Credential Guard :Say Good Bye to Pass The Hash/Ticket Attacks
Windows Modern Security
I have been evaluating Windows 10/ Server 2016 Security Features and one the one which I am working currently is "Credential Guard" - An awesome mitigation to PtH/T Attacks with just few clicks of Group policy configuration.
Introduced in Windows 10 Enterprise and Windows Server 2016, Credential Guard uses virtualization-based security to isolate secrets so that only privileged system software can access them. Unauthorized access to these secrets can lead to credential theft attacks, such as Pass-the-Hash or Pass-The-Ticket. Credential Guard prevents these attacks by protecting NTLM password hashes, Kerberos Ticket Granting Tickets, and credentials stored by applications as domain credentials.
By enabling Credential Guard, the following features and solutions are provided:
Hardware security NTLM, Kerberos, and Credential Manager take advantage of platform security features, including Secure Boot and virtualization, to protect credentials.
Virtualization-based security Windows NTLM and Kerberos derived credentials and other secrets run in a protected environment that is isolated from the running operating system.
When Credential Guard is enabled, NTLMv1, MS-CHAPv2, Digest, and CredSSP cannot use the signed-in credentials. Thus, single sign-on does not work with these protocols. However, applications can prompt for credentials or use credentials stored in the Windows Vault which are not protected by Credential Guard with any of these protocols. It is strongly recommended that valuable credentials, such as the sign-in credentials, not be used with any of these protocols. If these protocols must be used by domain or Azure AD users, secondary credentials should be provisioned for these use cases.+
When Credential Guard is enabled, Kerberos does not allow unconstrained Kerberos delegation or DES encryption, not only for signed-in credentials, but also prompted or saved credentials.
More details : /en-us/windows/access-protection/credential-guard/credential-guard-how-it-works
Prerequisites for Credential Guard : https://msdn.microsoft.com/en-us/windows/hardware/commercialize/design/minimum/device-guard-and-credential-guard
Here's a high-level overview on how the LSA is isolated by using virtualization-based security:
In this blog post I will show you different configurations and associated events and display information.
Firstly lets us examine a machine without credential guard enabled and see what we can derive from LSASS on Windows 10 - Build 1703 (Creators Update) machine / Domain Joined:
On my lab client machine I am using mimikatz tool to extract hashes from memory (LSASS)-
Figure 1.2
As in figure 1.2 we can see NTLM Hash is being displayed and can be utilized for PtH/T attacks.
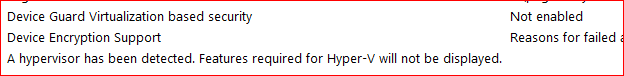
If you will check msinfo32 (Start > Run - msinfo32) report you will see following configuration being displayed :
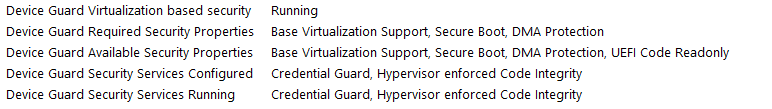
Device Guard Virtualization based security : Not Enabled
It would have been ideal if Microsoft should have kept different configuration / display names for credential guard and device guard.
