windows 2000 native or Windows Server 2003:
- Global to universal. This conversion is allowed only if the group that you want to change is not a member of another global scope group.
- Domain local to universal. This conversion is allowed only if the group that you want to change does not have another domain local group as a member.
- Universal to global. This conversion is allowed only if the group that you want to change does not have another universal group as a member.
- Universal to domain local. There are no restrictions for this operation.