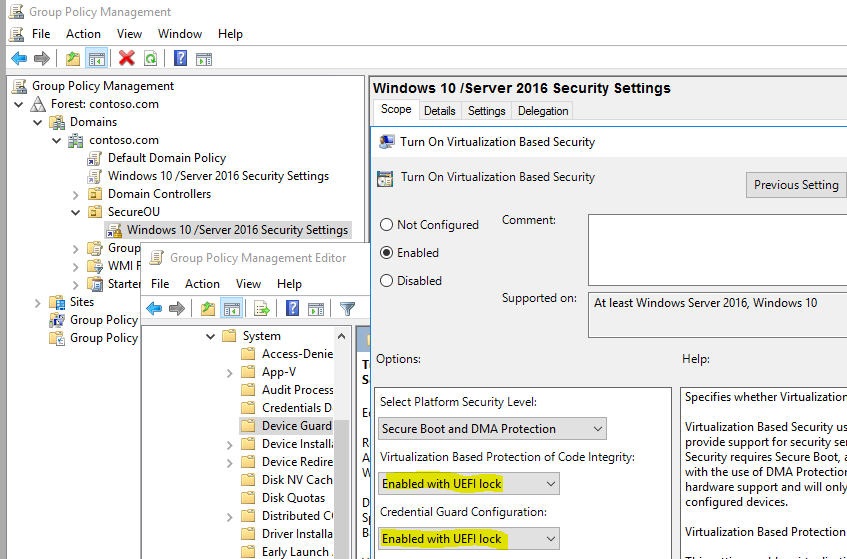
Let's now configure credential guard using active directory group policy (In my lab I am running Domain Controller on Windows Server 2016):
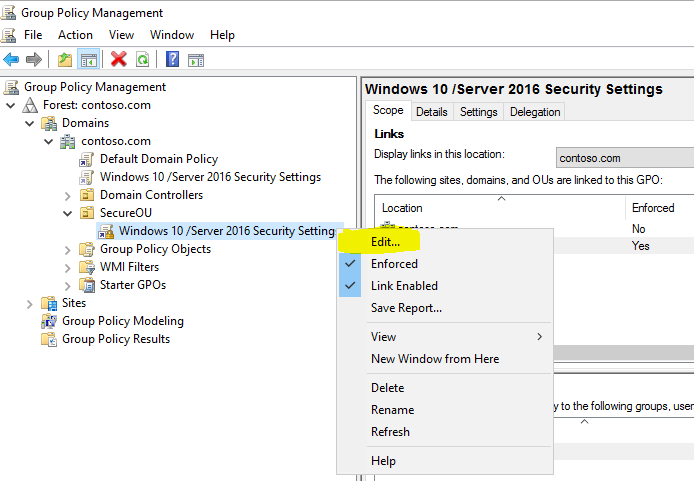
Open GPMC - Group Policy Management Configuration Management Console or AGPM - Advanced Group Policy Management MMC (Whatever you are using). Even for testing you can use local GPMC on Windows 10 or Server machine. In this post i am using GPMC.
Edit the GPO which is used for configuring Credential Guard
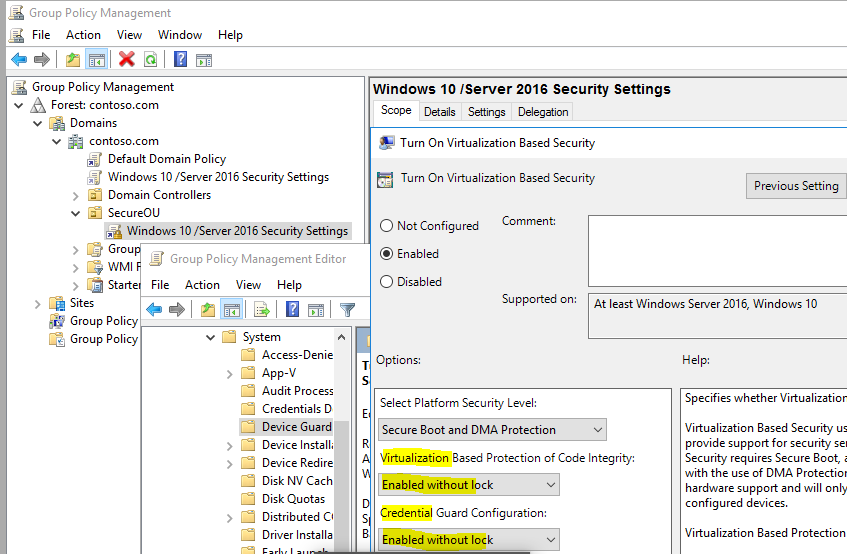
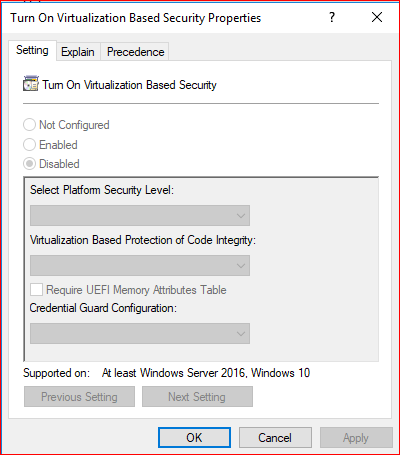
- Configure the configuration for Credential Guard
Policy Path: Computer Configuration\Administrative Templates\System\Device Guard
Policy Name |
Value |
Turn On Virtualization Based Security |
Enabled |
* Configurations:
Option |
Value |
Select Platform Security Level |
Secure Boot and DMA protection |
Virtualization Based Protection of Code Integrity |
Enabled without UEFI Lock |
Credential Guard Configuration |
Enabled without UEFI Lock |
We will discuss UEFI lock later in this blog
- Restart client and after reboot we can see "Running configuration" in msinfo32 summary:
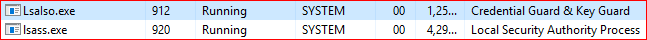
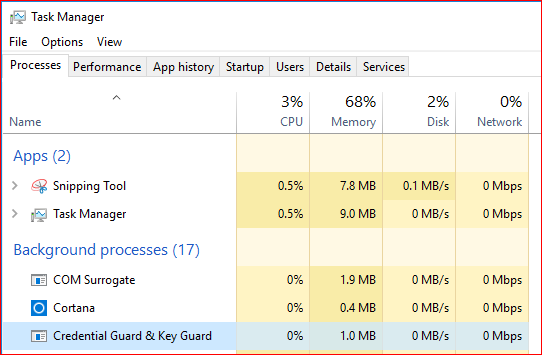
Also we can see one additional process called LSAISO under details TAB of Task manager and also as Credential Guard & Key Guard under Processes Tab :
- After running mimikatz tool again and this is what we will get from memory :
Fig 1.3
As we can see in Figure 1.3 there is no hash displayed and we can see an Encrypted Blob. Hence "ENDGAME" for Pass the Hash/Ticket (PtH/T) Attacks.
A peek at Event Viewer will show following informational Events :
SYSTEM Event ID 153 :
*The Virtualization Based Security (policies: VBS Enabled,VSM Required,Secure Boot,Iommu Protection,Mmio Nx,Strong MSR Filtering,Hvci,Boot Chain Signer Soft Enforced) is enabled due to VBS registry configuration with status STATUS_SUCCESS. *
Application and Services Logs > Microsoft > Windows > DeviceGuard- Event ID 7000

Device Guard successfully processed the Group Policy: Virtualization Based Security = Enabled, Secure Boot = On, DMA Protection = On, Virtualization Based Code Integrity = Enabled, Credential Guard = Enabled, Reboot required = No, Status = 0x0.
- In order to disable the setting , just configure GPO and choose option Disabled (Do not use Not Configured)
- Run gpupdate/force command or reboot the Client
After reboot you will see corresponding Event on Machine - Application and Services Logs > Microsoft > Windows > DeviceGuard- Event ID 7000
Configuration 2 : With UEFI Lock
Systems which support UEFI Secure Boot maintain an internal security database within UEFI Authenticated Variables. These variables are typically stored in erasable read/write memory with hardware protection against modification by unauthorized parties
In Event Viewer we will see System Event ID 153. However here we can see some difference :
Virtualization-based security (policies: VBS Enabled,VSM Required,Secure Boot,Iommu Protection,Mmio Nx,Strong MSR Filtering,Hvci,Boot Chain Signer Soft Enforced) is enabled due to VBS locked configuration.
As we can see configuration is set as "Enabled due to VBS locked configuration" and in earlier confirulation (Without UEFI lock) it was *enabled due to "*VBS registry configuration "
- In MSINFO32 summary following will be displayed :
So that means if we disable configuration using Group Policy as we did earlier that is not going to work and in this case we need to do following :
- Disable using GPO - choose option Disabled (Do not use Not Configured)
- We need to run following commands on elevated command prompt :
mountvol X: /s
copy %WINDIR%\System32\SecConfig.efi X:\EFI\Microsoft\Boot\SecConfig.efi /Y
bcdedit /create {0cb3b571-2f2e-4343-a879-d86a476d7215} /d "DebugTool" /application osloader
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} path "\EFI\Microsoft\Boot\SecConfig.efi"
bcdedit /set {bootmgr} bootsequence {0cb3b571-2f2e-4343-a879-d86a476d7215}
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} loadoptions DISABLE-LSA-ISO,DISABLE-VBS
bcdedit /set {0cb3b571-2f2e-4343-a879-d86a476d7215} device partition=X:
mountvol X: /d
Link : /en-us/windows/access-protection/credential-guard/credential-guard-manage>
Here we need to make sure we have both "DISABLE-LSA-ISO,DISABLE-VBS" added in command as GPO configuration which we used had both VBS Protection and Credential selected.
Above step is very Important in case of UEFI lock because of following :***
Systems which support UEFI Secure Boot maintain an internal security database within UEFI Authenticated Variables. T*hese variables are typically stored in erasable read/write memory with hardware protection against modification by unauthorized parties *
Even if we will format the OS drive or use new hard drive this setting will still be there as it is in stored in UEFI memory and only way to delete is to physically attend the machine and follow the steps that are in this blog
- After commands are executed successfully then Restart PC
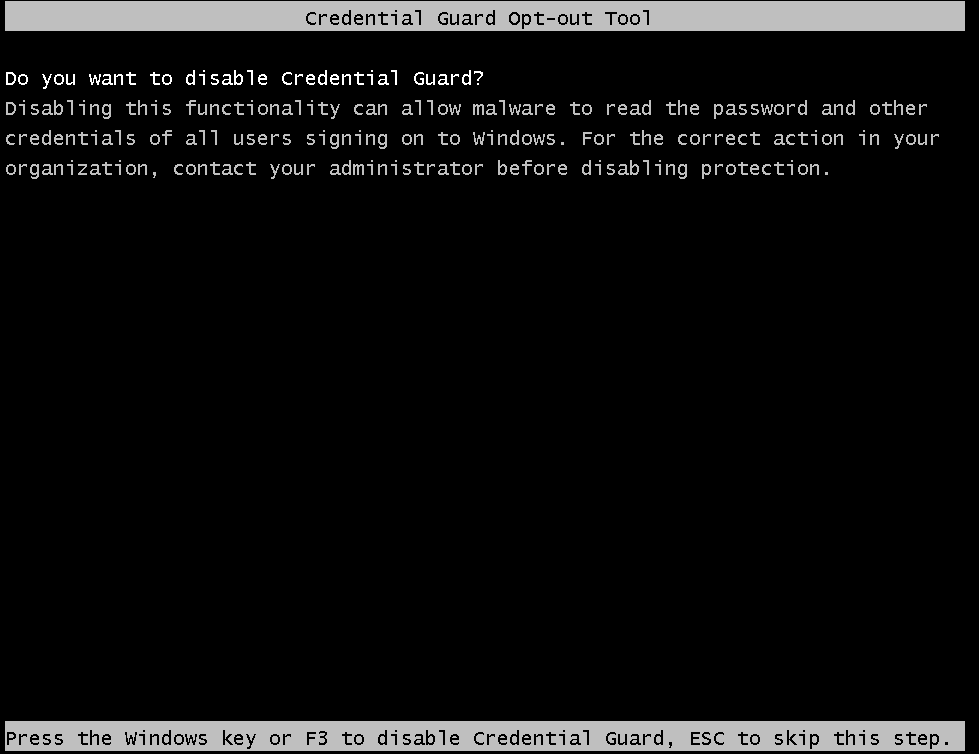
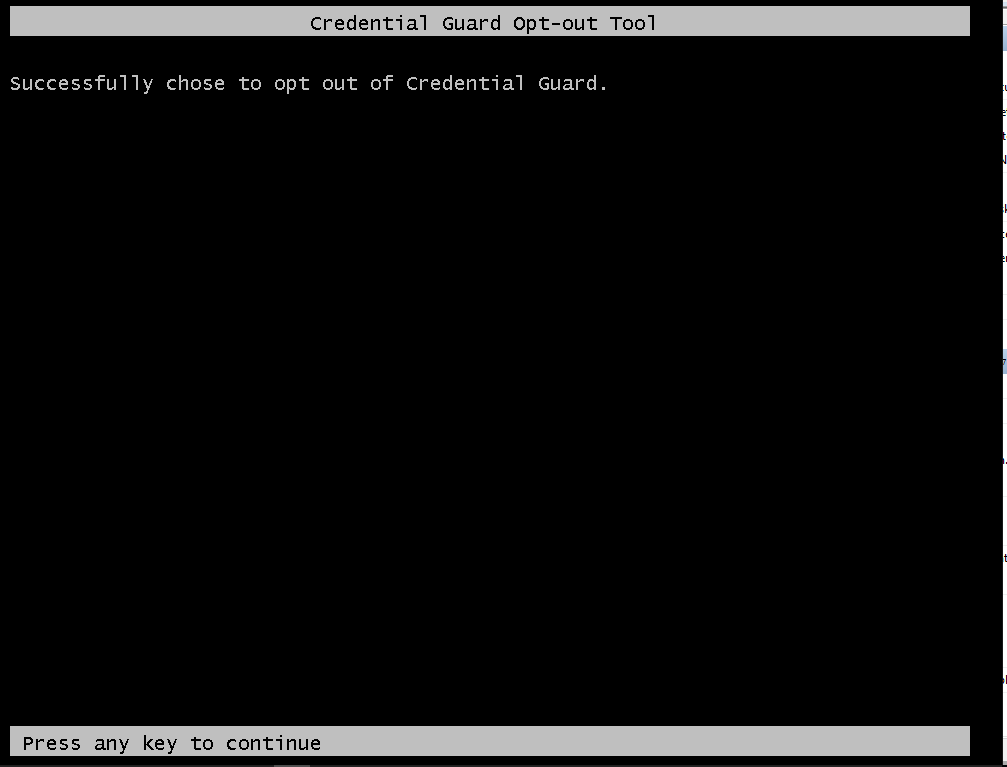
- Press F3 on Opt-Out Screen for Credential Guard and then Any key to continue:
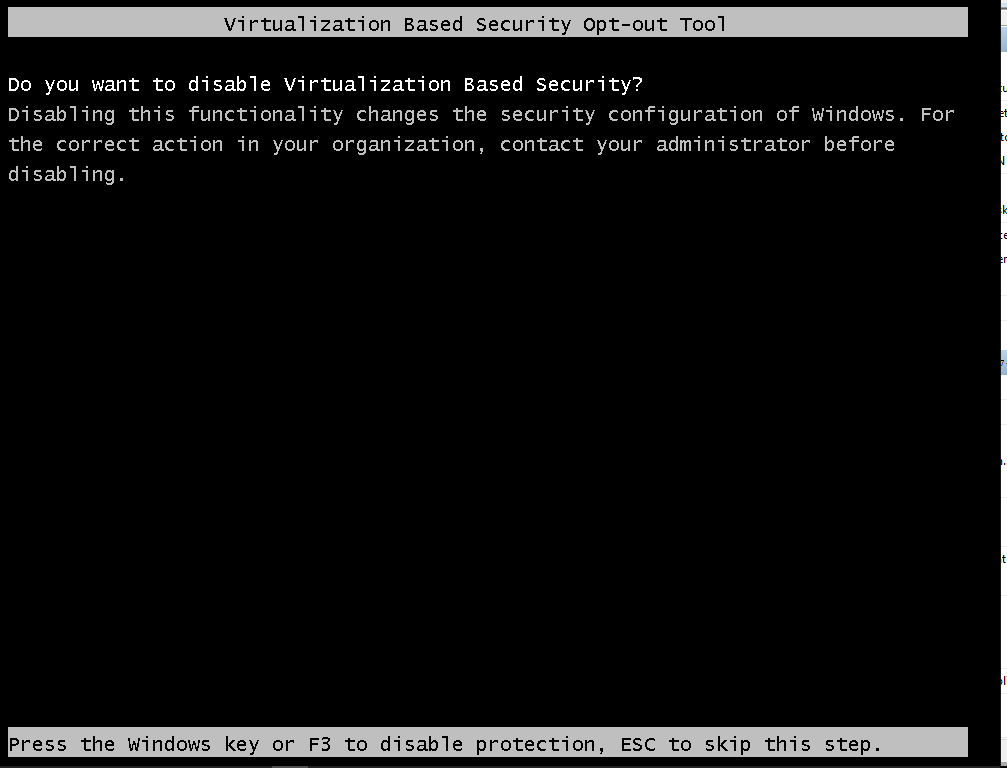
- Now press F3 again for Opt-Out for Virtualization Based Security and Any key to continue
- After reboot , MSINFO Summary will show following :
- Event will also show an event related to Opt-Out UEFI (System Event ID 153)

Virtualization-based security (policies: 0) is disabled due to opt-out UEFI variable.
- For Disabling VBS in Virtual Machine, following PowerShell command needs to executed on Host machine :
Set-VMSecurity -VMName <VMName> -VirtualizationBasedSecurityOptOut $true
Additional Information:
ETL Tracing example:
Logman.exe start kerb -p “Security: Kerberos Authentication” 0x40043 -o c:\kerb.etl –ets
Repro Issue
Logman.exe stop kerb -ets
PtH Mitigation Guide:
Credential Guard :
/en-us/windows/access-protection/credential-guard/credential-guard-how-it-works
Credential Guard Readiness Tool :
https://www.microsoft.com/en-us/download/details.aspx?id=53337